- Course Enquiry +91-7669 100 251 +91-9953 306 008
- Hire from Us +91-7845 696 520
- Interview Questions


WebGoat: A Complete Guide Tutorial For FREE | CHECK-OUT
Last updated on 18th Jul 2020, Blog, Tutorials
- WebGoat is a deliberately insecure J2EE web application designed to teach web application security lessons. In each lesson, users must demonstrate their understanding of a security issue by exploiting a real vulnerability in the WebGoat application.
- For example, in one of the lessons the user must use SQL injection to steal fake credit card numbers. The application is a realistic teaching environment, providing users with hints and code to further explain the lesson.
Why the name ‘WebGoat‘?
- Developers should not feel bad about not knowing security. Even the best programmers make security errors. What they need is a scapegoat, right? Just blame it on the ‘Goat!
Runtime environment for OWASP WebGoat
The following picture shows the ideal local setup for running WebGoat and following the lessons. It also shows WebWolf and how OWASP Zap can be used between the browser and OWASP WebGoat.
Subscribe For Free Demo
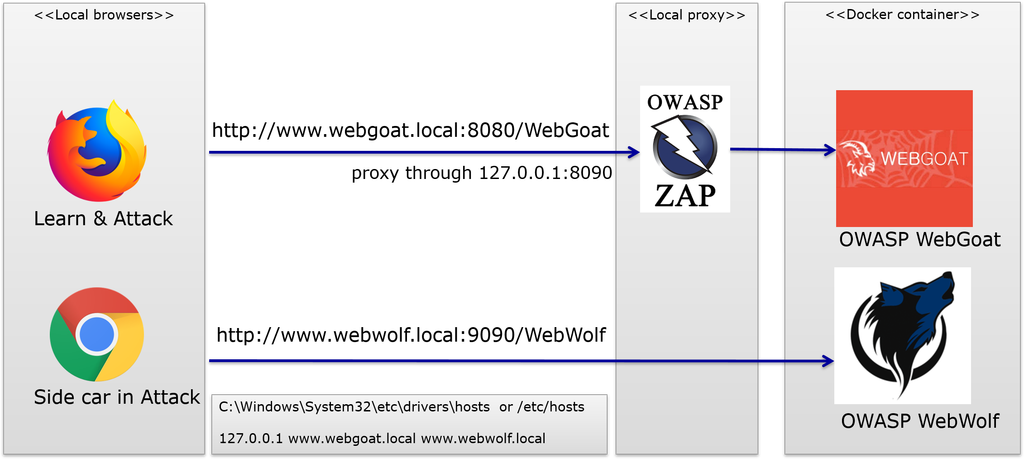
- WebGoat consists of two applications that work together. One is called WebGoat and one is called WebWolf. WebWolf depends on WebGoat and requires that WebGoat is started first.
- Both WebGoat and WebWolf are runnable jar files. Make sure the following ports are available: 80, 8080, 9090, 9001 when running locally.
- There are several options to run WebGoat (and WebWolf):
- Fork/Clone the repository, checkout the develop branch, build the artifacts using Java 11 and Maven 3.6+, and run the archives. mvn clean install
- java -jar webgoat-server/target/webgoat-server-v8.0.0-SNAPSHOT.jar
#then in another shell
java -jar webwolf/target/webwolf-v8.0.0-SNAPSHOT.jar
Download the released and build jar files and run using Java 11
Standalone WebGoat 8.0
Use the all-in-one docker container which contains a reverse proxy and both WebGoat and WebWolf which start in the correct order
Docker WebGoat 8.0
docker run -d -p 80:8888 -p 8080:8080 -p 9090:9090 -e TZ=Europe/Amsterdam webgoat/goatandwolf:latest
Installing Java
WebGoat requires installation of the Java Runtime Environment (JRE). If you already have Java installed, it is worth updating to the latest version to avoid any possible issues.
First, update the package index:
sudo apt-get update
Then install the JRE by running this command:
sudo apt-get install default-jre
To check the Java version after installing the package:
java -version
Installing WebGoat
Download and install the latest version of WebGoat Server to a suitable location, such as your Downloads folder.
All releases can be found here: https://github.com/WebGoat/WebGoat/releases
The latest version (at the time of writing) is: webgoat-server-8.0.0.M23.jar
wget https://github.com/WebGoat/WebGoat/releases/download/v8.0.0.M23/webgoat-server-8.0.0.M23.jar
To start the WebGoat Server:
java -jar webgoat-server-8.0.0.M23.jar
Note: if using Java 9 or higher you might need to start WebGoat as follows (update version number as required):
java –add-modules java.xml.bind -jar webgoat-server-8.0.0.M23.jar
You will see the following message when WebGoat has started successfully:
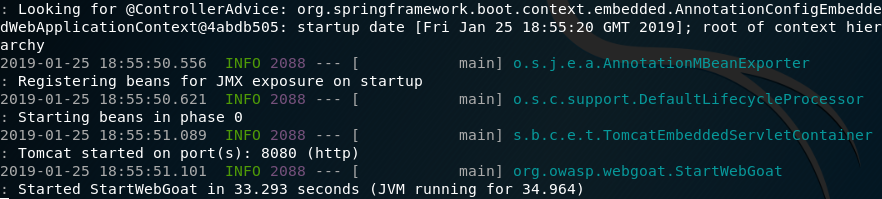
Note: if you wish to run WebGoat on an alternate port and address, you can do so with the following options:
java -jar webgoat-server-8.0.0.M23.jar [–server.port=8080] [–server.address=localhost]
Accessing the WebGoat Interface
To access the WebGoat interface, open your browser and navigate to:
You will then be presented with the WebGoat login screen:
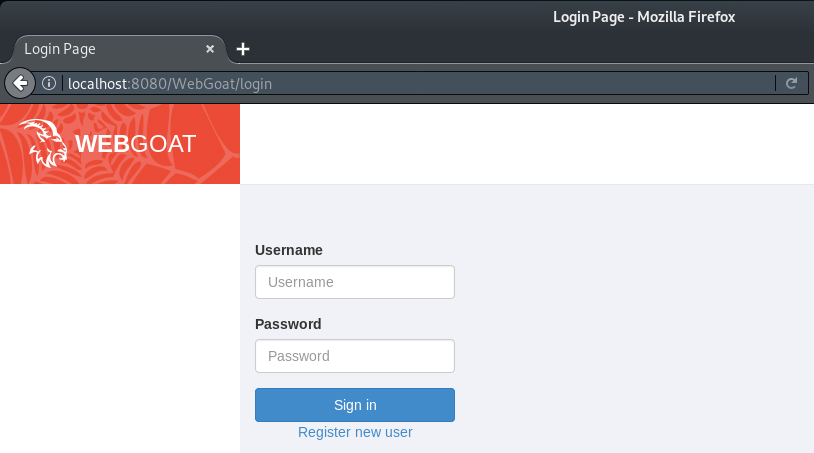
To access the lessons and challenges you will need to select ‘Register new user’ and create a login.

Get Webgoat Ethical Hacking Training from Certified Faculty
- Instructor-led Sessions
- Real-life Case Studies
- Assignments
Note the terms of use when creating a new user:
- While running this program your machine will be extremely vulnerable to attack. You should disconnect from the Internet while using this program. WebGoat’s default configuration binds to localhost to minimize the exposure.
- This program is for educational purposes only. If you attempt these techniques without authorization, you are very likely to get caught. If you are caught engaging in unauthorized hacking, most companies will fire you. Claiming that you were doing security research will not work as that is the first thing that all hackers claim.
Once you are logged in, then it’s time to get started:
Conclusion:
- Learning the basic techniques necessary to secure web applications is absolutely essential for professional web developers. The OWASP project and especially the WebGoat are great resources for doing exactly that. Especially in the field of web security, learning how to hack can be greatly beneficial for anyone aspiring to improve their skills in web security.
- But you don’t have to take my word for it, Michael Coates, Chief Information Security Officer at Twitter, in his great talk Applications Through an Attacker’s Lens at InfoQ, mentioned WebGoat and OWASP’s Security Shepherd as some of the best ways to learn how to hack in a safe environment.
- So if you’re interested in improving your web security skills, I encourage you to start out by hacking the WebGoat! ~:)
Are you looking training with Right Jobs?
Related Articles
- [MOST FREQUENTLY ASK] GIT Interview Questions & Answers
- KNOW Top 25+ GitHub Interview Questions & Answers
- How to Download & Install GIT Tutorial? – Practical Guide For FREE
- GIT Architecture Tutorial: A Complete Hands-on How To Use Guide For Free
- what is Git Push Command? All you need to know [ OverView ]
Popular Courses
11256 Learners
12562 Learners
11741 Learners
Latest Articles
- 40+ [REAL-TIME] SAP Transportation Management Interview Questions and Answers
- 50+ [REAL-TIME] SAP Hybris Interview Questions and Answers
- 50+ [REAL-TIME] Salesforce integration Interview Questions and Answers
- 50+ [REAL-TIME] SAP Analytics Cloud Interview Questions and Answers
- 40+ [REAL-TIME] SAP HCM Interview Questions and Answers
Get Training Quote for Free
Want to be our franchise, corporate training enquiry, internship training with certification, apply to job, browse by loation, connect with course advisor, talk to a career expert, schedule 1:1 free counselling, transform your ambitions into achievements..
- We Offer Practical Classes.
- 100% Placement Support Is Provided to Students.
- Trainers Have 9+ Years of Experience.
- Global Recognization Certification Provided.
Testimonials
Expert-Led No.1
Executive Post Graduate Certification in Data Science & Artificial Intelligence
- Java Training
- Python Training
- Software Testing Training
- Selenium Training
- Full Stack Development Training
- Data Science Training
- AWS Training
- Digital Marketing Training
- Devops Training
- Ethical Hacking Training
- View All Courses
- Combo Courses
- Full Stack Developer Training
- Manual Testing
- ETL Testing
- Test Complete
- Mobile Application Testing
- Database Testing
- SAP Testing
- SOA Testing
- Apache Cassandra
- WPF and WCF
- SharePoint Developer
- SharePoint admin
- Microsoft Dynamics
- Windows Power Shell
- SQL Server DBA
- DB2 DBA UDB
- Teradata DBA
- PhoneGap Apache Cordova
- Appcelerator Titanium
- Linux System Administrator
- Windows Server Administration
- Unix Administrator
- Citrix Server
- NetApp Storage
- EMC Storage
- Oracle Solaris
- Placement Training
- Amazon Web Services(AWS)
- Google Cloud
- Microsoft Azure
- Salesforce Admin
- Salesforce Developer
- Open Nebula
- VMWare Cloud
- Informatica
- MicroSoft Power BI
- MicroStrategy
- IBM Cognos TM1
- TIBCO Spotfire
- Big data Analytics
- Ab Initio Software
- Informatica Data Quality
- Informatica MDM
- BusinessObjects
- Tableau Software
- Apache Spark
- Data science
- Data Science with R
- Data Science With SAS
- Machine Learning Using R
- R Programming
- AI and Deep Learning
- Python with Machine Learning
- Artificial Intelligence
- Machine Learning
- Automation Anywhere
- Ethical Hacking
- Hardware & Networking
- Cyber Security
- Embedded Systems
- PLC and SCADA
- Oracle Developer
- Oracle Apps Finance
- Oracle Apps SCM
- Oracle Apps HRM
- Oracle Apps DBA
- Oracle Apps Technical
- Oracle PeopleSoft Finance
- Oracle PeopleSoft HCM
- Oracle SQL and PLSQL
- Oracle Admin
- Oracle GoldenGate
- Oracle Performance Tuning
- Oracle DataGuard
- Oracle Fusion HCM
- Oracle Fusion Financial
- Oracle Cloud
- Oracle Identity Manager
- Oracle Forms and Reports
- Oracle APEX
- Oracle 12 Certification
- Mainframe Developer
- Mainframe Administrator
- IBM Websphere Application Server
- IBM Websphere MQ System Admin
- WebSphere Message Brokers (MQ)
- Digital Marketing
- Google Analytics
- Google Adwords – PPC
- HTML & CSS
- PHP & MySQL
- Adobe Illustrator
- 2D Animation
- 3D Animation
- 3D Animation and VFX
- Game Technologies
- AR & VR Technologies
- Fashion Design
- Interior Design
- Digital Video Production
- Visual Effects
- Spoken English
- C & C++
- MicroSoft Office
- MicroSoft Advanced Excel
- Ruby on Rails
- UNIX Shell Scripting
- PERL Scripting
- Scrum Master
- Project Management Professional
- Freshers Masters Program & Placement
- FULL Stack Web Developer – MEAN Stack
- Cloud Computing Master Program
- DevOps Master Program
- Big Data masters Program
- Software Testing Master Program
- Web Design & PHP Master Program
- Full Stack Master Program
- Business Intelligence Master Program
- Data Analyst Masters Program
- Artificial Intelligence Masters Program
- PMP Masters Program
- Cyber Security Expert Masters Program
- AWS Cloud Architect Masters Program
- Six Sigma Expert Masters Program
- Java Full Stack Developer Masters Program
- Data Science Masters Program
- Digital Project Manager Masters Program
- ITIL Expert Capability Stream Masters Program
- Python Master Program
- ITIL Managing Professional Masters Program
- Digital Marketing Associate Masters Program
- Advanced Digital Marketing Masters Program
- Digital Marketing Masters Program
- Java Masters Program
- Machine Learning Masters Program
- Full Stack Developer Masters Program
- Automation Testing Masters Program
- Business Analyst Masters Program
- United Kingdom
- Placed Students list
- Sample Resume
- On Job Support
- Jobs in Chennai
- Jobs in Bangalore
- Jobs in Pune
- Jobs in Coimbatore
- Jobs in Hyderabad
- Velachery Reviews
- Tambaram Reviews
- Anna Nagar Reviews
- Porur Reviews
- Thiruvanmiyur Reviews
- Maraimalai Nagar Reviews
- T.Nagar Reviews
- Siruseri Reviews
- OMR Reviews
- Adyar Reviews
- Video Reviews
- Corporate Training
- Job seekers
Writing What I Want
Solving the Assignment in the OWASP WebGoat Crypto Basics Signature Lesson
So I’ve been playing around with the OWASP WebGoat project .

The WebGoat Logo
WebGoat is a web application with a Java Spring back-end. Its purpose is to teach - through a series of interactive lessons - vulnerabilities in web applications, particularly those with Java back-ends. As such, it is deliberately insecure.
I was chugging along with the lessons just fine until I reached the assignment on cryptographic signatures in the Crypto Basics section.
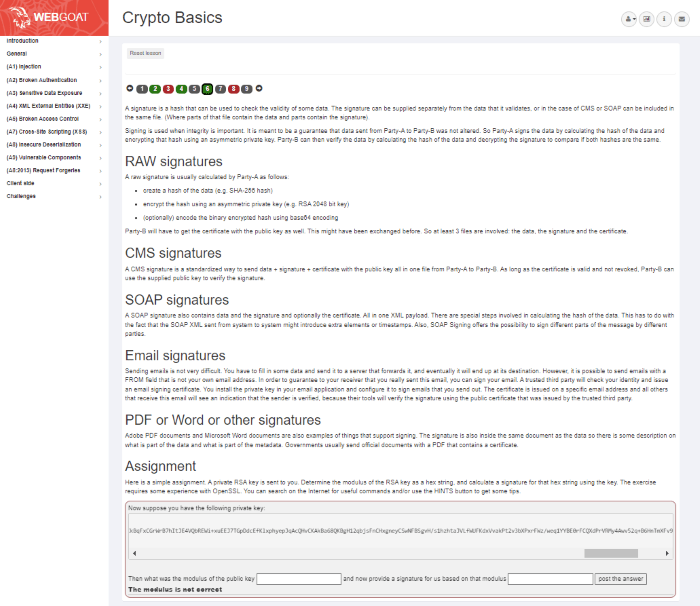
Screenshot of the Cryptographic Signatures Lesson in the Crypto Basics Section
Now, I understand what cryptographic signatures are. They’re a way of verifying that data hasn’t been modified since it was signed. Typically it’s a hash of the data that has been encrypted using a private key and verifiable with a public key.
What confused me was what format they wanted the answer to be in.
For context, here’s the assignment:
Assignment Here is a simple assignment. A private RSA key is sent to you. Determine the modulus of the RSA key as a hex string, and calculate a signature for that hex string using the key. The exercise requires some experience with OpenSSL. You can search on the Internet for useful commands and/or use the HINTS button to get some tips. Now suppose you have the following private key: -----BEGIN PRIVATE KEY----- MIIEuwIBADANBgkqhkiG9w0BAQEFAASCBKUwggShAgEAAoIBAQCWCh+WB5Kt8QdXcBQxae54TNkmqmYfm6Sdn+hQpiGnaFQoVDH/2+V/KbEd68nkk36Mm/5Gh1dQUFUB6E2/CWld866LSPTsJjlQRFIPoLZqMDTRoOY3hfuV9pUTESHE2rlxNArh6poWgdeBeR6r2ystCvkT+XmwN74Yvqui8b+CiRzkQSEgNGnNEQUqL2ttm8dpaMFaOVr09HuHAfARjUJydql/Azlk2ui72uYBo2hHgL9ZFsgfqISPfbDfxIEnYqfQG2iykKB3EjgM2CKjJr6HyYrPoW5Co2mYLfCCVmf89UmVxxHzPkdAnnS088cgHQKIC0zbgOm7kBLqzIy/BIdVAgEFAoIBAB4CBlE0tu+WmxF80NauyUtCkdSIetMfIOxTLnaHoFSudztECf/4x3/VI2xiW5Qdf7W4zHSBd9zc3c0udfMB4d+XIuioMPwHpRANqgMgJHujPcOGlHGBMlExUQPQOfQrvrA9m8bIhTezkYBLbIjFbwkCMdDLfrzX8tG/u+1jjLO0tl/oJBrDlnzdzqKxRakL9sYhQw+TYggmdF3AyzY3ikXA/RLFNocvKHI3O+kwkqWMhucZdx18H4T45/dLgMxewsh7spKHFlleDufY+MFSqMC15+3b3XQ2l2SeSTBtybvIxEZhZVYzNE1TLKEemUp30hD6+2BZb53e1uNBTMKvIG0CgYEApvQAQDPOg8YWF5amLjqTA6NvHmwgK+8zcD4n+1scNIpRuIp1pxyJ3Maomj2bwInSuTKb8KPGNGEs0wfe0joZNiANKKK5l64yBRoE8z8KH4siVbxnAiZjrOmOCWM/bsRTbRjcLqNx5XvRSn2pLziG0+gmT9gjCviZ05ZMjAFzAvkCgYEA5hC4LGaT9Zal5GYS4OXM8edTU6A4RN0AxXQV/KdbWotf/5azgaRlQboeIDYUyoHvY6L7g+h1spV0VgNsKu9vo8WjwzMzmQoJ6GuWU51/UzkZrW3vGNcux7eIeSzyCI22Bx0D6KDMXEItSxGxmXM/FEr+FCGesK2cDOQ5gPAl4j0CgYBkLAAmhXvoqg1BWmO1Vlg1Yg94p0aAwrh2i7GW0EQfhjEIUxNkRFK3qmUpWCpAUrGiUZDDlXbsOk4YN+wXvHWG4AflLm9bAh4DD5yR8p+shq4zcQqa49Vnv1U41SYPQph0qIQb+6q84+P5fpi17rdL8bCWTnts+49+88eHNBHOlQKBgQCKCggao/JgJzBV1tggieFd8TH++btchJoQEnOXl502U5//wNIaldZaot7gIHLf54+iLpbovq0EwBKaAg2zXHYvEC8OuFIon5+Lc8CYkbLLiKkBqFxCGrWrB7hItJE4VQbREWi+xuEEJ7TGpDdcEfKlxphyepJqAcQHvCKAkBa68QKBgH12qbjsFnCHxgneyCSwNFBSgvH/s1hzhtaJVLfWUFKdxVvakPt2v3bXPxrFWz/weq1YYBE0rFCQXdPrVRMy4Awv52q+B6HnTmXFv9+ZuHpFHWIhFWD3G1/8f9hh5PhzhFToNioVzR+451bLAOHXmiN3P4EPcmycNpXjmCJ4lwBx -----END PRIVATE KEY----- Then what was the modulus of the public key and now provide a signature for us based on that modulus post the answer
Ok, I’m a little confused. I know they want the modulus of the RSA as a hex string but what format do they want the signature in? Bits? Also a hex string? Maybe even a Base64 string - after all, one of the previous lessons covered Base64.
Let’s experiment. What happens if I click the post the answer without entering anything?
It turns out it outputs the following error: The modulus is not correct
Ok, let’s see if I can figure out the modulus (remember - as a hex string!) and see if it tells me anything different.
I want to use OpenSSL , however, since I’m running Windows, I don’t have it immediately available on the command line.
However, I’m running WebGoat in a Docker container . Which is in a Linux container. Which means I can go into the terminal of the WebGoat container and use OpenSSL. No extra installation required.
In case you’re wondering, here are the commands to run WebGoat in a Docker container: docker pull webgoat/webgoat-8.0 docker run -p 8080:8080 -t webgoat/webgoat-8.0
Inside the terminal, I copied the key with some echo commands:
And then ran the following openssl command to get the modulus:
There’s quite a bit of output, but what I’m interested in is this first part:
That most certainly looks like hex code - I’m only seeing numbers and the letters a through f . But if I copy that as-is into the modulus input box, I get another The modulus is not correct error.
It turns out I need to remove those pesky colons and white spaces - so instead I insert the following:
This time I get a different error: The signature does not match the data (modulus)
Yay - now I’m halfway through! I just need to provide a signature based on that modulus .
So I put the modulus into a file like I did the key:
And then try to sign the file like:
But when I paste the result (and just the hex bit) into the signature field, I just get another The signature does not match the data (modulus) message.
I even tried to convert the hex to a base64 string, or a binary string, and still got the same error. I even tried signing the modulus by piping it in instead of via a file, but it just gave me the same signature:
At this point, I have no idea if I’m doing the signature wrong (and if I am, please tell me what I’m doing wrong in the comments!) or if I’m simply not providing the right format that WebGoat wants.
It’s time to open up WebGoat and to figure this out.
Fortunately for me, I don’t have to extract WebGoat from the Docker container - the source code for WebGoat is available on GitHub .
As for where in the source code I need to look, WebGoat provides this useful bit of info in the log:
The log leads me to SigningAssignment.java - but more importantly to CryptoUtil.java. CryptoUtil.java has a signMessage method that returns a String - a String that I suspect is in the format that the lesson wants the answer.
So I made a short Java program to output that String signature:
And then copy-paste the signature into the answer text box, clicked on the button, and got the following message: Congratulations. You found it!
By the way, here’s the signature - in Base64. I don’t know what I needed to do to get this from OpenSSL: a0W78/05PoLBMPCBSTJiqyaEVkGvfoE8vVVMs0DB/p2GpZD5OHsQbHq59fCliXBjAZydSD4lNBccUpfxkPF1vyAMBBr0mqh+aZ9U/1JCKafn67CIA1xH7Kpllmw/ZIUtFQzIj8O34dVnLs1OWf03NXt3dWWXKLA6Emo4xytfWSnjIRvP0UTePfljDbCtyavAt7ReSu67QPaUPZdrkddczmq02klMPvosMHzdOgYn1j1UnAmWV/EKgNTIUkk3GhFPOKkBvc3kG6ZsqKiLVMQZQddaOR7smMcYH/21cVnMpQ1VqE/6bYd+nN7zPo5JLPqTmGPmsOjh+EMjKt1X2OchlQ==
Onto the next lesson!
2 comments for Solving the Assignment in the OWASP WebGoat Crypto Basics Signature Lesson
I had to use echo -n with the colon-less hex blurb in quotes, pipe it to what you have exactly with exception of the -hex, then pipe to base64
**99% of this came from the hints as they probably thought most of us would have issues with this concept.
Reply to This Thread
Thanks for the guidance. I was banging my head. I thought I’ll share the method that does not need find and replace in a separate text editor.
openssl pkey -in lesson6.key -pubout -out public.key openssl rsa -in public.key -pubin -modulus -noout
Copy the text after Modulus= to the first text box.
Leave a Reply
This website uses cookies to analyze our traffic and only share that information with our analytics partners.
OWASP WebGoat

Learn the hack - Stop the attack
WebGoat is a deliberately insecure application that allows interested developers just like you to test vulnerabilities commonly found in Java-based applications that use common and popular open source components.
Description
Web application security is difficult to learn and practice. Not many people have full blown web applications like online book stores or online banks that can be used to scan for vulnerabilities. In addition, security professionals frequently need to test tools against a platform known to be vulnerable to ensure that they perform as advertised. All of this needs to happen in a safe and legal environment.
Even if your intentions are good, we believe you should never attempt to find vulnerabilities without permission. The primary goal of the WebGoat project is simple: create a de-facto interactive teaching environment for web application security. In the future, the project team hopes to extend WebGoat into becoming a security benchmarking platform and a Java-based Web site Honeypot.
WARNING 1: While running this program your machine will be extremely vulnerable to attack. You should disconnect from the Internet while using this program. WebGoat’s default configuration binds to localhost to minimize the exposure.
WARNING 2: This program is for educational purposes only. If you attempt these techniques without authorization, you are very likely to get caught. If you are caught engaging in unauthorized hacking, most companies will fire you. Claiming that you were doing security research will not work as that is the first thing that all hackers claim.
Learn in three steps
Explain the vulnerability.

Teaching is now a first class citizen of WebGoat, we explain the vulnerability. Instead of ‘just hacking’ we now focus on explaining from the beginning what for example a SQL injection is.
Learn by doing
During the explanation of a vulnerability we build assignments which will help you understand how it works.

Explain mitigation
At the end of each lesson you will receive an overview of possible mitigations which will help you during your development work.

WebGoat contains lesson for almost all OWASP Top 10 vulnerabilities and more…

Future lessons
The following lessons are on our wish list:
- Lesson about cryptography (in progress)
- Lesson about path traversal (in progress)
- Session management
- More password reset lessons
See our Github page for more information.
Getting started
1. run using docker.
Already have a browser and ZAP and/or Burp installed on your machine in this case you can run the WebGoat image directly using Docker.
Every release is also published on DockerHub .
If you want to reuse the container, give it a name:
As long as you don’t remove the container you can use:
This way, you can start where you left off. If you remove the container, you need to use docker run again.
2. Run using Docker with complete Linux Desktop
Instead of installing tools locally we have a complete Docker image based on running a desktop in your browser. This way you only have to run a Docker image which will give you the best user experience.
3. Standalone
Download the latest WebGoat release from https://github.com/WebGoat/WebGoat/releases
Click the link in the log to start WebGoat.

WebWolf the small helper
WebWolf is a separate web application which simulates an attackers machine. It makes it possible for us to make a clear distinction between what takes place on the attacked website and the actions you need to do as an “attacker”. WebWolf was introduced after a couple of workshops where we received feedback that there was no clear distinction between what was part of the “attackers” role and what was part of the “users” role on the website. The following items are supported in WebWolf:
Host a file
Upload a file needed to be downloaded during an assignment

E-mail client
WebWolf serves a mail client with which we can easily simulate sending an e-mail.

Landing page for incoming requests
WebWolf can serve as a landing page to which you can make a call from inside an assignment, giving you as the attacker information about the complete request. Think of it as a very simple form of netcat .

If you started the Docker image, WebWolf is already running. Please point your browser to: http://localhost:9090/WebWolf
2. Standalone
If you want to use the standalone version, you will need to download the jar file and start it:
By default, WebWolf starts on port 9090 with --server.port you can specify a different port. With server.address you can bind it to a different address (default localhost)
- Standalone jars
- Docker Image
Code Repository
- Source code
Helping the Goat!
- Report an issue
- Contributing to WebGoat
- Forking WebGoat in GitHub
Around the Web
- StackOverflow
Classification
- Bruce Mayhew
- Nanne Baars
- Jason White
- René Zubčević
Upcoming OWASP Global Events
Owasp news & opinions.
Navigation Menu
Search code, repositories, users, issues, pull requests..., provide feedback.
We read every piece of feedback, and take your input very seriously.

Saved searches
Use saved searches to filter your results more quickly.
To see all available qualifiers, see our documentation .
- Notifications
WebGoat is a deliberately insecure application
WebGoat/WebGoat
Folders and files, repository files navigation, webgoat: a deliberately insecure web application.
Introduction
WebGoat is a deliberately insecure web application maintained by OWASP designed to teach web application security lessons.
This program is a demonstration of common server-side application flaws. The exercises are intended to be used by people to learn about application security and penetration testing techniques.
WARNING 1: While running this program your machine will be extremely vulnerable to attack. You should disconnect from the Internet while using this program. WebGoat's default configuration binds to localhost to minimize the exposure.
WARNING 2: This program is for educational purposes only. If you attempt these techniques without authorization, you are very likely to get caught. If you are caught engaging in unauthorized hacking, most companies will fire you. Claiming that you were doing security research will not work as that is the first thing that all hackers claim.

Installation instructions:
For more details check the Contribution guide
1. Run using Docker
Already have a browser and ZAP and/or Burp installed on your machine in this case you can run the WebGoat image directly using Docker.
Every release is also published on DockerHub .
For some lessons you need the container run in the same timezone. For this you can set the TZ environment variable. E.g.
If you want to use OWASP ZAP or another proxy, you can no longer use 127.0.0.1 or localhost. but you can use custom host entries. For example:
Then you can run the container with:
Then visit http://www.webgoat.local:8080/WebGoat/ and http://www.webwolf.local:9090/WebWolf/
2. Run using Docker with complete Linux Desktop
Instead of installing tools locally we have a complete Docker image based on running a desktop in your browser. This way you only have to run a Docker image which will give you the best user experience.
3. Standalone
Download the latest WebGoat release from https://github.com/WebGoat/WebGoat/releases
Click the link in the log to start WebGoat.
4. Run from the sources
Prerequisites:.
- Java 17 or 21
- Your favorite IDE
- Git, or Git support in your IDE
Open a command shell/window:
Now let's start by compiling the project.
Now we are ready to run the project. WebGoat is using Spring Boot.
... you should be running WebGoat on http://localhost:8080/WebGoat momentarily.
Note: The above link will redirect you to login page if you are not logged in. LogIn/Create account to proceed.
To change the IP address add the following variable to the WebGoat/webgoat-container/src/main/resources/application.properties file:
4. Run with custom menu
For specialist only. There is a way to set up WebGoat with a personalized menu. You can leave out some menu categories or individual lessons by setting certain environment variables.
For instance running as a jar on a Linux/macOS it will look like this:
Or in a docker run it would (once this version is pushed into docker hub) look like this:
Code of conduct
Releases 11, sponsor this project.
- https://owasp.org/donate/?reponame=www-project-webgoat&title=OWASP+WebGoat
Contributors 105
- JavaScript 47.6%
- RobotFramework 0.2%
- Dockerfile 0.0%
WebGoat 8: A deliberately insecure Web Application

Introduction
WebGoat is a deliberately insecure web application maintained by OWASP designed to teach web application security lessons.
This program is a demonstration of common server-side application flaws. The exercises are intended to be used by people to learn about application security and penetration testing techniques.
WARNING 1: While running this program your machine will be extremely vulnerable to attack. You should disconnect from the Internet while using this program. WebGoat’s default configuration binds to localhost to minimize the exposure.
WARNING 2: This program is for educational purposes only. If you attempt these techniques without authorization, you are very likely to get caught. If you are caught engaging in unauthorized hacking, most companies will fire you. Claiming that you were doing security research will not work as that is the first thing that all hackers claim.
Installation instructions:
For more details check the Contribution guide
1. Run using Docker
Already have a browser and ZAP and/or Burp installed on your machine in this case you can run the WebGoat image directly using Docker.
Every release is also published on DockerHub .
If you want to reuse the container, give it a name:
As long as you don’t remove the container you can use:
This way, you can start where you left off. If you remove the container, you need to use docker run again.
2. Run using Docker with complete Linux Desktop
Instead of installing tools locally we have a complete Docker image based on running a desktop in your browser. This way you only have to run a Docker image which will give you the best user experience.
3. Standalone
Download the latest WebGoat release from https://github.com/WebGoat/WebGoat/releases
Click the link in the log to start WebGoat.
4. Run from the sources
Prerequisites:.
- Your favorite IDE
- Git, or Git support in your IDE
Open a command shell/window:
Now let’s start by compiling the project.
Now we are ready to run the project. WebGoat is using Spring Boot.
… you should be running WebGoat on http://localhost:8080/WebGoat momentarily.
Note: The above link will redirect you to login page if you are not logged in. LogIn/Create account to proceed.
To change the IP address add the following variable to the WebGoat/webgoat-container/src/main/resources/application.properties file:
4. Run with custom menu
For specialist only. There is a way to set up WebGoat with a personalized menu. You can leave out some menu categories or individual lessons by setting certain environment variables.
For instance running as a jar on a Linux/macOS it will look like this:
Or in a docker run it would (once this version is pushed into docker hub) look like this:
- Application Security
- Infrastructure Security
- Ethical Hacking
- Sec-Sci AutoPT
- White Papers
- Training Courses
OWASP WebGoat
- Hands-On Learning : WebGoat provides a hands-on and interactive learning experience for individuals interested in understanding common web application security vulnerabilities. Users can directly engage with real-world scenarios and vulnerabilities.
- Safe Environment : Since WebGoat is intentionally vulnerable, users can practice their skills without any risk to real systems or applications. This controlled environment ensures that learning takes place in a safe and risk-free manner.
- Comprehensive Coverage : The application covers a wide range of security vulnerabilities, including Cross-Site Scripting (XSS), SQL injection, Cross-Site Request Forgery (CSRF), and more. This comprehensive coverage allows users to explore different types of vulnerabilities.
- Realistic Scenarios : WebGoat presents realistic scenarios that mimic vulnerabilities encountered in actual web applications. This authenticity enhances the learning experience by simulating real-world challenges.
- Guided Learning : The application provides explanations, hints, and guidance on exploiting vulnerabilities and implementing proper mitigation measures. This support helps users learn and understand the concepts behind the vulnerabilities.
Key Features of WebGoat
- Vulnerability Challenges : WebGoat includes a variety of challenges and lessons that focus on different security vulnerabilities. Each challenge presents a specific vulnerability scenario for users to identify and exploit.
- Progress Tracking : The platform allows users to track their progress and completion of challenges, providing a sense of accomplishment as they advance through the lessons.
- Built-in Hints : WebGoat offers hints and guidance for each challenge, helping users who may be stuck or seeking assistance to progress through the lessons.
- Exploit Prevention : Some challenges in WebGoat also focus on implementing proper security measures to prevent the exploitation of vulnerabilities. This helps users understand both sides of the security equation: exploiting and securing.
- Step-by-Step Instructions : The platform provides step-by-step instructions on how to set up and use the application, making it accessible even for those new to web application security.
- Open Source : WebGoat is an open-source project, meaning that it can be freely accessed, used, and even contributed to by the community.
- Extensibility : Users can modify and extend WebGoat to include new challenges, vulnerabilities, or lessons, allowing it to be customized to fit specific educational needs.
WebGoat serves as a valuable resource for individuals looking to enhance their understanding of web application security vulnerabilities and their mitigation strategies. It's widely used in training sessions, workshops, and educational programs to provide practical insights into the world of web application security. Installing WebGoat on Docker
- Pull the latest WebGoat image from hub.docker.com repository then run. docker pull webgoat/webgoat:latest docker run --name webgoat -it -p 127.0.0.1:8080:8080 -p 127.0.0.1:9090:9090 webgoat/webgoat
- Host a file : Upload a file needed to be downloaded during an assignment
- E-mail client : WebWolf serves a mail client with which we can easily simulate sending an e-mail.
- Landing page for incoming requests : WebWolf can serve as a landing page to which you can make a call from inside an assignment, giving you as the attacker information about the complete request. Think of it as a very simple form of netcat .
For more information about WebGoat, visit the following links: https://owasp.org/www-project-webgoat https://github.com/WebGoat/WebGoat https://hub.docker.com/r/webgoat/goatandwolf
- Post a Job Post a Job
- Find Talent Find Talent
- Log in Log in
Webgoat explained
WebGoat: A Powerful Tool for Teaching and Learning Web Application Security
Table of contents
Introduction, what is webgoat, history and background, purpose and usage, example lessons and challenges, relevance in the industry and standards.
In the realm of information security and cybersecurity, practical hands-on experience is crucial for professionals to develop the necessary skills to protect systems and applications from vulnerabilities and attacks. WebGoat, an open-source project developed by OWASP (Open Web Application security Project), is a powerful tool designed to provide a safe and interactive environment for teaching and learning about web application security. This article will delve deep into the various aspects of WebGoat, including its purpose, usage, background, examples, use cases, career relevance, and industry standards.
WebGoat is a deliberately insecure web application specifically designed to help individuals understand common web application vulnerabilities and learn how to Exploit and mitigate them. It simulates real-world scenarios, allowing users to practice identifying and exploiting vulnerabilities in a controlled environment. By providing a hands-on experience, WebGoat effectively teaches the principles of web application security, making it an invaluable tool for both beginners and experienced professionals.
The WebGoat project was initiated by OWASP in 2003 with the goal of creating a vulnerable web application that could be used as a training tool for individuals interested in learning about web application security. The project aimed to bridge the gap between theoretical knowledge and practical application by providing a platform to practice real-world attacks on web applications.
The initial version of WebGoat was developed by Bruce Mayhew and Jason White, and it quickly gained popularity within the cybersecurity community. Over the years, the project has evolved and been maintained by a dedicated group of volunteers, resulting in a robust and feature-rich tool that continues to be widely used for educational purposes.
WebGoat serves two primary purposes: education and training. It provides a practical environment for individuals to learn about web application security vulnerabilities and understand how to protect against them. WebGoat achieves this by presenting a series of lessons and challenges that cover a wide range of vulnerabilities, including injection attacks, cross-site Scripting (XSS), insecure direct object references (IDOR), and many others.
Users can interact with the vulnerable application through a web browser and attempt to exploit the identified Vulnerabilities . Each lesson includes a detailed explanation of the vulnerability, step-by-step instructions on how to exploit it, and suggestions for mitigation techniques. This interactive approach allows users to gain hands-on experience in a controlled environment, fostering a deeper understanding of web application security.
WebGoat offers a comprehensive set of lessons and challenges, covering various aspects of web Application security . Here are a few examples:
Cross-Site Scripting ( XSS ) : This lesson demonstrates the risks associated with cross-site scripting attacks. Users learn how to inject malicious scripts into web pages and understand the impact of such attacks on user data and application integrity.
SQL Injection : This lesson focuses on SQL injection vulnerabilities, teaching users how to manipulate database queries to extract sensitive information or perform unauthorized actions.
Access Control : This lesson covers insecure direct object references (IDOR) and broken access control mechanisms. Users learn how to bypass authentication and authorization controls to gain unauthorized access to protected resources.
Insecure Cryptographic Storage : This lesson explores the importance of proper cryptographic storage. Users learn about common mistakes in storing passwords and other sensitive information and the potential consequences of weak security practices.
These examples represent just a fraction of the lessons and challenges available in WebGoat. The tool covers a wide range of Vulnerabilities , ensuring users gain exposure to various real-world scenarios.
WebGoat has proven to be an invaluable tool for a variety of use cases within the information security industry. Some of the common use cases include:
Education and Training : WebGoat is widely used in educational institutions, training programs, and workshops to teach web application security concepts and provide hands-on experience to students and professionals.
Penetration Testing Practice : Penetration testers often utilize WebGoat to enhance their skills and practice exploiting vulnerabilities in a controlled environment. It allows them to sharpen their techniques and stay up-to-date with the latest attack vectors.
Security Awareness Programs : Many organizations leverage WebGoat to raise awareness about web application security among their employees. By allowing employees to interact with a vulnerable application, organizations can educate them about the risks and best practices in a practical and engaging manner.
Secure Development Training : WebGoat is also utilized by software development teams to educate developers about common vulnerabilities and teach secure coding practices. By understanding the potential pitfalls, developers can create more secure applications from the outset.
WebGoat's relevance in the cybersecurity industry cannot be overstated. It has become a staple tool for professionals looking to develop and enhance their web application security skills. By providing a practical learning environment, WebGoat helps bridge the gap between theoretical knowledge and real-world application.
Furthermore, WebGoat aligns with industry standards and best practices. It covers vulnerabilities and attack techniques outlined in the OWASP Top Ten Project, which serves as a benchmark for web application security. OWASP Top Ten lists the most critical web application security risks, and WebGoat effectively addresses these risks through its lessons and challenges.
WebGoat is a powerful and widely-used tool in the realm of information security and cybersecurity. By providing a safe and interactive environment, it enables individuals to learn about web application security vulnerabilities, understand their impact, and develop mitigation strategies. Whether used for educational purposes, penetration testing practice, security awareness programs, or secure development training, WebGoat plays a vital role in enhancing professionals' knowledge and skills.
References: - WebGoat GitHub Repository - OWASP WebGoat Project - OWASP Top Ten Project
SOC 2 Manager, Audit and Certification
@ Deloitte | US and CA Multiple Locations
Manager, Data Insights and Forensics
@ Kroll | New York City, United States
Corporate Security Engineer
@ DoorDash | United States - Remote
US Privacy Officer
@ Computershare | Canton, Massachusetts, United States
Sanctions Compliance Officer
@ Meta | Los Angeles, CA | Menlo Park, CA
Cyber Security Intern
@ Quantum Metric | Remote - Intern
Webgoat jobs
Looking for InfoSec / Cybersecurity jobs related to Webgoat? Check out all the latest job openings on our Webgoat job list page.
Webgoat talents
Looking for InfoSec / Cybersecurity talent with experience in Webgoat? Check out all the latest talent profiles on our Webgoat talent search page.
Related articles

OWASP WebGoat SQL advanced lesson 5
Last week I wrote about the OWASP WebGoat XSS lessons . Today I’d like to write a few pointers on how to solve the SQL injection (advanced) lesson 5. The goal is simple: you are presented with a login box and given a username; log in as that user.
The usual username’ OR ‘1’=’1 — unfortunately doesn’t work (that would have been too easy!), and since the last slide talked about blind SQL injection, it was pretty obvious that this was the way to go. After a few unfruitful hours trying to use SLEEP and UNION on the register new user page I started looked online for a hint. What I found was to register a new user, and then register it again with either TRUE or FALSE:
Register new user: testuser Again register the same user but like this: testuser’ AND ‘1’=’1 Which equates to “testuser and TRUE”. When registering this user, pay attention to the server reply:
User testuser’ and ‘1’=’1 already exists please try to register with a different username.
Now try registering: testuser’ AND ‘1’=’2 Which translates to “testuser and FALSE”. The server now replies:
User testuser’ and ‘1’=’2 created, please proceed to the login page.
At first I thought it literally created the user “ t estuser’ and ‘1’=’1 ” but no, it still creates only “testuser” but apparently the added 1=1 means “user already exists”, as opposed to 1=2 meaning user doesn’t exist, although it does (we already created user “testuser”).
Again, since the last slide talked about extracting the database version string with substring(database_version(),1,1)=’1 I tried tagging that on to the username instead of ‘1’=’1. Iterating through all 10 numbers for the database version, I got 2 as the only TRUE statement. Using this technique, I was able to find 2.3.4 as being the database version.
So what other kind of information can we extract using substring? I first tried ‘user’ and ‘username’, but got an error saying the string didn’t exist. ‘userid’ worked though, but I saw no need for that information. In a flash of inspiration I tried ‘password’, and lo and behold, the first letter that equated to TRUE was ‘t’:
tom’ AND substring(password,1,1)=’t
User tom’ AND substring(password,1,1)=’t already exists please try to register with a different username.
As we saw before, ‘1’=’1 equals TRUE and returns “user already exists”, so if the above command returns the same, it must equal TRUE as well. We now have the tool to extract Tom’s password!
At this point I got tired of going through all characters manually and fired up Burp and configured BURP Intruder for a sniper attack. There’s only 1 parameter to fuzz, the very last letter in the string. This is very easy to do with Intruder with the following settings:
Attack type: Sniper Payload: Brute Forcer Character set: abcdefghijklmnopqrstuvwxyz0123456789 Min length: 1 Max length: 1
To find a hit, sort the results by length. A successful hit is slightly longer than a miss.
Each time I got a hit I changed the start position of substring (2nd parameter) and ran intruder again. Within half an hour I had poor Tom’s password!
13 thoughts on “OWASP WebGoat SQL advanced lesson 5”
How did you discover the database version number? I understand that by iterating the ‘1 in testuser’ and substring(database_version(),1,1)=’1 gave you 2 but were did you discover the .3.4?
Hello! You find the subsequent numbers of the version by incrementing the second parameter of substring, i.e. substring(database_version(),2,1)=’. The syntax of substring is: SUBSTRING(string, start, length). I hope this helps!
thanky you for posting this as it’s the only resource on the internet. For database enumeration, did you use burp too?
Yeah, I used Burp Intruder back then. Now I’d probably use Burp Turbo Intruder though, it’s sooo much faster.
Please, tell how you do it with BURP? thanks!
Which part? The intruder? If you intercept the request in Burp you can right click it and send it to intruder, using the options I wrote in the article. Then you let intruder run until one of the replies indicates a hit, and change substring to the next index as I wrote in the above comment. However, you could also write your own script to automate this instead of using Burp.
How can I reset registered user information? Even if I try to register any name, it says “User tom ‘AND substring (password, 1,1) =’ ● already exists please try to register with a different username. ‘
Hmm you shouldn’t need to register any new users. The attack is done on the login form, not the register form. To completely reset WebGoat you could always just remove all its folders and run it as new. This would of course wipe your progress, too, so be careful.
Not sure what you are saying here. Your explanation is really good and helpful, thanks a lot for that, but we are attacking the register form, not the login form. Don’t you agree?
Sorry, you are right. It’s been several months since I did this exercise. Are you using a space between the quote and the AND? It’s possible it literally registers the user “User tom ‘AND substring (password, 1,1) =” and not user “tom”. Also, you are using the single quote (ASCII 0x27), right? It’s doesn’t seem like you are getting SQL injection. If none of this helps, you should try resetting WebGoat by removing all its folders though as I said, all your progress would be lost.
Your solution is excellent. Getting the idea in the first place is quite difficult. However, I wanted to ask you, how did you come up with the character set for the password? Did you just guess it? What if the password had special characters?
If the password had special characters I wouldn’t get a hit on that character position, and I’d have to expand the character set with special characters, which would make the brute forcing take longer. So it wouldn’t be any more difficult to brute force, just take longer.
This paragraph **At first I thought it literally created the user “testuser’ and ‘1’=’1” but no, it still creates only “testuser” but apparently the added 1=1 means “user already exists”, as opposed to 1=2 meaning user doesn’t exist, although it does (we already created user “testuser”).**
How did you ensured that payload “testuser’ and ‘1’=’1” is not created as user and only testuser is actually taken??
What is guessed is, first they must have checked if testuser username exist using select statment . which will always return false becoz of ‘1’=’2. so next they must have inserted user input (payload) testuser’ and ‘1’=’1 in db to create new user
Comments are closed.
NO PAIN NO GAIN
Webgoat通关流程.


IMAGES
VIDEO
COMMENTS
OWASP WebGoat: General — Lesson Solutions of HTTP Basics, HTTP Proxies & Developer Tools. This blog will help in solving lessons available in OWASP WebGoat: General — HTTP Basics, HTTP Proxies ...
This repository contains all the lessons for the WebGoat container. Every lesson is packaged as a separate jar file which can be placed into a running WebGoat server. Creating a new plugin
The following picture shows the ideal local setup for running WebGoat and following the lessons. It also shows WebWolf and how OWASP Zap can be used between the browser and OWASP WebGoat. ... (at the time of writing) is: webgoat-server-8...M23.jar. ... To access the lessons and challenges you will need to select 'Register new user' and ...
No extra installation required. In case you're wondering, here are the commands to run WebGoat in a Docker container: docker pull webgoat/webgoat-8.. docker run -p 8080:8080 -t webgoat/webgoat-8.. Inside the terminal, I copied the key with some echo commands: echo -----BEGIN PRIVATE KEY----- > private.key.
The primary goal of the WebGoat project is simple: create a de-facto interactive teaching environment for web application security. In the future, the project team hopes to extend WebGoat into becoming a security benchmarking platform and a Java-based Web site Honeypot. Learn in three steps. Explain the vulnerability
Introduction. WebGoat is a deliberately insecure web application maintained by OWASP designed to teach web application security lessons. This program is a demonstration of common server-side application flaws. The exercises are intended to be used by people to learn about application security and penetration testing techniques.
5. Look at source code of current lessons, learn how to write new lessons. 6. Write new lesson plan, implement lesson. 7. Suggest other improvements to current lessons. Background The WebGoat application contains lessons in how an attack can be performed and simulated on the local computer. As web applications are becoming more and more
Introduction. WebGoat is a deliberately insecure web application maintained by OWASP designed to teach web application security lessons. This program is a demonstration of common server-side application flaws. The exercises are intended to be used by people to learn about application security and penetration testing techniques.
WebGoat is a deliberately insecure J2EE web application designed to teach web application security lessons. In each lesson, users must demonstrate their understanding of a security issue by exploiting a real vulnerability in the WebGoat application. For example, in one of the lessons the user must use SQL injection to steal fake credit card numbers. […]
How do I solve lesson X? Subscribe to the WebGoat mailing list at [email protected]. Post your question to [email protected]. How do I contribute to the code i.e. fork/commit? Check out our instructions on Forking WebGoat in GitHub. Next Previous.
OWASP WebGoat: General section covers several topics such as HTTP Basics, HTTP Proxies, Developer Tools, CIA Triad and Crypto Basics. Valuable concepts covered in all these topics are -. A proxy ...
After having installed WebGoat, you may want to access it from another client. You can do this by launching it with the -server.address=x.x.x.x parameter. Also, if you don't want to reconfigure Burp or ZAP, -server.port=8081 allows you to run WebGoat on a different port from the default 8080 which these proxies normally use. The first 2 ...
docker run --name webgoat -it -p 127.0.0.1:8080:8080 -p 127.0.0.1:9090:9090 webgoat/webgoat. To access WebGoat, on the host machine, point the browser to https://localhost:8080/WebGoat. Important: Choose the correct timezone, so that the docker container and the host are in the same timezone. As it is important for the validity of JWT tokens ...
WebGoat 8 - Insecure Deserialization - Lesson 51. Find the path for end function code. Path:- https://github.com/WebGoat/WebGoat/blob/develop/webgoat-lessons...
About Press Copyright Contact us Creators Advertise Developers Terms Privacy Policy & Safety How YouTube works Test new features NFL Sunday Ticket Press Copyright ...
WebGoat is a powerful and widely-used tool in the realm of information security and cybersecurity. By providing a safe and interactive environment, it enables individuals to learn about web application security vulnerabilities, understand their impact, and develop mitigation strategies. Whether used for educational purposes, penetration testing ...
WebGoat SQL injection mitigation lesson 12. In the lesson for this exercise (lesson 11) WebGoat tells us that in case of ORDER BY SQL statement it is possible to check and eventually exploit the injection by substituting the ORDER BY column with a SQL statement. So we still have a TRUE and FALSE conditions where we can check for guessed values.
August 20, 2018. Last week I wrote about the OWASP WebGoat XSS lessons. Today I'd like to write a few pointers on how to solve the SQL injection (advanced) lesson 5. The goal is simple: you are presented with a login box and given a username; log in as that user. The usual username' OR '1'='1 — unfortunately doesn't work (that ...
Writing new lesson. 第一关介绍. 这个课程描述了向 WebGoat 添加新课程所需的步骤。通常,有四个步骤: 撰写内容。在 WebGoat 中,我们使用 AsciiDoc 作为格式。 创建一个课程类。 撰写 HTML 粘合页面,以便 WebGoat 知道如何显示内容。 在课程内添加一个或多个任务。
About Press Copyright Contact us Creators Advertise Developers Terms Privacy Policy & Safety How YouTube works Test new features NFL Sunday Ticket Press Copyright ...
The core distribution should include one or two examples that are suitable for copying as a starting point for a new lesson. A system property 'WebGoat-Plugins-dir' allows the user to specify where the 'plugins' directory is. If found, Webgoat will use that folder for lessons. On startup, it will expand core lessons into that folder ...
Join me as we delve into the world of WebGoat and learn the ins and outs of session hijacking. In this tutorial, we will explore the technique, discuss its r...
WebGoat is a deliberately insecure application that allows interested developers just like you to test vulnerabilities commonly found in Java-based applications that use common and popular open source components. Now, while we in no way condone causing intentional harm to any animal, goat or otherwise, we think learning everything you can about ...