Networking | Cloud | DevOps | IaC

IEEE 802.1X Authentication and Dynamic VLAN Assignment with NPS Radius Server
IEEE 802.1X Authentication and Dynamic VLAN Assignment with NPS Radius Server is an important element to networking in the real world. User location cannot be predicted as they may be at and out of a desk and up and about should they need to do so. Tying them to a local VLAN may only be helpful if they are bound to desks in those locations, although the most ideal outcome, it is not the most practical.
It is only wise to incorporate IEEE 802.1X Authentication and Dynamic VLAN Assignment with NPS Radius Server in areas where you expect different teams to come to. Meeting rooms could for a moment have the accounting group or the development group meeting there and based on the intelligent and dynamic vlan assignmnet with 802.1x authentication, users port-access are defined their appropriate vlans for their respective access to resources on the network.
How to Provision 802.1 X Authentication Step By Step With Dynamic VLAN Assignment With Windows Radius Server For 802.1x Clients.
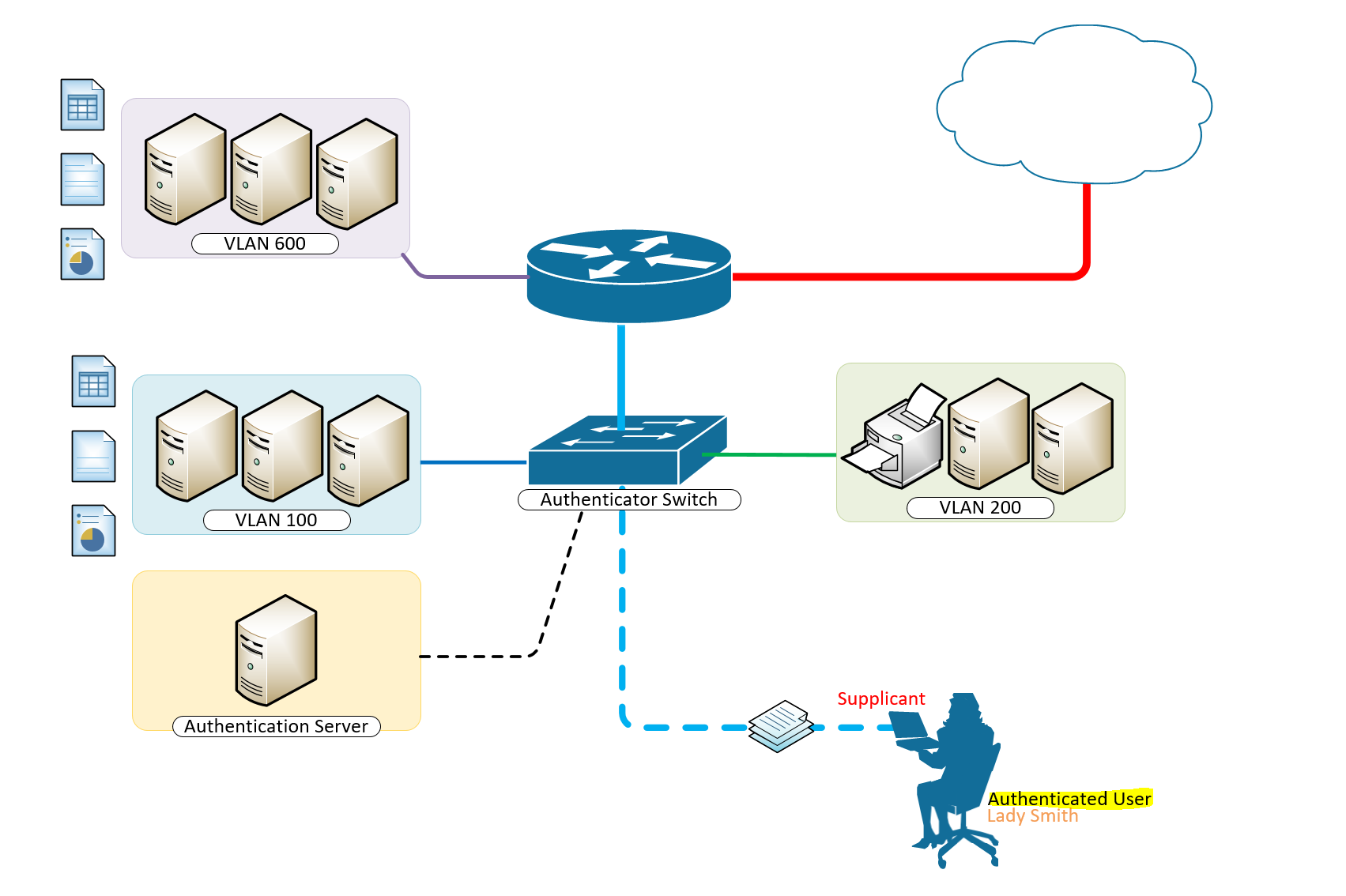
A typical configuration for a system under IEEE 802.1x Authentication control is shown in the following figure.
In this scenario, “Lady Smith” wishes to use services offered by servers on the LAN behind the switch. There are multiple VLANs with resources available based on user vlan membership. Her laptop computer is connected to a port on the Aruba 2920 Edge Switch that has 802.1x port authentication control enabled.
The laptop computer must therefore act in a supplicant role. Message exchanges take place between the supplicant and the authenticator which is the Aruba 2920 Switch, and the authenticator passes the supplicant’s credentials which is her (Windows Active Directory User Account Credentials) to the authentication server for verification. The NPS Server which is the authentication server then informs the authenticator whether or not the authentication attempt succeeded, at which point “Lady Smith” is either granted or denied access to the LAN behind the switch.
Setup Structure for IEEE 802.1X Authentication and Dynamic VLAN Assignment with NPS Radius Server
- Supplicant: Laptop running Microsoft Windows 10 or Windows 7
- Authenticator: HP Aruba 2920 Edge Switch
- Authentication Server: Microsoft NPS (Network Policy Server) running on Windows Server 2012 R2.
- User Database : Active Directory
For Windows Infrastructure
Create NPS Server – Add Role on Windows Server 2012 R2
- Create DHCP Scopes for VLANS
Create RADIUS Client on NAC using Network Policy Server
- Create Network Policies
- Configure a Network Policy for VLANs
- Start Wired Auto-Config Service
- Enable Network Authentication
Create the DHCP Scopes for VLAN100 and VLAN200 Groups
- Development Group Scope – VLAN 100
SVI: ip address 172.16.80.254 255.255.255.0 Scope Subnet: 172.16.80.1/24
- Accounting Group Scope – VLAN 200
SVI:ip address 172.16.70.254 255.255.255.0 Scope Subnet: 172.16.70.0/24
Secret Key: secret12
Add Edge Switch Management IP as the RADIUS Client
The Shared Secret Key: secret12 will be used in the Switch Configuration.
Create Network Policy Settings for Accounting Group for VLAN 200
Configuration Example
Here’s an example of how you might consider when configuring Microsoft NPS Server to assign users to a VLAN based on their user group, using NPS for the authentication and authorization of users. This configuration has worked flawlessly on the HP Aruba 2920 Switch. The key to getting this to work is the use of a RADIUS element called: ‘Tunnel-PVT-Group-ID’. This is a RADIUS attribute that may be passed back to the authenticator (i.e. the Aruba 2920 Switch) by the authentication server (i.e. Microsoft NPS Server) when a successful authentication has been achieved. There are a few other elements which need to accompany it, but this is the key element, as it specifies the VLAN number that the user should be assigned to.
The other elements that need to be returned by the NPS Server are as follows:
- Tunnel-PVT-Group-ID: 200
- Service-Type: Framed
- Tunnel-Type: VLAN
- Tunnel-Medium-Type: 802
For Client Infrastructure
On the Supplicant, Windows 7 or 10 configure the following steps on the Ethernet Adapter to enable IEEE 802.1X Authentication
For Network Infrastructure
Connect Server Infrastructure to VLAN 400
Create VLAN for Accounting Group
Create VLAN for Development Group
Create AAA Configuration on Switch for Radius Authentication
Download the Switch Configuration:
Test the IEEE 802.1X Authentication and Dynamic VLAN Assignment with NPS Radius Server
Verify Port-Access with the following user groups – VLAN 100 and VLAN 200
Think of what other clever things you can do from the information below;
Breakdown of Commands for RADIUS Authentication
Verification Commands
Thanks for reading. Please share your thoughts in the comment box below;
Published in Configuring , Design , Installing and Configuring , Networking , Security and Switching
- 802.1 x authentication step by step aruba
- 802.1 x authentication step by step cisco
- 802.1 x wireless authentication step by step
- 802.1x authentication process
- 802.1x authentication windows 10
- 802.1x authentication windows server 2012
- 802.1x certificate authentication
- assignment wlc
- cisco dot1x
- cisco ise dynamic vlan
- cisco ise dynamic vlan assignment wlc
- cisco wireless radius attributes
- configuration example
- dynamic vlan assignment cisco 2960 dynamic vlan configuration in packet tracer
- dynamic vlan assignment with windows radius server
- dynamic vlan cisco
- dynamic vlan ruckus
- meraki dynamic vlan assignment
- nps mac authentication wired
- nps policy for mac-based authentication
- radius multiple vlans
- vlan radius server
- vlan steering
- vmps server

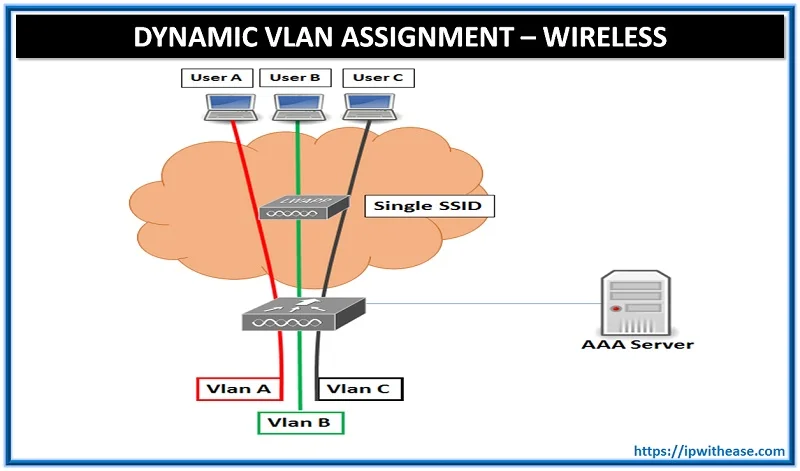
Dynamic VLAN Assignment: Wireless
Dynamic VLAN Assignment
Objective: To dynamically Assign Wireless User to VLAN based on user credentials. This type of setup is called “Dynamic VLAN Assignment”
Description: Dynamic VLAN assignment is one such feature that places a wireless user into a specific VLAN based on the credentials supplied by the user. This task of assigning users to a specific VLAN is handled by a RADIUS authentication server, such as Cisco Secure ACS. This can be used, for example, to allow the wireless host to remain on the same VLAN as it moves within a campus network.
Related- Cisco ACS vs ISE Comparison
Therefore, when a client attempts to associate to a LAP registered with a controller, the LAP passes the credentials of the user to the RADIUS server for validation. Once the authentication is successful, the RADIUS server passes certain Internet Engineering Task Force (IETF) attributes to the user. These RADIUS attributes decide the VLAN ID that should be assigned to the wireless client. The SSID ( WLAN , in terms of WLC) of the client does not matter because the user is always assigned to this predetermined VLAN ID.
WLC Configuration
This configuration requires these steps:
Configure the WLC with the Details of the Authentication Server
- Configure the Dynamic Interfaces (VLANs)
- Configure the WLANs ( SSID )
It is necessary to configure the WLC so it can communicate with the RADIUS server to authenticate the clients, and also for any other transactions.
Complete these steps:
- From the controller GUI, click Security .
- Enter the IP address of the RADIUS server and the Shared Secret key used between the RADIUS server and the WLC.
This Shared Secret key should be the same as the one configured in the RADIUS server under Network Configuration > AAA Clients > Add Entry. Here is an example window from the WLC:
Configure the Dynamic VLAN (Interfaces)
This procedure explains how to configure dynamic interfaces on the WLC. As explained earlier in this document, the VLAN ID specified under the Tunnel-Private-Group ID attribute of the RADIUS server must also exist in the WLC.
In the example, the user1 is specified with the Tunnel-Private-Group ID of 10 (VLAN =10) on the RADIUS server.
You can see the same dynamic interface (VLAN=10) configured in the WLC in this example. From the controller GUI, under the Controller > Interfaces window, the dynamic interface is configured.
- Click Apply on this window.
This takes you to the Edit window of this dynamic interface (VLAN 10 here).
Enter the IP Address and default Gateway of this dynamic interface
Note: Because this document uses an internal DHCP server on the controller, the primary DHCP server field of this window points to the Management Interface of the WLC itself. You can also use an external DHCP server, a router, or the RADIUS server itself as a DHCP server to the wireless clients. In such cases, the primary DHCP server field points to the IP address of that device used as the DHCP server. Refer to your DHCP server documentation for more information.
- Click Apply .
Now you are configured with a dynamic interface in your WLC. Similarly, you can configure several dynamic interfaces in your WLC. However, remember that the same VLAN ID must also exist in the RADIUS server for that particular VLAN to be assigned to the client.
Configure the WLANs (SSID)
This procedure explains how to configure the WLANs in the WLC.
- From the controller GUI, choose WLANs > New in order to create a new WLAN.
The New WLANs window is displayed.
- Enter the WLAN ID and WLAN SSID information.
You can enter any name to be the WLAN SSID. This example uses VLAN10 as the WLAN SSID.
- Click Apply in order to go to the Edit window of the WLAN SSID10.
Normally, in a wireless LAN controller, each WLAN is mapped to a specific VLAN (SSID) so that a particular user that belongs to that WLAN is put into the specific VLAN mapped. This mapping is normally done under the Interface Name field of the WLAN SSID window.
In the example provided, it is the job of the RADIUS server to assign a wireless client to a specific VLAN upon successful authentication. The WLANs need not be mapped to a specific dynamic interface on the WLC. Or, even though the WLAN to dynamic interface mapping is done on the WLC, the RADIUS server overrides this mapping and assigns the user that comes through that WLAN to the VLAN specified under the user Tunnel-Group-Private-ID field in the RADIUS server.
- Check the Allow AAA Override check box in order to override the WLC configurations by the RADIUS server.
- Enable the Allow AAA Override in the controller for each WLAN (SSID) configured.
When AAA Override is enabled, and a client has AAA and controller WLAN authentication parameters that conflict, client authentication is performed by the AAA (RADIUS) server. As part of this authentication, the operating system moves clients to a VLAN returned by the AAA server. This is predefined in the controller interface configuration.
For instance, if the corporate WLAN primarily uses a Management Interface assigned to VLAN 2, and if the AAA Override returns a redirect to VLAN 100, the operating system redirects all client transmissions to VLAN 100 even if the physical port to which VLAN 100 is assigned. When AAA Override is disabled, all client authentication defaults to the controller authentication parameter settings, and authentication is only performed by the AAA server if the controller WLAN does not contain any client-specific authentication parameters.
Continue Reading:
CONFIGURE INTERFACES ON WIRELESS CONTROLLER 5508
Wireless Interview Questions
ABOUT THE AUTHOR

I am here to share my knowledge and experience in the field of networking with the goal being – “The more you share, the more you learn.”
I am a biotechnologist by qualification and a Network Enthusiast by interest. I developed interest in networking being in the company of a passionate Network Professional, my husband.
I am a strong believer of the fact that “learning is a constant process of discovering yourself.” – Rashmi Bhardwaj (Author/Editor)
Related Posts
Kubernetes vs Docker : Detailed Comparison 2024

Step by Step Guide to Develop an E-commerce Website

3 Intellectual Property Threats Online and How to Avoid Them
Leave a comment cancel reply.
Your email address will not be published. Required fields are marked *
Log in to ask questions, share your expertise, or stay connected to content. Don’t have a login? Join now .

- Community Home
- Topic Thread
Wireless Access

- Discussion 120K
- Library 3.2K
- Members 2.9K

Dynamic vlan assignment with radius and Aruba Controller
1. dynamic vlan assignment with radius and aruba controller.
I would like to configure and understand how to dynamically assign vlan on one ssid by radius attribute ? With other vendor this is more easy. My environment is formed by 7240 controller and access point 135 .
Who can help me ? i don' t find a document that describe this solution.
2. RE: Dynamic vlan assignment with radius and Aruba Controller

3. RE: Dynamic vlan assignment with radius and Aruba Controller
MICROSOFT IAS
4. RE: Dynamic vlan assignment with radius and Aruba Controller
5. re: dynamic vlan assignment with radius and aruba controller.
Another way you can do this that you assign different role using that same logic I mentioned and then assign the VLAN to the role
6. RE: Dynamic vlan assignment with radius and Aruba Controller
see also Aruba-User-Vlan VSA as mentioned here by clembo
http://community.arubanetworks.com/t5/Unified-Wired-Wireless-Access/Assigning-users-different-vlan-subnet-based-on-AD-group/m-p/61082/highlight/true#M2011
7. RE: Dynamic vlan assignment with radius and Aruba Controller

Adding to the reply by Victor here are steps to configure the RAS policy for dynamic VLAN assignment.
Select New policy and give a name ( DemoPolicy)
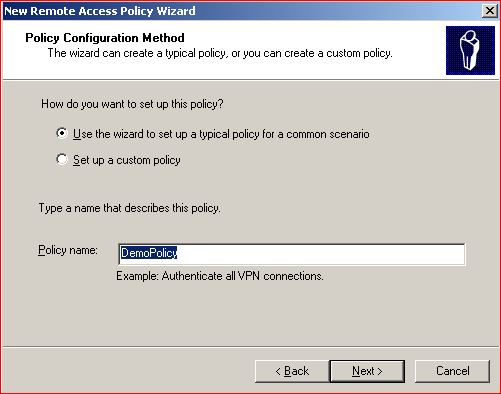
Select Wireless :
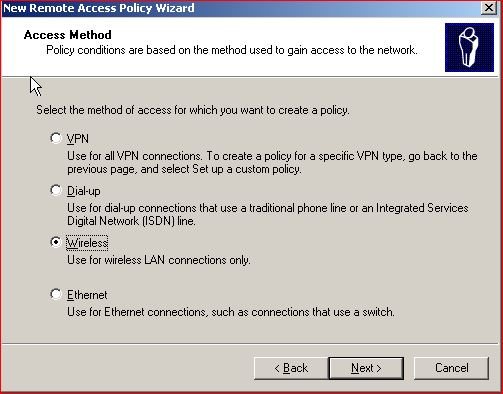
Select the user group to map this policy (Manager is a group)
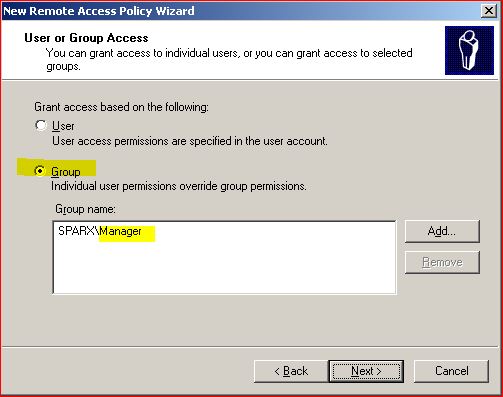
Select Grant RAS and click on Edit profile
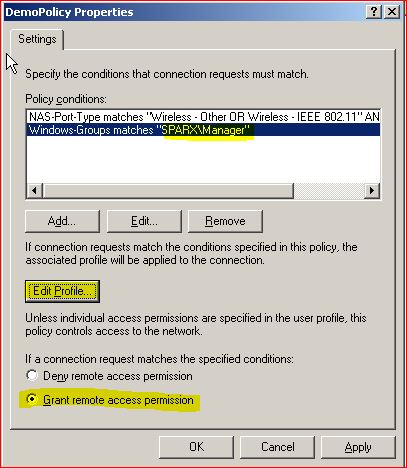
Select Advanced Tab and select Add
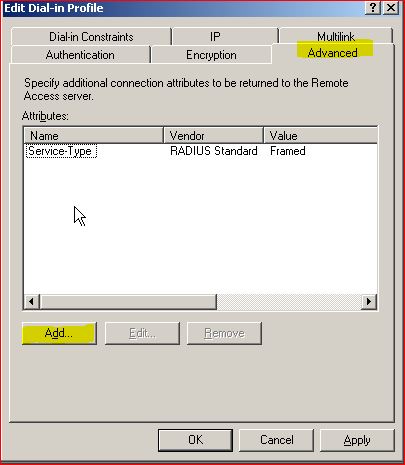
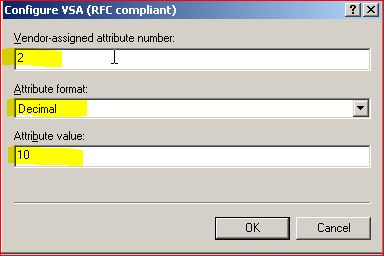
Select Attribute name as either Filterid or "Vendor specific". to make your life simple select "Vendor Specific" and click on Add.
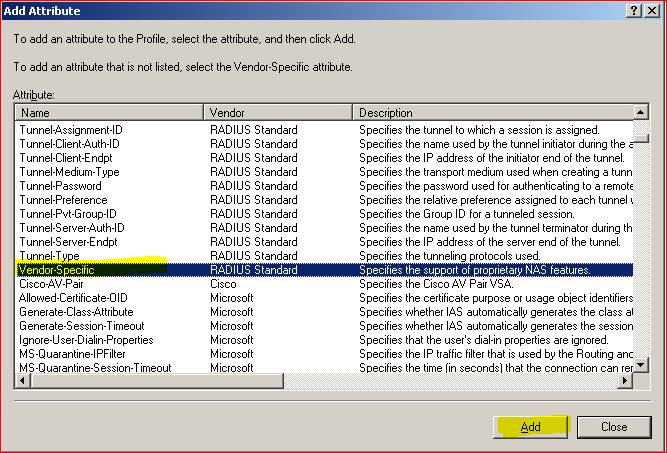
Select option, "Enter Vendor-code" the value for Aruba is 14823
Select option "It Confirms" and select "Configure Attributes"
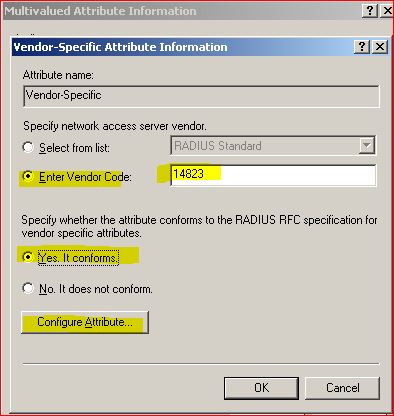
Select the appropriate value and type as shown bellow.
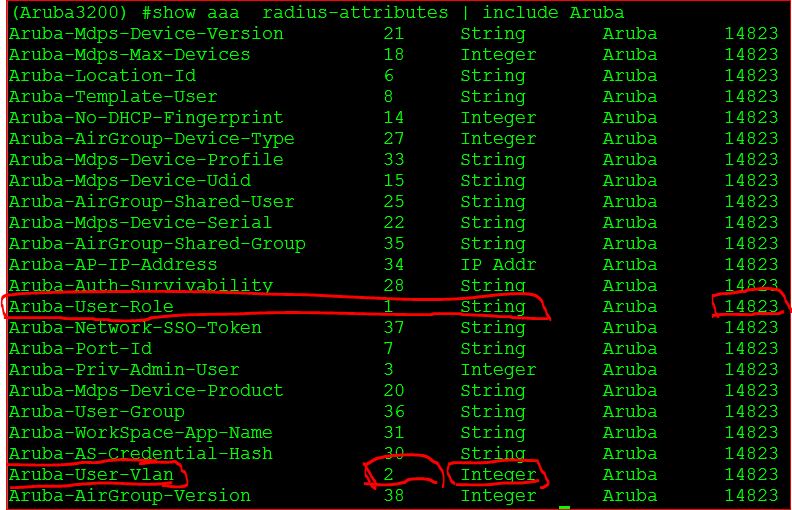
Here for returning VLAN id we should select attribute number as 2 and format as Integer (Decimal) and finally enter the vlan id as the Attribute value.
The server side configuration is done.
Now we should configure the server group to assign the return attribute ,
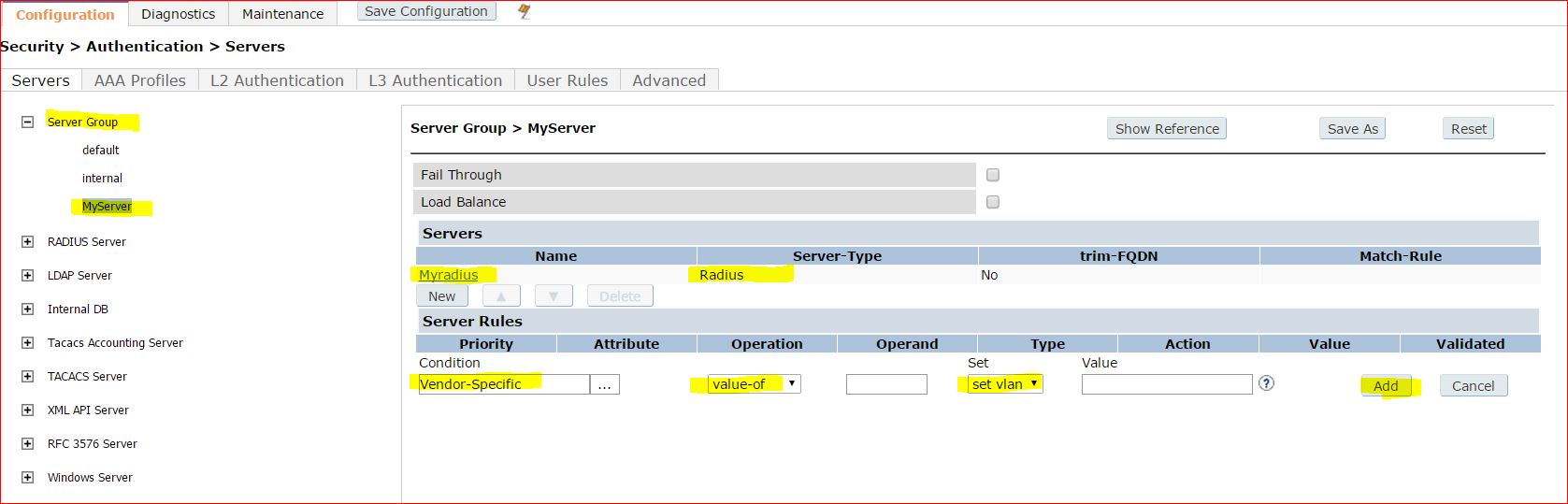
Another way is, map a VLAN to the user role and configure the IAS to return the role name
How to map a VLAN to a Role:
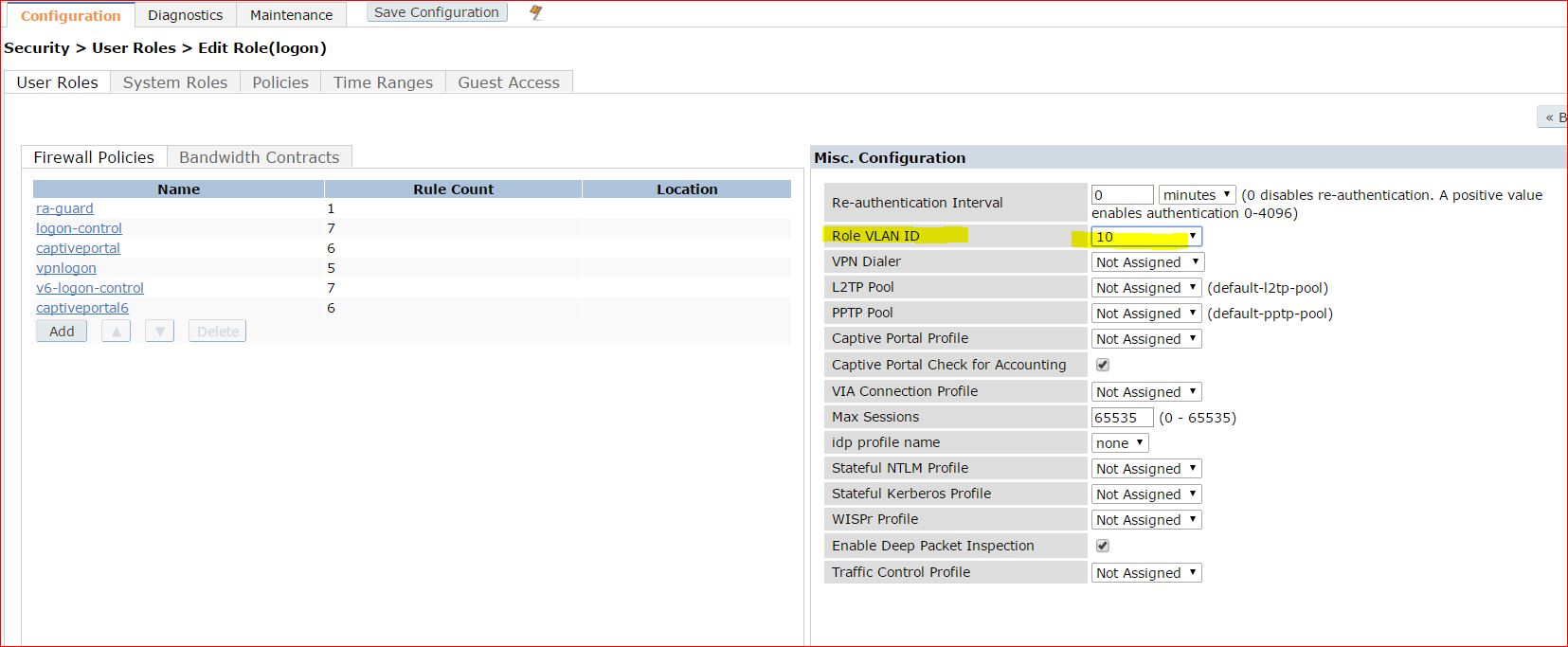
Hope got more clarity,
Please feel free for any further help on this,
Have fun with Aruba :)
8. RE: Dynamic vlan assignment with radius and Aruba Controller
i explain better :
In my environment i have different type of client, with different privilege on network, this type of client reside on many different campus (different ap group), i have many vlan pool for each campus. The radius should return the value of vlan pool not the vlan. With the configuration shown i understand that is not very flexible...
For example on cisco wlc i only enable a flag to allow aaa override.
9. RE: Dynamic vlan assignment with radius and Aruba Controller
The raiuds server sent back to controller the vlan pool, and is not flexible configure a static vlan.
10. RE: Dynamic vlan assignment with radius and Aruba Controller
Aruba supports this feature,
You can return the VLAN name through RADIUS attribute and you can have a VLAN pool with that name in the controller.
for your ref :
I just configured an attribute to return value test.
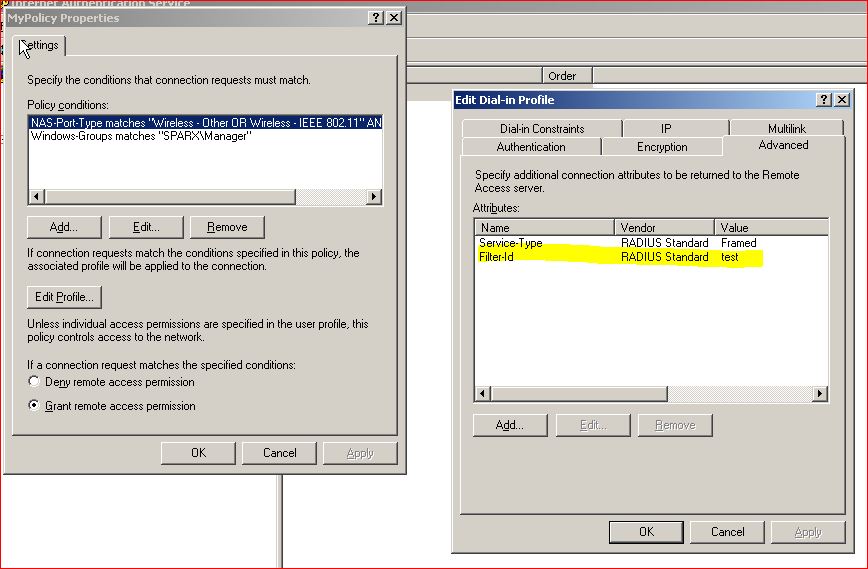
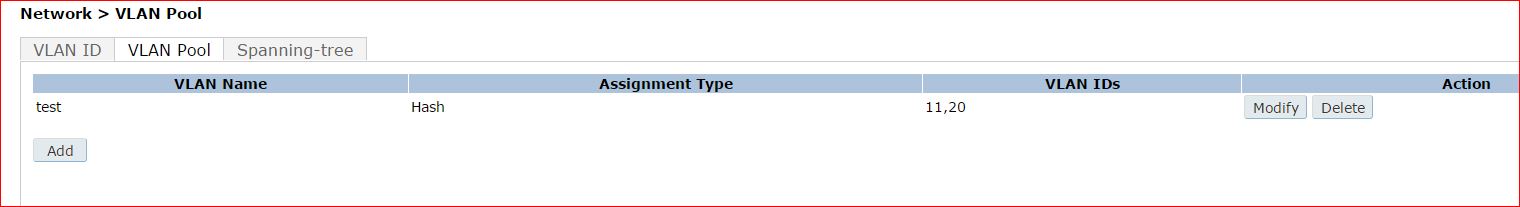
I have configured the server group to assign a VLAN pool ( test ).
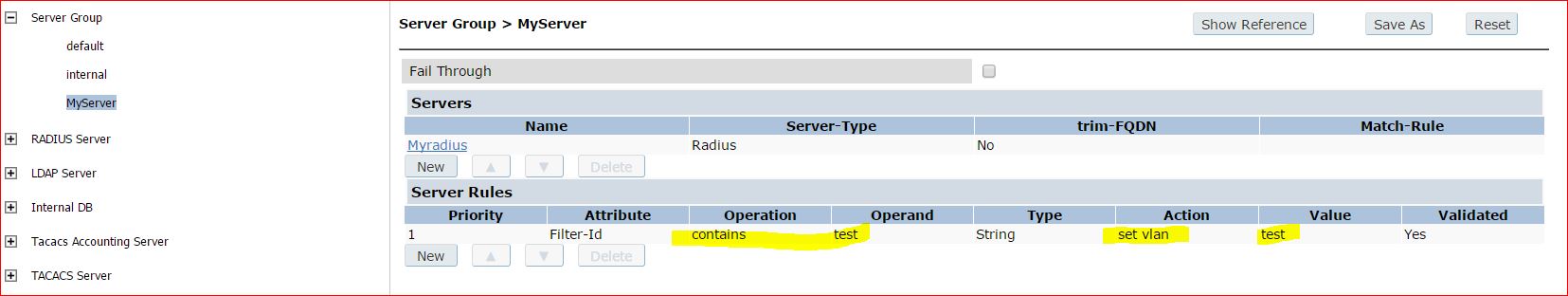
A VLAN pool with VLANs 11 and 20 :
An user got VLAN assignment through RADIUS .
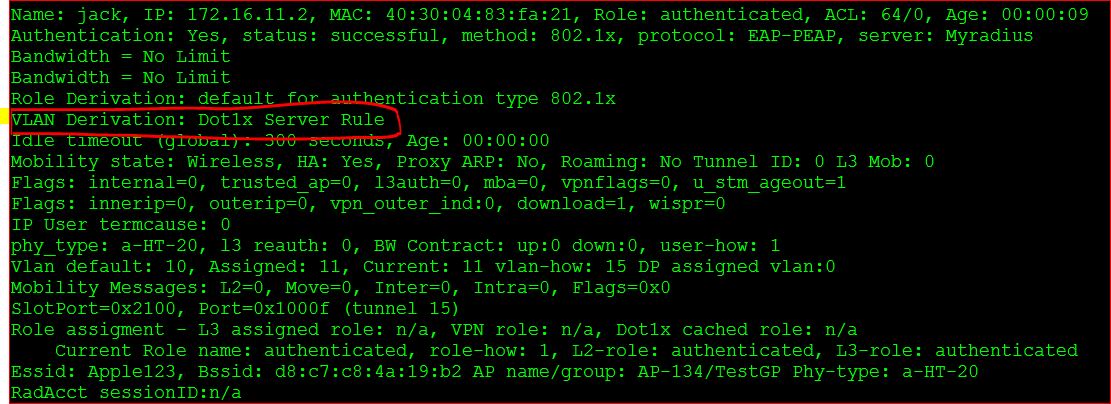
Hope it is prooved :)
Please feel free for any further help on this.
11. RE: Dynamic vlan assignment with radius and Aruba Controller
Ok, i must create a rule for each vlan pool ?? is not flexible..
12. RE: Dynamic vlan assignment with radius and Aruba Controller
Hi friend ,
Yes, we have to create policy for each user group.
Can you share your requirement so that I can give a best solution . I believe Aruba as flexible as other vendors in the market.
13. RE: Dynamic vlan assignment with radius and Aruba Controller Best Answer
Spillo4000,
Let's understand what you are trying to do:
1. - You have users that are authenticating via 802.1x
2. - You want them placed in a different VLAN or VLAN pool depending on what controller they are connected to?
If you only want to do those two things above, you would only need to:
- Create a VLAN Name or pool on the master controller ( http://www.arubanetworks.com/techdocs/ArubaOS_64_Web_Help/Web_Help_Index.htm#ArubaFrameStyles/Network_Parameters/Configuring_VLANs.htm)
- Assign that VLAN name to your Virtual AP instead of a VLAN number
- Define the value of that VLAN name/pool on each controller; the VLAN name assigned to each Virtual AP is global, but the VLAN numbers assigned to each name is local for each controller
You would be able to do it above without returning a radius attribute.
If the above is not what you want, please tell us in detail how it is accomplished with the combination of Cisco and IAS and we can give you the Aruba equivalent.
14. RE: Dynamic vlan assignment with radius and Aruba Controller
each rule for each vlan pool, is tedious..
15. RE: Dynamic vlan assignment with radius and Aruba Controller
If you have more than one pool, how do you indicate what user gets into what pool if you don't have rules? What decides who gets what pool? A rule has to be involved...
16. RE: Dynamic vlan assignment with radius and Aruba Controller
The user group mapped to a vlan pool name is configured on radius, i repeat for example on cisco wlc the vlan pool name must match from radius to controller, on controller i put only a flag to trust the vlan pool name send from radius. On aruba as well as configure radius i must create one server rule for every vlan pool, i understand correctly ? for this on my opinion it seems to be tedius.
17. RE: Dynamic vlan assignment with radius and Aruba Controller
on my server group i must create many server rule, one for each vlan pool.
18. RE: Dynamic vlan assignment with radius and Aruba Controller Best Answer
@Spillo4000 wrote: on my server group i must create many server rule, one for each vlan pool.
You do not have to create any server rules on the server. You just have to return the "Aruba-Named-User-Vlan" VSA with the name of the pool from the radius server. The client will automatically be placed into the named VLAN/Pool. Aruba Radius VSAs override any rules in a server group and they make server group rules unnecessary. As long on the radius server side you are sending back the "Aruba-Named-User-Vlan" attribute with the name of the pool, the client will be placed into that pool without creating rules on the Aruba controller side:
http://www.arubanetworks.com/techdocs/ArubaOS_64_Web_Help/Web_Help_Index.htm#ArubaFrameStyles/AAA_Servers/Configuring_Servers.htm

19. RE: Dynamic vlan assignment with radius and Aruba Controller
thank you and accept the solution.
New Best Answer

- Environmental Citizenship
- Support Services
- Contact Support
- Training & Certification
- Software Downloads
- Licensing Login
- Find a Partner
- Become a Partner
- Partner Ready for Networking
- Technology Partner Programs
- Privacy policy
- Terms of service
© Copyright 2024 Hewlett Packard Enterprise Development LP All Rights Reserved.

COMMENTS
Enter the AAA Client IP Address and Key. The IP address should be the Management Interface IP address of the WLC. Make sure that the key you enter is the same as the one configured on the WLC under the Security window. This is the secret key used for communication between the AAA client (WLC) and the RADIUS server.
IEEE 802.1X Authentication and Dynamic VLAN Assignment with NPS Radius Server is an important element to networking in the real world. User location cannot be predicted as they may be at and out of a desk and up and about should they need to do so. ... cisco ise dynamic vlan assignment wlc; cisco wireless radius attributes; configuration example;
Click the Controller tab in the menu at the top of the window, and choose Interfaces from the menu on the left. Click the WLANs tab in the menu at the top of the window, and click Create New. Enter the Service set identifier (SSID) and Profile Name and click Apply. This example usesVLAN 81for ease of understanding.
Go to the user1's Edit page. From the User Edit page, scroll down to the Cisco Airespace RADIUS Attributes section. Check the check box next to the Aire−Interface−Name attribute and specify the name of the dynamic interface to be assigned upon successful user authentication. This example assigns the user to admin VLAN.
Configure the RADIUS (IETF) attributes used for dynamic VLAN Assignment Configure the Switch for Multiple VLANs Catalyst 9800 WLC Configuration Step 1. Configure the WLC with the Details of the Authentication Server Step 2. Configure the VLANs Step 3. Configure the WLANs (SSID) Step 4. Configure the Policy Profile Step 5.
This type of setup is called "Dynamic VLAN Assignment" Description: Dynamic VLAN assignment is one such feature that places a wireless user into a specific VLAN based on the credentials supplied by the user. This task of assigning users to a specific VLAN is handled by a RADIUS authentication server, such as Cisco Secure ACS.
Configure a RADIUS Server and WLC for Dynamic VLAN Assignment - Cisco. Also, if I understand correctly, now you are evaluating products for deploying MSI. In this case, take a look at our cloud-based solution Action1 for deploying different types of software (msi and exe) on all computers on your network at the same time. Thanks for the info.
Adding to the reply by Victor here are steps to configure the RAS policy for dynamic VLAN assignment. Select New policy and give a name ( DemoPolicy) Select Wireless : ... The user group mapped to a vlan pool name is configured on radius, i repeat for example on cisco wlc the vlan pool name must match from radius to controller, on controller i ...