VLAN Configuration Commands Step by Step Explained
Switches do not understand broadcast messages. They forward them from all ports. VLAN is a switch feature. It allows us to create a group of devices that share broadcast messages.
We use the vlan command in global configuration mode to create a new VLAN or to update an existing VLAN. We use the switchport mode access vlan command in the interface configuration mode of a port to assign it to a VLAN.
Let's take an example to understand how to use these commands on Cisco switches.
Create a Packet Tracer lab as shown in the following image.

I explained the steps to create this practice lab in the following tutorial.
VLAN Practice Lab Setup in Packet Tracer
Packet Tracer is a network simulator software. You can download it from the following link.
Download Packet Tracer
In this lab, we have three switches and six PCs. Each switch has a connection to two PCs. All PCs have IP configurations. Three PCs have an IP configuration from the network 10.0.0.0/8, and the remaining three have an IP configuration from the network 20.0.0.0/8. The lab also has a router to provide connectivity between VLANs.

Configuring VLANs on switches
We will configure two VLANs in this network: VLAN-10 and VLAN-20 . We will use VLAN-10 for the network 10.0.0.0/8. We will use VLAN-20 for the network 20.0.0.0/8. We will keep one PC from each switch in a VLAN.

Access the first switch's CLI prompt. Enter global configuration mode and use the vlan command to create a new VLAN. This command needs a VLAN number as an argument. It checks the specified VLAN number for an existing VLAN before creating a new VLAN. If it finds an existing VLAN having the specified number, it does not create a new VLAN. It enters VLAN configuration mode for the existing VLAN. If it does not find an existing VLAN having the specified number, it creates a new VLAN and enters VLAN configuration mode for the new VLAN.
VLAN configuration mode allows us to configure additional options such as name and RSPAN . In a basic configuration, we do not need to configure these options. Use the exit command to exit VLAN configuration mode.
The following commands create VLAN-10.
The following commands create VLAN-20.
Since all three switches have PCs in these VLANs, you need to run the above commands on all switches.

After creating VLANs, we need to assign them to the switch ports. The switchport mode access vlan command assigns a VLAN to the switch port. It accepts a VLAN number as an argument. It runs in the interface configuration mode of the port. It assigns the specified VLAN number to the port. The device connected to the port becomes a member of the specified port.
The following commands make the device connected to port-1 a member of VLAN-10 .
The following commands make the device connected to port-2 a member of VLAN-20 .
You need to run the above commands on all switches.

A switch port can work in two modes: access and trunk. In access mode, it works with a single VLAN. In trunk mode, it works with multiple VLANs.
Access mode is the default mode on all switch ports. If you connect an end device to a switch port, you do not need to change the default mode. But if you connect a switch port to another switch port, you need to change the default mode to trunk mode on both ports.
Change default mode to trunk mode on ports you used to connect switches. Use the switchport mode trunk command to change the default mode. Run this command in the interface configuration mode of the port.
The following commands change the default mode to trunk mode on GigabitEtherent 0/1 .
The following commands change the default mode to trunk mode on GigabitEtherent 0/2 .
Run the above commands on all switches.

Testing and verifying VLANs
To test and verify VLAN configuration, you can check connectivity between PCs in the same VLAN.
Click the PC icon, click Desktop , and click Command prompt . Use the ping command to test connectivity.

PC0 is a member of VLAN-10. As we can see in the above image, it has connectivity with PC2 and PC4. PC2 and PC4 are other members of VLAN-10.

Similarly, you can also test connectivity between PC1, PC3, and PC5. These are members of VLAN-20.

PCs in the same VLAN have connectivity. It verifies VLAN configuration.
Connecting different VLANs
VLANs are logical subnets. PCs in different VLANs do not have connectivity. To provide connectivity between different VLANs, you need to configure a router. The last tutorial in this tutorial series explains how to configure a router to provide connectivity between different VLANs.
This tutorial is a part of the tutorial series on VLAN, VTP, and DTP Concepts and Configurations on Cisco Routers. Other parts of this series are the following.
Chapter 01 VLAN Basic Concepts Explained with Examples
Chapter 02 Advantages and Disadvantages of VLANs
Chapter 03 Static and Dynamic VLAN Membership Explained
Chapter 04 Access Link and Trunk Link Explained
Chapter 05 VLAN Tagging Explained with DTP Protocol
Chapter 06 DTP Modes and Protocol Explained
Chapter 07 802.1Q Native VLAN concept Explained
Chapter 08 Cisco Inter-Switch Link (ISL) Explained
Chapter 09 Trunk Tagging and Frame Tagging Explained
Chapter 10 VTP Modes and VTP Protocol Explained
Chapter 11 VTP Pruning on switches Explained
Chapter 12 VLAN Practice Lab Setup in Packet Tracer
Chapter 13 Configure VTP Server and Client in Switch
Chapter 14 VLAN Configuration Commands Step by Step Explained
Chapter 15 Router on Stick Configuration Explained
That's all for this tutorial. In this tutorial, we learned how to configure, test, and verify VLANs on switches.
By ComputerNetworkingNotes Updated on 2024-03-07 05:30:02 IST
ComputerNetworkingNotes CCNA Study Guide VLAN Configuration Commands Step by Step Explained
We do not accept any kind of Guest Post. Except Guest post submission, for any other query (such as adverting opportunity, product advertisement, feedback, suggestion, error reporting and technical issue) or simply just say to hello mail us [email protected]

Configuring 802.1X VLAN Assignment and MAB
1. Overview
2. Example for VLAN Assignment
3. Example for MAB
802.1X authentication is a network access control method which safeguards network security . If the client passes the RADIUS server authentication then the client can access the LAN. Otherwise, the client cannot access the LAN.
VLAN Assignment and MAB are two important features of 802.1X authentication, and act as safety controls.
VLAN Assignment
VLAN Assignment allows the RADIUS server to send the VLAN configuration to the port dynamically. VLAN Assignment is used together with 802.1X authentication. After the port is authenticated, the RADIUS server assigns the VLAN based on the username of the client connecting to the port. The username-to-VLAN mappings must already be stored in the RADIUS server database.
The figure below shows the typical topology of VLAN Assignment. VLAN Assignment is port-based. With VLAN Assignment enabled, the RADIUS server will send the VLAN configuration when the port is authenticated. VLAN IDs are assigned based on switch ports.
If the assigned VLAN is nonexistent on the switch, the switch will create the related VLAN automatically, add the authenticated port to the VLAN and change the PVID based on the assigned VLAN.
If the assigned VLAN exists on the switch, the switch will directly add the authenticated port to the related VLAN and change the PVID instead of creating a new VLAN .
If no VLAN is supplied by the RADIUS server or if 802.1X authentication is disabled, the port will be still in its original VLAN.

MAB (MAC Authentication Bypass) uses the MAC address of a device to determine whether the client can get access to the network. After checking the MAC addresses of the clients that you want to access the network, add these MAC addresses into the database of the RADIUS server. With MAB enabled on th port, the switch will learn the MAC address of the device automatically and send the authentication server a RADIUS access request frame with the client’s MAC address as the username and password. If the authorization succeeds, the RADIUS server grants the client access to the network. Thus devices can be authenticated without any client software installed. And MAB can be used to authenticate devices without 802.1X capability like IP phones.
MAB interacts with the other features:
802.1X authentication— MAB takes effect only if 802.1X authentication is enabled on the port.
VLAN Assignment— MAB can be used on a port with VLAN Assignment enabled. That is, if a client has an authorized MAC address identity, the switch assigns the client to a specific VLAN if VLAN Assignment is configured on the corresponding port.
2 Example for VLAN Assignment
2.1 Network Requirements
To enhance network security, a company requires that the employees can access the network normally only when their computers pass the authentication successfully. At the same time, to reduce the workload of the configuration, it is required that the ten authenticated computers can be automatically assigned to the VLANs of their departments. The network topology is shown as below.

2.2 Configuration Scheme
802.1X Authentication is commonly used in solving authentication and security problems for LAN ports. VLAN Assignment can assign multiple clients to different VLANs depending on their authentication information. Thus configure 802.1X Authentication and VLAN Assignment to meet the requirement.
The configuration is briefly summarized in the following outlines:
1) Build a RADIUS Server.
2) Configure 802.1X and VLAN Assignment on the switch.
3) Start the authentication on 802.1X client software.
2.3 RADIUS Server Introduction
A RADIUS server receives user authentication requests, authenticates the user, and then returns authentication results to the authenticator (the switch).
This guide takes FreeRADIUS.net as an example to build a RADIUS server. FreeRADIUS.net installation file can be downloaded from http://freeradius.net/index.html . Run the file and follow the wizard to install the FreeRADIUS.net on a local computer.
After installing FreeRADIUS.net on the computer, some configurations files should be modified to satisfy the 802.1X authentication requirements:
Modify the clients.conf to add RADIUS client (the switch) information.
Modify the users.conf to add user authentication information.
2.4 Configuration
Configuration Guidelines:
VLAN Assignment takes effect only when the control type is Port Based . Set the control type as Port Based on the ports connected to clients .
802.1X authentication and Port Security cannot be enabled at the same time. Before enabling 802.1X authentication, make sure that Port Security is disabled.
Keep 802.1X authentication disabled on ports connected to the authentication server, the internet and the management computer, which ensures the traffic will not be blocked for the switch.
Demonstrated with T2600G-28TS acting as the authenticator, FreeRADIUS.net acting as the RADIUS server and TP-Link 802.1X Client Software, the following sections provide configuration procedures. The configuration procedures on the switch will be given in two ways: using the GUI and using the CLI.
2.4.1 Build a RADIUS Server
For the network administrator, the first thing is to build a RADIUS server, and put the user information for employees into the RADIUS server. The network administrator can set different username and password for each employee or set a public username and password shared by all the employees in the same department. The setting of the username and password depends on the actual demands.

To avoid the format error of the adding code, use Notepad++ to edit configuration files.
One client section means a RADIUS client. You can choose one of the client sections and edit the following attributes. Or you can add a new client section to meet your requirements.
The clients.conf can be modified in three aspects:
The IP address of network segment of the authenticator (T2600G-28TS). After the installation is completed, the default configuration file contains the commonly used network segment. Thus you can keep it as default in most cases.
The secret which is the shared key between the RADIUS server and the switch. The RADIUS server and the switch use the key string to encrypt passwords and exchange responses.
The shortname which is used as an alias for the fully qualified domain name, or the IP address. A value can be filled in optionally for the shortname.
According to the network topology, add the following code and save the file.

The user information can be modified in four aspects:
User-name and User-Password , which is the authentication information of the clients . You can replace rfc3580 with the username which you want and replace demo with the new password. Or you can ignore the default user information and add new user information which has identical format in the next line.
Tunnel-Type , which indicates the tunneling protocol to be used. To configure VLAN Assignment, specify this value as VLAN.
Tunnel-Medium-Type , which indicates the transport medium to use when creating a tunnel for tunneling protocols. To configure VLAN Assignment, specify this value as IEEE-802.
Tunnel-Private-Group-Id , which indicates the group ID for a particular tunneled session, that is the assigned VLAN ID.
According to the network topology, add the following codes and save the file.

4) Click Restart FreeRaDIUS.net Service to restart FreeRaDIUS.net.
2.4.2 Configure VLAN Assignment on the Switch
Using the GUI
1) Choose the menu Network Security > AAA > Global Config to load the following page. In the Global Config section, enable AAA function and click Apply .
2) Choose the menu Network Security > AAA > Dot1x List to load the following page. In the Authentication Dot1x Method List section, select an existing RADIUS server group for authentication from the Pri1 drop-down list and click Apply .

3) Choose the menu Network Security > AAA > RADIUS Config to load the following page. Enter the IP address of the RADIUS server and the shared key which is pre-defined in the Radius Clients.conf.

4) Choose the menu Network Security > 802.1X > Global Config to load the following page. In the Global Config section, enable 802.1X and VLAN Assignment globally and click Apply .

5) Choose the menu Network Security > 802.1X > Port Config to load the following page. Select the port 1/0/3-13 which you want to deploy 802.1X VLAN Assignment and set the status for port1/0/3-13 as Enable . Set the control type as Port Based for port1/0/3-13. Set the status for port 1/0/1 and port 1/0/2 as Disable so that the RADIUS server and the internet will not be blocked for the switch.

Using the CLI
1) Enable AAA globally and configure the RADIUS parameters.
T2600G-28TS#configure
T2600G-28TS(config)#aaa enable
T2600G-28TS(config)#aaa authentication dot1x default radius
T2600G-28TS(config)#radius -server host 192.168.0.253 auth-port 1812 key 123456
2) Globally enable 802.1X authentication and set the authentication protocol. Enable VLAN Assignment.
T2600G-28TS(config)#dot1x system-auth-control
T2600G-28TS(config)#dot1x auth-method eap
T2600G-28TS(config)#dot1x vlan-assignment
3) Disable 802.1X authentication on port 1/0/1and port 1/0/2. Enable 802.1X authentication on port 1/0/3, set the mode as Auto, and set the control type as Port-Based.
T2600G-28TS(config)#interface range gigabitEthernet 1/0/1-2
T2600G-28TS(config-if-range)#no dot1x
T2600G-28TS(config-if-range)#exit
T2600G-28TS(config)#interface range gigabitEthernet 1/0/3-13
T2600G-28TS(config-if-range)#dot1x
T2600G-28TS(config-if-range)#dot1x port-method port-based
T2600G-28TS(config-if-range)#dot1x port-control auto
4) Verify the configurations.
Verify the global configurations of 802.1X authentication:
T2600G-28TS#show dot1x global
802.1X State: Enabled
Authentication Method: EAP
Handshake State: Enabled
Guest VLAN State: Disabled
Guest VLAN ID: N/A
802.1X Accounting State: Disabled
802.1X VLAN Assignment State: Enabled
Quiet-period State: Disabled
Quiet-period Timer: 10 sec.
Max Retry-times For RADIUS Packet: 3
Supplicant Timeout: 3 sec.
Verify the configurations of 802.1X authentication on the port:
T2600G-28TS#show dot1x interface
Port State MAB State GuestVLAN PortControl PortMethod Authorized LAG
---- ------ ------------ ------------ -------------- -------------- ------------- -----
Gi1/0/1 disabled disabled disabled auto mac-based authorized N/A
Gi1/0/2 disabled disabled disabled auto mac-based authorized N/A
Gi1/0/3 enabled disabled disabled auto port-based unauthorized N/A
Gi1/0/4 enabled disabled disabled auto port-based unauthorized N/A
Verify the configurations of RADIUS:
T2600G-28TS#show aaa global
AAA global status: Enable
Module Login List Enable List
Console default default
Telnet default default
Ssh default default
Http default default
T2600G-28TS#show aaa authentication dot1x
Methodlist pri1 pri2 pri3 pri4
default radius -- -- --
T2600G-28TS#show aaa group radius
192.168.0.253
2.4.3 Set Up Authentication on 802.1X Client Software
Before the employee can access the internet, the employee should input the authentication information on the 802.1X Client Software. The authentication information is the username and password which is set by the network administrator in the RADIUS server.

2) Enter the username and password. In this example, enter “tplink” as the username and “admin1” as the password , which is set in the RADIUS server, then click Connect .

Then the 802.1X client software will automatically register to the RADIUS server and get the authority to the internet from the RADIUS server.

When passing the authentication, the following screen will appear.

2.5 Verify the Configuration Result
After all the configurations are completed, you can follow the steps below to verify whether 802.1X VLAN Assignment works. Taking port 3 for a example, you can check the switch by using GUI and CLI.
1) Choose the menu Network Security > 802.1X > Port Config to check whether the port 1/0/3 passes the 802.1X authentication successfully. After passing the 802.1X authentication successfully, the Authorized state will change from Unauthorized to Authorized .

2) Choose the menu VLAN > 802.1Q VLAN > Global Config to check whether the port 1/0/3 is assigned to the corresponding VLAN.

1) Verify the 802.1X authorization states on the port:
---- ----- ---------- --------- ------------- ------------- ------------- -----
Gi1/0/3 enabled disabled disabled auto port-based authorized N/A
2) Verify the VLAN information:
T2600G-28TS#show vlan
VLAN Name Status Ports
----- -------------------- --------- ----------------------------------------
1 System-VLAN active Gi1/0/1, Gi1/0/2, Gi1/0/4, Gi1/0/5,
Gi1/0/6, Gi1/0/7, Gi1/0/8, Gi1/0/9,
Gi1/0/10, Gi1/0/11, Gi1/0/12, Gi1/0/13,
Gi1/0/14, Gi1/0/15, Gi1/0/16, Gi1/0/17,
Gi1/0/18, Gi1/0/19, Gi1/0/20, Gi1/0/21,
Gi1/0/22, Gi1/0/23, Gi1/0/24, Gi1/0/25,
Gi1/0/26, Gi1/0/27, Gi1/0/28
5 N/A active Gi1/0/3
Primary Secondary Type Ports
------- --------- ------------------ ----------------------------------------
The port has been assigned to the related VLAN. That means 802.1X VLAN Assignment works.
3 Example for MAB
3.1 Network Requirements
The network administrator wants to restrict the authority of a device to access the network resources. The device should be authenticated before getting access to the internet. For convenience, it is better that the authentication process can be performed automatically. The network topology is shown as below.

3.2 Configuration Scheme
MAB uses the MAC address of a device to determine whether the device can get access to the network. Thus MAB can be used to authenticate devices without 802.1X Client Software.
The configuration is briefly summarized in two steps:
2) Configure MAB on TP-Link switch.
3.3 Configuration
MAB uses the MAC address of the client as the username and password. Please check the MAC addresses of the clients that you want to access the network in advance.
MAB takes effect only when 802.1X Authentication is enabled. Enable 802.1X Authentication on the ports connected to clients.
MAB takes effect only when Guest VLAN is disabled. Ensure that Guest VLAN is disabled when configuring MAB.
Keep 802.1X authentication disabled on ports connected to the authentication server, the internet and the management computer, which ensures they will not be blocked from accessing the switch.
Demonstrated with T2600G-28TS acting as the authenticator, FreeRADIUS.net acting as the RADIUS server, the following sections provide configuration procedures. The configuration procedures on the switch will be given in two ways: using the GUI and using the CLI.
3.3.1 Build a RADIUS Server
1) Go to http://freeradius.net/index.html to download the FreeRADIUS.net and follow the wizard to install it.

To avoid the format errors when adding code, use Notepad++ to edit configuration files.
One client section means a RADIUS client. You can choose one of the section clients and edit the following attributes. Or you can add a new client section to meet your requirements. The Clients.conf should be modified in three aspects:
The shortname which is used as an alias for the fully qualified domain name, or the IP address of the RADIUS client. A value can be filled in optionally for the short name.

MAB uses the MAC address as the username and password. You can replace rfc3580 and demo with the allowed MAC address. Or you can ignore the default user information and add the MAC address in the next line.
Add the following codes and save the file:

5) Click Restart FreeRaDIUS.net Service to restart FreeRaDIUS.net.
3.3.2 Configure MAB on the Switch
1) Choose the menu Network Security > AAA > Global Config , enable AAA function on the switch and click Apply .
2) Choose the menu Network Security > AAA > Dot1x List, select an existing RADIUS server group for authentication from the Pri1 drop-down list and click Apply .
3) Choose the menu Network Security > AAA > RADIUS Config , and enter 192.168.0.253 which is the IP address of the RADIUS server. Enter the shared key between the RADIUS server and the switch. The RADIUS server and the switch use the key string to encrypt passwords and exchange responses.

4) Choose the menu Network Security > 802.1X > Global Config , enable 802.1X globally and click Apply .

5) Choose the menu Network Security > 802.1X > Port Config to load the following page. Select port 1/0/3 and set the status as Enable and set Control Type as Port Based . Enable MAB for port 1/0/3. Set the status for port 1/0/1 and port 1/0/2 as Disable so that the RADIUS server and the internet will not be blocked for the switch.

1) Enable AAA globally.
2) Globally enable 802.1X authentication and set the authentication protocol.
3) Disable 802.1X authentication on port 1/0/1and port 1/10/2. Enable 802.1X authentication and MAB on port 1/0/3, set the mode as Auto, and set the control type as Port Based.
T2600G-28TS(config)#interface gigabitEthernet 1/0/3
T2600G-28TS(config-if)#dot1x
T2600G-28TS(config-if)#dot1x port-method port-based
T2600G-28TS(config-if)#dot1x port-control auto
T2600G-28TS(config-if)#dot1x mab
T2600G-28TS(config-if)#exit
802.1X VLAN Assignment State: Disabled
---- ----- --------- ----------- -------------- ----------- ------------- -----
Gi1/0/3 enabled enabled disabled auto port-based unauthorized N/A
3.4 Verify the Configuration Result
After all configurations are completed, you can follow the steps below to test whether MAB works.
1) Choose the menu Network Security > 802.1X > Port Config to check whether the port 1/0/3 has passed the authentication successfully.

The port authentication state changes from Unauthorized to Authorized , that is, the port has passed the authentication.
2) Open a web browser and browse a website to check whether the PC can get access to the internet.
---- ------- ------------ ------------ ------------ --------------- ------------ -----
Gi1/0/3 enabled enabled disabled auto port-based authorized N/A
2) Open a web browser and browse a website and to check whether the PC can get access to the internet.

- Contact Sales

Named VLANs in MS Configurations
- Last updated
- Save as PDF
Meraki's VLAN Profiles provides the ability to map any VLAN to a name or a VLAN list to a group name. This function can be used for a number of scenarios on MR and MS as highlighted in the document: VLAN Profiles
Named VLANs on switchport configurations is currently an Early Access feature (Oct 2023) available under Organization > Early Access.
Named VLANs are available to be not only utilized for RADIUS based assignment, but also for dashboard based configurations. This provides a way to reference VLANs in a human-readable manner that helps alleviate the necessity for a secondary reference document to determine which VLAN is for which purpose.
Requirements
VLAN Names and Group Names for switchport configurations are supported on:
- All MS/CS networks on MS15 + firmware
- Trunk Port interfaces
- Access Port interfaces
VLAN Names and Groups are NOT currently supported on:
- MS/CS networks on < MS15 firmware
- Template Networks
- Switch Port Profiles
- MX switchports
- MR multi-port units (MR30H/MR36H)
NOTE: Please refer to the VLAN profiles documentation on the required firmware versions for use with RADIUS
Getting Started
For guidance on getting started and utilizing VLAN Profiles please see the documentation article here: VLAN Profiles
To be able to use names to reference VLANs on switchports, at least the Default VLAN Profile needs to be populated with as minimal as a single VLAN name and/or group. Every device in the network is bound to the default VLAN profile to start, with the ability for an admin to create non-default profiles for use-cases where a Meraki network device (MS / MR) utilizes a different VLAN ID or Group list for the same name.
Example: The default profile has a map of Employee to VLAN 10 , where on floor 2 the Employee VLAN is 20 . In this instance an administrator would create a non-default profile for Floor-2 and map Employee to VLAN 20 .
Once a VLAN or set of VLANs/groups are defined in the VLAN profile, the named VLANs will become available on switchport configurations under Switching > Switch Ports as well as under the per switch configurations found in Switching > Switches > {Select switch} > Ports. There are a few key things to keep in mind while using Named VLANs for configuration.
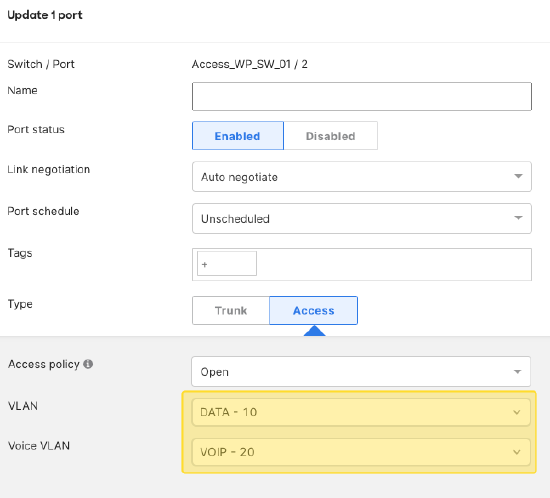
NOTE: Using integers instead of names can be configured by simply typing the VLAN ID instead of a name in the field/s on the switchport/s.
Validating Name to VLAN ID Assignments
Once the configurations are saved, the appropriate VLAN IDs should show on the switch port/s that were configured.
If a switch is receiving the VLAN ID from the default group, and the desire is for the switch to use a non-default profile, please validate the device's profile assignment under Network-wide > VLAN Profiles > Profile assignment.
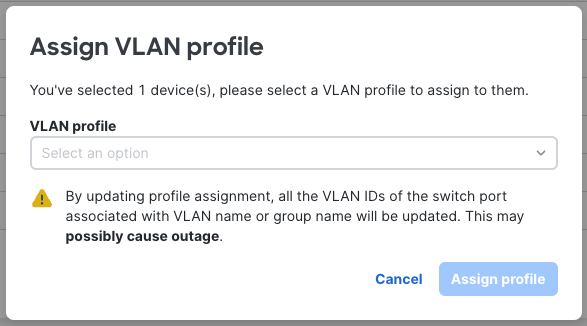
Changing a switch's profile
If a device or set of devices need to be moved from the default profile to a non-default profile, and if VLAN names have been used to configure the switch, the VLAN IDs will change with the profile. Please note if proper attention has not been paid, this could cause an outage as all Names and Groups will be updated with the destination profile's configuration.
The following warning will be presented:
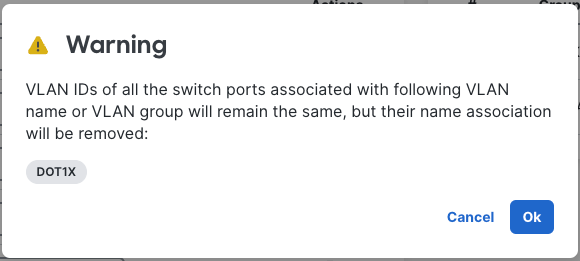
Deleting a VLAN Name from a profile
If a VLAN Name must be deleted, all switchports that were configured with the VLAN ID will retain the VLAN ID configuration, however the name will be removed from the individual port configuration in dashboard. The following warning will be presented:
Deleting a non-default profile with switches associated
In the event a non-default profile is deleted with switches associated to it, the respective switch port VLAN Names/Groups will be removed and the switches will retain their VLAN ID configuration.
- Engineering Mathematics
- Discrete Mathematics
- Operating System
- Computer Networks
- Digital Logic and Design
- C Programming
- Data Structures
- Theory of Computation
- Compiler Design
- Computer Org and Architecture
- CCNA Tutorial for Beginners
Basics of Computer Networking
- Network and Communication
- LAN Full Form
- What is OSI Model? - Layers of OSI Model
- TCP/IP Model
- How Data Encapsulation and De-encapsulation Works?
Components of Computer Networking
- NIC Full Form
- What is a network switch, and how does it work?
- What is Network Hub and How it Works?
- Introduction of a Router
- Types of Ethernet Cable
Transport Layer
- Transport Layer responsibilities
- Introduction of Ports in Computers
- What is Transmission Control Protocol (TCP)?
- TCP 3-Way Handshake Process
- User Datagram Protocol (UDP)
Network Layer
- Introduction and IPv4 Datagram Header
- Difference between Unicast, Broadcast and Multicast in Computer Network
- Structure and Types of IP Address
IPv4 Addressing
- What is IPv4?
- Role of Subnet Mask
- Introduction of Classful IP Addressing
- Introduction To Subnetting
- Classless Inter Domain Routing (CIDR)
- Introduction of Variable Length Subnet Mask (VLSM)
- Private IP Addresses in Networking
Data Link Layer
- What is Ethernet?
- What is MAC Address?
- What is an IP Address?
Physical Layer
- Ethernet Frame Format
- What is Power Over Ethernet (POE)?
Cisco Networking Devices
- Network Devices (Hub, Repeater, Bridge, Switch, Router, Gateways and Brouter)
- Collision Detection in CSMA/CD
- Collision Domain and Broadcast Domain in Computer Network
- Difference between layer-2 and layer-3 switches
Life of a Packet
- Working of Domain Name System (DNS) Server
- Configuring DHCP and Web Server in Cisco Packet Tracer
- How Address Resolution Protocol (ARP) works?
Router and Switch Basic Configuration
- Cisco Router basic commands
- Configure IP Address for Interface in Cisco Switches
- Transmission Modes in Computer Networks (Simplex, Half-Duplex and Full-Duplex)
- Link Layer Discovery Protocol (LLDP)
- What is Cisco Discovery Protocol (CDP)?
Cisco Device Management
- What are the different memories used in a CISCO router?
- Router Boot Sequence
- Recovering password in Cisco Routers
- Catalyst Switch Password Reset in Cisco
- Process of Backing Up and Restoring the Cisco IOS
- File Transfer Protocol (FTP)
- Difference between FTP and TFTP
- Backing up Cisco IOS Router image
- Steps Involves in Cisco Router Configuration Backups
Basic Network Trouble shooting
- Troubleshooting Questions on OS and Networking asked in Cloud based Interview
- Internet Control Message Protocol (ICMP)
- What is Ping?
- traceroute Command in Linux with Examples
IPv4 Routing
- What is IP Routing?
- Routing Tables in Computer Network
- Difference between Static and Dynamic Routing
- What is Floating Static Route ?
- How to Add a Static Route to Windows Routing Table?
Dynamic Routing Protocols
- Routing Protocol Code
- Difference between IGRP and BGP
- Administrative Distance (AD) and Autonomous System (AS)
- Configuring a Loopback Interface in Cisco
- What is a Loopback Address?
- What is Passive-Interface Command Behavior in RIP, EIGRP & OSPF?
Interior Gateway Protocols
- Routing Information Protocol (RIP)
- Configuring RIP Default Information Originate in Cisco
- Configuring RIP Versions 1 and 2 in Cisco
- EIGRP fundamentals
- Features of Enhanced Interior Gateway Routing Protocol (EIGRP)
- Types of EIGRP Packet in Computer Network
- How to Configure EIGRP Summarization in Cisco?
Open Shortest Path First(OSPF)
- Open shortest path first (OSPF) router roles and configuration
- Difference between EIGRP and OSPF
- Bandwidth Allocation Control Protocol (BACP)
- Open shortest path first (OSPF) - Set 2
- OSPF Implementation
- Explain OSPF DR/BDR Election?
- Configuring OSPF Passive Interface in Cisco
- Configuring OSPF Default Route Propagation
- Configuring OSPF Maximum Paths
- Configuring OSPF Route Summarization in Cisco
- Configuring OSPF Network Types in Cisco
Virtual Local Area Network(VLAN)
- Three-Layer Hierarchical Model in Cisco
- 2 - Tier And 3 - Tier Architecture in Networking
- Spine-Leaf Architecture
Virtual LAN (VLAN)
- Configuring and Verifying VLANs in Cisco
- Access and Trunk Ports
- What is ISL(Inter-Switch Link)?
- Inter-Switch Link (ISL) and IEEE 802.1Q
- Access Ports (Data and Voice) in CCNA
- Dynamic Trunking Protocol (DTP)
- VLAN Trunking Protocol (VTP)
- What are the VTP Modes?
Inter-V LAN Routing
- Inter VLAN Routing by Layer 3 Switch
- Configuration of Router on a stick
Dynamic Host Control Protocol(DHCP)
- Difference between DNS and DHCP
- How to Configure DHCP Server on a Cisco Router?
- DHCP Relay Agent in Computer Network
- What is APIPA (Automatic Private IP Addressing)?
Hot Standby Routing Protocol(HSRP)
- Redundant Link problems in Computer Network
- Firsthop Redundancy Protocol
- Hot Standby Router Protocol (HSRP)
Spanning Tree Protocol(STP)
- Introduction of Spanning Tree Protocol (STP)
- What is Bridge in Computer Network - Types, Uses, Functions & Differences
- Working of Spanning Tree Protocol (STP)
- Root Bridge Election in Spanning Tree Protocol
- How Spanning Tree Protocol (STP) Select Designated Port?
- Types of Spanning Tree Protocol (STP)
- Rapid Spanning Tree Protocol
- Configuring Spanning Tree Protocol Portfast
Ethernet Channel
- EtherChannel in Computer Network
- Configure, Verify and Troubleshoot (Layer 2/Layer 3) EtherChannel
- Link Aggregation Control Protocol
Switch Security
- DHCP Snooping
- Wireless Security | Set 1
- Port Security in Computer Network
- Configuring Port Security on Cisco IOS Switch
Access Control List(ACL)
- Standard Access-List
- Static NAT Configuration in Cisco
- Dynamic NAT Configuration in Cisco
- Extended Access-List
- Reflexive Access-List
IPv6 Addressing and Routing
- What is IPv6?
- Internet Protocol version 6 (IPv6)
- IPv6 EUI-64 (Extended Unique Identifier)
- Differences between IPv4 and IPv6
- Global Unicast Address in CCNA
- Link Local Address
- What is IPv6 Address Planning?
- How to Configure IPv6 on CISCO Router?
- What is IPv6 Stateless Address Autoconfiguration ?
- RPL (IPv6 Routing protocol)
Wide Area Network
- WAN Full Form
- What is VPN and How It Works?
- Overview of Wireless Wide Area Network (WWAN)
- Multi Protocol Label Switching (MPLS)
- Point-to-Point Protocol (PPP) Suite
Security Concepts
- Types of Cyber Attacks
- Types of Network Firewall
- Introduction of Firewall in Computer Network
- Intrusion Detection System (IDS)
- Intrusion Prevention System (IPS)
- Difference Between Symmetric and Asymmetric Key Encryption
- HTTP Full Form
- Explain the Working of HTTPS
- What is Attack Mitigation?
Network Device Security
- TELNET and SSH in Cisco devices
- How to configure SSH Client in Linux ?
- AAA (Authentication, Authorization and Accounting) configuration (locally)
- RADIUS Protocol
- TACACS+ Protocol
- Network Time Protocol (NTP)
- Configure and Verify NTP Operating in Client and Server Mode
Network Device Management
- What is Syslog server and its working ?
- Command-Line Tools and Utilities For Network Management in Linux
- Simple Network Management Protocol (SNMP)
- Overview of SNMPv3
Wireless Networking
- Wired and Wireless Networking
- What is a Wireless Access Point?
- Cisco Wireless Architecture and AP Modes
- Physical Infrastructure Connections of WLAN Components
- WiFi and its Amendments
- Types of Wireless Security Encryption
Virtual LAN (VLAN) is a concept in which we can divide the devices logically on layer 2 (data link layer). Generally, layer 3 devices divide the broadcast domain but the broadcast domain can be divided by switches using the concept of VLAN.
A broadcast domain is a network segment in which if a device broadcast a packet then all the devices in the same broadcast domain will receive it. The devices in the same broadcast domain will receive all the broadcast packets but it is limited to switches only as routers don’t forward out the broadcast packet. To forward out the packets to different VLAN (from one VLAN to another) or broadcast domains, inter Vlan routing is needed. Through VLAN, different small-size sub-networks are created which are comparatively easy to handle.
VLAN ranges:
- VLAN 0, 4095: These are reserved VLAN which cannot be seen or used.
- VLAN 1: It is the default VLAN of switches. By default, all switch ports are in VLAN. This VLAN can’t be deleted or edit but can be used.
- VLAN 2-1001: This is a normal VLAN range. We can create, edit and delete these VLAN.
- VLAN 1002-1005: These are CISCO defaults for fddi and token rings. These VLAN can’t be deleted.
- Vlan 1006-4094: This is the extended range of Vlan.
Configuration – We can simply create VLANs by simply assigning the vlan-id and Vlan name.
Here, 2 is the Vlan I’d and accounts is the Vlan name. Now, we assign Vlan to the switch ports.e.g-
Also, switchport range can be assigned to required vlans.
By this, switchport fa0/0, fa0/1, fa0-2 will be assigned Vlan 2.
Example –

Assigning IP address 192.168.1.1/24, 192.168.1.2/24 and 192.168.2.1/24 to the PC’s. Now, we will create Vlan 2 and 3 on switch.
We have made VLANs but the most important part is to assign switch ports to the VLANs.
As seen, we have assigned Vlan 2 to fa0/0, fa0/2, and Vlan 3 to fa0/1.
VLANs offer several features and benefits, including:
- Improved network security: VLANs can be used to separate network traffic and limit access to specific network resources. This improves security by preventing unauthorized access to sensitive data and network resources.
- Better network performance: By segregating network traffic into smaller logical networks, VLANs can reduce the amount of broadcast traffic and improve network performance.
- Simplified network management: VLANs allow network administrators to group devices together logically, rather than physically, which can simplify network management tasks such as configuration, troubleshooting, and maintenance.
- Flexibility: VLANs can be configured dynamically, allowing network administrators to quickly and easily adjust network configurations as needed.
- Cost savings: VLANs can help reduce hardware costs by allowing multiple virtual networks to share a single physical network infrastructure.
- Scalability: VLANs can be used to segment a network into smaller, more manageable groups as the network grows in size and complexity.
Some of the key features of VLANs include:
- VLAN tagging: VLAN tagging is a way to identify and distinguish VLAN traffic from other network traffic. This is typically done by adding a VLAN tag to the Ethernet frame header.
- VLAN membership: VLAN membership determines which devices are assigned to which VLANs. Devices can be assigned to VLANs based on port, MAC address, or other criteria.
- VLAN trunking: VLAN trunking allows multiple VLANs to be carried over a single physical link. This is typically done using a protocol such as IEEE 802.1Q.
- VLAN management: VLAN management involves configuring and managing VLANs, including assigning devices to VLANs, configuring VLAN tags, and configuring VLAN trunking.
Types of connections in VLAN –
There are three ways to connect devices on a VLAN, the type of connections are based on the connected devices i.e. whether they are VLAN-aware(A device that understands VLAN formats and VLAN membership) or VLAN-unaware(A device that doesn’t understand VLAN format and VLAN membership).
- Trunk Link – All connected devices to a trunk link must be VLAN-aware. All frames on this should have a special header attached to it called tagged frames.
- Access link – It connects VLAN-unaware devices to a VLAN-aware bridge. All frames on the access link must be untagged.
- Hybrid link – It is a combination of the Trunk link and Access link. Here both VLAN-unaware and VLAN-aware devices are attached and it can have both tagged and untagged frames.
Advantages –
- Performance – The network traffic is full of broadcast and multicast. VLAN reduces the need to send such traffic to unnecessary destinations. e.g.-If the traffic is intended for 2 users but as 10 devices are present in the same broadcast domain, therefore, all will receive the traffic i.e. wastage of bandwidth but if we make VLANs, then the broadcast or multicast packet will go to the intended users only.
- Formation of virtual groups – As there are different departments in every organization namely sales, finance etc., VLANs can be very useful in order to group the devices logically according to their departments.
- Security – In the same network, sensitive data can be broadcast which can be accessed by the outsider but by creating VLAN, we can control broadcast domains, set up firewalls, restrict access. Also, VLANs can be used to inform the network manager of an intrusion. Hence, VLANs greatly enhance network security.
- Flexibility – VLAN provide flexibility to add, remove the number of host we want.
- Cost reduction – VLANs can be used to create broadcast domains which eliminate the need for expensive routers. By using Vlan, the number of small size broadcast domain can be increased which are easy to handle as compared to a bigger broadcast domain.
Disadvantages of VLAN
- Complexity: VLANs can be complex to configure and manage, particularly in large or dynamic cloud computing environments.
- Limited scalability: VLANs are limited by the number of available VLAN IDs, which can be a constraint in larger cloud computing environments.
- Limited security : VLANs do not provide complete security and can be compromised by malicious actors who are able to gain access to the network.
- Limited interoperability : VLANs may not be fully compatible with all types of network devices and protocols, which can limit their usefulness in cloud computing environments.
- Limited mobility : VLANs may not support the movement of devices or users between different network segments, which can limit their usefulness in mobile or remote cloud computing environments.
- Cost: Implementing and maintaining VLANs can be costly, especially if specialized hardware or software is required.
- Limited visibility: VLANs can make it more difficult to monitor and troubleshoot network issues, as traffic is isolated in different segments.
Real-Time Applications of VLAN
Virtual LANs (VLANs) are widely used in cloud computing environments to improve network performance and security. Here are a few examples of real-time applications of VLANs:
- Voice over IP (VoIP) : VLANs can be used to isolate voice traffic from data traffic, which improves the quality of VoIP calls and reduces the risk of network congestion.
- Video Conferencing : VLANs can be used to prioritize video traffic and ensure that it receives the bandwidth and resources it needs for high-quality video conferencing.
- Remote Access : VLANs can be used to provide secure remote access to cloud-based applications and resources, by isolating remote users from the rest of the network.
- Cloud Backup and Recovery : VLANs can be used to isolate backup and recovery traffic, which reduces the risk of network congestion and improves the performance of backup and recovery operations.
- Gaming : VLANs can be used to prioritize gaming traffic, which ensures that gamers receive the bandwidth and resources they need for a smooth gaming experience.
- IoT : VLANs can be used to isolate Internet of Things (IoT) devices from the rest of the network, which improves security and reduces the risk of network congestion.
Please Login to comment...
Similar reads.

Improve your Coding Skills with Practice
What kind of Experience do you want to share?
Networking | Cloud | DevOps | IaC
IEEE 802.1X Authentication and Dynamic VLAN Assignment with NPS Radius Server
IEEE 802.1X Authentication and Dynamic VLAN Assignment with NPS Radius Server is an important element to networking in the real world. User location cannot be predicted as they may be at and out of a desk and up and about should they need to do so. Tying them to a local VLAN may only be helpful if they are bound to desks in those locations, although the most ideal outcome, it is not the most practical.
It is only wise to incorporate IEEE 802.1X Authentication and Dynamic VLAN Assignment with NPS Radius Server in areas where you expect different teams to come to. Meeting rooms could for a moment have the accounting group or the development group meeting there and based on the intelligent and dynamic vlan assignmnet with 802.1x authentication, users port-access are defined their appropriate vlans for their respective access to resources on the network.
How to Provision 802.1 X Authentication Step By Step With Dynamic VLAN Assignment With Windows Radius Server For 802.1x Clients.
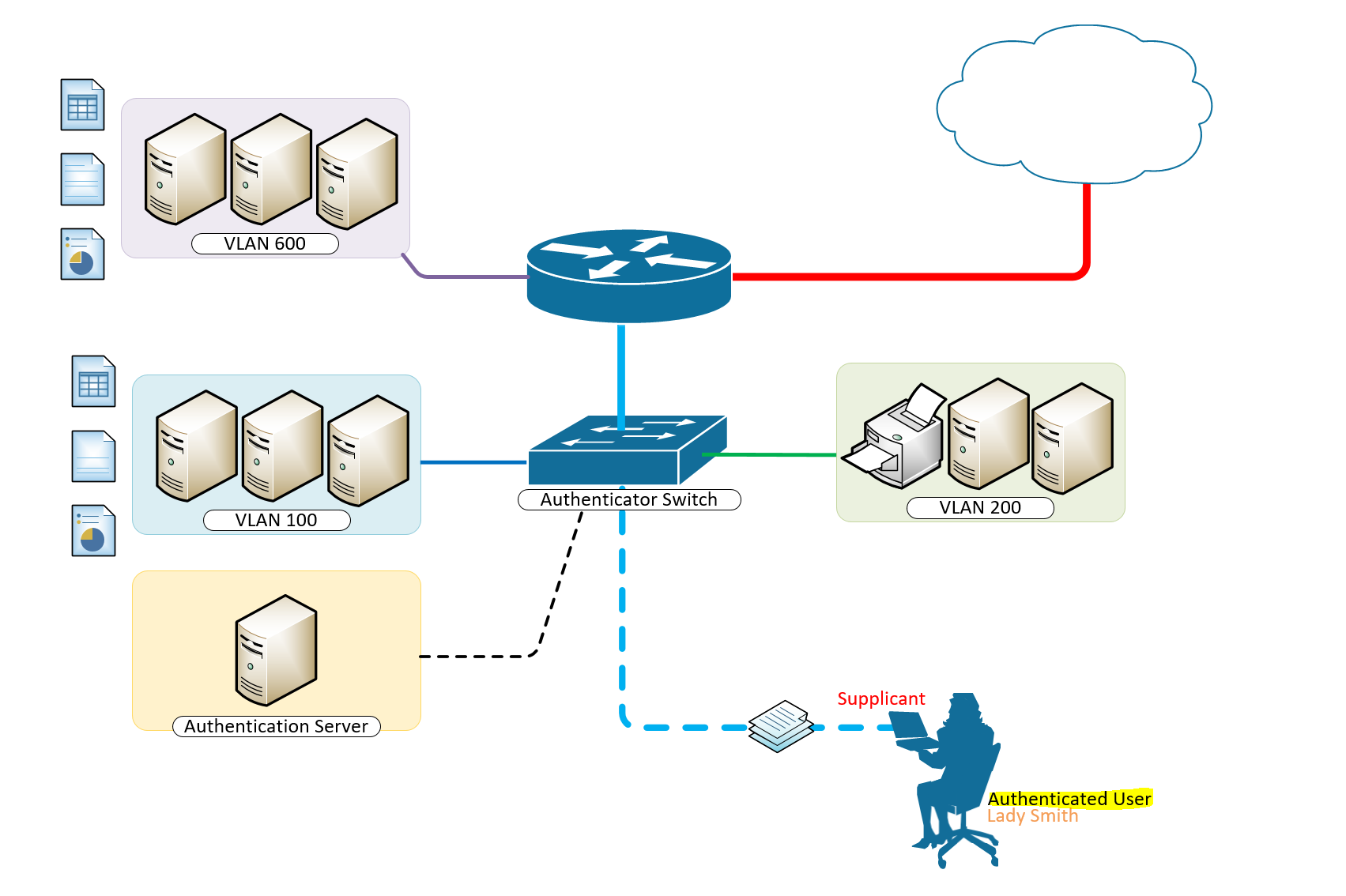
A typical configuration for a system under IEEE 802.1x Authentication control is shown in the following figure.
In this scenario, “Lady Smith” wishes to use services offered by servers on the LAN behind the switch. There are multiple VLANs with resources available based on user vlan membership. Her laptop computer is connected to a port on the Aruba 2920 Edge Switch that has 802.1x port authentication control enabled.
The laptop computer must therefore act in a supplicant role. Message exchanges take place between the supplicant and the authenticator which is the Aruba 2920 Switch, and the authenticator passes the supplicant’s credentials which is her (Windows Active Directory User Account Credentials) to the authentication server for verification. The NPS Server which is the authentication server then informs the authenticator whether or not the authentication attempt succeeded, at which point “Lady Smith” is either granted or denied access to the LAN behind the switch.
Setup Structure for IEEE 802.1X Authentication and Dynamic VLAN Assignment with NPS Radius Server
- Supplicant: Laptop running Microsoft Windows 10 or Windows 7
- Authenticator: HP Aruba 2920 Edge Switch
- Authentication Server: Microsoft NPS (Network Policy Server) running on Windows Server 2012 R2.
- User Database : Active Directory
For Windows Infrastructure
Create NPS Server – Add Role on Windows Server 2012 R2
- Create DHCP Scopes for VLANS
Create RADIUS Client on NAC using Network Policy Server
- Create Network Policies
- Configure a Network Policy for VLANs
- Start Wired Auto-Config Service
- Enable Network Authentication
Create the DHCP Scopes for VLAN100 and VLAN200 Groups
- Development Group Scope – VLAN 100
SVI: ip address 172.16.80.254 255.255.255.0 Scope Subnet: 172.16.80.1/24
- Accounting Group Scope – VLAN 200
SVI:ip address 172.16.70.254 255.255.255.0 Scope Subnet: 172.16.70.0/24
Secret Key: secret12
Add Edge Switch Management IP as the RADIUS Client
The Shared Secret Key: secret12 will be used in the Switch Configuration.
Create Network Policy Settings for Accounting Group for VLAN 200
Configuration Example
Here’s an example of how you might consider when configuring Microsoft NPS Server to assign users to a VLAN based on their user group, using NPS for the authentication and authorization of users. This configuration has worked flawlessly on the HP Aruba 2920 Switch. The key to getting this to work is the use of a RADIUS element called: ‘Tunnel-PVT-Group-ID’. This is a RADIUS attribute that may be passed back to the authenticator (i.e. the Aruba 2920 Switch) by the authentication server (i.e. Microsoft NPS Server) when a successful authentication has been achieved. There are a few other elements which need to accompany it, but this is the key element, as it specifies the VLAN number that the user should be assigned to.
The other elements that need to be returned by the NPS Server are as follows:
- Tunnel-PVT-Group-ID: 200
- Service-Type: Framed
- Tunnel-Type: VLAN
- Tunnel-Medium-Type: 802
For Client Infrastructure
On the Supplicant, Windows 7 or 10 configure the following steps on the Ethernet Adapter to enable IEEE 802.1X Authentication
For Network Infrastructure
Connect Server Infrastructure to VLAN 400
Create VLAN for Accounting Group
Create VLAN for Development Group
Create AAA Configuration on Switch for Radius Authentication
Download the Switch Configuration:
Test the IEEE 802.1X Authentication and Dynamic VLAN Assignment with NPS Radius Server
Verify Port-Access with the following user groups – VLAN 100 and VLAN 200
Think of what other clever things you can do from the information below;
Breakdown of Commands for RADIUS Authentication
Verification Commands
Thanks for reading. Please share your thoughts in the comment box below;
Published in Configuring , Design , Installing and Configuring , Networking , Security and Switching
- 802.1 x authentication step by step aruba
- 802.1 x authentication step by step cisco
- 802.1 x wireless authentication step by step
- 802.1x authentication process
- 802.1x authentication windows 10
- 802.1x authentication windows server 2012
- 802.1x certificate authentication
- assignment wlc
- cisco dot1x
- cisco ise dynamic vlan
- cisco ise dynamic vlan assignment wlc
- cisco wireless radius attributes
- configuration example
- dynamic vlan assignment cisco 2960 dynamic vlan configuration in packet tracer
- dynamic vlan assignment with windows radius server
- dynamic vlan cisco
- dynamic vlan ruckus
- meraki dynamic vlan assignment
- nps mac authentication wired
- nps policy for mac-based authentication
- radius multiple vlans
- vlan radius server
- vlan steering
- vmps server
- Help center
- Chinese (traditional)
Learn more
- Case Study
- Knowledge Center
- Glossary
Product Updates (120)
Getting Started (118)
News & Announcements (37)
Self Service (10)
Troubleshooting Guide (6)
Client Reviews (5)
Configuration Guide (5)
Product Testing (4)
Installation Guide (3)
Hear It from Experts (1)
Optics and Transceivers (97)
Switches (97)
Networking Devices (62)
Network Cabling and Wiring (59)
Optical Networking (18)
Networking (84)
Fiber Optic Communication (53)
Data Center (29)
General (26)
Wireless and Mobility (8)
Business Type (6)
Routing and Switching (5)
United Kingdom (1)
- Product Updates
- Networking Devices
- Case Study
- Knowledge Center

A Comprehensive Comparison of VLAN vs SVI
Network architecture is a critical backbone for any modern business or complex IT environment. As networks grow in complexity and size, understanding the various components and technologies that make up these networks becomes crucial. Among these components, VLANs (Virtual Local Area Networks) and SVIs (Switched Virtual Interfaces) play pivotal roles. Although both are integral to network segmentation and traffic management, their functions, applications, and benefits are distinct. This article delves into VLAN vs SVI, elucidating their differences and benefits.
What is VLAN (Virtual Local Area Network)?
A VLAN is a network protocol designed to create separate, smaller network segments within a larger physical network, regardless of the physical location of the users or devices. VLANs enhance network security, efficiency, and performance by segmenting networks into distinct broadcast domains. This allows network administrators to control traffic, restrict access between network segments, and apply different policies based on requirements. VLANs operate at OSI layer 2 (Data Link layer).

Benefits of Using VLAN
Enhanced Network Security: By segregating networks into different segments, sensitive data can be isolated and protected.
Improved Network Performance: VLANs reduce broadcast traffic, which, in turn, lessens the load on network resources.
Flexibility and Scalability: Network administrators can easily create, modify, or delete VLANs without the need for extensive changes to the physical network.
What Is SVI in Networking?
SVI, an abbreviation for Switched Virtual Interface, is a logical interface found on a layer 3 switch. Its purpose is to connect a VLAN to the routing engine of the switch. By doing so, SVI enables the routing of traffic between VLANs by acting as the default gateway for each VLAN. In addition, SVI provides layer 3 IP connectivity to the switch and supports both bridging and routing protocols.
Unlike a physical interface on a router, SVI allows multiple VLANs to utilize the same physical interface on the switch. However, each VLAN has its own distinct logical interface and broadcast domain, differentiating them from one another.

To create an SVI, the first step is to establish a layer 2 VLAN on the switch. Subsequently, an IP address is assigned to the corresponding layer 3 interface (SVI). For instance, if VLAN 10 and VLAN 20 exist on the switch, SVI 10 and SVI 20 can be created with separate IP addresses, enabling routing between them. Additionally, an IP address can be assigned to the default SVI (VLAN 1) to facilitate remote management of the switch.

Benefits of Using SVI
Enhanced speed and efficiency are achieved through hardware-based switching and routing, surpassing the limitations of the router-on-a-stick method.
Streamlined inter-VLAN routing that eliminates the necessity for external links or devices.
Improved network performance with reduced latency compared to the utilization of a router, offering higher levels of efficiency.
Comparison Table: VLAN vs SVI
The following table provides an overview of the variances between them:
Application of VLAN in PoE switches
In networks using PoE switches, VLAN technology can help administrators effectively divide the network, improve security, and improve performance. For those in need of robust and versatile PoE switches to support complex VLAN configurations and high-power devices, the PoE+ and PoE++ switches from FS are highly recommended. These switches offer a seamless experience for deploying IP cameras, VoIP phones, and other PoE-capable devices across multiple VLANs, ensuring efficient traffic management and enhanced security. Additionally, administrators can benefit from features such as QoS (Quality of Service), which prioritizes critical traffic, and advanced security protocols to protect the network. For example, an administrator might configure different VLANs for different types of devices connected to the same PoE switch. IP cameras may be in one VLAN and VoIP phone in another to ensure traffic isolation, thereby increasing network security and reducing the impact of broadcast traffic. With FS PoE switches , integrating advanced VLAN functionalities into your network has never been easier, making them an ideal choice for modern, secure, and efficient networks.
In the constantly evolving world of networking technology, mastering the core concepts and differences of VLAN vs SVI can help organizations and IT professionals build and manage complex networks that stand the test of time, scalability, and security challenges.
- # PoE Switch
- # Networking Devices
- # PoE Network
You might be interested in

Email Address
Please enter your email address.
Please make sure you agree to our Privacy Policy and Terms of Use.

Cloud-based Networks Grow with Your Business

Anchor Your Hybrid Cloud Networking Strategy
- Network Cabling and Wiring
- Buying Guide
- Fiber Optic Communication
- Optics and Transceivers
- Data Center
- Ethernet Patch Cords
- Business Type
- Routing and Switching
- Optical Networking
- Best Practices
- 10G Network
- Home Networking

Fiber Optic Cable Types: Single Mode vs Multimode Fiber Cable
May 10, 2022

Layer 2 vs Layer 3 Switch: Which One Do You Need?
Oct 6, 2021

Multimode Fiber Types: OM1 vs OM2 vs OM3 vs OM4 vs OM5
Sep 22, 2021

Running 10GBASE-T Over Cat6 vs Cat6a vs Cat7 Cabling?
Mar 18, 2024

PoE vs PoE+ vs PoE++ Switch: How to Choose?
Mar 16, 2023
- Skip to content
- Skip to search
- Skip to footer
Configure a RADIUS Server and WLC for Dynamic VLAN Assignment
Available languages, download options.
- PDF (906.6 KB) View with Adobe Reader on a variety of devices
Bias-Free Language
The documentation set for this product strives to use bias-free language. For the purposes of this documentation set, bias-free is defined as language that does not imply discrimination based on age, disability, gender, racial identity, ethnic identity, sexual orientation, socioeconomic status, and intersectionality. Exceptions may be present in the documentation due to language that is hardcoded in the user interfaces of the product software, language used based on RFP documentation, or language that is used by a referenced third-party product. Learn more about how Cisco is using Inclusive Language.
Introduction
This document introduces the concept of dynamic VLAN assignment. The document describes how to configure the wireless LAN controller (WLC) and a RADIUS server to assign wireless LAN (WLAN) clients into a specific VLAN dynamically.
Prerequisites
Requirements.
Ensure that you meet these requirements before you attempt this configuration:
Have basic knowledge of the WLC and Lightweight Access Points (LAPs)
Have functional knowledge of the AAA server
Have thorough knowledge of wireless networks and wireless security issues
Have basic knowledge of Lightweight AP Protocol (LWAPP)
Components Used
The information in this document is based on these software and hardware versions:
Cisco 4400 WLC that runs firmware release 5.2
Cisco 1130 Series LAP
Cisco 802.11a/b/g Wireless Client Adapter that runs firmware release 4.4
Cisco Aironet Desktop Utility (ADU) that runs version 4.4
CiscoSecure Access Control Server (ACS) that runs version 4.1
Cisco 2950 series switch
The information in this document was created from the devices in a specific lab environment. All of the devices used in this document started with a cleared (default) configuration. If your network is live, make sure that you understand the potential impact of any command.
Conventions
Refer to Cisco Technical Tips Conventions for more information on document conventions.
Dynamic VLAN Assignment with RADIUS Server
In most WLAN systems, each WLAN has a static policy that applies to all clients associated with a Service Set Identifier (SSID), or WLAN in the controller terminology. Although powerful, this method has limitations because it requires clients to associate with different SSIDs in order to inherit different QoS and security policies.
However, the Cisco WLAN solution supports identity networking. This allows the network to advertise a single SSID, but allows specific users to inherit different QoS or security policies based on the user credential.
Dynamic VLAN assignment is one such feature that places a wireless user into a specific VLAN based on the credentials supplied by the user. This task of assigning users to a specific VLAN is handled by a RADIUS authentication server, such as CiscoSecure ACS. This can be used, for example, to allow the wireless host to remain on the same VLAN as it moves within a campus network.
Therefore, when a client attempts to associate to a LAP registered with a controller, the LAP passes the credentials of the user to the RADIUS server for validation. Once the authentication is successful, the RADIUS server passes certain Internet Engineering Task Force (IETF) attributes to the user. These RADIUS attributes decide the VLAN ID that should be assigned to the wireless client. The SSID (WLAN, in terms of WLC) of the client does not matter because the user is always assigned to this predetermined VLAN ID.
The RADIUS user attributes used for the VLAN ID assignment are:
IETF 64 (Tunnel Type)—Set this to VLAN.
IETF 65 (Tunnel Medium Type)—Set this to 802
IETF 81 (Tunnel Private Group ID)—Set this to VLAN ID.
In this section, you are presented with the information to configure the features described in this document.
Network Diagram
This document uses this network setup:
These are the configuration details of the components used in this diagram:
The IP address of the ACS (RADIUS) server is 172.16.1.1.
The Management Interface address of the WLC is 172.16.1.30.
The AP-Manager Interface address of the WLC is 172.16.1.31.
The DHCP server address 172.16.1.1 is used to assign IP addresses to the LWAPP. The internal DHCP server on the controller is used to assign the IP address to wireless clients.
VLAN10 and VLAN11 are used throughout this configuration. The user1 is configured to be placed into the VLAN10 and user2 is configured to be placed into VLAN11 by the RADIUS server.
Note: This document only shows all the configuration information related to user1. Complete the same procedure explained in this document for the user2.
This document uses 802.1x with LEAP as the security mechanism.
Note: Cisco recommends that you use advanced authentication methods, such as EAP-FAST and EAP-TLS authentication, in order to secure the WLAN. This document uses LEAP only for simplicity.
Configuration
Prior to the configuration, this document assumes that the LAP is already registered with the WLC. Refer to Wireless LAN Controller and Lightweight Access Point Basic Configuration Example for more information. Refer to Lightweight AP (LAP) Registration to a Wireless LAN Controller (WLC) for information about the registration procedure involved.
Configuration Steps
This configuration is separated into three categories:
RADIUS Server Configuration
Configure the switch for multiple vlans, wlc configuration, wireless client utility configuration.
This configuration requires these steps:
Configure the WLC as an AAA Client on the RADIUS Server
Configure the Users and the RADIUS (IETF) Attributes Used for Dynamic VLAN Assignment on the RADIUS Server
Configure the aaa client for the wlc on the radius server.
This procedure explains how to add the WLC as a AAA client on the RADIUS server so that the WLC can pass the user credentials to the RADIUS server.
Complete these steps:
From the ACS GUI, click Network Configuration .
Click the Add Entry section under the AAA Clients field.
Enter the AAA Client IP Address and Key.
The IP address should be the Management Interface IP address of the WLC.
Make sure that the key you enter is the same as the one configured on the WLC under the Security window. This is the secret key used for communication between the AAA client (WLC) and the RADIUS server.
Choose RADIUS (Cisco Airespace) from the Authenticate Using field for the authentication type.
This procedure explains how to configure the users in the RADIUS server and the RADIUS (IETF) attributes used to assign VLAN IDs to these users.
From the ACS GUI, click User Setup .
In the User Setup window, enter a username in the User field and click Add/Edit .
On the Edit page, enter the necessary user information as shown here:
In this diagram, notice that the password you provide under the User Setup section should be the same as the one provided at the client side during the user authentication.
Scroll down the Edit page and find the IETF RADIUS Attributes field.
In the IETF RADIUS Attributes field, check the check boxes next to the three Tunnel attributes and configure the attribute values as shown here:
Note: In the initial configuration of the ACS server, IETF RADIUS attributes might not be displayed.
Choose Interface Configuration > RADIUS (IETF) in order to enable IETF attributes in the user configuration window.
Then, check the check boxes for attributes 64, 65, and 81 in the User and Group columns.
Note: In order for the RADIUS server to dynamically assign the client to a specific VLAN, it is required that the VLAN-ID configured under the IETF 81 (Tunnel-Private-Group-ID) field of the RADIUS server exist on the WLC.
Check the Per User TACACS+/RADIUS attribute check box under Interface Configuration > Advanced Options in order to enable the RADIUS server for per user configurations.
Also, because LEAP is used as the Authentication protocol, ensure that LEAP is enabled in the System Configuration window of the RADIUS server as shown here:
Configure the ACS with Cisco Airespace VSA Attributes for Dynamic VLAN Assignment
In the latest ACS versions, you can also configure the Cisco Airespace [VSA (Vendor-Specific)] attribute to assign a successfully authenticated user with a VLAN interface name (not the VLAN ID) as per the user configuration on the ACS. In order to accomplish this, perform the steps in this section.
Note: This section uses ACS 4.1 version to configure the Cisco Airespace VSA attribute.
Configure the ACS Group with Cisco Airespace VSA Attribute Option
From the ACS 4.1 GUI, click Interface Configuration from the navigation bar. Then, select RADIUS (Cisco Airespace) from the Interface Configuration page in order to configure the Cisco Airespace attribute option.
From the RADIUS (Cisco Airespace) window, check the User check box (Group check box if needed) next to Aire-Interface-Name in order to display it on the User Edit page. Then, click Submit .
Go to the user1's Edit page.
From the User Edit page, scroll down to the Cisco Airespace RADIUS Attributes section. Check the check box next to the Aire-Interface-Name attribute and specify the name of the dynamic interface to be assigned upon successful user authentication.
This example assigns the user to admin VLAN.
Click Submit .
In order to allow multiple VLANs through the switch, you need to issue these commands to configure the switch port connected to the controller:
Switch(config-if)# switchport mode trunk
Switch(config-if)# switchport trunk encapsulation dot1q
Note: By default, most of the switches allow all VLANs created on that switch via the trunk port.
These commands vary for a Catalyst operating system (CatOS) switch.
If a wired network is connected to the switch, then this same configuration can be applied to the switch port that connects to the wired network. This enables the communication between the same VLANs in the wired and wireless network.
Note: This document does not discuss inter-VLAN communication. This is beyond the scope of this document. You must understand that for inter-VLAN routing, a Layer 3 switch or an external router with proper VLAN and trunking configurations is needed. There are several documents that explain inter-VLAN routing configuration.
Configure the WLC with the Details of the Authentication Server
Configure the dynamic interfaces (vlans), configure the wlans (ssid).
It is necessary to configure the WLC so it can communicate with the RADIUS server to authenticate the clients, and also for any other transactions.
From the controller GUI, click Security .
Enter the IP address of the RADIUS server and the Shared Secret key used between the RADIUS server and the WLC.
This Shared Secret key should be the same as the one configured in the RADIUS server under Network Configuration > AAA Clients > Add Entry. Here is an example window from the WLC:
This procedure explains how to configure dynamic interfaces on the WLC. As explained earlier in this document, the VLAN ID specified under the Tunnel-Private-Group ID attribute of the RADIUS server must also exist in the WLC.
In the example, the user1 is specified with the Tunnel-Private-Group ID of 10 (VLAN =10) on the RADIUS server. See the IETF RADIUS Attributes section of the user1 User Setup window.
You can see the same dynamic interface (VLAN=10) configured in the WLC in this example. From the controller GUI, under the Controller > Interfaces window, the dynamic interface is configured.
Click Apply on this window.
This takes you to the Edit window of this dynamic interface (VLAN 10 here).
Enter the IP Address and default Gateway of this dynamic interface.
Note: Because this document uses an internal DHCP server on the controller, the primary DHCP server field of this window points to the Management Interface of the WLC itself. You can also use an external DHCP server, a router, or the RADIUS server itself as a DHCP server to the wireless clients. In such cases, the primary DHCP server field points to the IP address of that device used as the DHCP server. Refer to your DHCP server documentation for more information.
Click Apply .
Now you are configured with a dynamic interface in your WLC. Similarly, you can configure several dynamic interfaces in your WLC. However, remember that the same VLAN ID must also exist in the RADIUS server for that particular VLAN to be assigned to the client.
This procedure explains how to configure the WLANs in the WLC.
From the controller GUI, choose WLANs > New in order to create a new WLAN.
The New WLANs window is displayed.
Enter the WLAN ID and WLAN SSID information.
You can enter any name to be the WLAN SSID. This example uses VLAN10 as the WLAN SSID.
Click Apply in order to go to the Edit window of the WLAN SSID10.
Normally, in a wireless LAN controller, each WLAN is mapped to a specific VLAN (SSID) so that a particular user that belongs to that WLAN is put into the specific VLAN mapped. This mapping is normally done under the Interface Name field of the WLAN SSID window.
In the example provided, it is the job of the RADIUS server to assign a wireless client to a specific VLAN upon successful authentication. The WLANs need not be mapped to a specific dynamic interface on the WLC. Or, even though the WLAN to dynamic interface mapping is done on the WLC, the RADIUS server overrides this mapping and assigns the user that comes through that WLAN to the VLAN specified under the user Tunnel-Group-Private-ID field in the RADIUS server.
Check the Allow AAA Override check box in order to override the WLC configurations by the RADIUS server.
Enable the Allow AAA Override in the controller for each WLAN (SSID) configured.
When AAA Override is enabled, and a client has AAA and controller WLAN authentication parameters that conflict, client authentication is performed by the AAA (RADIUS) server. As part of this authentication, the operating system moves clients to a VLAN returned by the AAA server. This is predefined in the controller interface configuration.
For instance, if the corporate WLAN primarily uses a Management Interface assigned to VLAN 2, and if the AAA Override returns a redirect to VLAN 100, the operating system redirects all client transmissions to VLAN 100 even if the physical port to which VLAN 100 is assigned. When AAA Override is disabled, all client authentication defaults to the controller authentication parameter settings, and authentication is only performed by the AAA server if the controller WLAN does not contain any client-specific authentication parameters.
This document uses ADU as the client utility for the configuration of the user profiles. This configuration also uses LEAP as the authentication protocol. Configure the ADU as shown in the example in this section.
From the ADU Menu bar, choose Profile Management > New in order to create a new profile.
The example client is configured to be a part of SSID VLAN10. These diagrams show how to configure a user profile on a client:
Activate the user profile you have configured in the ADU. Based on the configuration, you are prompted for a username and password. You can also instruct the ADU to use the Windows username and password for authentication. There are a number of options from which the client can receive authentication. You can configure these options under the Security > Configure tab of the user profile you have created.
In the previous example, notice that user1 is assigned to the VLAN10 as specified in the RADIUS server.
This example uses this username and password from the client side to receive authentication and to be assigned to a VLAN by the RADIUS server:
User Name = user1
Password = user1
This example shows how the SSID VLAN10 is prompted for the username and password. The username and password are entered in this example:
Once the authentication and the corresponding validation is successful, you receive success as the status message.
Then, you need to verify that your client is assigned to the proper VLAN as per the RADIUS attributes sent. Complete these steps in order to accomplish this:
From the controller GUI, choose Wireless > AP .
Click Clients , which appears on the left corner of the Access Points (APs) window.
The client statistics are displayed.
Click Details in order to identify the complete details of the client, such as IP address, the VLAN to which it is assigned, and so forth.
This example displays these details of the client, user1:
From this window, you can observe that this client is assigned to VLAN10 as per the RADIUS attributes configured on the RADIUS server.
Note: If the dynamic VLAN assignment is based on the Cisco Airespace VSA Attribute setting, the Interface name will display it as admin as per this example on the client details page.
Use this section to confirm that your configuration works properly.
debug aaa events enable —This command can be used to ensure successful transfer of the RADIUS attributes to the client via the controller. This portion of the debug output ensures a successful transmission of RADIUS attributes:
Fri Jan 20 02:25:08 2006: 00:40:96:ac:e6:57 processing avps[0]: attribute 64, vendorId 0, valueLen 4 Fri Jan 20 02:25:08 2006: 00:40:96:ac:e6:57 processing avps[1]: attribute 65, vendorId 0, valueLen 4 Fri Jan 20 02:25:08 2006: 00:40:96:ac:e6:57 processing avps[2]: attribute 81, vendorId 0, valueLen 3 Fri Jan 20 02:25:08 2006: 00:40:96:ac:e6:57 processing avps[3]: attribute 79, vendorId 0, valueLen 32 Fri Jan 20 02:25:08 2006: 00:40:96:ac:e6:57 Received EAP Attribute (code=2, length=32,id=0) for mobile 00:40:96:ac:e6:57 Fri Jan 20 02:25:08 2006: 00000000: 02 00 00 20 11 01 00 18 4a 27 65 69 6d e4 05 f5 ........J'eim...00000010: d0 98 0c cb 1a 0c 8a 3c ........44 a9 da 6c 36 94 0a f3 <D..l6... Fri Jan 20 02:25:08 2006: 00:40:96:ac:e6:57 processing avps[4]: attribute 1, vendorId 9, valueLen 16 Fri Jan 20 02:25:08 2006: 00:40:96:ac:e6:57 processing avps[5]: attribute 25, vendorId 0, valueLen 28 Fri Jan 20 02:25:08 2006: 00:40:96:ac:e6:57 processing avps[6]: attribute 80, vendorId 0, valueLen 16 Fri Jan 20 02:25:08 2006: 00:40:96:ac:e6:57 Tunnel-Type 16777229 should be 13 for STA 00:40:96:ac:e6:57 Fri Jan 20 02:25:08 2006: 00:40:96:ac:e6:57 Tunnel-Medium-Type 16777222 should be 6 for STA 00:40:96:ac:e6:57 Fri Jan 20 02:30:00 2006: 00:40:96:ac:e6:57 Station 00:40:96:ac:e6:57 setting dot1x reauth timeout = 1800
These commands can also be useful:
debug dot1x aaa enable
debug aaa packets enable
Troubleshoot
There is currently no specific troubleshooting information available for this configuration.
Note: Dynamic VLAN assignment does not work for web authentication from a WLC.
Related Information
- EAP Authentication with RADIUS Server
- Cisco Wireless LAN Controller Configuration Guide, Release 4.0
- Technical Support & Documentation - Cisco Systems
Revision History
Was this document helpful.

Contact Cisco
- (Requires a Cisco Service Contract )
This Document Applies to These Products
- Aironet Wireless LAN Client Adapters
You are using an outdated browser. Please upgrade your browser to improve your experience.
You can use esxcli network vswitch standard portgroup set to manage VLANs.
VLANs allow you to further segment a single physical LAN segment so that groups of ports are isolated as if they were on physically different segments. The standard is IEEE 802.1Q.
A VLAN ID restricts port group traffic to a logical Ethernet segment within the physical network.
- Set the VLAN ID to 4095 to allow a port group to reach port groups located on other VLAN.
- Set the VLAN ID to 0 to disable the VLAN for this port group.
If you use VLAN IDs, you must change the port group labels and VLAN IDs together so that the labels properly represent connectivity. VLAN IDs are optional.
You can use the following commands for VLAN management.
- Allow port groups to reach port groups located on other VLANs. esxcli <conn_options> network vswitch standard portgroup set -p <pg_name> --vlan-id 4095 Run the command multiple times to allow all ports to reach port groups located on other VLANs.
- Disable VLAN for port group g42. esxcli <conn_options> network vswitch standard portgroup set --vlan-id 0 -p g42
Run esxcli network vswitch standard portgroup list to list all port groups and associated VLAN IDs.
Meraki Community
- Community Platform Help
- Contact Community Team
- Meraki Documentation
- Meraki DevNet Developer Hub
- Meraki System Status
- Technical Forums
Dynamic VLAN Assignment on MR
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Printer Friendly Page
- Mark as New
- Report Inappropriate Content
Solved! Go to solution.

View solution in original post
- All forum topics
- Previous Topic

- New May 13: Join us in some fun wordplay for National Limerick Day, hooray!
- May 7: Community Platform Update: Reducing space within content
- May 2: Recognizing the April 2024 Members of the Month
- Installation 207
- Interference 77
- RF Spectrum 96
- Community guidelines
- Cisco privacy
- Khoros privacy
- Terms of service
Understanding VLAN Assignments
A client is assigned to a VLAN by one of several methods. There is an order of precedence by which VLANs are assigned. The assignment of VLANs are (from lowest to highest precedence):
Tunnel-Type="VLAN"(13)
Tunnel-Medium-Type="IEEE-802" (6)
Tunnel-Private-Group-Id="101"
Aruba -User-VLAN
Aruba -Named-User-VLAN
How a VLAN Obtains an IP Address
A VLAN on the controller obtains its IP address in one of the following ways:
Assigning a Static Address to a VLAN
You can manually assign a static IP address to a VLAN on the controller . At least one VLAN on the controller must be assigned a static IP address.
In the WebUI
(host) (config) # interface vlan < id>
ip address < address> < netmask>
Configuring a VLAN to Receive a Dynamic Address
In a branch office, you can connect a controller to an uplink switch or server that dynamically assigns IP addresses to connected devices. For example, the controller can be connected to a DSL or cable modem, or a broadband remote access server (BRAS). shows a branch office where a controller connects to a cable modem. VLAN 1 has a static IP address, while VLAN 2 has a dynamic IP address assigned via DHCP or PPPoE from the uplink device.
Figure 1 IP Address Assignment to VLAN via DHCP or PPPoE

Configuring Multiple Wired Uplink Interfaces (Active-Standby)
You can assign up to four VLAN interfaces to operate in active-standby topology. An active-standby topology provides redundancy so that when an active interface fails, the user traffic can failover to the standby interface.
To allow the controller to obtain a dynamic IP address for a VLAN, enable the DHCP or PPPoE client on the controller for the VLAN.
The following restrictions apply when enabling the DHCP or PPPoE client on the controller :
Enabling the DHCP Client
The DHCP server assigns an IP address for a specified amount of time called a lease. The controller automatically renews the lease before it expires. When you shut down the VLAN, the DHCP lease is released.
Figure 2 Assigning VLAN uplink priority—Active-Standby configuration

In this example, the DHCP client has the client ID name myclient and the interface VLAN 62 has an uplink priority of 2.
interface vlan 62
uplink wired vlan 62 priority 3
interface vlan 62 ip address dhcp-client client-id myclient
Enabling the PPPoE Client
To authenticate to the BRAS and request a dynamic IP address, the controller must have the following configured:
When you shut down the VLAN, the PPPoE session terminates.
In this example, a PPoE service name, username and password are assigned. The interface VLAN 14 has an uplink priority of 3.
(host) (config) # interface vlan 14
ip address pppoe
(host) (config) # interface vlan 14 ip pppoe-service-name < service_name >
(host) (config) # interface vlan 14 ip pppoe-username < username >
(host) (config) #(host) (config) # interface vlan 14 ip pppoe-password *****
(host) (config) # uplink wired vlan 14 priority 3
Default Gateway from DHCP/PPPoE
You can specify that the router IP address obtained from the DHCP or PPPoE server be used as the default gateway for the controller .
(host) (config) # ip default-gateway import
Configuring DNS/WINS Server from DHPC/PPPoE
The DHCP or PPPoE server can also provide the IP address of a DNS server or NetBIOS name server, which can be passed to wireless clients through the controller ’s internal DHCP server.
For example, the following configures the DHCP server on the controller to assign addresses to authenticated employees; the IP address of the DNS server obtained by the controller via DHCP/PPPoE is provided to clients along with their IP address.
(host) (config) # ip dhcp pool employee-pool
d>efault-router 10.1.1.254
d>ns-server import
netbios-name-server import
network 10.1.1.0 255.255.255.0
Configuring Source NAT to Dynamic VLAN Address
When a VLAN interface obtains an IP address through DHCP or PPPoE, a NAT pool (dynamic-srcnat) and a session ACL (dynamic-session-acl) are automatically created which reference the dynamically-assigned IP addresses. This allows you to configure policies that map private local addresses to the public address(es) provided to the DHCP or PPPoE client. Whenever the IP address on the VLAN changes, the dynamic NAT pool address also changes to match the new address.
For example, the following rules for a guest policy deny traffic to internal network addresses. Traffic to other (external) destinations are source NATed to the IP address of the DHCP/PPPoE client on the controller .
(host) (config) # ip access-list session guest
any network 10.1.0.0 255.255.0.0 any deny
any any any src-nat pool dynamic-srcnat
Configuring Source NAT for VLAN Interfaces
The example configuration in the previous section illustrates how to configure source NAT using a policy that is applied to a user role. You can also enable source NAT for a VLAN interface to cause NAT to be performed on the source address for all traffic that exits the VLAN.
Packets that exit the VLAN are given a source IP address of the “outside” interface, which is determined by the following:
Example Configuration
In the following example, the controller operates within an enterprise network. VLAN 1 is the outside VLAN. Traffic from VLAN 6 is source NATed using the IP address of the controller . In this example, the IP address assigned to VLAN 1 is used as the controller ’s IP address; thus traffic from VLAN 6 would be source NATed to 66.1.131.5.
Figure 3 Example: Source NAT using Controller IP Address

(host) (config) # interface vlan 1
ip address 66.1.131.5 255.255.255.0
(host) (config) # interface vlan 6
(host) (config) # ip address 192.168.2.1 255.255.255.0
ip nat inside
ip default-gateway 66.1.131.1
Inter-VLAN Routing
On the controller , you can map a VLAN to a layer-3 subnetwork by assigning a static IP address and netmask or by configuring a DHCP or PPPoE server to provide a dynamic IP address and netmask to the VLAN interface. The controller , acting as a layer-3 switch, routes traffic between VLANs that are mapped to IP subnetworks; this forwarding is enabled by default.
In Figure 4 , VLAN 200 and VLAN 300 are assigned the IP addresses 2.1.1.1/24 and 3.1.1.1/24, respectively. Client A in VLAN 200 is able to access server B in VLAN 300 and vice versa, provided that there is no firewall rule configured on the controller to prevent the flow of traffic between the VLANs.
Figure 4 Default Inter-VLAN Routing

You can optionally disable layer-3 traffic forwarding to or from a specified VLAN. When you disable layer-3 forwarding on a VLAN, the following restrictions apply:
To disable layer-3 forwarding for a VLAN configured on the controller :
Using the WebUI to restrict VLAN routing
Using the cli.
interface vlan <id>
ip address {<ipaddr> <netmask>|dhcp-client|pppoe}
no ip routing
Sample configuration of Windows virtual machine VLAN Tagging (VGT Mode) in ESX
Article id: 324529, updated on:, issue/introduction, environment.
- 802.1Q VLAN trunking driver is required inside the virtual machine
- 64bit Windows guest operating system automatically loads the 802.1q E1000 driver
- 32bit guest Operating Systems require manual configuration of the VMX file to point to the E1000 driver
- Physical switch is set to trunk mode by using VLAN ID 4095
- Windows: Only 64-bit Windows ships with the E1000 Drivers
Configuration of VirtualSwitch (vSwitch)
To set a standard vSwitch portgroup to trunk mode:
- Edit host networking via the Virtual infrastructure Client.
- Navigate to Host > Configuration > Networking > vSwitch > Properties .
- Click Ports > Portgroup > Edit .
- Click the General tab.
- Set the VLAN ID to 4095. A VLAN ID of 4095 represents all trunked VLANs.
To set a distributed vSwitch portgroup to trunk mode:
- Navigate to Home > Inventory > Networking .
- Right-click on the dvPortGroup and select Edit Settings .
- Within that dvPortGroup, go to Policies > VLAN .
- Set VLAN type to VLAN Trunking and specify a range of VLANs or specificy a list of VLANs to be passed to the Virtual machines connected to this portgroup. Note: To improve security, virtual Distributed Switches allow you to specify a range or selection of VLANs to trunk rather than allowing all VLANS via VLAN 4095.
Configuration of Windows TCP/IP
- Download the e1000 NIC drivers from the Intel website into the 32-bit Windows virtual machine. Note: The preceding link was correct as of September 15, 2015. If you find the link is broken, provide feedback and a VMware employee will update the link.
- Power off the virtual machine.
- Configure the virtual machine to use the e1000 virtual NIC. Enter a new line (or replace the existing virtual NIC) in the .vmx file of the virtual machine: Ethernet n .virtualDev = "e1000" Replace n with the number of the Ethernet adapter. For example, the entry for the first Ethernet adapter that has number 0 is: Ethernet0.virtualDev = "e1000"
- Power on the virtual machine.
- Configure the e1000 network connection.
- Download ProWinx64 from Intel located here Network Adapter Driver for Windows Note : Intel has moved some drivers to historical status, if the above link does not have the correct driver, see this link for specific driver versions: http://www.intel.com/support/network/sb/CS-023752.htm?wapkw=e1g6032e Note : The preceding link was correct as of September 15, 2015. If you find the link is broken, provide feedback and a VMware employee will update the link.
- Run this command to extract the Intel drivers downloaded to the temp folder: Prowinx64.exe /s /e /f "C:\temp If 7zip is installed, run this as alternate command on Windows PowerShell Get-ChildItem "*.exe" | foreach { C:\Windows\System32\7z.exe e -y $_.fullname
- Right-click the network adapter and click Update Driver Software .
- Click Browse my computer for driver software .
- Click Let me pick from a list of device drivers on my computer .
- Click Have Disk .
- Click Browse .
- Browse to C:\temp\pro1000\winx64\ndis61\e1g6032e.inf .
- Click Next to install the driver.
- Repeat Steps 2-8 for each network adapter you have for the virtual machine.
- After all the adapters are updated, run the Intel setup program. You should now be able to install the advanced network services software with VLANs.
- You can also find the instructions in the manual/readme file for the driver.
- The Intel driver download contains ProWin64.exe . This is not a separate install.
- This process applies to the vmxnet3 driver as well. However to have multiple vlans you need to use multiple vmxnet3 NIC's.
Additional Information

Red Hat OpenShift 101 for OpenStack admins: Configuration

In the previous post , we oversaw the required Red Hat OpenShift Container Platform operators , their roles, and the format used to create the Red Hat OpenStack Services on OpenShift (RHOSO) control plane. In this article, let’s review the deployment process.
We’ll base our observations on the Development Preview 3 code from https://github.com/rh-osp-demo/dp-demo/ .
Let’s begin with the OpenStack Operator.
The OpenStack Operator
The OpenStack Operator consists of three parts (a CatalogSource , an OperatorGroup , and a Subscription ), each defining a different resource for managing Operators within an OpenShift/ Kubernetes cluster using the Operator Lifecycle Manager (OLM). The resources aim to set up an Operator for OpenStack, likely for managing OpenStack services within the cluster, are as follows:
These resources collectively set up an environment where the OpenStack Operator is available to be installed in the openstack-operators namespace. The CatalogSource provides the metadata about available operators, including the OpenStack Operator, sourced from a specified image. The OperatorGroup defines the scope within which the Operator can operate, and the Subscription triggers the installation and management of the OpenStack Operator according to the specified channel and source catalog.
Let’s focus on the CatalogSource part:
- name: openstack-operator-index - The name of the CatalogSource .
- namespace: openstack-operators - The namespace where the CatalogSource is created.
- sourceType: grpc - Indicates that the catalog source uses gRPC to serve the index of available operators.
- secrets: A list of secrets, in this case, osp-operators-secret , that might be used by the catalog source, potentially for accessing private repositories.
- gprcPodConfig : Contains configuration specific to the pod serving the gRPC requests.
- securityContextConfig: legacy - Specifies a security context configuration for the pod. The exact meaning of "legacy" can depend on the cluster configuration.
- image : The container image URL for the operator index image, which should be adjusted to match the environment. This image hosts metadata about the operators available for installation, including the OpenStack operator.
Network isolation
Now that the operator is installed, let’s prepare the networking for the control plane, then the data plane.
First, we’ll work with the NNCP file used to configure the data plane network, which will configure the topology for each data plane network. It looks like the following ( source file ):
This YAML file defines a NodeNetworkConfigurationPolicy for use with the NMState Operator in an OpenShift or Kubernetes environment. The policy specifies desired network configurations for nodes that match the defined nodeSelector. Here's a breakdown of the key components:
- apiVersion : Specifies the version of the NMState API used.
- kind : Identifies the resource type as NodeNetworkConfigurationPolicy , indicating that it's a policy for configuring network interfaces on nodes.
- name : The name of the policy, osp-enp1s0-worker-ocp4-worker1 , uniquely identifies it within the namespace.
- The first three are VLAN interfaces (type: vlan ) with the names enp1s0.20 , enp1s0.21 , and enp1s0.22 . Each interface is configured with a static IPv4 address ( 172.17.0.10/24 , 172.18.0.10/24 , 172.19.0.10/24 , respectively) and specifies that IPv6 is disabled. DHCP is also disabled for IPv4, and each interface is brought to the up state. They are all based on the parent interface enp1s0 and have VLAN IDs 20, 21, and 22, respectively.
- The fourth interface configuration applies to enp1s0 itself, setting it as an Ethernet interface (type: ethernet ) with a static IPv4 address 172.22.0.10/24 , DHCP disabled, and IPv6 disabled. The interface is also set to the up state with an MTU of 1500.
- nodeSelector : Specifies a node's criteria for the policy to be applied. In this case, it selects a node with the hostname ocp4-worker1.aio.example.com with a worker role.
This policy aims to configure multiple VLANs on a specific worker node's enp1s0 interface in an OpenShift or Kubernetes cluster, assigning static IPv4 addresses to each VLAN and the parent interface. It effectively segregates network traffic into different VLANs for purposes such as separating internal API traffic, storage traffic, and tenant traffic, while also configuring the parent interface for another network segment. The policy targets a specific node identified by its hostname and role, ensuring that these configurations are only applied to the intended node.
NetworkAttachDefinition (NAD) file
This YAML snippet defines a NetworkAttachmentDefinition object, part of the Kubernetes Network Custom Resource Definition (CRD) framework enabled by the Multus CNI plugin. This CRD is used to create multiple network interfaces in a Kubernetes pod. We will configure a NAD resource for each isolated network to attach a service pod to the network:
Let’s look at it:
- apiVersion: k8s.cni.cncf.io/v1 : Specifies the API version for the CRD. The k8s.cni.cncf.io/v1 indicates it's related to the CNI (Container Network Interface) plug-ins managed under the CNCF (Cloud Native Computing Foundation).
- kind: NetworkAttachmentDefinition : This tells Kubernetes that the defined resource is a NetworkAttachmentDefinition , which Multus uses to understand how to attach secondary networks to pods.
- name: ctlplane : The name of the NetworkAttachmentDefinition , which will be referenced by pods that want to use this network configuration.
- namespace: openstack : Specifies the namespace where this NetworkAttachmentDefinition is created, indicating it's intended for use by pods running in the openstack namespace.
- cniVersion : The version of the CNI specification to use.
- name : A name for this specific network configuration.
- type : Specifies the CNI plug-in to use, in this case, macvlan, which allows a Kubernetes pod to have a unique MAC address via a parent host interface.
- master : The master interface on the host that the macvlan interface will be created on top of. Here, it's ens224.4 , indicating a VLAN interface.
- type : The type of IPAM plugin to use, here whereabouts, which supports assigning IP addresses across multiple host nodes, avoiding IP address conflicts.
- range : The CIDR range from which IP addresses will be allocated.
- range_start , range_end: Define the start and end of the IP allocation pool within the specified range.
NMState resources
As described earlier, we must define IP address pools and L2 advertisements for the NMstate Operator. We must create an IPAddressPool resource to specify the range of IP addresses MetalLB can assign to services. Let’s have a look at our osp-ng-metal-lb-ip-address-pool . It contains several entries, one per IP address pool we define. Let’s just pick one to detail, the ctlplane one:
What do we have:
- apiVersion: metallb.io/v1beta1 : Specifies the API version of MetalLB being used.
- kind: IPAddressPool : Denotes the kind of Kubernetes resource. Here, IPAddressPool is a resource type provided by MetalLB for defining a pool of IP addresses.
- namespace: metallb-system : Specifies the namespace where the resource is located. MetalLB's resources typically reside in a dedicated namespace, metallb-system , isolated from other workloads.
- name: ctlplane : The name of the IPAddressPool resource. This name is used to identify the pool within the MetalLB configuration.
- addresses : Lists the IP address ranges that MetalLB can allocate to LoadBalancer services.
- - 172.22.0.80-172.22.0.90 : Defines a specific range of IP addresses (from 172.22.0.80 to 172.22.0.90 ) that MetalLB is allowed to assign. This range should be within the network subnet accessible by the cluster and not used by other devices or services to avoid IP conflicts.
As we are using MetalLB in Layer 2 mode, define an L2Advertisement resource. This tells MetalLB to advertise the IP addresses from your network's specified pool(s).
Let’s have a look at our osp-ng-metal-lb-l2-advertisement YAML file. It contains several entries, let’s just pick the one relevant to ctlplane :
Here's a succinct explanation of its contents:
- apiVersion: metallb.io/v1beta1 : Specifies the version of the MetalLB API being used.
- kind: L2Advertisement : Indicates the resource type, an L2Advertisement . This type controls how MetalLB advertises IP addresses to the local network.
- name: ctlplane : The name of the L2Advertisement resource.
- namespace: metallb-system : The namespace where the resource is deployed, typically MetalLB's dedicated namespace.
- ipAddressPools : Lists the names of the IP address pools that MetalLB should advertise. In this case, it references the IPAddressPool ctlplane , which we defined earlier.
- interfaces : Specifies which network interfaces MetalLB should use to advertise IP addresses. Here, it's configured to use the interface named enp1s0 .
This file tells MetalLB to advertise IP addresses from the ctlplane IP address pool over the enp1s0 network interface, making these IP addresses reachable on the local network through standard L2 networking mechanisms (ARP for IPv4, NDP for IPv6).
Let’s regroup what we have seen so far before we keep deploying our OpenStack Control Plane. When deploying MetalLB, you first apply the MetalLB resource to install MetalLB itself. Then, you define one or more IPAddressPool resources to specify the range of IPs MetalLB can manage. Finally, you use L2Advertisement resources to control the advertisement of these IPs on your network in Layer 2 mode.
MetalLB and NAD ( NetworkAttachmentDefinition ) serve different purposes. MetalLB is used to expose Kubernetes services of type LoadBalancer externally, allowing them to be accessible from outside the Kubernetes cluster. It's particularly useful in bare-metal environments where you don't have a cloud provider to provision external load balancers automatically.
NAD with Multus allows for attaching additional network interfaces to pods. This is useful in scenarios where pods need to communicate over different networks or require specific network configurations that the default Kubernetes network doesn't provide.
In essence, MetalLB simplifies external access to services, while Multus and NAD enhance pod networking capabilities within the cluster.
Data plane network configuration
The data plane network configuration file will configure the topology for each data plane network. Its YAML file contains a NetConfig header and then various network sub-sections, each defining a network to expose to the data plane network.
Here is an extract of this sample configuration file:
The YAML snippet defines a custom resource named NetConfig under the API group network.openstack.org/v1beta1 . This is not a standard Kubernetes API group, which implies it's part of a specific operator that extends OpenShift functionality related to integrating OpenStack networking capabilities with Kubernetes.
Here's a breakdown of what this YAML does:
- apiVersion: network.openstack.org/v1beta1 : Specifies the version of the API that the resource definition is compatible with. This is a custom resource definition (CRD) related to OpenStack networking under the v1beta1 version.
- kind: NetConfig : This indicates the type of the resource. The resource is used to configure how networking should be set up within for OpenStack-managed resources within Kubernetes.
- name: openstacknetconfig : The name of the NetConfig resource.
- namespace: openstack : This resource is in the openstack namespace.
- name: ctlPlane : Specifies the name of the network. It refers to a control plane network used for management and orchestration traffic in OpenStack.
- dnsDomain: ctlplane.aio.example.com : Defines the DNS domain used for the network.
- name: subnet1 : The name of the subnet.
- From 172.22.0.100 to 172.22.0.120
- From 172.22.0.150 to 172.22.0.200
- cidr: 172.22.0.0/24 : Typically, the CIDR should match the network of the allocation ranges and the gateway.
- gateway: 172.22.0.1 : Specifies the gateway for the subnet, which is the IP address used as the default route for traffic leaving the subnet.
From the internalaip section, we also see we can define VLAN IDs and exclusion ranges:
- excludeAddresses: IP range that the data plane should not use (these are the IP addresses used by the OCP cluster compute nodes (check the NNCP section above).
- vlan: VLAN ID used by the internalapi network. The lack of this entry in the ctlplane section denotes using a flat network.
OpenStack Control Plane deployment
Now that we have all of our networking defined, and provided we have our storage configured (the sample file we use relies on NFS, but we did not discuss it here), we can deploy the control plane.
The control plane deployment YAML defines the different OpenStack services that should be instantiated, and for each service its configuration. The file is quite long, so copying it here is difficult, but you can check a sample file here .
Here is, from the above sample, the list of defined Services and Key Configurations (note that some services are disabled):
- Utilizes MetalLB for LoadBalancer with an IP of 172.22.0.89.
- Configured to use an external DNS server at 192.168.123.100.
- Database instance named openstack , using a secret osp-secret .
- Cinder API exposed via MetalLB with an IP of 172.17.0.80.
- NFS backend for Cinder Volumes with specific NFS configurations.
- Storage backend set to use Cinder with specific Glance and Cinder configurations.
- Glance API exposed via MetalLB with an IP of 172.17.0.80.
- Uses NFS for storage with a request of 10G.
- Exposed via MetalLB with an IP of 172.17.0.80.
- Uses a database instance named openstack and a secret osp-secret .
- Enabled with storage requests set for the database and cell instances.
- Uses a secret osp-secret .
- Deployed with a single replica.
- Deployed with a single replica, using a secret osp-secret .
- API and Metadata services exposed via MetalLB with an IP of 172.17.0.80.
- API exposed via MetalLB with an IP of 172.17.0.80.
- Configuration for northbound and southbound DBs, as well as the OVN Controller.
- Exposed via MetalLB with specific IPs for RabbitMQ services.
- API and Engine exposed via MetalLB with an IP of 172.17.0.80.
- Disabled in this configuration.
- Ceilometer enabled, with configurations for autoscaling and metric storage.
In summary, MetalLB is extensively used to expose various OpenStack services externally via LoadBalancer type services, with annotations specifying address pools and IPs. Storage utilizes both Cinder (block storage) and NFS, with specific service configurations detailed for different services.
Each service utilizes a specific database instance and secrets for configuration and credentials management. Replicas and scaling define the number of replicas for certain services, indicating considerations for availability and scaling. And, finally, several services specify network attachments, indicating integration with specific network configurations for service communication.
We’ll complete the deployment process in the final part of this series: Red Hat OpenShift 101 for OpenStack admins: Data plane deployment
- Red Hat Enterprise Linux
- Red Hat OpenShift
- Red Hat Ansible Automation Platform
- See all products
- See all technologies
- Developer Sandbox
- Developer Tools
- Interactive Tutorials
- API Catalog
- Operators Marketplace
- Learning Resources
- Cheat Sheets
Communicate
- Contact sales
- Find a partner
Report a website issue
- Site Status Dashboard
- Report a security problem
RED HAT DEVELOPER
Build here. Go anywhere.
We serve the builders. The problem solvers who create careers with code.
Join us if you’re a developer, software engineer, web designer, front-end designer, UX designer, computer scientist, architect, tester, product manager, project manager or team lead.
Red Hat legal and privacy links
- About Red Hat
- Contact Red Hat
- Red Hat Blog
- Diversity, equity, and inclusion
- Cool Stuff Store
- Red Hat Summit
- Privacy statement
- Terms of use
- All policies and guidelines
- Digital accessibility

COMMENTS
To create a VLAN, enter the vlan command with an unused ID. To verify whether a particular ID is in use, enter the show vlan id ID command. To modify a VLAN, enter the vlan command for an existing VLAN. See the "VLAN Default Configuration" section on page 10-4 for the list of default parameters that are assigned when you create a VLAN.
In the CLI (host)(config) # interface vlan < id> ip address < address> < netmask> Configuring a VLAN to Receive a Dynamic Address. In a branch office, you can connect a controller to an uplink switch or server that dynamically assigns IP addresses to connected devices. For example, you can connect the controller to a DSL or cable modem, or a broadband remote access server (BRAS).
Cisco Business routers come with VLAN 1 assigned to all ports by default. A management VLAN is the VLAN that is used to remotely manage, control, and monitor the devices in you network using Telnet, SSH, SNMP, syslog, or Cisco's FindIT. By default, this is also VLAN 1. A good security practice is to separate management and user data traffic.
A VLAN represents a broadcast domain. VLANs are identified by a VLAN ID (a number between 0 - 4095), with the default VLAN on any network being VLAN 1. Each port on a switch or router can be assigned to be a member of a VLAN (i.e., to allow receiving and sending traffic on that VLAN). For example: on a switch, traffic that is sent to a port ...
A VLAN is identified on network switches by a VLAN ID. Each port on a switch can have one or more VLAN IDs assigned to it and will land in a default VLAN if no other one is assigned. Each VLAN provides data-link access to all hosts connected to switch ports configured with its VLAN ID. A VLAN ID is translated to a VLAN tag, a 12-bit field in ...
Usually, Static assignment of VLANs to switch ports is configured. To be able to do so, first, all different VLAN subnets need to be defined. Afterwards, VLAN IDs can be assigned to switch ports and a host that attaches on a given port automatically assumes the VLAN membership of that port. ... You can use the show vlan id [vlan#] command to ...
To test and verify VLAN configuration, you can check connectivity between PCs in the same VLAN. Click the PC icon, click Desktop, and click Command prompt. Use the ping command to test connectivity. PC0 is a member of VLAN-10. As we can see in the above image, it has connectivity with PC2 and PC4.
Static assignments for ports 5 and 6 on the access switch and 5/1-12 and 5/18-24 on the distribution switch into VLAN 10. Distribution_1 will be assigned the IP address 10.1.1.1 and will serve as a VMPS server and get a file called vmpsconfig.txt (shown at the end of the example) from the server 10.1.1.101. Ports 13-16 will be dynamic on ...
To configure VLAN Assignment, specify this value as IEEE-802. Tunnel-Private-Group-Id, which indicates the group ID for a particular tunneled session, that is the assigned VLAN ID. According to the network topology, add the following codes and save the file.
Assigning VLAN profiles. On the profile assignment tab, select the access points, switch (es), and/or stack (s) to assign a profile to. Choose the profile to apply by clicking the drop down profile menu, then "Assign profile". Note: VLAN profiles are applied to standalone switches or entire switch stacks.
Once the configurations are saved, the appropriate VLAN IDs should show on the switch port/s that were configured. If a switch is receiving the VLAN ID from the default group, and the desire is for the switch to use a non-default profile, please validate the device's profile assignment under Network-wide > VLAN Profiles > Profile assignment.
If you attempt to create a VLAN with an existing VLAN ID, the device goes into the VLAN submode but does not create the same VLAN again. Newly created VLANs remain unused until Layer 2 ports are assigned to the specific VLAN. All the ports are assigned to VLAN1 by default.
Virtual LAN (VLAN) is a concept in which we can divide the devices logically on layer 2 (data link layer). Generally, layer 3 devices divide the broadcast domain but the broadcast domain can be divided by switches using the concept of VLAN. A broadcast domain is a network segment in which if a device broadcast a packet then all the devices in ...
Select Dynamic in Client VLAN Assignment to specify a VLAN ID. To create a VLAN assignment rule, click + Add Rule under VLAN Assignment Rules. The New VLAN Assignment Rule window is displayed. Configure the following parameters: Attribute —Select an attribute from the drop-down list.
How to Provision 802.1 X Authentication Step By Step With Dynamic VLAN Assignment With Windows Radius Server For 802.1x Clients. ... 'Tunnel-PVT-Group-ID'. This is a RADIUS attribute that may be passed back to the authenticator (i.e. the Aruba 2920 Switch) by the authentication server (i.e. Microsoft NPS Server) when a successful ...
Additionally, an IP address can be assigned to the default SVI (VLAN 1) to facilitate remote management of the switch. Benefits of Using SVI. Enhanced speed and efficiency are achieved through hardware-based switching and routing, surpassing the limitations of the router-on-a-stick method. ... Interface VLAN (VLAN ID) OSI Layer: Works on Layer ...
These RADIUS attributes decide the VLAN ID that should be assigned to the wireless client. The SSID (WLAN, in terms of WLC) of the client does not matter because the user is always assigned to this predetermined VLAN ID. The RADIUS user attributes used for the VLAN ID assignment are: IETF 64 (Tunnel Type)—Set this to VLAN.
You can use the following commands for VLAN management. Allow port groups to reach port groups located on other VLANs. esxcli <conn_options> network vswitch standard portgroup set -p <pg_name> --vlan-id 4095. Run the command multiple times to allow all ports to reach port groups located on other VLANs. Disable VLAN for port group g42.
You need to send the following attributes from Clearpass in the Access-Accept Message: [64] Tunnel-type = VLAN. [65] Tunnel-Medium-Type = 802. [81] Tunnel-Private-Group-ID = <vlan name>. VLAN name is the name you configure in the VLAN Profiles that has the associated VLANs to it.
In the CLI (host) (config) # interface vlan < id> ip address < address> < netmask> Configuring a VLAN to Receive a Dynamic Address. In a branch office, you can connect a controller to an uplink switch or server that dynamically assigns IP addresses to connected devices. For example, the controller can be connected to a DSL or cable modem, or a broadband remote access server (BRAS).
You can set the VLAN ID in the vmxnet3 driver under Advanced setting of the NIC card. Set the vlan driver in Windows to 4095 when setting multiple specific vLANs in the vDS. When enabling VGT by setting a VLAN range in vDS or VLAN 4095 in vSS, have one VMXNET3 VNIC per VLAN to use within the guest. The real benefit of using VGT is that the ...
When an untagged packet enters a switch port, it gets linked with the Native VLAN (Port VLAN ID) and sent to a VLAN determined by the VID within that Native VLAN. Consequently, a packet received on a specific port inherits the Native VLAN of that port and is then routed to the port corresponding to the packet's destination address. If the Native VLAN of the receiving port differs from that of ...
Here, it's ens224.4, indicating a VLAN interface. ipam: Stands for IP Address Management. It specifies how IP addresses are assigned to the pod interface. type: The type of IPAM plugin to use, here whereabouts, which supports assigning IP addresses across multiple host nodes, avoiding IP address conflicts.