Change Password
Your password must have 6 characters or more:.
- a lower case character,
- an upper case character,
- a special character

Password Changed Successfully
Your password has been changed
Create your account
Forget yout password.
Enter your email address below and we will send you the reset instructions
If the address matches an existing account you will receive an email with instructions to reset your password
Forgot your Username?
Enter your email address below and we will send you your username
If the address matches an existing account you will receive an email with instructions to retrieve your username

- April 01, 2024 | VOL. 181, NO. 4 CURRENT ISSUE pp.255-346
- March 01, 2024 | VOL. 181, NO. 3 pp.171-254
- February 01, 2024 | VOL. 181, NO. 2 pp.83-170
- January 01, 2024 | VOL. 181, NO. 1 pp.1-82
The American Psychiatric Association (APA) has updated its Privacy Policy and Terms of Use , including with new information specifically addressed to individuals in the European Economic Area. As described in the Privacy Policy and Terms of Use, this website utilizes cookies, including for the purpose of offering an optimal online experience and services tailored to your preferences.
Please read the entire Privacy Policy and Terms of Use. By closing this message, browsing this website, continuing the navigation, or otherwise continuing to use the APA's websites, you confirm that you understand and accept the terms of the Privacy Policy and Terms of Use, including the utilization of cookies.
Criminal Profiling: An Introduction to Behavioral Evidence Analysis
- ROBERT T. FINTZY , M.D. ,
Search for more papers by this author
Henceforth, be forewarned: not everyone doing criminal profile work is doing it correctly. “Many dangerously unqualified, unscrupulous individuals [are in] the practice of creating criminal profiles” (p. xxix), declares Brent Turvey, which is why he wrote this book. It is his attempt at providing the solid foundation on which a standard of workmanship, ethics, definitions, practices, methodology, training, education, and peer review can be uniformly established so that criminal profiling can become a profession rather than a haphazard job for ill-prepared probers. This text documents the principles of proper criminal profiling and undertakes to establish definite criteria for professionalization.
What is criminal profiling? Whatever one has gleaned from films and fiction—with all due respect to Sir Arthur Conan Doyle and Sherlock Holmes—is misleading. The current loose definition describes criminal profiling as any process elucidating notions about a sought-after criminal. However, Turvey dismisses the popular myth that profilers are born with an intuitive gift. Instead, Turvey advocates a discipline that will necessitate the careful evaluation of physical evidence, collected and properly analyzed by a team of specialists from different areas, for the purpose of systematically reconstructing the crime scene, developing a strategy to assist in the capture of the offender, and thereafter aiding in the trial. In his schema, a criminal profiler is only one component, although an integral one, in the criminal investigation process.
Turvey differentiates between inductive and deductive criminal profiling. The former involves broad generalizations and/or statistical reasoning—a subjective approach in Turvey’s view. Turvey favors the deductive method of criminal profiling, in which the criminal profiler possesses an open mind; questions all assumptions, premises, and opinions put forth; and demands collaboration regardless of how distinguished the supplier of the input. Here, the emphasis is on the profiler’s objectivity, self-knowledge (to overcome transference distortions), and critical thinking skills—plus an ability to try to understand the needs being satisfied by each behavior of the offender as well as the offender’s patterns. Turvey places great emphasis on all forms of forensic analysis (e.g., wound analysis, blood stain pattern analysis, and bullet trajectory analysis), crime scene characteristics (including photos), victim and witness statements, and a thorough study of the characteristics of the victim—yes, the victim. He uses the crime scene characteristics to differentiate between modus operandi and “signature behaviors” (i.e., actions unique to the crime but not necessary to commit the crime), as well as to determine inferences about the offender’s state of mind at the time of the crime, his or her planning, level of skill, victim selection, fantasy, motivation, and degree of risk taken. Turvey labels his process behavioral evidence analysis and considers it objective because it is based on facts rather than averages and extrapolations from statistics. He acknowledges that criminal profiling is a skill rather than an art or science.
Turvey reminds the reader that no two cases are exactly alike; hence, the inductive method, with its “magical” quality, is great for Hollywood but is not the most effective practice. The criminal profiler’s gut instinct, unless it can be concretely confirmed, tends to lead the criminal profiler astray and wastes valuable time. Not only do criminals think differently than most people, but Turvey points out that behavior has different meanings between cultures and from region to region. Necessarily, behavioral evidence analysis must be a dynamic process, ever-changing as the successful criminal’s methods become more refined, or deteriorate, over the course of time.
As I understand it, a criminal profiler needs to be a monitor, coordinator, interpreter, and advisor to the different branches of the investigator tree—with a premium placed on facts rather than theories. The value of teamwork is crucial. Each team member must recognize the complementarity of all team members and be willing to share information. Historically, many unsuccessful investigations have been marked by a lack of interagency cooperation (secondary to politics, turf battles, etc.). Furthermore, there are differences in skill levels among team members, despite the number of years of experience. Since the criminal profile is vitiated whenever any part lacks merit, the criminal profiler must check all assumptions. Wound patterns, for example, are complex, and even well-trained medical examiners can miss and/or misinterpret them—thus, the need for multiple forensic scientists. In addition, the criminal profiler’s competency can be compromised if he or she fails to visit the crime scene.
Although forensic psychiatrists can perform clinical interviews for the purpose of diagnosis, treatment, and courtroom competency/sanity assessment, they cannot do the work of a criminal profiler. A psychiatrist can contribute to the criminal profile but is only one member of a team. The same can be said of law enforcement agents, psychologists, sociologists, medical examiners, and detectives. Far more advanced training is required to become a professional criminal profiler, training that has heretofore been nonregulated—a situation that Turvey hopes to radically change, with this book as catalyst and guide.
The sections of the book that interested me the most are diverse. The preface, where the author relates those factors which led him to become a criminal profiler, is a sensitive, well-written, personal introduction. Then, as gory as is the chapter on wound analysis (color photos included—not meant for the squeamish!), I ultimately became convinced that the minute details described by the medical examiner rank as one of the most enlightening, mind-stimulating contributing factors in the effort to weed out a killer.
Intensive case examples in the appendixes of the book provocatively exercised my own detective mind. In appendix IIA, the Jon Benet Ramsey presentation includes a detailed autopsy description that evidently had not appeared publicly and, without stating it directly, unequivocally points to a particular suspect. To my chagrin, John Douglas, a highly respected criminal consultant, certainly seems to have goofed by basing his profile solely on his own conjoint 4.5-hour interview with the parents. Appendix I details more about the “Jack the Ripper” murders than one probably is familiar with and also permitted me the opportunity to think along as an involved investigator. Appendix IIIA presents an actual behavioral evidence analysis report, 56 pages worth, that is thorough and clear.
Most of the chapters are by Turvey himself. The writing and direction are consistent throughout—with the exception of chapter 21 by U.K. psychiatrist Dr. Diana Tamlyn, which reveals a lack of knowledge about what truly constitutes a professional criminal profiler and therefore made me wonder why these nine pages were included. Most chapters are mercifully brief, thus allowing for relief and frequent respites to assimilate the information. Unique, and more helpful than traditional footnotes, are numbered asides that appear in the more-than-ample margins. Wide borders also allow for spontaneous reader’s notes, and I highly recommend this format for future books.
The chapters address investigative as well as trial strategies, ethics, alternate methods of criminal profiling, arson, serial rape/homicide, criminal behavior on the Internet, task force management, and more. This book is a text, reference source, and proselytizing attempt, all in one. A glossary, bibliography, and index abet this worthy contribution. One disappointment, though: Turvey (pp. 195, 448) incorrectly says that the only difference between a sociopath and a psychopath is that the former originates from social forces and early experiences. Not only is the etiology of both these entities unclear, but 40 years in psychiatry has taught me that the only distinction is that a psychopath commits violent crimes.
Certainly, quite a few of Turvey’s opinions are subject to controversy. For instance, in chapter 24, he attributes society’s interest in serial rape and serial homicide to venial excitement rather than considering it might be an attempt at self-protection and/or understanding for prophylactic reasons. I also object to his facile dismissal of less-than-scientific sources, such as handwriting analysis and polygraph tests, as psychological speculations. Although these have their limitations, when facts are lacking, as they often are, such intuitive offerings can prove useful. It seems to me that a conflation of both inductive and deductive criminal profiling, with the main emphasis on the latter, rather than Turvey’s idealistic unitary bias, could be practical.
Criminal Profiling is not for casual or marathon reading. It requires the concentration and diligence possible only in short spurts of study. Remarkably, the redundancy throughout the book serves a didactic function by clarifying and reinforcing important points. Psychiatrists will be interested to know that behavioral evidence analysis techniques have no clinical purpose—they are not based on an interest in an offender’s mental well-being but on the goal of protecting society. Turvey further adds, “Freudian theories…are not designed for investigative purposes” (p. 237). The primary goals of criminal profiling include the reduction of the viable suspect pool in a criminal investigation, assistance in the linkage of potentially related crimes, assessment of the potential for escalation of criminal behavior, provision of relevant leads and strategies, and keeping the investigation on track. The criminal profiler is not preoccupied with specifically naming the offender. Criminal profilers are advisors; detectives and investigators solve cases.
This book should be reviewed by anyone intent on becoming a professional criminal profiler. It would also be a good idea if such an aspirant possessed an ample cache of compulsive traits because the efficient criminal profile has to be so meticulous. The material contained in this book is only a beginning; prolonged first-hand investigatory experience under an expert’s tutelage is mandatory.
Criminal Profiling would be of value to psychiatrists in two respects: 1) as a humbling experience in terms of recognizing the limitations of a psychiatrist in a criminal investigation and 2) as an intellectual expansion for those with polymathic proclivities.
By Brent Turvey, M.S. San Diego, Academic Press, 1999, 451 pp., $79.95.
- Cited by None

An official website of the United States government
The .gov means it’s official. Federal government websites often end in .gov or .mil. Before sharing sensitive information, make sure you’re on a federal government site.
The site is secure. The https:// ensures that you are connecting to the official website and that any information you provide is encrypted and transmitted securely.
- Publications
- Account settings
Preview improvements coming to the PMC website in October 2024. Learn More or Try it out now .
- Advanced Search
- Journal List
- Psychiatr Psychol Law
- v.28(5); 2021

Reframing criminal profiling: a guide for integrated practice
Wayne petherick.
a Criminology Department, Faculty of Society and Design, Bond University, Gold Coast, QLD, Australia
Nathan Brooks
b School of Health, Medical and Applied Sciences, Central Queensland University, Townsville, QLD, Australia
Profiling aims to identify the major personality and behavioural characteristics of offenders from their interactions in the crime. The discipline has undergone numerous changes and advances since its first modern use by the psychological/psychiatric community. The current paper reviews the different approaches to criminal profiling, exploring the reasoning and justification utilised across profiling practices. Profiling aims to assist criminal investigators; however, the variance in profiling approaches has contributed to inconsistency across the field, bringing the utility of profiling into question. To address the current areas of practice deficit in criminal profiling, a framework is proposed to promote integrated practice. The CRIME approach provides a framework (consisting of crime scene evaluations, relevancy of research, investigative or clinical opinions, methods of investigation, and evaluation) to promote structure and uniformity in profile development, aiming to assist in the reliability of the practice by providing an integrative framework for developing profiles.
In its most basic form, criminal profiling (also known as offender profiling and behavioural profiling, among others) is an investigative tool to discern offender characteristics from behaviour. This base understanding is common to most, if not all, approaches to profiling, with the main difference between practices being the reasoning and decision-making processes used to arrive at the final profile (Petherick, 2014a , 2014b ). Despite the level of scientific reasoning being notably different across the approaches, there has been little attempt to understand what this reasoning is and how it impacts on profile content. Profiling has been subject to discrepancies across practice, with a dearth of processes or principles to promote integrated practice. There have, however, been many attempts to understand more advanced aspects of profiling such as the accuracy of one group over another (Kocsis et al., 2000 ; Pinizzotto & Finkel, 1990 ), or the assistance offered by profilers to end consumers (Cole & Brown, 2011 ; Copson, 1995 ), mental health professional’s attitudes to profiling (Torres et al., 2006 ) and the operational utility of offender profiling (Gekoski & Gray, 2011 ).
Criminal profiling details the characteristics of the likely perpetrator of a given crime. Far from having an abstract relationship to criminal profiling, logic is pivotal to constructing rational and robust arguments about offender characteristics, not only in the profile itself but also in the communication of the elements of the profile to consumers. Indeed, devoid of any logical process, conclusions about the offender remain nothing more than unfounded assumption or ill-informed guesswork. The type of logic reasoning employed by the profiler is the most fundamental difference between approaches, and it is critical to consider the different types of reasoning employed across profiling practices. Logic, the process of argumentation, is defined by Farber ( 1942 , p. 41) as ‘a unified discipline which investigates the structure and validity of ordered knowledge’. Further, according to Battacharyya ( 1958 , p. 326):
Logic is usually defined as the science of valid thought. But as thought may mean either the act of thinking of the object of valid thought, we get two definitions of logic: logic as the science (1) of the act of valid thinking, or (2) of the objects of valid thinking.
Stock ( 2004 , p. 8) adopts a different approach:
Logic may be declared to be both the science and the art of thinking. It is the art of thinking in the same sense that grammar is the art of speaking. Grammar is not in itself the right use of words, but a knowledge of it enables men to use words correctly. In the same way a knowledge of logic enables men to think correctly or at least to avoid incorrect thoughts. As an art, logic may be called the navigation of the sea of thought.
It is the purpose of logic to analyse the methods by which valid judgements are obtained in any science or discourse, which is met by the formulation of general laws dictating the validity of judgements (Farber, 1942 ). More than simply providing a theoretical framework for structuring arguments, the basic principles of logic allow for a more rigorous formulation and testing of any argument. A better understanding of this theoretical framework provides a better understanding of the processes employed by the profiler, as well as the discipline itself. Additionally, the difference in the ways that profiles are argued is of great practical importance (Goldsworthy, 2001 , p. 30):
One important factor that should be considered is how acceptable the method of profiling is to those who will be using the profile. . . . Like any product, the profile must be end-user friendly. Few law enforcement personnel have qualifications in psychology or related disciplines, and it is this very fact that can make investigators dubious as to how conclusions presented in the profile were reached. For instance, a claim that a particular type of serial murderer will be 40 years old, white and a blue collar worker will be treated with derision by investigators unless it can be shown how that conclusion was reached, and further that the conclusion is likely to be true.
Goldsworthy argues two key points: first, that logic and reasoning should be employed in the construction of the profile, and, second, that the logic and reasoning employed be clearly elucidated throughout. While it should stand to reason that logic and reasoning should be used in profiling, we use the term in a more formal sense to move the process away from such idiosyncrasies as ‘intuition’ or ‘common sense’.
There are primarily three types of logic used in developing profiles: induction, abduction and deduction. Rather than representing different types of logic, these are best thought of as different points along the logical continuum, beginning with various hypotheses about what may have occurred or that may be true (induction), and through the scientific method we falsify each conclusion until we are left with the best possible explanation (abduction) or only one that is based on universal laws or principles and cannot be falsified (deduction). Sometimes, because of the nature of human behaviour, evidence dynamics or active attempts to thwart the investigation (referred to as staging, among others), we are left with the best explanation for the evidence we are observing – that is, abduction.
An inductive argument is where the conclusion is likely or a matter of probability based on supporting premises, such as physical evidence or research. While a good inductive argument provides strong support for the conclusion, the argument is still not infallible. For example, in research on behavioural consistency, Bateman and Salfati ( 2007 ) found that hiding the body occurred 67.8% of the time, and that moving the body after the homicide occurred in 61.1% of the time. While cited as high-frequency behaviours, these results suggest that each will only be found approximately two thirds of the time. As a result, investigators using a profile that reports such statistical inferences may equate probability with certainty. However, these behaviours occur in some cases and not others, raising an issue with both the utility of this information and in determining where offending behaviour is consistent and inconsistent with research. This may be especially true in cases where the level of certainty is communicated in a vague or general way, such as ‘most of the time the body will be hidden’. While technically true, this argument does not communicate the exact level of certainty.
Induction proceeds from a specific set of observations to a generalisation known as a premise, and the premise is a working assumption (Thornton, 1997 ). From observations in each case, comparisons are made to determine the level of similarity to past cases sharing similar features. These similarities provide generalisations that may then be offered as a conclusion in the current case. For example, a woman is found murdered, and a generalised conclusion is reached that the suspect is likely to be male, due to male offenders perpetrating between 85–90% of homicides (Federal Bureau of Investigation [FBI], 2002 ; Mouzos, 2005 ). The central premise in induction is similarity, where analysis of unlawful activity reveals that criminal activity often has common features (Navarro & Schafer, 2003 ). The application of inductive logic where the similarity is drawn from research on criminal behavioural patterns can be appreciated through the following (Kocsis, 2001 , p. 32):
To use this model to produce a psychological profile, behaviours from any of the [behaviour] patterns are compared and matched with those of the unsolved case. Once a behaviour pattern has been matched with the unsolved case it can be cross referenced with offender characteristics.
Abduction is a style of reasoning that could be summed up as reasoning to the best explanation (Davis et al., 2018 ). That is, the evidence in a case is more indicative of a single hypothesis from a number of possible hypotheses, though not inclusive of one to the exclusion of all others. According to Niiniluoto ( 1999 ) this type of reasoning has been the staple heuristic method of classical detective stories, and ‘the logic of the “deductions” of Sherlock Holmes is typically abductive’ (p. S441).
Deduction relies on induction, where hypotheses are drawn based on case similarities and are then tested against the evidence in the current case. Offender characteristics are arrived at through a systematic study of the patterns and themes present in the physical and behavioural evidence, where if the premise is true, the conclusion must also be true (Bevel & Gardner, 2008 ). Neblett ( 1985 , p. 114) goes further, stating that ‘ if the conclusion is false, then at least one of the premises must be false ’. For this reason, when employing a deductive approach, it is incumbent on the profiler to establish the validity of each and every premise before drawing conclusions from them.
Because a deductive argument is structured so that the conclusion is implicitly contained within the premise unless the reasoning is invalid, the conclusion will follow as a matter of course. Put another way, a deductive argument is designed to go from truth to truth. A deductive argument will therefore be valid if (Alexandra et al., 2002 , p. 65):
- It is not logically possible for the conclusions to be false if the premises are true.
- The conclusions must be true, if the premises are true.
- It would be contradictory to assert the premises yet deny the conclusions.
In profiling, deduction relies upon the scientific method which is a ‘reasoned step by step procedure involving observations and experimentation in problem solving’ (Bevel, 2001 , p. 154). Induction, abduction and deduction relying on the scientific method go hand-in-hand in criminal profiling: theories are developed based on research and experience (induction), which are then examined in light of the current case to determine which may or may not be true given the available evidence (abduction), and attempts are then made to falsify those that remain through hypothesis testing and revision (the scientific method that in ideal scenarios would lead to deduction). Only when theories have withstood this process of falsification can they be considered complete, and that a truth has been determined.
While there is no conclusive data on the commonality and occurrences of profiling practices, it would make reasoned sense to suggest that induction is the most common, given that many approaches rely on statistics or case experience in developing the final profile. Furthermore, induction is the foundation for both abduction and deduction. Owing to the nature of crime scenes and criminal behaviour and the lack of universal principle in human behaviour overall, deduction would be considered the least common type of reasoning, making abduction second by default. Although deduction is concerned with absolutes, abduction centres on probable reasoning derived through hypothesis testing. Hence, in abductive reasoning, conclusions are reached without the reliance on a definitive cause, instead determined based on the likelihood, feasibility and practicality of a given hypothesis. According to Niiniluoto ( 1999 ), in consideration of Pierce’s ( 1898 ) position on an abductive argument, the following is concluded (p. S439):
- The surprising fact C is observed.
- But if A were true, C would be a matter of course.
- Hence, there is reason to suspect that A is true.
The use of abductive reasoning is common practice in the clinical process of differential diagnosis, along with providing the underpinnings for crime assessment and profile development (Davis et al., 2018 ; Rainbow & Gregory, 2011 ). As Davis et al. ( 2018 ) observed, ‘profilers should take time to argue against their opinions and consider alternate hypotheses (p. 187–206). Consequently, the current review intends to examine the reasoning and decision making employed across offender profiling. The major profiling practices are discussed, and the utility of these approaches explored. As noted by Fox and Farrington ( 2018 ), ‘there appears to be substantial variation in what is considered to be OP [offender profiling], who is conducting it, the methodology and approach that is used, the findings that are achieved, as well as where and how the results are presented’ (p. 1248). The significant differences amongst approaches to offender profiling, along with widespread disputes between practitioners, have greatly impeded the field (Fox et al., 2020 ). These limitations have caused scepticism about the investigative utility of profiling, along with the scientific efficacy of the practice (Fox et al., 2020 ). For offender profiling to have scientific validity and more widespread recognition in investigations and admissibility in court, a uniformed approach to practise remains essential (Fox & Farrington, 2018 ; Freckelton, 2008 ). The current review contends that for profiling to be recognised as a scientific and evidence-based tool, homogeny in practice must be achieved, best viewed through an integrative approach to offender profiling.
Profiling approaches
While there is considerable overlap between practitioners and how they approach the development of a profile, there are also significant differences. Whether these constitute enough to be considered different methodologies is currently a subject of debate, with some suggesting that differences are more about emphasis on various parts of the process (Davis et al., 2018 ).
Criminal investigative analysis
Owing to its depiction in film and television, perhaps the best known profiling approach would be that developed by the FBI. Criminal investigative analysis, or CIA, is inductive and abductive with its roots in early law enforcement attempts to understand patterns of criminal behaviour. Early CIA thinking allocated offenders to one of two types: The organised asocial and the disorganised nonsocial, with these terms first appearing in The Lust Murderer in 1980 (see Hazelwood & Douglas, 1980 ). Between 1979 and 1983, FBI agents interviewed offenders in federal custody (see Burgess & Ressler, 1985 ) to formalise this taxonomy and determine whether there were consistent features across offences that may be useful in classifying future offenders (Petherick, 2014a ). At these early stages, the FBI method employed this organised/disorganised typology as a decision process model, which classifies offenders by virtue of the level of sophistication, planning and competence evident in the crime scene. According to the study’s authors, ‘the agents involved in profiling were able to classify murders as either organised or disorganised in the commission of their crimes ’ further noting that ‘ because this method of identifying offenders was based largely on a combination of experience and intuition, it had its failures as well as its successes’ (Burgess & Ressler, 1985 , p. 3). Indeed, the study’s two quantitative objectives were to first identify whether there are crime scene differences between organised and disorganised murderers and second to identify variables that may be useful in profiling sexual murderers for which organised and disorganised murderers differ. However, Douglas et al. ( 1986 ), acknowledged that profile development did not solely rely on a classification of organised or disorganised, explaining that profiles are derived through ‘the classification of the crime, its organised/disorganised aspects, the offender’s selection of a victim, strategies used to control the victim, the sequence of the crime, the staging (or not) of the crime, the offender’s motivation for the crime and the crime scene dynamics’ (p. 412).
An organised crime is one with evidence of planning, where the victim is a targeted stranger, where the crime scene reflects overall control, restraints are used, and there are aggressive acts prior to death. This suggests the offender is organised with the crime scene being a reflection of personality; they will generally be above average intelligence, be socially competent, prefer skilled work, have a high birth order, have a controlled mood during the crime, and are more likely to use alcohol (Douglas & Burgess, 1986 ; Ressler et al., 1992 ). Conversely, a disorganised crime shows spontaneity, where the victim or location is known, the crime scene is random and sloppy, there is sudden violence, minimal restraints are used, and there are sexual acts after death. This is again suggestive of the personality of the offender, with a disorganised offender being below average intelligence and socially inadequate, and having lower birth order, anxious mood during the crime and minimal use of alcohol or drugs (Douglas & Burgess, 1986 ; Ressler et al., 1992 ). Despite having discrete classifications, it is generally acknowledged that no one offender will fit so neatly into either type, with most being categorised as ‘mixed’ – that is, having elements of both types. The FBI dichotomy has received criticism from some practitioners (Canter et al., 2004 ; Canter & Heritage, 1990 ; Canter & Youngs, 2003 ), and there have been limited empirical findings published by the FBI in relation to practice changes (Fox & Farrington, 2018 ). One exception to this was the study conducted by Morton et al. ( 2014 ), who observed that ‘Dichotomous typologies by their very nature have challenges, as an “either/or” choice, cannot possibly explain complex, multiple event human interactions’ (p. 5). Further to this, Morton and colleagues suggested that profiling should serve as a tool that provides law enforcement investigators with investigative information, rather than providing classifications from predetermined categories or cumbersome typologies.
Diagnostic evaluations
Diagnostic evaluations do not represent a single profiling method per se but are instead a generic description of the services offered by mental health professionals, and largely rely on clinical judgement (Bradley, 2003 ). The profile provided by psychiatrist Dr James Brussel in 1956 to assist in the ‘Mad Bomber’ case is by far the most famous example of this approach to profiling (Brussel, 1968 ). In the early stages of profiling, the diagnostic and clinical approach occurred on an as-needed basis (Wilson et al., 1997 ), usually as one part of a broad range of psychological services. The contribution of mental health experts to investigations took shape when various police services asked whether clinical interpretations of unknown offenders might help in identification and apprehension (Canter, 1989 ). Even though other methods have come to the fore, largely eclipsing these early contributions, at the time of publication, Copson ( 1995 ) claimed that over half of the profiling done in the United Kingdom was by psychologists and psychiatrists using a clinical approach. In an early study of the range of services offered by police psychologists, Bartol ( 1996 ) found that, on average, 2% of the total monthly workload of in-house psychologists was spent on profiling, and that 3.4% of the monthly workload of part-time consultants was spent on profiling. Interestingly, despite diagnostic evaluations being among the earliest approaches, research on the attitudes of clinical practitioners revealed scepticism of profiling as a whole. For example, Bartol ( 1996 ) found that 70% of those questioned did not feel comfortable giving this advice, and felt that the practice was questionable. What is more (Bartol, 1996 , p. 79):
One well-known police psychologist with more than 20 years of experience in the field, considered criminal profiling ‘virtually pointless and dangerous’. Many of the respondents wrote that much more research needs to be done before the process becomes a useful tool.
Torres et al. ( 2006 ) show similar disdain for the practice. Of the 161 survey respondents, 10% had profiling experience, and 25% considered themselves knowledgeable of the practice. Less than 25% considered the practice to have sufficient scientific reliability or validity. However, despite this, many respondents also considered profiling a useful tool for law enforcement. In examining their role in profiling, McGrath ( 2001 , p. 321) suggests that clinicians may be well suited to the profiling process, owing to the following reasons:
- Their background in the behavioural sciences and their training in psychopathology place them in an enviable position to deduce personality and behavioural characteristics from crime scene information.
- The forensic psychiatrist is in a good position to infer the meaning behind signature behaviours.
- Given their training, education, and focus on critical and analytical thinking, the forensic psychiatrist is in a good position to ‘channel their training into a new field’.
Despite supporting this role, McGrath ( 2001 ) also notes that the clinician should be careful not to get caught up in, or focus too heavily on, treatment issues. This role confusion may come about because those conducting diagnostic evaluations may not often be exposed to the needs and wants of investigations, having little experience in reviewing crime scene data or witness depositions (West, 2000 ). However, the diagnostic evaluation approach to profiling has largely changed since these empirical studies were conducted during the 1990s through to the early 2000s. There has been an uprising in specialised police roles requiring registration as a psychiatrist or psychologist along with knowledge or experience in law enforcement investigations (e.g. see below a description of behavioural investigative advice). Consequently, the clinical and diagnostic approach to profiling is now embedded in specialised police positions, rather than in general forensic psychology and psychiatry practice.
Investigative psychology
Investigative psychology (IP) employs scientific research and is largely dependent on the empirical analysis conducted on individual crime types. Because IP relies more on empirical research than other inductive methods, strengths of this approach to practice are evident. However, a considerable issue in the use of applying this process to developing a criminal profile is the potential variance that may arise between profilers in determining the details of the crime and the applicability of relevant or suitable research. Furthermore, reliance on research may mean that crimes of extreme violence or low frequency may not be adequately researched to base a profile on. As with CIA, IP identifies profiling as only one part of an overall approach (Canter, 2000 , p. 1091):
The domain of investigative psychology covers all aspects of psychology that are relevant to the conduct of criminal and civil investigations. Its focus is on the ways in which criminal activities may be examined and understood in order for the detection of crime to be effective and legal proceedings to be appropriate. As such, investigative psychology is concerned with psychological input to the full range of issues that relate to the management, investigation and prosecution of crime.
Canter ( 2011 ) discussed the action–characteristics equation, whereby crime scene actions are followed by a process of deriving inferences, resulting in the identification of offender characteristics. The stage of inference development employs empirical procedures and a conceptually driven approach to establish actions and characteristics. The inference process seeks to examine interpersonal style, emotions, intellect, knowledge and familiarity, and skills. Upon analysis, conclusions are provided regarding the salience of the crime, case linkage, offender characteristics and based location. At the cornerstone of the IP approach to profiling is advanced statistical modelling and facet theory, forming both the empirical and conceptual approaches to IP practice (Canter & Youngs, 2003 ; Davis et al., 2018 ). However, although IP empirical research has provided a substantial contrition to profiling and investigating the nuanced aspects of offending, there is contention in regard to whether IP constitutes an individual approach to profiling, or instead an essential step in the provision of a profile (Davis et al., 2018 ; Rainbow et al., 2014 ; Snook et al., 2010 ).
Behavioural evidence analysis
The literature on behavioural evidence analysis (BEA) identifies that when rigorously applied to a criminal investigation the method aims to be largely deductive in nature; however, it should be noted than an absence of universal principles in the behavioural sciences renders this more an ideal than a reality. Additionally, given the reliance of deductive logic on inductive theories and the scientific method, it would be wrong to classify the method as wholly deductive. The theory of BEA states that conclusions about the offender should not be rendered unless specific physical evidence (based on a detailed crime reconstruction) exists. In BEA, the profiler spends a great deal of time establishing the veracity and validity of the physical evidence and its relationship to the criminal event. Indeed, this focus on detail is listed by some as a problem with the practice, specifically that deductive approaches are time consuming and provide limited information to investigators (see Holmes & Holmes, 2002 ).
Like many approaches, BEA is composed of steps or stages. The first, forensic analysis , refers to the examination, testing and interpretation of any and all physical evidence (Petherick & Turvey, 2008 ). To be able to understand any behavioural evidence, a full and complete reckoning of the physical evidence must be undertaken. Victimology , the second stage, examines any and all victim-related information such as height, sex, age, hobbies, habits and routines. Information derived during this stage can also help determine victim risk and target selection. Crime scene characteristics seeks to establish the distinguishing features of the crime scene, including the method of approach and attack, the method of control, location type, nature and sequence of any sexual acts, materials used, precautionary acts and verbal activity (Petherick & Turvey, 2008 ).
Offender characteristics , the final stage, assesses all of the above information for themes that collectively suggest personality or behavioural characteristics of the offender. In contrast to other approaches, BEA proposes a smaller number of characteristics that can be definitively established, including knowledge of the victim, knowledge of the crime scene, knowledge of methods and materials, criminal skill and motive (see Petherick, 2014a ).
Behavioural investigative advice
In the early 2000s, a new method of supporting police investigation known as behavioural investigative advice (BIA) emerged in the United Kingdom. The BIA discipline seeks to offer a broad range of psychological and scientific assistance to police investigations, including, but not limited to offender profiling (Rainbow et al., 2014 ). The role of BIAs is to offer senior investigative officers extra support and enhance their decision making during serious crime investigations through the use of behavioural science theory, research and expertise (Davis et al., 2018 ). The use of BIAs to assist investigations is considered to be positive and an essential step in incorporating specialised expertise into policing. However, in considering offender profiling, it is unclear as to the processes that BIAs use in assisting investigations and developing profiles. It would seem that BIA is a distinct profession, rather than a variation in profiling practice (Davis et al., 2018 ). Although research presented by BIAs has proposed the use of decision-making models (see Alison et al., 2003 ) to reach profile conclusions, the standards of evidence required for a BIA to develop a profile appears varied. An example of the decision making employed in BIA profiles was provided by Alison et al. ( 2003 ) who proposed the application of Toulmin’s ( 1958 ) philosophy of argument. The principles of applying this structure of argument to profiling was due to ‘the need for the justificatory functioning of substantive argument, whilst also being aware of the limitations of formal deductive, decontextualized logic for practical, ‘real world’ issues’ (Alison et al., 2003 , p. 174). In applying these principles to derive a profile, a profile statement must be derived from backing, warrant, grounds, modality and the consideration of rebuttal. The application of structured argument and evidence-based consideration in a profile is considered to be paramount to scientific practice and demonstrates support for the BIA discipline. BIA appears to be a progressive approach to criminal profiling and has received empirical recognition through a developing body of research (Alison et al., 2010 ; Almond et al., 2011 ; Marshall & Alison, 2011 ). For example, studies have reported positive police satisfaction with BIA involvement in cases and recommendations (Almond et al., 2011 ; Cole & Brown, 2011 ). The development of BIA practice is considered promising for both profiling and investigative assistance; however, the discipline would benefit from further scientific scrutiny in relation to operational approaches. The use of principles to derive a structured argument is essential in profiling, yet the development of a supported argument is only part of the required decision-making processes for producing a profile, with considerable degree and variation possible without a standardised practice framework. BIA is a progressive discipline, although subject to fallibility without process prioritisation and practice uniformity.
Towards integrated practice in criminal profiling
The variation across profiling practices has resulted in inconsistencies emerging in relation to the reliance on evidence, conclusions provided and the investigative utility of profiles (Almond et al., 2011 ; Fox et al., 2020 ). This has ranged from profiles providing statements without justification or the possibility of falsification, being derived predominantly on research conclusions, dismissing inconsistencies in a case, preferencing typology characteristics, omitting victimology evidence, selectively reporting confirmatory evidence, being provided verbally and without documentation, and failing to evaluate all case materials (Almond et al., 2011 ; Morton et al., 2014 ; Petherick & Brooks, 2014 ; Petherick & Ferguson, 2010 ; Turvey, 2012 ; Wilson et al., 1997 ). Each approach is characterised by strengths and weakness. For example, the linking of crime scene evidence with valid conclusions as evident in the BEA method provides scientific efficacy; however, this method can also be limiting, offering a narrow profile and minimal investigate assistance. According to Alison et al. ( 2003 ), the success of a profile is dependent on the types of conclusions provided, rather than the method used to derive these. For substantiated conclusions in profiles, there must be evidence of logical argument and pragmatic utility, ensuring conclusions are both logical and practical (Alison et al., 2010 ; Almond et al., 2011 ). Any conclusion/statement provided in a profile must have grounding, warrant, veracity and the capacity for falsification consistent with principles of the structure of argument (Toulmin, 1958 ). The grounding of the argument must be supported by scientific knowledge, whilst the warrant of the argument must permit this to be demonstrated in specialised research. In relation to veracity, there must be a form of specification in regard to the likelihood or probability of the claim occurring, whilst falsification must be possible, ensuring that that the statement or claim can be tested or disproven (Alison et al., 2003 ; Toulmin, 1958 ). Along with the profiles being derived from evidence and grounded in logical conclusions, statistical regularities between the types of offence and the types of offender characteristics can offer further investigative utility (Fox et al., 2020 ). As Fox and Farrington ( 2018 ) state, ‘all future profiles should be developed using a solid empirical approach that relies on advanced statistical analysis of large data sets’ (p. 1263). Consequently, it appears that the discipline of criminal profiling would benefit from an integrated approach to practice that provides a framework for the provision of profiles. An integrated framework serves to support the strengths of each methodology, whilst providing a structured guide to profile development. The current issues pertaining to profiling are akin to the limitations identified with the early generation of psychological risk assessments, with a need to integrate empirical findings, practitioner expertise and processes of practice. The issues in the field of risk assessment resulted in adjustments to practice and the development of a new generation of assessment instruments known as structured professional judgments (SPJs; Cooper et al., 2008 ; Davis & Ogloff, 2008 ; Gormley & Petherick, 2015 ). The introduction of SPJs has permitted an integrative approach to risk assessment, assimilating the scientific basis of the actuarial approach along with the benefits of the clinical approach. In accordance with the need for integrated practice in criminal profiling, a structural framework is proposed, represented by the acronym CRIME. The CRIME framework seeks to overcome the pitfalls of singular profiling approaches and instead provide a structured framework for profile development, incorporating the strengths of each of the examined practices, whilst acknowledging the limitations and weakness of utilising a specific process. This framework is similar to other recommendations and is based upon a similar philosophy to that of at least the works of Davis and Bennett ( 2016 ) and Ackley ( 2017 ).
- C – Crime scene evaluations
- R – Relevancy of research
- I – Investigative or clinical opinion
- M – Methods of investigation
- E - Evaluation
The CRIME framework is centred on a tiered process of profile development. The first tier, crime scene evaluations , relies largely on the crime scene and the evidence present to determine justifications. Consistent with a BEA approach, conclusions cannot be reached without the presence of evidence at the crime scene indicating that a set behaviour or event has occurred. This tier is considered to carry primary significance in the profile, accompanied by the other tiers, which provide additional information of assistance to investigations. At this first phase, evaluations are determined in respect to crime scene evidence, victimology and offender behaviour. The second tier, relevancy of research , is intended to provide investigators with an overview of research on similar offending behaviour, noting factors of relevance in similar crimes and characteristics that have been found on these occasions. This step must specify the limitations of relying on this research and instead seek to provide education and background on the offending matter. The third tier, investigative or clinical opinion , is considered to carry less weight and should be included in profiles with caution. This may include investigators’ unique understanding of factors such as access of local areas, criminal trends or past victim patterns. These factors are provided in the profile as suggestions and knowledge that may be of note for investigators to consider and review during the investigative processes. This information is considered of lower investigative relevance and not based in fact. The penultimate stage and tier of the CRIME framework is methods of investigation . This stage aims to provide detailed implications arising from the aforementioned steps, indicating avenues for investigators to explore and offering techniques of investigation and advice in relation to the suspect. The final stage is evaluation , and involves a critical examination of the profile itself, the logic, reasoning and sequencing used to arrive at the profile, and any input the investigators have about the document. This also includes an evaluation of the profile in light of new information or evidence that has come to light since the profile was generated, along with a peer review of the profile before this is provided to the consumer.
An example of the application of the CRIME framework to the below scenario (adapted from Aydin & Dirilen-Gumus, 2011 , p. 2615–2616; Douglas et al., 1986 , p. 416) is as follows:
At 3.00 pm a young woman’s nude body was discovered on the roof top of an apartment building where she was living. The female had been extensively beaten to her face, and she had been strangled with the bag strap that belonged to her purse. Her nipples had been cut off after her death, and these had been placed on her chest. On the inside of her thigh in ink, were the words, ‘You can’t stop me’. On her abdomen, the words, ‘Fuck you’ were scrawled on this section of her body. The pendant that was usually worn by the woman, a Jewish sign (Chai) for good luck, was missing from around her neck. The missing pendant was presumed taken by the murderer. Her nylon stockings had been removed and loosely tied around her wrists and ankles near a railing, with her underpants pulled over her face. The crime scene revealed that the victim’s earrings that she had been wearing were placed symmetrically on either side of her head. An umbrella and ink pen had been inserted into the woman’s vagina and a hair comb was placed into her pubic hairs. Her jaw and nose had been broken, her molars were loosened, and due to the blunt force trauma, she had sustained multiple face fractures. The cause of death was determined to be asphyxia by ligature (purse strap) strangulation. There were also post-mortem bite marks on the victim’s thighs, along with several contusions, haemorrhages and lacerations to the body. The killer had defecated on the roof top and this was covered with the victims’ clothing.
The preliminary police reports revealed that another resident of the apartment building, a white male, aged 15 years, had discovered the victim’s wallet. The young male discovered the wallet in the stairwell between the third and fourth floors at approximately 8.20 am, keeping the wallet with him until he returned home from school for lunch that afternoon. Upon returning home, he gave the wallet to his father, a white male, aged 40 years. After receiving the wallet, the father went to the victim’s apartment at 2.50 pm and handed this to the victim’s mother whom she resided with. The mother contacted the day-care centre to inform her daughter about the wallet; however, upon contacting the centre, she learnt that her daughter had not appeared for work that morning. The mother, the victim’s sister and a neighbour began searching the building. Shortly afterwards they discovered the body, and the neighbour called the police. Initial investigations by police revealed that no witnesses had seen the victim after she left her apartment that morning.
The investigation revealed that the victim was a 26-year-old, 4′11″, 90-lb, white female. The victim resided with her mother and father in the apartment building. She awoke around 6.30 am on the day of her murder, dressed, had breakfast (consisting of coffee and juice) and left for work. The woman worked at a near-by day-care centre, where she was employed as a group teacher for handicapped children. When she would leave for work in the morning, she would often alternate between taking the elevator or walking down the stairs, depending on her mood. She had a slight curvature of the spine (kyphoscoliosis) and was a shy and quiet woman. The medical examiner’s report revealed that there was no semen in the victim’s vagina, but semen was detected on the victim’s body. There were visible bite marks on the victim’s thigh and knee area and the murderer had cut the victim’s nipples with a knife after she was deceased and written on her body. The stab wounds that she had sustained were not deep. The examination concluded that the cause of death was strangulation, first manual, then ligature, with the strap of her purse.
While the challenges of developing a profile based on a short scenario are evident, the outline in Table 1 of the integrated CRIME framework details a summary of how the steps may be initially formed and subsequently utilised. The profile should start with an overview of the crime and the details, before integrating the CRIME steps. Upon completion of the five steps, the practitioner producing the profile should summarise the information and provide a review of the importance of the information provided within the profile, again emphasising the reliance of evidence-based information in the profile, from both the standing research corpus and crime scene evidence.
CRIME profile development.
Not only is this approach useful for providing as holistic an understanding of the case as possible, undertaking the CRIME framework may also serve as a bootstrapping process for other types of advice investigators may request as a natural extension of the assistance. For example, having a deep understanding of the crimes of a serial criminal may assist with the process of case linkage where one attempts to link previously unlinked cases to one offender or offender group. Similarly, the profiler/analyst may be able to provide insight into risk assessment of a serial or other offender to determine the likelihood that they will escalate or graduate to other crimes, such as from a sex offender to a killer.
Recommendations and conclusion
For profiling to develop as a discipline, greater scientific rigor is required, with profiles needing to incorporate logic and reasoning that are supported by appropriate evidence and justification. Criminal profiling must have investigative utility, assisting investigations, rather than creating confusion or misleading cases. Secondly, for profiling to advance there must be a move towards scientific practice, with uniformity across the field essential for admissibility in court (Freckelton, 2008 ) should the profiler/analyst be appropriately qualified for such endeavours. Although profiling is intended to develop investigative hypotheses, given the progression towards evidence-based policing, some proponents have suggested that for profiling to constitute a scientific method, court and legal admissibility is essential (Bosco et al., 2010 ; Freckelton, 2008 ; Petherick & Brooks, 2014 ). Currently, profiling regularly fails to add probative value to cases, and instead is considered to have a greater prejudicial effect (Bosco et al., 2010 ). One of the central challenges to profiling meeting admissibility standards in courts has been due to the inconsistencies in practice, with large discrepancies observed across approaches and methods of practice. The reliance on singular methods appears largely problematic, failing to consider the strengths of other profiling modalities, while also exposing investigations to the fragility of a sole method approach.
For profiling to develop as a forensic science and ultimately have admissibility in court, the discipline must be reliable, subject to peer review and scientific publication, be generally accepted amongst fellow practitioners, have guiding or governing standards, have identifiable error rates, and be implemented only in appropriate and applicable cases (Bosco et al., 2010 ). Subsequently, it is proposed that a joint methodology be employed when constructing criminal profiles, focusing on the strengths of each profiling approach and establishing uniformity in practice standards. It is suggested that this approach form the CRIME framework, consisting of crime scene evaluations, relevancy of research, investigative or clinical opinions, methods of investigation and evaluation. The CRIME approach provides a framework to promote the scientific practice of profiling, aiming to assist in the reliability of the practice by detailing a standardised process of developing profiles. It is intended that through the CRIME framework profiles will encompass error rates, specified in the crime scene evaluation and relevancy of research stages, whilst the evaluation stage seeks to incorporate peer review and consultation into practice. For profile to continue as a discipline, systemisation and evidence-based practice is required. Although the CRIME framework is not the ultimate solution to developing a ‘gold standard’ in criminal profiling, the approach seeks to promote integration and unity in practice, an essential first step in establishing practice consistency. It is recommended that future research seek to explore the benefit of profiles derived through the framework, reviewing the consistency and emergence of evidence-based practice. This could be investigated through police satisfaction, profile accuracy and the evidence of reasoning underpinning profiles derived through the CRIME framework. The future of profiling is dependent on the discipline progressing towards science, and integrated practice is the first fundamental step (Fox & Farrington, 2018 ).
Ethical standards
Declaration of conflicts of interest.
Wayne Petherick has declared no conflicts of interest
Nathan Brooks has declared no conflicts of interest
Informed consent
The article does not contain any studies with human participants or animals performed by any of the authors.
- Ackley, C. N. (2017). Criminal investigative advice: A move toward a scientific, multidisciplinary model. In Van Haselt V. B. & Bourke M. L. (Eds.), Handbook of behavioural criminology (pp. 215–238). Springer. [ Google Scholar ]
- Alexandra, A., Matthews, S., & Miller, M. (2002). Reasons, values, and institutions . Tertiary Press. [ Google Scholar ]
- Alison, L., Smith, M. D., Eastman, O., & Rainbow, L. (2003). Toulmin’s philosophy of argument and its relevance to offender profiling . Psychology, Crime & Law , 9 , 173–183. doi: 10.1080/1068316031000116265 [ CrossRef ] [ Google Scholar ]
- Alison, L., Goodwill, A., Almond, L., van den Heuvel, C., & Winter, J. (2010). Pragmatic solutions to offender profiling and behavioural investigative advice. Legal and Criminological Psychology , 15 (1), 115–132. doi: 10.1348/135532509X463347 [ CrossRef ] [ Google Scholar ]
- Almond, L., Alison, L., & Porter, L. (2011). An evaluation and comparison of claims made in behavioural investigative advice reports compiled by the National Policing Improvement Agency in the United Kingdom. In Alison L., Rainbow L., & Knabe S. (Eds.), Professionalising offender profiling: Forensic and investigative psychology in practice . Routledge. [ Google Scholar ]
- Aydin, F., & Dirilen-Gumus, O. (2011). Development of a criminal profiling instrument . Procedia Social and Behavioural Sciences , 30 , 2612–2616. [ Google Scholar ]
- Bartol, C. R. (1996). Police psychology: Then, now and beyond . Criminal Justice and Behaviour , 23 ( 1 ), 70–89. doi: 10.1177/0093854896023001006 [ CrossRef ] [ Google Scholar ]
- Battacharyya, S. (1958). The concept of logic . Philosophy and Phenomenological Research , 18 ( 3 ), 326–340. [ Google Scholar ]
- Bateman, A. L., & Salfati, C. G. (2007). An examination of behavioral consistency using individual behaviors or groups of behaviors in serial homicide . Behavioral Sciences & the Law , 25 ( 4 ), 527–544. doi: 10.1002/bsl.742 [ PubMed ] [ CrossRef ] [ Google Scholar ]
- Bevel, T. (2001). Applying the scientific method to crime scene reconstruction . Journal of Forensic Identification , 51 ( 2 ), 150–165. [ Google Scholar ]
- Bevel, T., & Gardner, R. M. (2008). Bloodstain pattern analysis with an introduction to crime reconstruction (3rd ed.). CRC Press. [ Google Scholar ]
- Bosco, D., Zappalà, A., & Santtila, P. (2010). The admissibility of offender profiling in courtroom: A review of legal issues and court opinions . International Journal of Law and Psychiatry , 33 ( 3 ), 184–191. doi: 10.1016/j.ijlp.2010.03.009 [ PubMed ] [ CrossRef ] [ Google Scholar ]
- Bradley, P. (2003). Criminal profiling: What’s it all about? Inpsych. [ Google Scholar ]
- Brussel, J. A. (1968). Casebook of a crime psychiatrist . Bernard Geis Associates. [ Google Scholar ]
- Burgess, A. W., & Ressler, R. K. (1985). Sexual homicides: Crime scene and pattern of criminal behaviour . National Institute of Justice Grant 82-IJ-CX-0065, US Department of Justice. https://www.ncjrs.gov/App/Publications/abstract.aspx?ID=98230 .
- Canter, D. (1989). Offender profiles . The Psychologist , 2 ( 1 ), 12–16. [ Google Scholar ]
- Canter, D. (2000). Investigative psychology. In Siegel J., Knupfer G., & Saukko P. (Eds.), Encyclopedia of forensic science . Academic Press. [ Google Scholar ]
- Canter, D. V. (2011). Resolving the offender “Profiling equations” and the emergence of an investigative psychology . Current Directions in Psychological Science , 20 ( 1 ), 5–10. doi: 10.1177/0963721410396825 [ CrossRef ] [ Google Scholar ]
- Canter, D. V., Alison, L. J., Alison, E., & Wentink, N. (2004). The organized/disorganized typology of serial murder: Myth or model? Psychology, Public Policy, and Law , 21 , 293–320. [ Google Scholar ]
- Canter, D. V., & Heritage, R. (1990). A multivariate model of sexual offence behaviour: Development in “offender profiling”: I . The Journal of Forensic Psychiatry , 1 ( 2 ), 185–212. doi: 10.1080/09585189008408469 [ CrossRef ] [ Google Scholar ]
- Canter, D. V., & Youngs, D. (2003). Beyond ‘offender profiling’: The need for an investigative psychology. In Carson D. & Bull R. (Eds.), Handbook of psychology in legal contexts (2nd ed., pp. 171–205). Wiley. [ Google Scholar ]
- Cole, T., & Brown, J. (2011). What do senior investigative police officers want from behavioural investigative advisers. In Alison L., Rainbow L., & Knabe S. (Eds.), Professionalising offender profiling: Forensic and investigative psychology in practice . Routledge. [ Google Scholar ]
- Cooper, B. S., Griesel, D., & Yuille, J. C. (2008). Clinical-forensic risk assessment. The past and current state of affairs . Journal of Forensic Psychology Practice , 7 ( 4 ), 1–63. doi: 10.1300/J158v07n04_01 [ CrossRef ] [ Google Scholar ]
- Copson, G. (1995). Coals to Newcastle? Part 1: A study of offender profiling. Police Research Group Special Interest Paper 7 . Home Office. [ Google Scholar ]
- Davis, M. R., & Bennett, D. (2016). Future directions for criminal behaviour analysis of deliberately set fire events. In Doley R. M., Dickens G. L., & Gannon T. A. (Eds.), The psychology of arson: A practical guide to understanding and managing deliberate firesetters (p. 131–146). Routledge/Taylor & Francis Group. [ Google Scholar ]
- Davis, M. R., & Ogloff, J. R. P. (2008). Risk assessment. In Fritzon K. & Wilson P. (Eds.), Forensic psychology and criminology: An Australian perspective (pp. 141–164). McGraw-Hill Australia Pty Ltd. [ Google Scholar ]
- Davis, M., Rainbow, L., Fritzon, K., West, A., & Brooks, N. (2018). Behavioural investigative advice: A contemporary commentary on offender profiling activity. In Griffiths A. & Milne R. (Eds.), The psychology of criminal investigation: From theory to practice (pp. 187–206). Routledge. [ Google Scholar ]
- Douglas, J. E., & Burgess, A. E. (1986). Criminal profiling: A viable investigative tool against violent crime . FBI Law Enforcement Bulletin , 55 , 9–13. [ Google Scholar ]
- Douglas, J. E., Ressler, R. K., Burgess, A. W., & Hartman, C. R. (1986). Criminal profiling from crime scene analysis . Behavioral Sciences & the Law , 4 ( 4 ), 401–422. doi: 10.1002/bsl.2370040405 [ CrossRef ] [ Google Scholar ]
- Farber, M. (1942). Logical systems and the principles of logic . Philosophy of Science , 9 ( 1 ), 40–54. doi: 10.1086/286747 [ CrossRef ] [ Google Scholar ]
- Federal Bureau of Investigation. (2002). Uniform crime report . www.fbi.gov/ucr/cius_02/html/web/index.html
- Fox, B., Farrington, D. P., Kapardis, A., & Hambly, O. C. (2020). Evidence-based offender profiling . Routledge. [ Google Scholar ]
- Fox, B., & Farrington, D. P. (2018). What have we learned from offender profiling? A systematic review and meta-analysis of 40 years of research . Psychological Bulletin , 144 ( 12 ), 1247–1274. doi: 10.1037/bul0000170 [ PubMed ] [ CrossRef ] [ Google Scholar ]
- Freckelton, I. (2008). Profiling evidence in the courts. In Canter D. & Žukauskienė R. (Eds.), Psychology and law: Bridging the gap (pp. 79–102). Routledge. [ Google Scholar ]
- Gekoski, A., & Gray, J. M. (2011). It may be true, but how’s it helping?’: UK police detectives’ views of the operational usefulness of offender profiling . International Journal of Police Science & Management , 13 ( 2 ), 103–116. doi: 10.1350/ijps.2011.13.2.236 [ CrossRef ] [ Google Scholar ]
- Goldsworthy, T. (2001). Criminal profiling. Is it investigatively relevant? [Master of criminology dissertation]. Bond University. [ Google Scholar ]
- Gormley, J., & Petherick, W. (2015). Risk assessment. In Petherick W. (Ed.), Applied crime analysis: A social science approach to understanding crime, criminals, and victims (pp. 172–189). Elsevier. [ Google Scholar ]
- Hazelwood, R. R., & Douglas, J. E. (1980). The lust murderer . FBI Law Enforcement Bulletin , 49 ( 4 ), 1–5. [ Google Scholar ]
- Holmes, R., & Holmes, S. (2002). Profiling violent crimes: An investigative tool (3rd ed.). Sage Publications. [ Google Scholar ]
- Kocsis, R. N. (2001). Serial arsonist crime profiling: An Australian empirical study . Firenews. [ Google Scholar ]
- Kocsis, R. N., Irwin, H. J., Hayes, A. F., & Nunn, R. (2000). Expertise in psychological profiling: A comparative assessment . Journal of Interpersonal Violence , 15 ( 3 ), 311–331. doi: 10.1177/088626000015003006 [ CrossRef ] [ Google Scholar ]
- Marshall, B. C., & Alison, L. (2011). Stereotyping, congruence and presentation order: Interpretative biases in utilizing offender profiles. In Alison L., Rainbow L., & Knabe S. (Eds.), Professionalising offender profiling: Forensic and investigative psychology in practice . Routledge. [ Google Scholar ]
- McGrath, M. (2001). Criminal profiling: Is there a role for the forensic psychiatrist? Journal of the American Academy of Forensic Psychiatry and Law , 28 ( 3 ), 315–324. [ PubMed ] [ Google Scholar ]
- Morton, R. J., Tillman, J. M., & Gaines, S. J. (2014). Serial murder: Pathways for investigations . U.S. Department of Justice. [ Google Scholar ]
- Mouzos, J. (2005). Homicide in Australia: 2003-2004 national homicide monitoring program (NHMP) annual report . Australian Institute of Criminology. [ Google Scholar ]
- Navarro, J., & Schafer, J. R. (2003). Universal principles of criminal behavior: A tool for analyzing criminal intent. FBI Law Enforcement Bulletin , 72 (1), 22–24. https://heinonline.org/HOL/P?h=hein.journals/fbileb72&i=23 [ Google Scholar ]
- Neblett, W. (1985). Sherlock’s logic: Learn to reason like a master detective . Barnes and Noble Books. [ Google Scholar ]
- Niiniluoto, I. (1999). Defending abduction . Philosophy of Science , 66 , S436–S451. http://www.jstor.com/stable/188790 [ Google Scholar ]
- Petherick, W. A. (2014a). Criminal profiling methods. In Petherick W. A. (Ed.), Profiling and serial crime: Theoretical and practical issues in behavioural profiling (3rd ed.). Anderson Publishing. [ Google Scholar ]
- Petherick, W. A. (2014b). Induction and deduction in criminal profiling. In Petherick W. A. (Ed.), Profiling and serial crime: Theoretical and practical issues in behavioural profiling (3rd ed.). Anderson Publishing. [ Google Scholar ]
- Petherick, W. A., & Brooks, N. (2014). Where to from here? In Petherick W. A. (Ed.), Profiling and serial crime: Theoretical and practical issues in behavioural profiling (3rd ed., pp. 241–259). Anderson Publishing. [ Google Scholar ]
- Petherick, W. A., & Ferguson, C. E. (2010). Ethics for the forensic criminologist. In Petherick W. A., Turvey B. E., & Ferguson C. E. (Eds.), Forensic Criminology . Elsevier Science. [ Google Scholar ]
- Petherick, W. A., & Turvey, B. E. (2008). Behavioral evidence analysis: An ideo deductive method of criminal profiling. In Turvey B. E. (Ed.), Criminal profiling: An introduction to behavioral evidence analysis (3rd ed). Academic Press. [ Google Scholar ]
- Pierce, C. S. (1898). Reasoning and the logic of things: The Cambridge conferences lectures of 1898 . In K. L. Ketner (Ed.). Harvard University Press. [ Google Scholar ]
- Pinizzotto, A. J., & Finkel, N. J. (1990). Criminal personality profiling: An outcome and process study . Law and Human Behavior , 14 ( 3 ), 215–233. doi: 10.1007/BF01352750 [ CrossRef ] [ Google Scholar ]
- Rainbow, L., & Gregory, A. (2011). What behavioural investigative advisers actually do. In L. Alison & L. Rainbow (Eds.), Professionalizing offender profiling: Forensic and investigative psychology in practice (pp. 35–50). Routledge. [ Google Scholar ]
- Rainbow, L., Gregory, A., & Alison, L. (2014). Behavioural investigative advice. In Bruinsma G. J. N. & Weisburd D. L. (Eds.), Encyclopedia of criminology and criminal justice (pp. 125–134). Springer. [ Google Scholar ]
- Ressler, R. K., Burgess, A. W., & Douglas, J. E. (1992). Sexual homicide: Patterns and motives . Free Press. [ Google Scholar ]
- Snook, B., Eastwood, J., Gendreau, P., & Bennell, C. (2010). The importance of knowledge cumulation and the search for hidden agendas: A reply to Kocsis, Middledorp, and Karpin (2008). Journal of Forensic Psychology Practice , 10 (3), 214–223. doi: 10.1080/15228930903550541 [ CrossRef ] [ Google Scholar ]
- Stock, G. W. J. (2004). Deductive logic . Project Gutenberg Press. [ Google Scholar ]
- Thornton, J. (1997). The general assumptions and rationale of forensic identification. In Faigman D. L., Kaye D. H., Saks M. J., & Sanders J. (Eds.), Modern scientific evidence: The law and expert testimony . West Publishing. [ Google Scholar ]
- Torres, A. N., Boccaccini, M. T., & Miller, H. A. (2006). Perceptions of the validity and utility of criminal profiling among forensic psychologists and psychiatrists . Professional Psychology: Research and Practice , 37 ( 1 ), 51–58. doi: 10.1037/0735-7028.37.1.51 [ CrossRef ] [ Google Scholar ]
- Toulmin, S. (1958). The uses of argument . Cambridge University Press. [ Google Scholar ]
- Turvey, B. E. (2012). Ethics and the criminal profiler. In Turvey B. E. (Ed.), Criminal Profiling: An introduction to Behavioral Evidence Analysis (4th ed., pp. 601–626). Academic Press. [ Google Scholar ]
- West, A. (2000). Clinical assessment of homicide offenders: The significance of crime scene in offense and offender analysis . Homicide Studies , 4 ( 3 ), 219–233. [ Google Scholar ]
- Wilson, P., Lincoln, R., & Kocsis, R. N. (1997). Validity, utility and ethics for serial violent and sex offenders . Psychiatry, Psychology and Law , 4 ( 1 ), 1–12. doi: 10.1080/13218719709524891 [ CrossRef ] [ Google Scholar ]

- © 2007
Criminal Profiling
International Theory, Research, and Practice
- Richard N. Kocsis (Forensic Psychologist)
You can also search for this editor in PubMed Google Scholar
Combines vast empirical research with the author's personal experiences
Draws together for the time the characteristics of the CAP approach to profiling violent crimes
Describes for the experienced and lay person how to use the various CAP models to profile a particular crime without necessarily needing to comprehend how each model was originally built
91k Accesses
123 Citations
5 Altmetric
- Table of contents
About this book
Bibliographic information.
- Publish with us
Buying options
- Available as EPUB and PDF
- Read on any device
- Instant download
- Own it forever
- Compact, lightweight edition
- Dispatched in 3 to 5 business days
- Free shipping worldwide - see info
- Durable hardcover edition
Tax calculation will be finalised at checkout
Other ways to access
This is a preview of subscription content, log in via an institution to check for access.
Table of contents (20 chapters)
Front matter, profiling crimes of violence, homicidal syndromes.
- George B. Palermo
Offender Profiles and Crime Scene Patterns in Belgian Sexual Murders
- Fanny Gerard, Christian Mormont, Richard N. Kocsis
Profiling Sexual Fantasy
- Dion Gee, Aleksandra Belofastov
Murder by Manual and Ligature Strangulation
- Helinä Häkkänen
Criminal Propensity and Criminal Opportunity
- Eric Beauregard, Patrick Lussier, Jean Proulx
New Techniques and Applications
Case linkage.
- Jessica Woodhams, Ray Bull, Clive R. Hollin
Predicting Offender Profiles From Offense and Victim Characteristics
- David P. Farrington, Sandra Lambert
Criminal Profiling in a Terrorism Context
Geographic profiling of terrorist attacks.
- Craig Bennell, Shevaun Corey
Legal and Policy Considerations for Criminal Profiling
Criminal profiling as expert evidence.
- Caroline B. Meyer
- Anne Marie R. Paclebar, Bryan Myers, Jocelyn Brineman
The Phenomenon of Serial Murder and the Judicial Admission of Criminal Profiling in Italy
- Angelo Zappalá, Dario Bosco
Criminal Profiling and Public Policy
- Jeffrey B. Bumgarner
The Observations of the French Judiciary
- Laurent Montet
The Image of Profiling
- James S. Herndon
Critiques and Conceptual Dimensions to Criminal Profiling
- Violent Crime
- identification
Book Title : Criminal Profiling
Book Subtitle : International Theory, Research, and Practice
Editors : Richard N. Kocsis
DOI : https://doi.org/10.1007/978-1-60327-146-2
Publisher : Humana Totowa, NJ
eBook Packages : Medicine , Medicine (R0)
Copyright Information : Humana Press 2007
Hardcover ISBN : 978-1-58829-684-9 Published: 06 July 2007
Softcover ISBN : 978-1-61737-717-4 Published: 05 November 2010
eBook ISBN : 978-1-60327-146-2 Published: 30 June 2007
Edition Number : 1
Number of Pages : XXII, 418
Number of Illustrations : 10 b/w illustrations
Topics : Forensic Medicine
Policies and ethics
- Find a journal
- Track your research
- Technical Support
- Find My Rep
You are here
Criminal & Behavioral Profiling
- Curt R. Bartol
- Anne M. Bartol
- Description
See what’s new to this edition by selecting the Features tab on this page. Should you need additional information or have questions regarding the HEOA information provided for this title, including what is new to this edition, please email [email protected] . Please include your name, contact information, and the name of the title for which you would like more information. For information on the HEOA, please go to http://ed.gov/policy/highered/leg/hea08/index.html .
For assistance with your order: Please email us at [email protected] or connect with your SAGE representative.
SAGE 2455 Teller Road Thousand Oaks, CA 91320 www.sagepub.com
(Due to changes in the curriculum we have not adopted this book or any similar text.) The book gives a good basic overview of the field of criminal and behavioural profiling. The text is very accessible and should be ok to read even for non-native English readers. I would not hesitate to use this book at our university of applied sciences or at a university in the Netherland. The development of the field is described along historical lines and works towards the current way that theory, research and practice are still evolving. It’s very much a relatively young discipline and not without it’s controversies. These and different schools of thought within the field are well presented in the book. The book is a very nice and concise introduction into the field of criminal and behavioural profiling.
throughout the book there are interesting articles that relate to the study my learners have to complete in certain modules, especially on difference and diversity and assumptions a great book to use for reference in study and in professional parctice.
This book has been considered as supplemental reading for our MSc programme. It provides a comprehensive overview of criminal profiling in an interesting and accessible manner. Case studies help bring the theory and techniques to life.
Very good text. up-to-date and includes an international perspective
This is a really well-written and interesting book that our students will hopefully connect with well. Uses a good range of examples and relevant research.
Most appropriate for my new course called Profiling and Threat Assessment Hits on all the appropriate topics in a writing style well-liked by the students and is more than authoritative enough for my requirements
My profiling class is very specific and this just didn't quite fit it.
Easy to read and useful for entry level learners in crime investigation
Interesting coverage of the subject area. Recommended as additional reading
Used a lot of the information for the topic of offender profiling and have recommended the book to the students if they want to take this topic further in their final year dissertations.
FEATURES & BENEFITS
- Presents an international perspective, integrating research, theory, practice, and examples from not only the United States, but also Great Britain, Canada, Australia, the Netherlands, Finland, and more.
- Includes case examples to illustrate theory and techniques.
- Offers historical information about the origins of profiling, including its development by the FBI Behavioral Science Unit.
- Highlights the victimology approach, with an emphasis on the importance—for profiling purposes—of gathering information about the victim and how serial offenders treat their victims.
- Features Focus Boxes in each chapter to provide applied information from practice.
- Integrates timely literature from the rapidly growing international research in criminal profiling
Sample Materials & Chapters
For instructors, select a purchasing option.

The usefulness of criminal profiling
Craig Jackson, David Wilson and Baljit Kaur Rana review some of the evidence on the profiling process
In 2010 we published a critical review of a book by the legendary FBI profiler John Douglas, covering his role in the hunt for the ‘Bind, Torture Kill’ (‘BTK’) serial murderer, in Wichita, Kansas, USA (Douglas and Dodd, 2007). Our article was essentially critical of the role of ‘embedded profiling’ where experts, such as Douglas, use emotive aspects of cases to help develop profiles of active offenders, especially in the context of serial murder investigations.
Our central contention was that such profiling, where Douglas and Dodd (2007) claim to ‘delve inside the swamp-like minds of murderers’, was certainly not scientific psychology, and we questioned if any empirical evidence existed to support its claimed usefulness. In the 30-year case of the ‘BTK’, investigators possibly had the richest ever assembly of clues, direct correspondence, crime-scene details, physical descriptions and access to FBI expertise ever amassed in an ongoing serial murder investigation. It was therefore surely the best chance that proponents of criminal profiling (CP) would have in proving its usefulness as an applied technique. It was both surprising and disappointing then that CP failed to lead to the direct apprehension of the ‘BTK’ killer.
'Educated guesswork'
Additionally we also set a challenge at a press conference for the British Festival of Science in September 2010 at the Royal Institution, for anyone to provide us with evidence where a criminal profile has led to the direct apprehension and sound conviction of a suspect in a serial murder enquiry. Douglas is unapologetic for the embedded nature of his brand of profiling, pointing out similarities between profilers and physicians who ‘learn skills through brainstorming, intuition, and educated guesswork’. Our article (Wilson et al., 2010) caught the imaginations of journalists and was widely reported in many broadsheet and tabloid newspapers and sources – becoming known as the ‘cracker-basher’ article – referencing the TV series of the same name while providing acknowledgement to the inaccurate and limited view of the role of profilers that the public have. One small intricacy in our article is that we contained our criticism to the context of serial murder investigations, although the journalist reports of our paper broadened our criticism to all investigations using profiling. A re-cap on the usefulness of CP is therefore probably timely.
Allegations
Douglas et al. (1986) argued that a criminal's personality as well as behavioural and demographic details could be predicted from crime scene evidence, and further, despite little supporting evidence, CP became widely accepted and used (Snook et al., 2007). The allegations we lodged at profilers were by no means new, and such criticism has been aired previously by journalists as well as other academics (Snook et al., 2008) who went so far as to declare the successful acceptance of CP by the public as the ‘profiling illusion’ – the success of which was down to how the public chose to accept some fields of applied science in favour of others that they do not adopt.
An acknowledgement of a divergence in CP must be made. Some approaches have a statistical and probabilistic leaning, with other areas being based more on clinical and intuitive premises, and indeed it is this form of CP that uses ‘wet-skills’ and ‘street smarts’ (that Douglas and Dodd (2007) claim only those from a police background truly master). It appears to be the brand of CP (and related academic testing of it) that uses statistical empirical evidence that seems to hold greater longevity and influence in this field. However, regardless of the type of CP used, most surveys of police personnel show that the majority of officers polled found CP to have some level of operational usefulness (see for example, Trager and Brewster, 2001).
The methodological concerns about bias in these studies, and the relatively small sample sizes in some research should be considered. As CP has evolved, and as the statistical approaches of ‘investigative psychology’ have become more widespread, some of the early principles adopted by proponents have been modified or outgrown. The main outdated principle here being the binary notion of offenders belonging to organised or disorganised trait sub-types, and that such traits can be predictive of offence mechanisms. Research has shown this to be an outmoded concept of little predictive usefulness (Canter et al., 2004). It is widely acknowledged that offender traits are not reliably predictive of the crimes they commit, and given that murder may often primarily be an ill-thought-through response to a highly-charged emotional situation, it is intuitive that the usefulness of trait-based approaches will be limited.
That demographic features could be predicted from an assessment of particular configurations of specific behaviours occurring in short-term, highly traumatic situations seems an ambitious and unlikely possibility. Until the process is more formally verified, the evidential usefulness of profiles should be treated cautiously, or even entirely excluded from consideration in court.
A similar fate awaited the ‘intuitive’ classification of serial sexual murders by Keppel and Walter (1999) as being power-assertive, power-reassuring, retaliatory-angered or excited-angered; as such classifications often did not bear fruit under statistical analysis.
Snook et al. (2007) conducted a systematic review using 130 studies in the field and were able to conclude in some respects that CP relies on being justified by common sense – or as Pierre Laplace may have called it, ‘common sense reduced to calculation’. In addition, despite the methodological and theoretical arguments, a further complication in the review of CP arises with the argument of who can best apply such techniques in the field. Snook et al., (Ibid) used a meta-analysis of the literature to show that profilers were often little better – if at all – than non-experts and laypersons in predicting offender characteristics from crime-scenes. Unsurprisingly, their conclusions about the existence and future of CP as a pseudoscience were even bleaker than the ones we expressed in response to Douglas and Dodd's (2007) account of their ‘BTK’ experiences.
In terms of the value of evidence provided by CP, the field will struggle to prove its relevance. Not many profilers would assert that CP can identify a single actual perpetrator, preferring to state that its role is to indicate the type of person responsible, being the person most likely to commit a crime with such specific and unique characteristics. This inability to deliver an identifying profile is the hurdle most guaranteed to cause CP to stumble.
Contradictory
In conclusion, much of the literature in the area is contradictory, which in its own way is a positive and healthy way for the discipline and the methods used in evaluating it to develop and evolve. Some reviews of CP have used systematic approaches, and others are more narrative and theoretical approaches, but they often arrive at the same conclusions: despite limitations in the research corpus, CP shows it has the promise to evolve into something more robust and useful. However, in the absence of that evolutionary step just yet, it must be said that there is very little evidence of the compelling kind that would actually support CP in enjoying the large level of public and police acceptance that it currently enjoys. Its appeal still remains in its potential.
Further, while some of the fundamental principles of CP that have been proved outdated by other areas of empirical psychology and behavioural science standards still remain within the applied field, the scrutiny and criticism of the whole field will remain.
Other academics in the field also suggest that the public have a role in shaping how such science is shaped, by being more discerning in how they perceive and adopt accepted wisdom. However, some would argue that such public education and discernment is not necessary in order for the discipline to become more refined; after all, how many laypersons understand the intricacies of DNA matching but yet have absolute faith in its probabilistic certainties and correct application? CP can hopefully prove itself by the virtues of large-scale ideographic research, rather than by the anecdotal nomothetic case studies that linger in the memory. But until then it still promises much more than it currently delivers, and its role as just another tool to be used by senior investigating officers in murder investigations will not develop any further.
Craig Jackson is Professor of Workplace Health Psychology and Head of the Psychology Division, David Wilson is Professor of Criminology and Head of the Centre for Applied Criminology and Baljit Kaur Rana is Senior Lecturer in Organisational Psychology, in the Psychology Division, at Birmingham City University.
Canter, D.V., Alison, L.J., Alison, E. and Wentink, N. (2004), The organized/ disorganized typology of serial murder: Myth or model?’. Psychology, Public Policy and Law, 10: 293–320.
Douglas , J. and Dodd , J. (2007), Inside the Mind of the BTK: The True Story behind the Thirty Year Hunt for the Notorious Wichita Serial Killer , San Francisco : Jossey-Bass.
Douglas, J., Ressler, R., Burgess, A. and Hartman, C. (1986), 'Criminal profiling from crime scene analysis’. Behavioral Sciences and the Law , 4: 401–421.
Keppel, R.D. and Walter, R. (1999), Profiling killers: A revised classification model for understanding sexual murder’. International Journal of Offender Therapy and Comparative Criminology , 43: 417–434.
Snook, B., Cullen, R.M., Bennell, C., Taylor, P.J. and Gendreau, P. (2008), The criminal profiling illusion: What's behind the smoke and mirrors’. Criminal Justice and Behavior , 35: 1257–1276.
Snook, B., Eastwood, J., Gendreau, P., Coggin, C. and Cullen, R.M. (2007), Taking stock of criminal profiling: A narrative review and metal-analysis’. Criminal Justice and Behavior , 34: 437–453.
Trager, J. and Brewster, J. (2001) 'The effectiveness of psychological profiles’. Journal of Police and Criminal Psychology , 16: 20–28.
Wilson, D., Jackson, C.A. and Rana, B. (2010) 'Against the medical- psychological tradition of understanding serial killing by studying the killers: The case of BTK’. Amicus Journal , 22: 8–16.
What Is Criminal Profiling and What Is Its Role in Law Enforcement?

Fill out the form below and we’ll email you more information about UCF’s online Criminal Justice programs.
- Name * First Last
- Degree * Corrections Leadership Crime Analysis Criminal Justice, BA/BS Criminal Justice, MS Digital Forensics, MS Juvenile Justice Leadership Legal Studies, BA/BS Police Leadership Political Science, BA
- Phone This field is for validation purposes and should be left unchanged.
Privacy Notice
With the popularity of psychological TV crime thrillers such as Mindhunter and many others, people may wonder what criminal profiling is and how accurately it’s portrayed on television. Beginning with high profile cases such as the “Mad Bomber” — where the psychiatrist and criminologist James A. Brussel created a profile to help identify the bomber as George Metesky — the FBI’s Behavioral Analysis Unit developed advanced techniques and databases that led to arrests of notorious serial killers such as Ted Bundy.
In practice, criminal profilers are highly trained experts who specialize in identifying the perpetrators behind serious crimes. Using techniques such as extensive knowledge of behavior and statistical probability, profilers work in tandem with forensics teams and other members of law enforcement to apprehend suspects. For those interested in a career in law enforcement, programs and certificates in criminal justice, forensic sciences, and crime analysis can allow officers to pursue these specialized roles.
The History of Criminal Profiling
As far back as the late 19th century, investigators used psychology to understand and attempt to apprehend infamous killers such as Jack the Ripper. In those days however, law enforcement often lacked reliable information to follow up on, relying instead on witness testimony and conclusions they could draw from victims and crime scenes. Since those rudimentary examinations, the tools and techniques available to law enforcement officers have evolved significantly, including advances in technology and improvements in forensic science.
Pioneers such as former FBI Special Agent John Edward Douglas were able to master and develop a criminal profiling methodology that is still in use today. By interviewing serial killers, terrorists and other violent criminals, Douglas was able to research the psychopathologies and behavioral abnormalities of serious criminals, beginning the process of identifying patterns and correlating behaviors.
The Advancement of Criminal Profiling
Using modern technology and databases such as the Violent Criminal Apprehension Program (ViCAP), today’s investigators can link cases and evidence that may have previously been overlooked. What is involved in criminal profiling has changed significantly, enabling the FBI to establish a more reliable standard of evidence-based profiling. By working with members of law enforcement and forensic scientists, profilers are able to better understand and analyze psychological, behavioral and other angles of a case.
Criminal Profiling’s Role in Law Enforcement
The question “why?” is at the heart of any criminal investigation. In many violent crimes, the victim is often somehow related to or acquainted with their attacker. But what often sets criminals such as serial killers or terrorists apart is their motive. It is not specific to the victim, but rather to the crime itself. By carefully studying patterns of behavior, profilers can formulate theories of when and how a criminal will act next, facilitating their apprehension before they commit another crime.
Criminal Profilers in Action
Profilers are especially effective in cases involving hostage takers, rapists, arsonists, sexual murders and the identification of writers of threatening letters. By using psychology, profilers are better able to predict the behaviors of these criminals. What is unique to criminal profiling is that many of these crimes do not follow common patterns or motives, making perpetrators less predictable and more difficult to apprehend.
The examination of methodology, criminal signature and forensic connections aid in the creation of a criminal profile by identifying patterns of behavior. Studying the psychology behind a crime allows profilers to establish probable cause for search warrants and assist detectives in compiling evidence for their legal case. Furthermore, the understanding of criminal behavior and the connections between details of a crime produce a basis on which criminal profilers can provide testimony in court as expert witnesses.
Criminal Profilers and Cybercrime
In the early days of criminal profiling, the technology to commit cybercrime had not yet been invented. Today however, cybercrime has become one of the fastest growing types of illegal activity and greatest threats to national security, making the skills and knowledge to address it a vital focus in current training programs. Combining the coordination of technological skills and the implementation of traditional core methodologies, profilers can aid in the apprehension of cyber criminals.
Criminal Profilers Working in Law Enforcement
What is unique about criminal profiling is that practitioners can serve as intermediaries between organizations in law enforcement. While they are not a substitute for skilled detective work, profilers can provide detectives with interrogation techniques or a profile of a suspect. In local and state law enforcement, profilers can also be hired as detectives or criminal investigators, assisting in cases of multijurisdictional scope and facilitating the collection of evidence.
Criminal Profilers in Federal Agencies
The FBI and the Bureau of Alcohol, Tobacco, Firearms and Explosives (ATF) employ profilers who have undergone specialized training to address recurring or unusual violent crimes. Practicing criminal investigative analysis, profilers provide behavioral-based operational support to partner agencies. As technical experts in the field, they can build a profile by conducting an examination, evaluation and interpretation of a crime, as well as providing technical training, research and intelligence reports.
Requirements for federal criminal profilers include a bachelor’s degree in a related field such as criminal justice or psychology and completion of the FBI’s Behavioral Analysis Unit (BAU) training program. Prior to applying, applicants typically have logged a minimum of 7 to 15 years of investigative experience to understand and properly integrate behavior into law enforcement strategy. After completing the program, candidates gain experience through on-the-job training, working alongside experts on active cases.
Law Enforcement and Profiling in Tandem
Building an accurate criminal profile involves the thorough examination of a crime scene to identify notable psychological traits of the suspect such as psychopathologies, behavioral patterns or demographic variations. Understanding what is behind criminal profiling takes many years of experience and training, making the available roles in profiling both limited and highly competitive. Fortunately for those inspired by profiling, there are several other avenues in criminal justice, psychology or forensics available.
Forensic Sciences and Profiling
Without forensic sciences to support criminal profiling, it would be nearly impossible to build an evidence-based case to argue effectively in court. While a profile can aid forensics teams to locate or give context to evidence, it is the evidence itself, collected by forensic scientists, that becomes the backbone of a case. Forensic science and digital forensics professionals have the advanced technological skills to assist in prosecuting both traditional crimes and cybercriminal activity.
Profiling and Criminal Justice
With a thorough understanding of the nature of crime, criminal justice theory, and an in-depth knowledge of how the judicial system works, experts in criminal justice can play an important role at both the local and federal level. Working in tandem with law enforcement agencies, criminal profilers, and federal representatives, leaders in criminal justice can act as a voice for fairness, progressive growth and safety in our justice system.
Law Enforcement and Psychology
Psychology and law enforcement often work hand in hand, in dealing with individuals suffering from mental illness, understanding the motivation behind criminal activity and providing care or resources to the individuals that need them. From building an effective profile to safely detaining a criminal suffering from mental illness or acting as the psychiatric professional that aids in the care of those individuals, psychology plays a critical role in justice and criminal justice reform.

Prepare for a Career in Law Enforcement
Dedicated to understanding the “why?” behind dangerous crimes, profilers are passionate and talented members of law enforcement and federal agencies and an essential component to solving some of the most challenging and infamous cases. From forensic scientists to law enforcement officers and criminal justice experts, there are a variety of exciting opportunities open to those who want to act as a voice for change and make a positive impact in the lives of others.
Designed with flexibility and excellence in mind, the criminal justice programs at UCF Online , such as the master’s in digital forensics and master’s in forensic science , are dedicated to providing a high quality education to the next generation of criminal justice leaders. Whether you are passionate about pursuing forensic sciences and juvenile justice , or inspired by the crime analysis and criminal profiling certificate programs, UCF Online is committed to empowering you with a wide variety of specialized skills.
Discover how you can make a difference as a criminal justice graduate.
UCF’s Online Criminal Justice Degrees
- Corrections Leadership
- Crime Analysis
- Criminal Justice, BA/BS
- Criminal Justice, MS
- Digital Forensics, MS
- Juvenile Justice Leadership
- Legal Studies, BA/BS
- Police Leadership
- Political Science, BA
You May Also Enjoy


Forensic Psychology
Skeptical of fbi criminal profiling’s validity, there are alternative profiling approaches..
Posted September 27, 2020

Not everyone believes in the FBI criminal profiling process that has been popularly depicted in the hit Netflix series Mindhunter .
For several decades now, clinical and forensic psychologists have been conducting research in order to assess the scientific rigor and validity of criminal profiling techniques. In that regard, a number of experiments have been conducted by psychologists on the central assumptions and techniques of FBI criminal profiling, but these studies have usually involved recreations in a controlled setting and were not based on actual criminal cases. Moreover, many of these studies have never been replicated, so their reliability is questionable or unknown.
Despite an inability to conduct utility tests on actual serial homicide cases, several prominent psychologists who oppose the FBI system have nonetheless developed new approaches to profiling which they claim outperform the FBI process. At least two of these newer approaches have gained acceptance among criminal justice practitioners over the past few decades. They are as follows.
Investigative Psychology and Offender Profiling
This approach is based on the work of applied psychologist David Canter, Ph.D., who pioneered the field of investigative psychology in the early 1990s. He founded the Centre for Investigative Psychology at the University of Liverpool in England. Investigative psychology, according to Dr. Canter, includes many areas where psychology can contribute to criminal investigations, including behavioral profiling.
The goal of offender profiling, as performed by investigative psychologists, is similar to the goal of the FBI system of profiling—that is, to infer the defining characteristics of an unknown suspect based on his/her behavior during the commission of a crime. The difference between the two systems, according to Canter, is that all of the inferences made by investigative psychologists are based on empirical, peer-reviewed research, as opposed to the FBI model where inferences are based on the anecdotal experiences of individual criminal investigators.
Canter and his colleagues analyzed crime scene data from 100 serial homicide cases they found in the Centre for Investigative Psychology database to test the FBI's organized/disorganized dichotomy of serial crimes.
Their findings indicate that, contrary to the assertions of FBI profilers, virtually all serial murderers in their study exhibited some level of organization. Canter contends that organized behaviors such as concealing the victim's body are “constants“ of serial homicide that tend to occur along with variables such as mutilation or necrophilia.
Canter and his colleagues concluded that the actual difference between serial murderers lies in the type of “disorganized behaviors they exhibit” rather than the organized/disorganized dichotomy adhered to by the FBI. They further concluded that serial murderers can be divided into categories based on their interactions with their victims, including sexual control and domination, mutilation, or torture.
Canter argues that empirical research studies performed by investigative psychologists, based on proven scientific methods, are the only way to establish valid and reliable descriptions, categories, and classifications of serial killers. The approach utilized by investigative psychologists, according to Canter, "considers all the information that may be apparent at the crime scene and to carry out theory-based studies to determine the underlying structures of that material" (1).
Canter and his colleagues have little faith in the serial offender descriptions and categories developed by FBI agents from their own personal crime scene investigations. Canter believes that investigative psychologists must work from the ground up to gather data, develop theories, and classify offenders using empirical research methods that are not limited or biased by the experiences of criminal investigators.
Forensic Psychology and Crime Action Profiling
In the late 1990s, forensic psychologist Richard Kocsis, Ph.D., sought to construct criminal profiles for serial crimes that are not readily solved through conventional police investigative methods. Dr. Kocsis and his colleagues developed highly regarded profiling models based on large-scale analyses of serial murder, rape, and arson. Their system which is known as Crime Action Profiling (CAP) came into being as a result of a massive research study funded by the Australian government.

It was developed by Kocsis in collaboration with law enforcement agencies in that country. Their approach is distinctly different than the FBI system. The models developed by Kocsis and his associates are similar in design to in-depth structured interviews that clinical psychologists use to make diagnoses of their patients (2).
Kocsis, who is now in private practice, says that crime action profiling models are rooted in practical knowledge developed by forensic psychologists, psychiatrists, and criminologists. CAP models provide demographic, geographic, and psychographic measures or predictors of unknown subjects. He contends that a vital part of every crime action profile is an examination of the process of behavioral profiling itself. Kocsis says:
What seems to have been overlooked is any systematic examination of how to compose a profile. What type of information… should profiles contain? What type of case material do you need [in order] to construct a profile? How does the presence or absence of [case] material affect the accuracy of a profile? (3).
Kocsis and his colleagues in forensic psychology believe that the future of behavioral profiling lies in more empirically-based scientific research, similar to the beliefs of Canter and investigative psychologists. He believes that profiling is an acquired skill and that levels of ability vary greatly among practitioners. Just as some clinical psychologists are better therapists than others, some forensic psychologists are better practitioners of CAP than others. Kocsis readily admits that CAP is not an exact science.
When asked by the APA Monitor on Psychology whether the practice of profiling is more of an art or a science, Kocsis said, “Realistically, I think it is probably a bit of both." Nevertheless, his CAP system has received acceptance among forensic psychologists, criminologists, and profilers around the world.
Follow me @DocBonn on Twitter and visit my website at docbonn.com.
1. Canter, D.V., Alison, L.J., Alison, E. and Wentink, N. 2004. “The organized/disorganized typology of serial murder: Myth or model? Psychology, Public Policy and Law, 10 (3), pp. 293-320.
2. Kocsis, R.N. 2006. Criminal Profiling: Principles and Practice. Totowa, NJ: Humana Press.
3. Winerman, L. 2004. “Criminal profiling: The reality behind the myth.” Monitor on Psychology, 35 (7), p. 68.

Scott Bonn, Ph.D., is a criminologist, TV news commentator, and best-selling author of Why We Love Serial Killers: The Curious Appeal of the World's Savage Murderers.
- Find a Therapist
- Find a Treatment Center
- Find a Psychiatrist
- Find a Support Group
- Find Teletherapy
- United States
- Brooklyn, NY
- Chicago, IL
- Houston, TX
- Los Angeles, CA
- New York, NY
- Portland, OR
- San Diego, CA
- San Francisco, CA
- Seattle, WA
- Washington, DC
- Asperger's
- Bipolar Disorder
- Chronic Pain
- Eating Disorders
- Passive Aggression
- Personality
- Goal Setting
- Positive Psychology
- Stopping Smoking
- Low Sexual Desire
- Relationships
- Child Development
- Therapy Center NEW
- Diagnosis Dictionary
- Types of Therapy

Understanding what emotional intelligence looks like and the steps needed to improve it could light a path to a more emotionally adept world.
- Coronavirus Disease 2019
- Affective Forecasting
- Neuroscience

Copy of Change Your World Week for grading
- Change Your World Week
- Access to Healthy Food
- Addiction Unplugged
- Beyond the Surface: Exploring the Roots and Effects of Racial Profiling
- Bridge the Gap: Healing Racial Inequalities in Healthcare
- Discrimination in the Workplace
- Dismantling Inequality In K-12 Education
- The Effects of Cultural Appropriation
- Erasing Black History from Curriculum
- A Fight Against Mass Incarceration
- The Harmful and Negative Effects of Cultural Appropriation
- Hate No More
- How can we decrease Environmental Racism, and improve the living situation of marginalized neighborhoods?
- How Systemic Racism Affects Access to Mental Health Care
- How Xenophobia Continues to Negatively Impact Immigration Policies in America
- Human Trafficking
- Racial Discrimination in Hiring
- Racial Discrimination in Housing
- Racial Disparities Among Maternal Mortality
- Racial Disparities in Health Outcomes and Life Expectancy Among Ethnic Groups
- Racial Disparities in Infant Mortality
- Racial Disparities in Sentencing
- School Punishment: A Closer Look
- The School-to-Prison Pipeline: the Awful Truth
- Seeking Healthcare as a Person of Color
- Stereotypes in the Media
- The Truth of Fast Fashion
- Why is Plastic Pollution a Social Issue?

What is racial profiling?
Racial profiling is the discriminatory practice of targeting individuals or groups for suspicion, investigation, or enforcement based solely on their race, ethnicity, or national origin. it involves the use of stereotypes and assumptions about certain racial or ethnic groups to guide law enforcement actions, security measures, or other institutional practices. racial profiling often results in the disproportionate surveillance, stops, searches, and arrests of marginalized communities, particularly black, indigenous, and people of color (bipoc). this practice undermines the principles of equality and justice by perpetuating systemic biases and reinforcing harmful stereotypes. ultimately, racial profiling contributes to the erosion of trust between communities and institutions, exacerbating social divisions and hindering efforts to create inclusive and equitable societies., social impact of racial profiling.

Legal and Ethical Concerns

Policing Practices and Patterns
Racial profiling is pervasive in policing practices, manifesting in disproportionate stops, searches, and arrests of minority individuals. These patterns often reflect implicit biases among law enforcement officers, leading to discriminatory treatment based on race or ethnicity. Such practices erode trust in law enforcement and undermine community relations, making it difficult to foster cooperation and collaboration in crime prevention efforts. Addressing these disparities requires systemic reforms and cultural sensitivity training within law enforcement agencies.
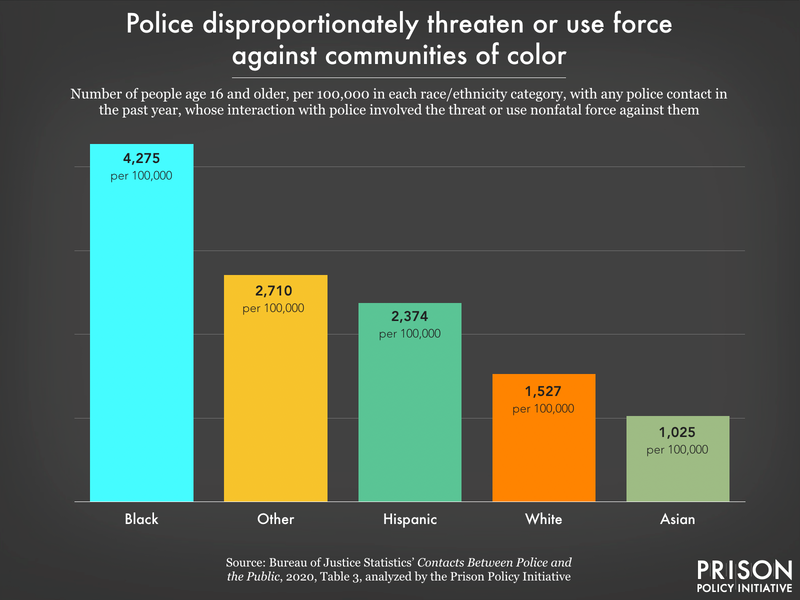
Racial Profiling in Counterterrorism:
Racial profiling is a contentious issue in national security and counterterrorism efforts, where it is sometimes used as a means to identify potential threats. However, relying on race or ethnicity as indicators of suspicious behavior can lead to unjust targeting of innocent individuals and communities. Moreover, profiling based on stereotypes can obscure genuine security risks and divert resources away from more effective investigative methods. Balancing security concerns with civil liberties requires nuanced approaches that prioritize intelligence-driven strategies over blanket profiling tactics. Perceptions of Black individuals as being more likely to engage in criminal or terrorist activities are often influenced by stereotypes and biases, perpetuating racial profiling and systemic discrimination. Nonetheless, in the chart provided below, it is evident that whites exhibit the highest rates of terrorism.
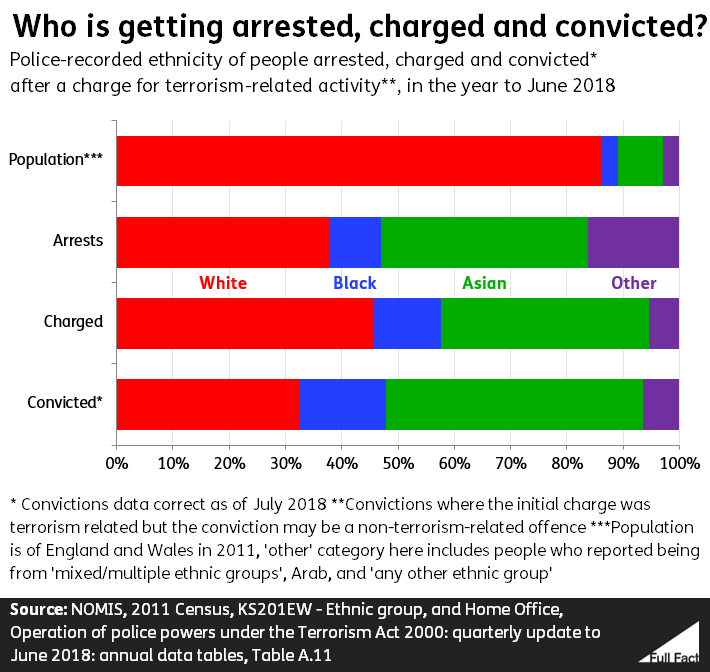
Possible Solutions
Addressing racial profiling requires multifaceted solutions that address systemic issues and promote equity and justice. First, implementing comprehensive training programs for law enforcement personnel to raise awareness about implicit biases and cultural sensitivity can help reduce discriminatory practices. Second, establishing clear policies and accountability mechanisms within law enforcement agencies to ensure fair and equitable treatment of all individuals, regardless of race or ethnicity, is essential. Finally, fostering community engagement and dialogue between law enforcement and marginalized communities can promote trust, cooperation, and mutual understanding, contributing to a more inclusive and equitable society.
How do you perceive the role of racial profiling in contemporary society's law enforcement practices?
Short clips from the australian human rights commission.
- Elevator - Racism. It Stops With Me
- Taxi - Racism. It Stops With Me
Works Cited
Laurencin, Cato T. and Joanne M Walker. “Racial Profiling is a Public Health and Health Disparities Issue. Journal of Racial and Ethnic Health Disparities, U.S. National Library of Medicine, June 2020, www.ncbi.nlm.nih.gov/pmc/articles/PMC7231642/ .
Delsol, R. (2015). Racial profiling. Racial profiling . https://www.crimeandjustice.org.uk/publications/cjm/article/racial-profiling
End Racial Profiling Act. (n.d.). Human Rights Campaign. https://www.hrc.org/resources/end-racial-religious-profiling-act
Yan, Holly. “This Is Why Everyday Racial Profiling Is so Dangerous.” CNN, 11 May 2018, www.cnn.com/2018/05/11/us/everyday-racial-profiling-consequences-trnd/index.html.
- << Previous: Addiction Unplugged
- Next: Bridge the Gap: Healing Racial Inequalities in Healthcare >>
- Last Updated: Apr 5, 2024 9:17 AM
- URL: https://library.delta.edu/cywwgrading
Debunking the perceived associations between ethnicity and youth gangs
In Australia, as with many other countries around the world, migrant young people receive significant media and political attention as alleged perpetrators of gang-based criminal activity.
Media and political discourses consistently portray them as being responsible for antisocial, delinquent and criminal behaviour, which in turns fuels public perceptions that young people are out of control, threatening, violent and dangerous.
Assumptions are often erroneously made about the behaviour of youth by their ethnicity. Gang identities are frequently described by police and media in racial terms.
Our new research debunks the myths. Our paper in the Journal of Youth Studies shows that after separating ethnicity from other “youth crime” risk factors (family, neighbourhood, individual “delinquency”, school, peers, law enforcement) there is, in fact, no association between migrant status and youth crime in Australia.
“This is not to say that no members of youth gangs in Australia are first or second-generation migrants,” the paper states, “but rather that the perception of gangs based exclusively on ethnic identity is unfounded.”
Racial profiling ‘detrimental’
The study explores the risk factors and uses data from the Australia Youth Safety Survey from 2945 young people aged 14-25 years.
While it acknowledges youth gangs and youth violence do exist, it says racial or ethnic profiling of migrant cohorts in relation to crime is “detrimental to those who are affected by such labels” and affected by “moral panics created by media and political discourse”.
This isn’t a new phenomenon. After all, this has been a consistent feature over time, with “Asian gangs” in the 1990s in the US, UK and Australia, “Middle-Eastern gangs” around the time of 9/11, “Turkish gangs” and “Albanian gangs” in the UK and Europe, and “African gangs” in Australia since the early 2000s.
Read more: Unlocking the fear and myths around ‘African gangs’ in Melbourne
This has detrimental impacts on the sense of belonging felt by migrant young people. The teenage years are vital, formative years for developing identity, self-worth and purpose.
Constantly facing scrutiny from the public, politicians and media because of physical appearance is taxing.
Traditionally, gang involvement can be seen through multiple marginalities, with ecological, historical, structural, and the social control factors coalescing with street socialisation to lead to gang membership.
Factors preventing gang involvement
Results show being a first or second-generation migrant has no relation to gang membership. That is, neither being a migrant, nor a child of a migrant, increases the odds of joining a gang.
While we didn’t identify any factors that make a young person more likely to be involved in a gang, we found several factors that reduced the odds of them being in a gang.
Having a high sense of self-control and strong morals actively worked to prevent gang membership. These factors are instilled in children from a young age.
Read more: Ripple effect: The social consequences of the ‘everyday’ hate crime
A youth gang is defined as “any durable, street-oriented youth group whose involvement in illegal activity is part of its group identity”.
We also analysed the importance of neighbourhood conditions on youth gang membership to explore ecological differences in the environment in which a young person lives.
At the wider neighbourhood level, gang membership is more likely for those who live in a neighbourhood with high levels of disorder, or cohesive, tight-knit neighbourhoods.
Integration undermined by messaging
The challenges associated with immigration and settlement experiences are numerous, and community integration of immigrants is undermined by racialised public messaging strategies that promote dichotomies of “us” and “them”, and seek to accentuate differences.
A focus on creating and strengthening positive images of immigrants, rather than instilling blame and mistrust, will be more conducive to social benefits for society.
Building on this research, the team plans to undertake future research into the impact of stigma and labelling on young people from migrant backgrounds, and develop strategies to build community capacity to counter these harmful narratives to ensure they’re not detrimental to young peoples’ development.
This article was co-authored by Associate Professor Angela Higginson, Faculty of Creative Industries, Education and Social Justice, Queensland University of Technology.
- youth crime
- youth gangs
- youth crime and ethnicity
- youth gangs and migrants
- youth violence

Kathryn Benier
Senior Lecturer in Criminology, School of Social Sciences

Ripple effect: The social consequences of the ‘everyday’ hate crime
New research shows that those who witness hate crime express greater anger towards ethnic minorities.

Reinforcing racism
The so-called Moomba 'riot' and subsequent media sensationalism has had a detrimental effect on young South Sudanese in Victoria.

Deconstructing 'African gangs'
A moral panic and sensationalist media reporting demonstrates how rhetoric can promote fear and intolerance.

A tale of two cities
Melbourne is undoubtedly a multicultural hub, but questions over social exclusion show that it's far from perfect.

The legacy of the Moomba 'riot'
Missing from the debate about "ethnic gangs" are the voices of young people from the South Sudanese community.
You may republish this article online or in print under our Creative Commons licence. You may not edit or shorten the text, you must attribute the article to Monash Lens, and you must include the author’s name in your republication.
If you have any questions, please email [email protected]
Republishing Guidelines
https://lens.monash.edu/republishing-guidelines

- Reference Manager
- Simple TEXT file
People also looked at
Original research article, psychological profiling of hackers via machine learning toward sustainable cybersecurity.

- 1 College of Computing and Information Sciences, Karachi Institute of Economics and Technology, Karachi, Pakistan
- 2 School of Business, American University of Ras Al Khaimah, Ras Al Khaimah, United Arab Emirates
- 3 Department of Computer Science, University of Technology Sydney, Sydney, NSW, Australia
- 4 College of Humanities and Social Sciences, Libraries and Information Department, Princess Nourah Bint Abdulrahman University, Riyadh, Saudi Arabia
This research addresses a challenge of the hacker classification framework based on the “big five personality traits” model (OCEAN) and explores associations between personality traits and hacker types. The method's application prediction performance was evaluated in two groups: Students with hacking experience who intend to pursue information security and ethical hacking and industry professionals who work as White Hat hackers. These professionals were further categorized based on their behavioral tendencies, incorporating Gray Hat traits. The k-means algorithm analyzed intra-cluster dependencies, elucidating variations within different clusters and their correlation with Hat types. The study achieved an 88% accuracy in mapping clusters with Hat types, effectively identifying cyber-criminal behaviors. Ethical considerations regarding privacy and bias in personality profiling methodologies within cybersecurity are discussed, emphasizing the importance of informed consent, transparency, and accountability in data management practices. Furthermore, the research underscores the need for sustainable cybersecurity practices, integrating environmental and societal impacts into security frameworks. This study aims to advance responsible cybersecurity practices by promoting awareness and ethical considerations and prioritizing privacy, equity, and sustainability principles.
1 Introduction
The rise of the Internet has led to a corresponding surge in cybercrime instances, as computers have become integral to various facets of life, including commerce, entertainment, and government operations ( Siddiqi et al., 2022 ). Additionally, the emergence of novel networking models such as mobile, wireless, cognitive, mesh, Internet of Things (IoT), and cloud technologies has further complicated the landscape of cybersecurity ( Islam and Shaikh, 2016 ; Tandera et al., 2017 ; Wong et al., 2020 ). This evolving scenario poses significant challenges in combating cyber threats. Cybercrime utilizes computers as tools and mediums for criminal activities, targeting security objectives such as privacy, confidentiality, availability, and integrity of information. Common cyber crimes encompass phishing, honeypots, social engineering, spoofing, and disseminating viruses or worms.
The discussion on cybercrimes highlights previous research findings indicating that these activities are primarily carried out by individuals with low technical sophistication and are driven by motivations such as fame, financial gain, revenge, and self-satisfaction ( John et al., 1999 ; Gulati et al., 2016 ; Buch et al., 2017 ; Matulessy and Humaira, 2017 ; Suryapranata et al., 2017 ). Hacking, a specialized form of cybercrime, involves illegally accessing personal or sensitive data using technology and knowledge, with various countermeasures such as firewalls and intrusion detection systems in place to mitigate such threats ( Gulati et al., 2016 ; Akdag, 2020 ). Building on this understanding, the concept of “sustainable cybersecurity” is introduced in this study, emphasizing the need for enduring and efficient strategies to adapt to the evolving challenges posed by hackers ( Shackelford et al., 2016 ; Medoh and Telukdarie, 2022 ). This approach aligns with corporate social responsibility (CSR) practices, with an increasing number of managers recognizing cybersecurity as integral to safeguarding customers and the public, thereby expanding risk management practices to encompass the prevention of social-engineering-linked attacks ( Shackelford et al., 2016 ; Medoh and Telukdarie, 2022 ).
In this study, the term “sustainable” indicates the formulation of enduring and efficient cybersecurity strategies. Within this framework, sustainability encompasses the creation of practices, methodologies, and tools capable of persisting and adjusting over time to adeptly confront the continuously evolving challenges presented by hackers. The concept of “Sustainable Cybersecurity” suggests implementing robust and resilient defense mechanisms designed not only to react to existing threats but also to foresee and alleviate potential risks. For instance, social engineering, which focuses on exploiting human psychology to both perpetrate and prevent cyberattacks, diverges from relying solely on technical hacking methods. It is associated with attacks such as phishing emails, deepfakes, and spear phishing ( Siddiqi et al., 2022 ). This field also underscores the application of social psychology to reinforce cybersecurity policies within organizations. Tools such as the Cyber Risk Index (CRI) and the Cybercrime Rapid Identification Tool (CRIT) ( Buch et al., 2017 ) can be implemented and utilized to bolster this approach. The gap between “social engineering” linked attacks and their avoidance measures creates an ongoing challenge for security experts. Therefore, security through technology is not the sole solution; it is the much-needed side to sustain the cyber security world. Even the World Economic Forum declares social engineering cyber-attacks as the reason for organizations' alarming security situation.
This study is grounded in research utilizing data collected from personality trait rating scales ( Buch et al., 2017 ; Novikova and Alexandra, 2019 ; Wong et al., 2020 ), with Matulessy and Humaira (2017) providing insight into hacker personality profiles based on the Big Five Personality Traits model. The aim is to construct a machine learning model capable of predicting and analyzing the personality profiles of hackers, utilizing the Big Five personality model and validating its reliability. Understanding the psychology or personality of hackers is essential for implementing effective preventive measures ( Javaid, 2013 ; Ali et al., 2020 ). The research inquiry addresses the dominant personality traits (openness to experience, conscientiousness, extraversion, agreeableness, and neuroticism) abbreviated as OCEAN that are exhibited by various hacker types (White, Black, and Gray Hats) and how these traits can be accurately identified and categorized through a machine learning-based approach. This identification mechanism holds promise for informing targeted cybercrime prevention strategies. Figure 1 illustrates the research flow and target, detailing a secure model for predicting personality traits. The authors devised a questionnaire based on the OCEAN model and applied machine learning models to classify hacker types.
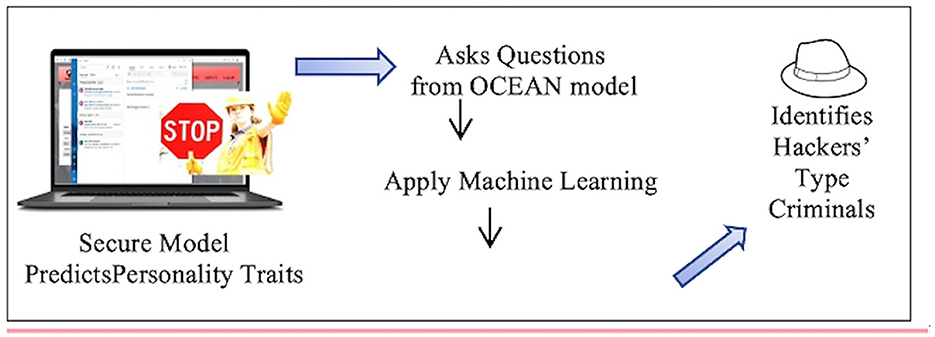
Figure 1 . Research flow and target.
Different sections in this article are as follows. The section covers relevant literature, Section 3 covers the research method, Section 4 covers experimentation and results of the secure model, Section 5 covers discussions on results and threats to validity, and Section 6 concludes the study and highlights potential future work.
2 Literature review
In today's technologically advancing world, cybercrimes are on the rise. This section discusses targeted studies published previously to investigate contemporary cybercriminal acts.
In the realm of cybersecurity research, many studies have leveraged machine learning methodologies to delve into the intricacies of cybercrime data analysis. Concurrently, Geluvaraj et al. (2019) have tackled prevalent cybersecurity challenges, proposing innovative machine-learning solutions for their mitigation. Drawing from diverse machine learning techniques, Zheng et al. (2003) have unraveled concealed patterns within crime data, underscoring the indispensability of data-driven approaches in cybercrime investigations. Meanwhile, Islam et al. (2021) have explored the transformative potential of artificial intelligence and deep learning in bolstering cybersecurity frameworks. Adewumi and Akinyelu (2017) have harnessed machine learning algorithms to discern distinctive authorship patterns and shed light on attributing illicit messages in cyberspace. Pastrana et al. (2018) proposed a comprehensive approach to counter the spread of fake news online, leveraging machine learning technologies. This effort aligns with the rise of blockchain technology, which has become a cornerstone in fortifying applications across mobile and cloud networks, exemplified by the study by Mohammed et al. (2023) and Tamboli et al. (2023) . Furthermore, pioneering approaches, such as the Low-Latency and High-Throughput Multipath routing technique, as elucidated by Ramachandran et al. (2022) , have been devised to counter novel threats such as black hole attacks. Meanwhile, Imran et al. (2019) have employed machine learning and nature-inspired algorithms to scrutinize credit card data, fortifying fraud prevention measures. Against this backdrop, integrating artificial intelligence, machine learning, and IoT technologies has heralded a new era in cybercrime analysis and cybersecurity enhancement, a paradigm eloquently underscored by Sood and Enbody (2013) and epitomized in the broader research landscape.
Bridging the gap between psychology and information security, investigations by Del Pozo et al. (2018) and Chayal and Patel (2021) have illuminated the psychological underpinnings crucial to fortifying cyber defenses. Suryapranata et al. (2017) studied the activities of a user forum to identify the variables that can be used to predict the likelihood of a user being involved in cybercrime. An intervention can benefit in avoiding a crime. The study reports users in an underground forum as providers, advertisers, and buyers ( Fox and Holt, 2021 ). Alashti et al. (2022) employed logistic regression and latent class analysis to identify risk factors associated with juvenile hacking. Odemis et al. (2022) observed the behaviors of Iranian hackers via interviews. It was found that young hackers enjoyed the pleasure of cybercrime. Back et al. (2019) addresses whether we can analyze the psychology and behavior of a hacker by investigating their computer logs. A honeypot system was created for this purpose. Suryapranata et al. (2017) built profiles of cybercriminals by analyzing court records and media documents for incidents in South Korea. It was found that there is a difference in motivation between young and adult hackers.
The hidden Markov Model has been used in various studies to identify the personality traits of cybercriminals over social media networks ( Xie and Wei, 2022 ). The method comprises a training and identification phase. The average likelihood of the observation sequence is performed in the identification phase. The text information posted by users over social media, blogs, and language characteristics can be analyzed using neural networks, logistic regression, and support vector machines for personality analysis ( Golbeck et al., 2011 ; Adali and Golbeck, 2012 ; Lima and De Castro, 2014 ).
Novikova and Alexandra (2019) discuss the Five Factor Model in detail. The Five Factor Model suggests that all people, regardless of their age, gender, or culture, share some essential traits, but every person differs in their degree of manifestation. John et al. (1999) discuss the result of an eight-item Cybercrime Rapid Identification Tool (CRIT). It evaluates the psychometric properties of the proposed scale on samples of secondary school and university students. A study on Personality Prediction Systems from Facebook Users attempts to build a system to predict a person's personality based on user information ( Buch et al., 2017 ). The research mentioned in the above studies discusses cybercrimes in general. This includes the essential five personality traits all humans are divided into, the tool for identifying Cybercrimes, and especially the personality profiles of the hackers.
In the realm of hacker classification, researchers often employ a framework akin to the concept of White, Black, and Gray Hats ( Buch et al., 2017 ). White Hat Hackers, the first category, embody ethical hacking practices. Despite engaging in illegal activities, they channel their skills toward constructive and positive ends, often for the betterment of security systems. Contrastingly, Black Hat Hackers, the second category, operate with nefarious intent, breaching security measures for personal gain. Their activities typically involve theft, exploitation, and the illicit sale of data driven by self-interest. Gray Hat Hackers constitute the third category, occupying a space between the ethical and the malicious. While they may identify and exploit vulnerabilities, their actions are not motivated by financial gain. However, their endeavors still fall within the realm of illegality, as they typically lack consent from the system's owner. Gray Hats often have associations with Black Hat hackers, blurring the lines between ethical and unethical practices. In another perspective Javaid (2013) offered, Gray Hats are portrayed as reformed Black Hats. These individuals, often independent security experts, consultants, or corporate researchers, transition from illicit activities to a more legitimate stance. Notable figures such as Kevin Mitnick exemplify this transformation.
In summary, the delineation between White, Black, and Gray Hats provides a nuanced understanding of hacker motivations and behaviors, shedding light on the spectrum between ethical and malicious hacking practices. Each of the three types of hackers utilizes their skills for different purposes. The previous research defines that each possesses other personality profiles regarding Big Five Personality Traits (OCEAN Model). The research study conducted by Matulessy and Humaira (2017) described the personality profiles of the hackers concerning the Big Five Personality Traits model using 30 hacker subjects and utilized descriptive qualitative research.
The research claims that hackers are positioned in the middle of the personality trait of extraversion regardless of the categories of hackers. White Hats have more dominant personality traits of agreeableness, and Black Hats have more dominant personality traits of openness to experience. In contrast, Gray Hats have more dominant personality traits in terms of neuroticism (see Table 1 ). Table 2 presents the summary of the previous research.
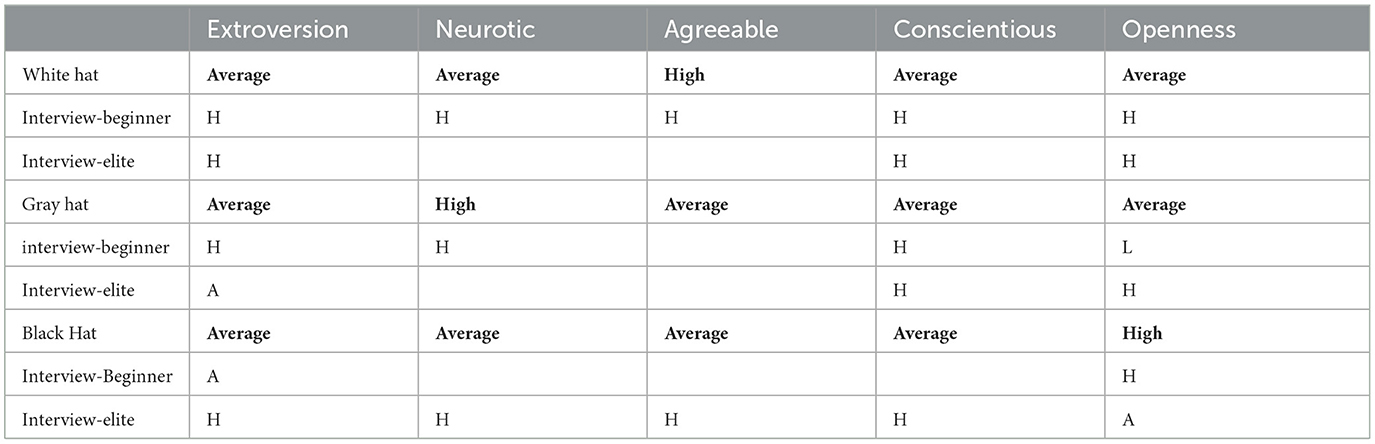
Table 1 . OCEAN traits claimed in earlier research ( Matulessy and Humaira, 2017 ).
Table 2 . Summary of previous research and hacker profiling gap analysis.
Previous researchers have primarily focused on broad aspects of cybercrime identification and personality prediction. While some studies have explored personality prediction systems utilizing social media platforms ( Buch et al., 2017 ), others have theorized based on research findings obtained from personality trait rating scales, interviews, surveys, and questionnaires ( Matulessy and Humaira, 2017 ; Novikova and Alexandra, 2019 ). However, the scope of investigation in these studies remains somewhat limited, predominantly addressing general trends rather than delving into nuanced aspects of cybercriminal behavior and personality profiling.
This research implements a machine learning-based model that predicts and analyzes the personality profiles of hackers using the Big Five personality model, and it also validates the model on real-life datasets. This study mainly targets White and Gray hackers who either use hacking as their profession or have career motivation to adopt it professionally. For detailed classification, refer to the study by Martineau et al. (2023) and Chng et al. (2022) w.r.t hacker type, their possible motivations, and personality type.
3 Research methodology
Figure 2 shows the research method adopted in this study ( McAlaney et al., 2020 ; Bakas et al., 2021 ). This study uses a machine learning-based approach to validate the classification of different hacker types (White, Black, and Gray Hats) based on their dominant personality traits (openness to experience, conscientiousness, extraversion, agreeableness, and neuroticism).
Figure 2 . Research method.
The K-means algorithm was chosen for its simplicity, ease of implementation, and speed. It is widely used for clustering tasks, including in high-volume datasets such as those associated with criminal data, as described by Aldhyani and Alkahtani (2022) . K-means can generate clusters based on similarities in the data, aiming to group data points close to each other while being far from points in other clusters. This study applied K-means to cluster individuals based on their responses to personality trait questions. By clustering individuals with similar personality trait profiles together, the algorithm aids in identifying distinct groups or “clusters” that may correspond to different types of hackers based on their dominant personality traits. The study also seeks to develop an effective hacker identification mechanism that can accurately categorize these traits and contribute to developing targeted cybercrime prevention strategies related to social policies.
The Big Five Inventory is a 44-item inventory that measures an individual on the Big Five Factors (dimensions or traits) of personality. Each of the five factors is then further divided into personality characteristics. The inventory shares some questions for generic OCEAN personality traits. These are given in the dataset of Kaggle ( Akdag, 2020 ). A reduced set of questions was used from the Five Personality questionnaire comprising 40 questions ( Akdag, 2020 ). The users were asked to indicate their favorable responses to the questionnaire items by selecting an appropriate score. After collecting the questions' responses, a machine learning code runs and predicts results against all five personality traits. Based on the results, different hacker types are identified.
3.1 Research questionnaire
There are several instruments to measure the Big Five Trait Factors, such as the Big Five Inventory (BFI), the NEO Personality Inventory-Revised (NEO-PI-R), and the International Personality Item Tool (IPIP). This study used the dataset constructed from the IPIP for our research. This dataset was collected (2016–2018) through an interactive online personality test and comprises 10,12,050 records ( Akdag, 2020 ). The training dataset trains the clustering model for OCEAN trait prediction.
Following the points concluded in the research mentioned in Table 1 , 21 questions were selected. Redundant reverse questions were not included to reduce user frustration. In the questionnaire development process, the reverse questions are normally designed to verify the authenticity of answers recorded by random users.
Suárez Álvarez et al. (2018) demonstrated the conventional way of handling reverse coding. Here, the reduction was made for all reverse-scored questions included in the 40 questions. These were negatively phrased to ensure the user knew his point of view. Including such questions requires reserve scoring. The negative consequences of using the reverse scoring include a) the flawed measurement precision of the instrument, b) the variance of the combined form is reduced, c) examinees' scores differ significantly from those obtained in tests where all of the items are of a similar form, and d) verbal skills influence examinees' responses ( Suárez Álvarez et al., 2018 ). Minor changes in wording can also have a significant effect on responses. One should, therefore, be careful when looking at alternative wordings. Negative words such as “not” should be avoided in questions as respondents easily miss them. In addition, using “not” in a scale such as “Satisfied,” “Neither,” and “Not satisfied” does not provide a true opposite as defined by the Australian Statistic Bureau ( Corallo et al., 2022 ). The questions were then rephrased from native English speakers' style into a more understandable one for non-native speakers. See Table 3 for a detailed set of questions used in this study.

Table 3 . Research questions with no reverse questions.
3.2 Questionnaire reliability
The questionnaire's accuracy and precision, i.e., its internal validity (consistency) or reliability, have been checked using Cronbach's alpha score. Its value was reported as 0.874 in previous research ( Matulessy and Humaira, 2017 ) on 40 questions. In this research's reduced set of 21 questions, its value is 0.82, which shows acceptable reliability, i.e., >0.7. It always gives the same results when applied to the same group at different times or circumstances ( Matulessy and Humaira, 2017 ).
4 Experimentation of results of secure model
4.1 algorithms used and experimentation.
The research experimentation is based on two algorithms:
1. The machine learning-based OCEAN traits identification dataset is from Kaggle, developed by Akdag (2020) .
2. Identification of specific OCEAN traits-related combinations found in criminals and hackers.
The experiment starts with creating an optimal number of clusters on the training dataset downloaded from Kaggle ( Akdag, 2020 ). The k-means algorithm generates clusters (groups of similar data) because of its ease of implementation, simplicity, and speed, which is very appealing in practice. This has been described in detail by Aldhyani and Alkahtani (2022) , who targeted the classification of criminal data. According to the study, K-means is suitable for high-volume crime datasets and can help to extract useful information.
K-means applied in this research is a complete, partitioned clustering technique that attempts to find user-specified clusters (K) represented by their centroids. The distance between any two points in different groups is larger than the distance between any two points within a group. Well-separated clusters do not need to be spherical but can have any shape ( Tan et al., 2016 ).
Figure 3 shows methods Python uses to calculate an optimum cluster value. The KElbowVisualizer or elbow method selects the optimal number of clusters by fitting the model with a range of values for K, which shows that the calculated value of K is 6. The Silhouette coefficient method is used to know the truth about the dataset by computing the density of clusters. This produces a score between 1 and −1, where 1 is a highly dense cluster and −1 is a completely incorrect cluster. Here, the value is approximately 0.06, which shows that the number of clusters in this research is dense and thus correct.
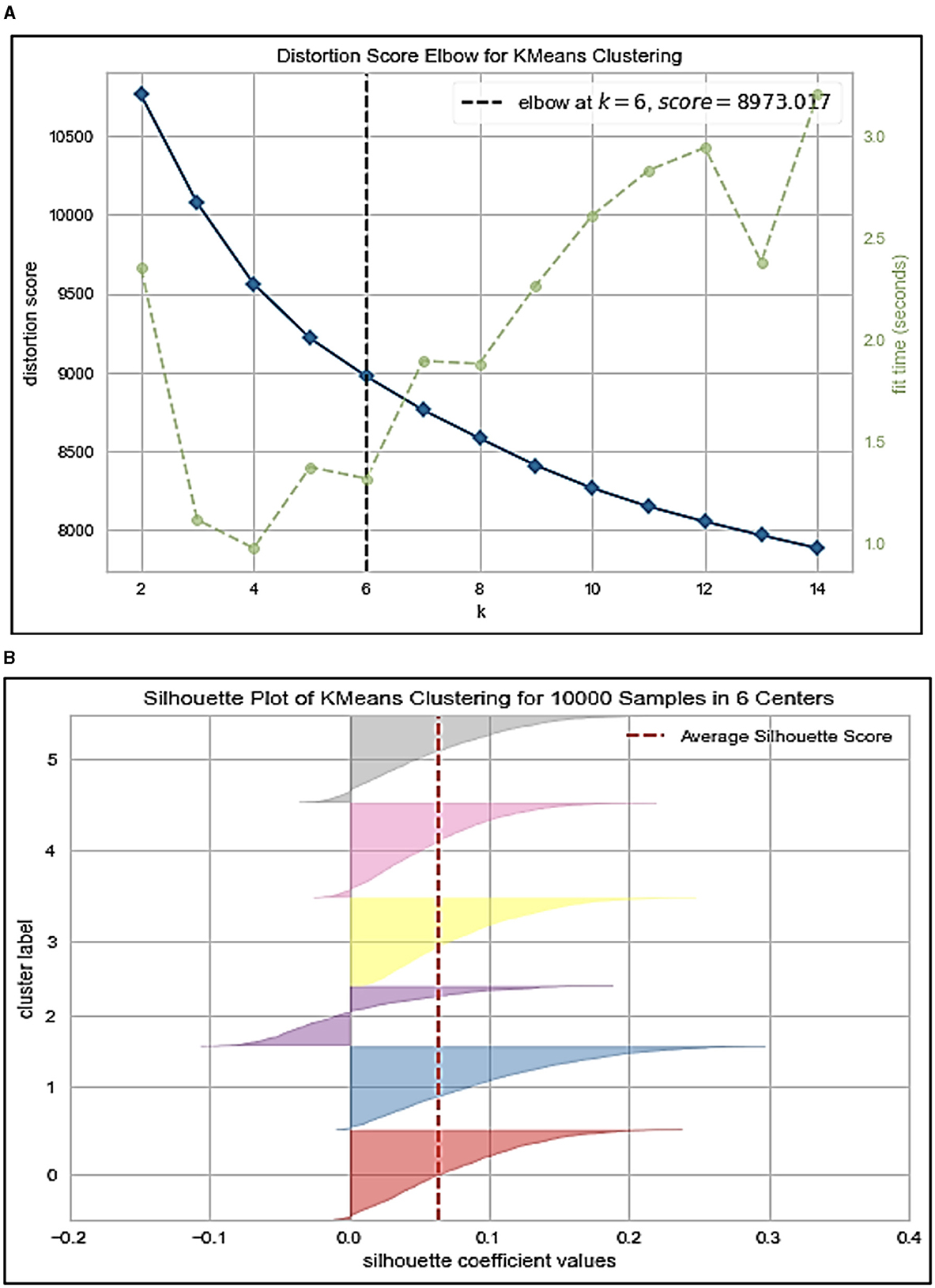
Figure 3 . Optimal cluster number. (A) KElbowVisualizar; (B) Silhouette coefficient.
After clustering the training dataset on 6 clusters (0–5), the score of the five personality traits is calculated individually based on the responses to the questions. Then, the system is trained to predict the cluster for each dataset and calculate each trait's score respectively (see Figure 4 ). Figure 4 shows how many datasets were assigned to identify each cluster; even the worst count shows 6,200 records.
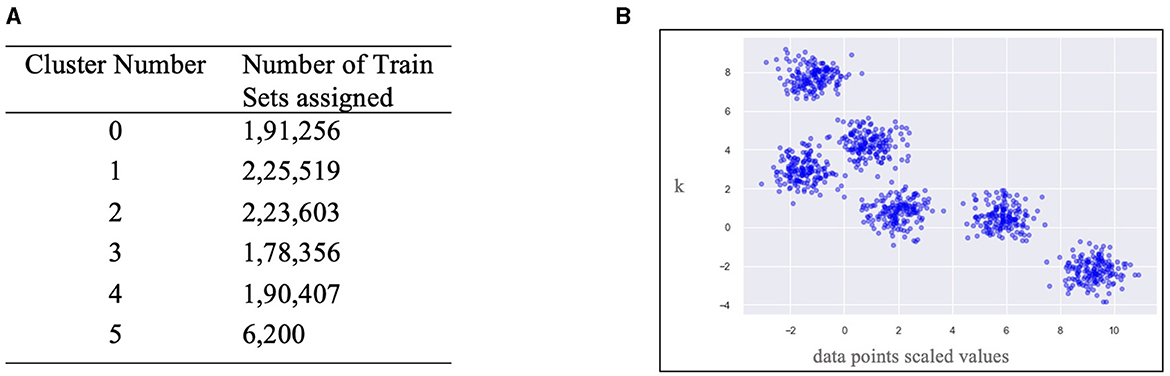
Figure 4 . Cluster's centers picked by K-means Python estimator. (A) Training data distribution across calculated clusters. (B) Train data points spread across calculated clusters.
4.2 Scoring values to identify hackers
The same technique is applied to the responses taken from the test datasets, which were collected on 21 questions and converted into responses. According to the user's responses, the system calculates the score of each personality trait. It determines the cluster where the user belongs to three types of hackers who have one most dominant personality trait among all. In previous research ( Matulessy and Humaira, 2017 ), as shown in Table 1 , for OCEAN traits, the generalized most dominant traits are agreeableness for the White hacker, openness to experience for the Black hacker, and neuroticism for the Gray Hackers. If any of these traits have the maximum score among all four traits, there is a strong possibility that the person can be a hacker or have any illegal intentions.
4.3 Organizational preventive measures
If the user is found to be suspicious, the system temporarily holds that user on a “watch list” before granting further access to the site or organizational sensitive resources. The organization can add its name to the social policy list to use resources under organizational or web access monitoring software. As mentioned earlier, proper social security and communication policies should be designed based on identified “social psychology” and Crime Risk Index, as suggested by Siddiqi et al. (2022) , or Cybercrime Rapid Identification Tool (CRIT), as suggested by Buch et al. (2017) , must be maintained to differentiate naïve users from the one who can harm other colleagues or employer organization.
5 Validation of secure model
Rather than blindly implementing clusters on previous research claims ( Matulessy and Humaira, 2017 ), its proper validation is performed on (a) average scores as well as on (b) clusters using a prediction performance accuracy measurement of machine learning ( Matulessy and Humaira, 2017 ). In validating the secure model, several techniques are applied to ensure the reliability and accuracy of the model's predictions. These include comparing average scores of the test dataset with established category claims for hacker types, validating clustering outcomes through cluster predictions on the test dataset, analyzing correlations between personality traits using Spearman's rho, quantitatively measuring model performance, examining demographic information, and mapping clusters to hacker types based on observed traits. Collectively, these validation techniques ensure the effectiveness and robustness of the model in identifying hacker types based on personality traits.
5.1 Data collection for test set
Test data were collected reliably for a major research project to gather personality traits data across various professional domains in computer science. These data were used to develop a career counseling system for final-year students in higher education institutions. It included responses from final-year students and professionals in domains such as information security, such as hackers, auditors, trainers, and security administrators. The response rate was highly encouraging. Out of 300 records, around 32 were related to hackers, with 30 ultimately included after data cleaning. This aligns with validation criteria from previous psychology research. Despite the lack of progressive research in hacker personality detection, the study aimed to contribute positively to career counseling. The data collection process was based on high trust, as participants and the research team belonged to the same information security professionals community. Data collected from final-year students were deemed reliable due to their field of interest and relevant academic projects noted during their tenure.
5.2 Demographics on test data
Demographics and frequency scores of the collected dataset for Gray and White hackers are given in Table 4 . The total respondents for this study were 30 professionals and final-year students who intend to adopt hacking as their profession. The majority of them were male respondents, whereas only two were female respondents. Table 5 shows all possible details of the collected test dataset.
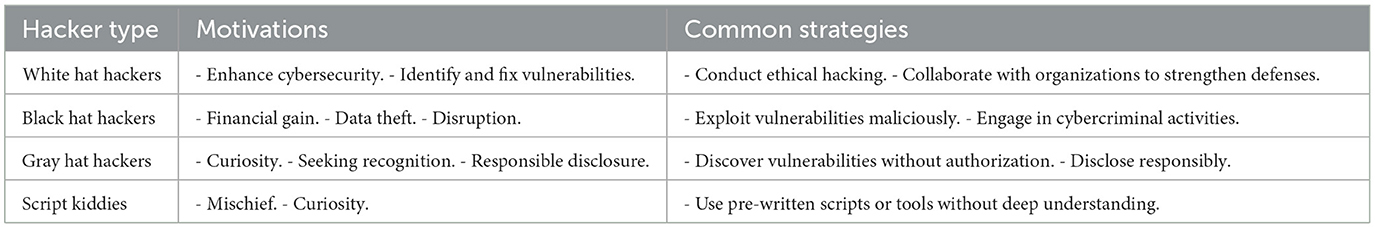
Table 4 . Hacker type, motivations, and common strategies.
Table 5 . Number of test datasets and their demographics.
5.3 Cluster trends on test dataset with hat type mapping for validation
First, the test dataset was given as an input in the clustering algorithm generated, as discussed in Section 4, and clusters were predicted on all datasets. The cluster distribution will be discussed in detail in later sections.
To better understand the cluster trends and establish their mapping with Hat types, there was a need to consider the correlation between the traits on test data. Correlation is a statistical measure that measures the extent to which two variables are in a linear relationship without calculating cause and effect. This means they constantly change; when one changes, the other also changes. It is measured on a scale of −1/0/+1, which means an indirect, no, or a direct relationship. For the stated reason, Spearman's correlation was applied to the test dataset (see Table 6 ), showing a few other significant but moderate level inter-dependencies between traits in the correlation coefficient range +/– 0.4.
Table 6 . Spearman's rho correlation checking to make multiple trait-based Hat-type selections.
These visible correlations can be generalized as given by Matulessy and Humaira (2017) :
a. The openness to experience keeps conscientiousness closer. High openness was claimed to be the major trait of Black Hats.
b. Neuroticism depends directly on no other traits. High neuroticism was claimed to be the major trait of Gray Hats.
c. Agreeableness keeps extroversion closer. High agreeable was claimed to be the major trait of White Hats.
Figure 5 graphically shows all 6 clusters with average score values and reflects apparent behavior across each cluster on both training and test datasets. It is visible from the two graphs that the K-means clustering algorithm does not just check the average score values while designating the cluster numbers but also reflects intra-cluster trends within specific clusters. Following are the conclusions to map the cluster numbers with the Hat types purely over hacker's data:
1. The first cluster, “Cluster-0,” shows the same trend among both datasets. Still, the training dataset has shown less sense of taking creative challenges by the White Hats because their job demands carefully defined method's adaptation. In this combination, the highest level starts with an extra high level of neuroticism, then comes a high level of agreeableness, conscientiousness, openness, and the last somewhat above-average level of extroversion.
• Conclusion: “Cluster-0” represents Gray Hats with the highest neuroticism; therefore, it does not depend on other traits.
2. The second cluster, which is “Cluster-1,” is closer to the first cluster but has high neuroticism and agreeableness.
• Conclusion: “Cluster-0” represents a switching behavior of White Hats with a Gray Hat tendency. White has the highest level of agreeableness but also has a high level of neuroticism; therefore, it does not depend on any other traits.
3. The third cluster, “Cluster-2,” is closer to the fourth cluster but has an average level of neuroticism.
• Conclusion: “Cluster-2” represents White Hats with average neurotic tendencies and with high agreeableness and average values of extroversion.
4. The fifth cluster, “Cluster-4,” shows the same trend captured on the training and test datasets. The highest trait is agreeableness, followed by openness, an average level of conscientiousness, and an average value of extroversion.
•Conclusion: “Cluster-4” represents White Hats with low neuroticism, high agreeableness, and average values of extroversion.
Figure 5 . Average score value against each cluster for OCEAN traits prediction on training data.
See Table 7 for clusters to Hat-type mapping with quantitative values of average scores across each trait for all clusters predicted on the test dataset.
Table 7 . Cluster to Hat-types mapping.
5.4 Validation of average scores
A test dataset of 30 records is collected to check the claims of previous research ( Matulessy and Humaira, 2017 ) without applying the clustering algorithm. In Table 7 , the test dataset matches the previous research's ( Matulessy and Humaira, 2017 ) generalized category claim of White Hats, as shown in Table 1 .
After the detailed experimentation performed in Section 4, a better interpretation of validation results on test data can be made based on Table 7 cluster to Hat-type mappings (see Table 8 ).
1. The average scores of the test dataset for professionals match the generalized score claim for White Hats in previous research ( Matulessy and Humaira, 2017 ) but show an average extroversion value (see Table 6 ); therefore, after the following cluster-level validation, it could be placed under Cluster-4.
2. The average scores of the test dataset for student hackers match the generalized score claim for White hackers ( Matulessy and Humaira, 2017 ) but show an average neuroticism value (see Table 6 ). Therefore, the student's class belongs to the White Hats but tilts toward Gray Hat traits, and after performing the cluster-level validation, it will be placed under Cluster-2.
Table 8 . Validation of average trait scores on test datasets about previous research ( Matulessy and Humaira, 2017 ).
5.5 Secure model's clustering model validation
The secure model uses the clusters to predict the criminal's or hacker's personality type.
In this section, the clustering outcomes are validated to visualize the cluster's outcome spread when run over the test dataset (see Figure 6 ). Validation was performed by making cluster predictions over the test dataset using a 6-clusters-based model trained on 21 factors-based train datasets. As shown in Table 9 , the overall prediction performance accuracy is 100% of the time. This can be seen when using the correlation information in Table 6 to better understand the varying trait-wise mapping for hackers in the test dataset.
1. The professional dataset has shown 100% accuracy as they are all White Hats since Cluster-2 and Cluster-4 represent White Hats.
2. The student's dataset predicts 88% of White Hats and 11.7% of Gray Hats or White Hats with Gray Hat tendency. Both Cluster-0 and Cluster-1 show Gray Hat tendencies.
Figure 6 . Test data points spread across the predicted clusters.
Table 9 . Distribution of test dataset on 5 and 6 cluster-based hacker identification models.
6 Discussion
This research uses machine learning to validate the proposed approach on approximately 30 real-life datasets. The application prediction performance was evaluated on (a) the final-year students who have some experience in hacking and intend to choose information security and ethical hacking as their profession and (b) professionals from the industry who are working as White Hackers. The study aimed to understand cluster trends and their association with different Hat types, requiring consideration of trait correlations in the test data. Spearman's correlation analysis was conducted, revealing moderate inter-dependencies between traits. These correlations were generalized, associating certain traits with specific Hat types.
The clustering analysis highlighted distinct trends across datasets, with clusters exhibiting varying trait compositions. The validation of these clusters using a 6-cluster model showed a high prediction accuracy of 100%, with professionals predominantly classified as White Hats and students displaying a mix of White Hat and Gray Hat tendencies. It has successfully mapped the different clusters with the different Hat types in the test dataset (see Table 9 ) with 88% accuracy. This can predict 11.7% of our false understanding of test data to consider two correctly predicted students as we conceived Gray Hats as White Hats. Previous research ( Matulessy and Humaira, 2017 ) being conducted under the psychology domain only discusses results at generalized higher levels, covers no scientific experimentation, and has no detail of cluster assignments; therefore, it was neither possible to correctly understand individual tests nor the implementation done for cyber-criminal identification as hackers.
6.1 Implications
Incorporating personality profiling methodologies within the realm of cybersecurity elicits profound ethical inquiries necessitating meticulous examination. Chief among these concerns is the pivotal issue of privacy, wherein the acquisition and scrutiny of individuals' personality traits may encroach upon their privacy entitlements, and absent explicit consent and robust protective measures, with a palpable risk of unauthorized access to sensitive personal data, potentially precipitating privacy breaches and data misuse. Additionally, the deployment of personality profiling algorithms introduces the specter of bias, engendering the prospect of unjust treatment or discriminatory practices targeting specific individuals or demographic groups.
Securing informed consent stands as a crucial element in navigating these ethical challenges. Organizations are responsible for ensuring that individuals are comprehensively informed about the intentions and potential consequences of gathering and scrutinizing their personality data for cybersecurity aims. This empowers individuals to make informed decisions regarding their participation, allowing them to grant consent or abstain. Transparency and accountability take center stage in this process, compelling organizations to openly disclose their data management procedures and to shoulder accountability for any ethical implications arising from the application of personality profiling.
Moreover, the cultivation of sustainable cybersecurity practices assumes critical importance in ensuring that security measures are deployed to minimize adverse environmental and societal impacts. This necessitates concerted efforts to curtail the environmental footprint associated with cybersecurity operations, promote social responsibility, and fortify resilience against cyber threats over the long term. Organizations can bolster security postures by integrating sustainability imperatives into cybersecurity frameworks while advancing equitable and environmentally conscious digital ecosystems.
The implications of our research underscore the imperative of comprehending hacker behavior, advocating for ethical considerations in cybersecurity practices, and promoting sustainable security paradigms. Through the dissemination of awareness on these issues, our endeavor is to facilitate informed decision-making and foster responsible cybersecurity practices that accord primacy to principles of privacy, equity, and sustainability.
6.2 Conclusion and future work
Following the research, it can be concluded that at a higher level, the hackers possess personality traits of agreeableness, neuroticism, and openness to experience. K-means algorithm of machine learning can be used to detect the personality traits of hackers. This research is an in-depth study to establish a quantitative and statistically significant mapping between predicted clusters and their respective Hat types using machine learning and correlation techniques. The mapping established in this research justifies the test dataset prediction performance accuracy of ~94%. Cross-validation was not utilized due to the ample size of the training set. Additionally, the training and test sets were distinct. For future work, it is suggested that if reliable access to hackers becomes available, the training set could primarily consist of hacker data, which would then be validated using cross-validation techniques.
The model must also validate the test dataset for Black Hat types from reliable resources. Further work can be done to make this approach more advanced by replacing the questionnaire with some other graphical or pictorial techniques to judge the personalities of employees before the contract signup stage or at the time of the signup process on office systems.
Despite the strength of our approach and findings, it is important to recognize some limitations. One key issue is the size and diversity of our sample. Our study's sample might not be big or varied enough to apply our findings to all hackers. Most of our participants were final-year students and cybersecurity professionals, so our conclusions might not fully represent all hacker personality traits. In addition, since our sample was mostly male, we might not have captured the full range of hacker demographics. Additionally, relying on self-reported data and personality tests could introduce biases. Participants might try to give answers they think are socially desirable, affecting the accuracy of our data.
Finally, our study focused on specific personality traits linked to hackers, but there could be other factors at play in cybersecurity behavior. Future research should aim to overcome these limitations by using more diverse samples, which would help make our findings more reliable and widely applicable.
Data availability statement
The raw data supporting the conclusions of this article will be made available by the authors, without undue reservation.
Ethics statement
Ethical review and approval was not required for the study on human participants in accordance with the local legislation and institutional requirements. Written informed consent from the [patients/ participants OR patients/participants legal guardian/next of kin] was not required to participate in this study in accordance with the national legislation and the institutional requirements.
Author contributions
UH: Conceptualization, Formal analysis, Investigation, Methodology, Writing – original draft, Writing – review and editing. OS: Methodology, Supervision, Validation, Writing – review and editing. KK: Methodology, Supervision, Writing – review and editing. AA: Methodology, Resources, Writing – review and editing. NI: Methodology, Supervision, Writing – review and editing.
The author(s) declare that no financial support was received for the research, authorship, and/or publication of this article.
Conflict of interest
The authors declare that the research was conducted in the absence of any commercial or financial relationships that could be construed as a potential conflict of interest.
Publisher's note
All claims expressed in this article are solely those of the authors and do not necessarily represent those of their affiliated organizations, or those of the publisher, the editors and the reviewers. Any product that may be evaluated in this article, or claim that may be made by its manufacturer, is not guaranteed or endorsed by the publisher.
Adali, S., and Golbeck, J. (2012). “Predicting personality with social behavior,” in 2012 IEEE/ACM International Conference on Advances in Social Networks Analysis and Mining (Istanbul: IEEE), 302–309.
Google Scholar
Adewumi, A. O., and Akinyelu, A. A. (2017). A survey of machine-learning and nature-inspired based credit card fraud detection techniques. Int. J. Syst. Assurance Eng. Manage. 8, 937–953. doi: 10.1007/s13198-016-0551-y
Crossref Full Text | Google Scholar
Akdag, M. (2020). Open Psychometrics, Big Five Personality Test, International Personality Item Pool IPIP-BFFM . Available online at: https://www.kaggle.com/akdagmelih/five-personality-clusters-k-means (accessed November 27, 2023).
Alashti, Z. F., Bojnordi, A. J. J., and Sani, S. M. S. (2022). Toward a carnivalesque analysis of hacking: a qualitative study of Iranian hackers. Asian J. Soc. Sci . 50, 147–155. doi: 10.1016/j.ajss.2022.01.001
Aldhyani, T. H., and Alkahtani, H. (2022). Attacks to autonomous vehicles: a deep learning algorithm for cybersecurity. Sensors 22, 360. doi: 10.3390/s22010360
PubMed Abstract | Crossref Full Text | Google Scholar
Ali, A., Wasim, A., Husam, A., and Manasa, K. N. (2020). Crime analysis and prediction using K-means clustering technique. EPRA Int. J. Econ. Business Rev. 3, 2925–2929. doi: 10.36713/epra2016
Back, S., LaPrade, J., Shehadeh, L., and Kim, M. (2019). “Youth hackers and adult hackers in South Korea: An application of cybercriminal profiling,” in 2019 IEEE European Symposium on Security and Privacy Workshops (EuroS&PW) (Stockholm: IEEE), 410–413.
Bakas, A., Wagner, A., Johnston, S., Kennison, S., and Chan-Tin, E. (2021). Impact of personality types and matching messaging on password strength. EAI Endors. Trans. Secur. Safety . 8, e1-e1. doi: 10.4108/eai.1-6-2021.170012
Buch, R., Dhatri, G., Pooja, K., and Nirali, B. (2017). World of cyber security and cybercrime. RTPL 4, 18–23.
Chayal, N. M., and Patel, N. P. (2021). Review of machine learning and data mining methods to predict different cyberattacks. Data Sci. Intellig. Applicat. 43–51. doi: 10.1007/978-981-15-4474-3_5
Chng, S., Lu, H. Y., Kumar, A., and Yau, D. (2022). Hacker types, motivations and strategies: A comprehensive framework. Comp. Human Behav. Rep. 5, 100167. doi: 10.1016/j.chbr.2022.100167
Corallo, A., Lazoi, M., Lezzi, M., and Luperto, A. (2022). Cybersecurity awareness in the context of the Industrial Internet of Things: a systematic literature review. Comp. Indust. 137, 103614. doi: 10.1016/j.compind.2022.103614
Del Pozo, I., Iturralde, M., and Restrepo, F. (2018). “Social engineering: Application of psychology to information security,” in 2018 6th International Conference on Future Internet of Things and Cloud Workshops (FiCloudW) (Barcelona: IEEE), 108–114.
Fox, B., and Holt, T. J. (2021). Use of a multitheoretic model to understand and classify juvenile computer hacking behavior. Crim. Justice Behav. 48, 943–963. doi: 10.1177/0093854820969754
Geluvaraj, B., Satwik, P. M., and Ashok Kumar, T. A. (2019). “The future of cybersecurity: Major role of artificial intelligence, machine learning, and deep learning in cyberspace,” in International Conference on Computer Networks and Communication Technologies (Cham: Springer), 739–747.
Golbeck, J., Robles, C., Edmondson, M., and Turner, K. (2011). “Predicting personality from twitter,” in 2011 IEEE Third International Conference on Privacy, Security, Risk and Trust and 2011 IEEE Third International Conference on Social Computing (Boston: IEEE), 149–156.
Gulati, J., Priya, B., Bharti, S., and Anu, S. L. (2016). A study of the relationship between performance, temperament, and personality of a software programmer. ACM SIGSOFT Softw. Eng. Notes 41, 1–5. doi: 10.1145/2853073.2853089
Imran, M., Faisal, M., and Islam, N. (2019). “Problems and vulnerabilities of ethical hacking in Pakistan,” in 2019 Second International Conference on Latest Trends in Electrical Engineering and Computing Technologies (INTELLECT) (Karachi: IEEE), 1–6.
Islam, N., Shaikh, A., Qaiser, A., Asiri, Y., Almakdi, S., Sulaiman, A., et al. (2021). Ternion: an autonomous model for fake news detection. Appl. Sci. 11, 9292. doi: 10.3390/app11199292
Islam, N., and Shaikh, Z. A. (2016). “A study of research trends and issues in wireless ad hoc networks,” in Mobile Computing and Wireless Networks: Concepts, Methodologies, Tools, and Applications , ed I. Management Association (IGI Global), 1819–1859. doi: 10.4018/978-1-4666-8751-6.ch081
Javaid, M. A. (2013). Psychology of hackers. SSRN Electr. J . 15, 26. doi: 10.2139/ssrn.2342620
John, P., and Oliver, Sanjay, S. (1999). The Big-Five Trait Taxonomy: History, Measurement, and Theoretical Perspectives . Berkeley: University of California. Available online at: https://personality-project.org/revelle/syllabi/classreadings/john.pdf (accessed March 10, 2024).
Larose, D. T., and Chantal, D. L. (2014). “Discovering knowledge in data: an introduction to data mining,” in IEEE Computer Society, 2nd ed . Hoboken: John Wiley and Sons.
Lima, A. C. E., and De Castro, L. N. (2014). A multi-label, semi-supervised classification approach applied to personality prediction in social media. Neural Netw. 58, 122–130. doi: 10.1016/j.neunet.2014.05.020
Martineau, M., Spiridon, E., and Aiken, M. (2023). A comprehensive framework for cyber behavioral analysis based on a systematic review of cyber profiling literature. Forens. Sci. 3, 452–477 doi: 10.3390/forensicsci3030032
Matulessy, A., and Humaira, N. H. (2017). Hacker personality profiles reviewed in terms of the big five personality traits. Psychol. Behav. Sci. 5, 137–142. doi: 10.11648/j.pbs.20160506.12
McAlaney, J., Hambidge, S., Kimpton, E., and Thackray, H. (2020). “Knowledge is power: an analysis of discussions on hacking forums,” in 2020 IEEE European Symposium on Security and Privacy Workshops (EuroS&PW) (Genoa: IEEE), 477–483.
Medoh, C., and Telukdarie, A. (2022). The future of cybersecurity: a system dynamics approach. Procedia Comp. Sci. 200, 318–326. doi: 10.1016/j.procs.2022.01.230
Mohammed, Z. H., Chankaew, K., Vallabhuni, R. R., Sonawane, V. R., Ambala, S., and Markkandan, S. (2023). Blockchain-enabled bioacoustics signal authentication for cloud-based electronic medical records. Measurem. Sens . 26, 100706. doi: 10.1016/j.measen.2023.100706
Novikova, I. A., and Alexandra, A. V. (2019). “The five-factor model: contemporary personality theory,” in Cross-Cultural Psychology: Contemporary Themes and Perspectives (Hoboken: John Wiley and Sons Press), 685–706.
Odemis, M., Yucel, C., and Koltuksuz, A. (2022). Detecting user behavior in cyber threat intelligence: development of honeypsy system. Secur Commun. Netw. 2022, 7620125. doi: 10.1155/2022/7620125
Pastrana, S., Hutchings, A., Caines, A., and Buttery, P. (2018). “Characterizing eve: Analysing cybercrime actors in a large underground forum,” in International Symposium on Research in Attacks, Intrusions, and Defenses (Cham: Springer), 207–227.
Ramachandran, D., Rajeev Ratna, V., PT, V. R., and Garip, I. (2022). A low-latency and high-throughput multipath technique to overcome black hole attack in mobile ad hoc network (MTBD). Secur. Commun. Netw . 2022, 8067447. doi: 10.1155/2022/8067447
Shackelford, S. J., Raymond, A., Fort, T. L., and Charoen, D. A. (2016). Sustainable Cybersecurity: Applying Lessons from the Green Movement to Managing Cyber Attacks . Chicago: University of Illinios Law Review. Available online at: https://illinoislawrev.web.illinois.edu/wp-content/uploads/2016/10/Shackelford.pdf (accessed March 10, 2024).
Siddiqi, M. A., Pak, W., and Siddiqi, M. A. (2022). A study on the psychology of social engineering-based cyberattacks and existing countermeasures. Appl. Sci . 12, 6042. doi: 10.3390/app12126042
Sood, A. K., and Enbody, R. J. (2013). Crimeware-as-a-service: a survey of commoditized crimeware in the underground market. Int. J. Criti. Infrastruct. Protect. 6, 28–38. doi: 10.1016/j.ijcip.2013.01.002
Suárez Álvarez, J., Pedrosa, I., Lozano, L. M., García Cueto, E., Cuesta Izquierdo, M., and Muñiz Fernández, J. (2018). “Using reversed items in Likert scales: A questionable practice,” in Psicothema , 30. Available online at: https://digibuo.uniovi.es/dspace/bitstream/handle/10651/48979/Using%20.pdf?sequence=1 (accessed March 10, 2024).
PubMed Abstract | Google Scholar
Suryapranata, K. P., Louis, P. K., Gede, H., Yaya, H., Bahtiar, S. A., et al. (2017). “Personality trait prediction based on game character design using a machine learning approach,” in Proc. ICITech (Salatiga: IEEE), 1–5.
Tamboli, M. S., Vallabhuni, R. R., Shinde, A., Kataraki, K., and Makineedi, R. B. (2023). Block chain based integrated data aggregation and segmentation framework by reputation metrics for mobile adhoc networks. Measurem.: Sens. 27, 100803. doi: 10.1016/j.measen.2023.100803
Tan, P. N., Steinbach, M., and Kumar, V. (2016). Introduction to Data Mining . Washington DC: Pearson Education India. Available online at: https://www-users.cse.umn.edu/~kumar001/dmbook/ch7_clustering.pdf (accessed March 10, 2024).
Tandera, T., Derwin, S., Rini, W., and Yen, L. P. (2017). Personality prediction system from Facebook users. Procedia Comp. Sci. 116, 604–611. doi: 10.1016/j.procs.2017.10.016
Wong, S., and Dennis Sai-fu, F. (2020). Development of the cybercrime rapid identification tool for adolescents. Int. J. Environ. Res. Public Health 17, 4691. doi: 10.3390/ijerph17134691
Xie, B., and Wei, N. (2022). “Personality trait identification based on hidden semi-Markov model in online social networks,” in Proceedings of the 2022 7th International Conference on Intelligent Information Technology (ICIIT '22) (New York, NY: Association for Computing Machinery), 52–58. doi: 10.1145/3524889.3524898
Zheng, R., Qin, Y., Huang, Z., and Chen, H. (2003). “Authorship analysis in cybercrime investigation,” in International Conference on Intelligence and Security Informatics (Berlin: Springer), 59–73.
Keywords: hacker identification, personality traits, K-means clustering, cyber security, social engineering
Citation: Hani U, Sohaib O, Khan K, Aleidi A and Islam N (2024) Psychological profiling of hackers via machine learning toward sustainable cybersecurity. Front. Comput. Sci. 6:1381351. doi: 10.3389/fcomp.2024.1381351
Received: 03 February 2024; Accepted: 22 March 2024; Published: 08 April 2024.
Reviewed by:
Copyright © 2024 Hani, Sohaib, Khan, Aleidi and Islam. This is an open-access article distributed under the terms of the Creative Commons Attribution License (CC BY) . The use, distribution or reproduction in other forums is permitted, provided the original author(s) and the copyright owner(s) are credited and that the original publication in this journal is cited, in accordance with accepted academic practice. No use, distribution or reproduction is permitted which does not comply with these terms.
*Correspondence: Osama Sohaib, osama.sohaib@uts.edu.au
This article is part of the Research Topic
Human-Centered Approaches in Modern Software Engineering
- Skip to main content
- Skip to FDA Search
- Skip to in this section menu
- Skip to footer links

The .gov means it’s official. Federal government websites often end in .gov or .mil. Before sharing sensitive information, make sure you're on a federal government site.
The site is secure. The https:// ensures that you are connecting to the official website and that any information you provide is encrypted and transmitted securely.
U.S. Food and Drug Administration
- Search
- Menu
- Inspections, Compliance, Enforcement, and Criminal Investigations
- Compliance Actions and Activities
- Warning Letters
- Agena Bioscience, Inc. - 665159 - 03/21/2024
WARNING LETTER
Agena Bioscience, Inc. MARCS-CMS 665159 — March 21, 2024
4755 Eastgate Mall San Diego , CA 92121 United States
United States
WARNING LETTER CMS # 665159
March 21, 2024
Dear Mr. Haehn,
During an inspection of your firm located at 4755 Eastgate Mall, San Diego, CA on June 7, 2023, through June 13, 2023, an investigator from the United States Food and Drug Administration (FDA) determined that your firm is a manufacturer of the MassARRAY4 System (MA4) and the iPLEX HS chemistry panels including the iPLEX HS Colon Panel in vitro diagnostic (IVD) products. Based on the inspection and our review of your firm’s website, it appears the iPLEX HS Colon Panel intended for use with the MA4 is intended for clinical diagnostic use. Under section 201(h) of the Federal Food, Drug, and Cosmetic Act (the Act), 21 U.S.C. § 321(h), this product is a device because it is intended for use in the diagnosis of disease or other conditions or in the cure, mitigation, treatment, or prevention of disease, or to affect the structure or any function of the body.
The evidence reveals that the iPLEX HS Colon Panel intended for use with the MA4 is adulterated under section 501(f)(1)(B) of the Act, 21 U.S.C. § 351(f)(1)(B), because your firm does not have an approved application for premarket approval (PMA) in effect pursuant to section 515(a) of the Act, 21 U.S.C. § 360e(a), or an approved application for an investigational device exemption under section 520(g) of the Act, 21 U.S.C. § 360j(g). The device is also misbranded under section 502(o) the Act, 21 U.S.C. § 352(o), because your firm did not notify the agency of its intent to introduce the device into commercial distribution, as required by section 510(k) of the Act, 21 U.S.C. § 360(k).
You currently have clearance for the Impact Dx™ Factor V Leiden and Factor II Genotyping Test on the IMPACT Dx™ System (K132978) under 21 CFR 864.7280 for the following indications:
The IMPACT Dx™ Factor V Leiden and Factor II Genotyping Test is a qualitative in vitro diagnostic device intended for use in the detection and genotyping of a single point mutation (G1691A, referred to as the Factor V Leiden mutation or FVL) of the Factor V gene, located on Chromosome 1q23, and a single point mutation (G20210A) of the prothrombin gene (referred to as Factor II or FII), located on Chromosome 11p11-q12, from genomic DNA isolated from EDTA anti-coagulated human whole blood samples. The test is to be performed on the IMPACT Dx™ System and is indicated for use as an aid in diagnosis of patients with suspected thrombophilia.
During the inspection, your firm’s Director of Regulatory and Quality made verbal statements to the FDA investigator that your firm no longer sells the cleared Impact Dx™ Factor V Leiden and Factor II Genotyping Test on the IMPACT Dx™ System and has since only marketed and distributed the MA4.
Based on evidence obtained during the inspection and a review of your firm’s website the iPLEX HS Colon Panel intended for use with the MA4 appears intended for clinical diagnostic use. Such evidence includes:
- Verbal statements made to the FDA investigator during the inspection on behalf of your firm by your firm’s Director of Regulatory and Quality indicating that your firm no longer sells the Impact Dx™ Factor V Leiden and Factor II Genotyping Test on the IMPACT Dx™ System (K132978) and has instead replaced it with a new system, the MA4, and admitting that your firm sells the MA4 and reagent panels to companies who analyze patient samples that are used for clinical diagnosis.
- Distribution records and a customer list obtained during inspection that indicates your firm shipped MA4 Systems and iPLEX HS Colon Panels to clinical testing laboratories.
- A customer notification your firm sent to customers dated June 1, 2021, regarding distributed iPLEX HS Colon Panels that alerted customers of an increase in false negative results of certain reagent lots and stated that Agena was taking steps “to not impact your laboratory workflow.” This customer notification was sent to a clinical hospital in Texas and there is no evidence that these reagents were intended for research use only.
- A copy of the iPLEX HS Panels User Guide obtained during inspection that included instructions for preparing and testing samples as well as instructions for interpreting iPLEX HS Reports including the iPLEX HS Colon Panel intended for use with the MA4.
- Your firm’s website (last accessed on March 20, 2024) includes product descriptions and statements that the iPLEX HS Colon Panel “enables tumor profiling studies of colorectal cancer specimens”, and that, with the iPLEX HS Colon Panel, users can “Detect more than 80 clinically relevant variants across BRAF, EGFR, KRAS, NRAS, and PIK3CA” and “Identify variants at as low as 1% variant allele frequency.” [https://www.agenabio.com/products/panel/iplex-hs-colon-panel/]
- Your firm’s website (last accessed on March 20, 2024) includes customer stories from clients of Agena that indicate your MA4 System is intended for clinical diagnostic use. For instance, on the “FEATURED CUSTOMER STORIES” page, a portion of a testimonial reads, “Accurate, Cost-effective Newborn Screening for the Illinois Department of Health on the MassARRAY [MA4]…” And a statement from your CEO reads, “We are proud to have the MassARRAY System [MA4] chosen to be an integral part of one of the top newborn screening programs in the country…” [https://www.agenabio.com/stories/hgt/accurate-cost-effective-cftr-variant-detection-newborn-screening/]. Another customer story comes from a client that is identified as a hospital system that uses your MA4 and iPLEX HS chemistry panels in tumor profiling and can deliver a quick and cost-effective test for clinically informative variants with a statement that other labs should explore the MassARRAY (MA4) for rapid, low-cost tumor profiling panels with a link to a product page for the iPLEX HS Colon Panel. [https://www.agenabio.com/stories/onc/massarray-enables-sensitivity-quick-turnaround-tumor-profiling-bsw/].
Your firm’s Director of Regulatory and Quality indicated that your firm markets the MA4 as a research use only (RUO) product and that your firm sells and distributes the MA4 to both research and clinical diagnostic companies. Your firm’s Director of Regulatory and Quality also indicated that labeling distributed with your MA4 products, and the labeling obtained during the inspection for your iPLEX HS Colon Panel, included the statement that these devices are “For Research Use Only. Not for use in diagnostic procedures.” Your firm’s website also includes the statement that these devices are “For Research Use Only. Not for use in diagnostic procedures.” But, as discussed in this letter, on numerous occasions your iPLEX HS Colon Panel and your MA4 were not being shipped or delivered for an investigation (21 CFR 809.10(c)). And these devices were not for use in the laboratory research phase of development but rather were represented as effective IVDs (21 CFR 809.10(c)(2)(i)). Your disclaimers that the MA4 and your iPLEX HS Colon Panel are intended for research use only (RUO) are inconsistent with the evidence obtained during the inspection and statements identified on your firm’s website as identified above and FDA has determined that your MA4 and iPLEX HS Colon Panel are intended for clinical diagnostic use.
Your iPLEX HS Colon Panel intended for use with the MA4 appears to be a tumor profiling test intended for the diagnosis of colorectal cancer. You were required to submit to FDA a 510(k) for this device, because it either is a new device (21 CFR 807.81(a)(1)) or, if your iPLEX HS Colon Panel intended for use with the MA4 represents a change or modification from the device cleared in K132978 (which is indicated for use as an aid in diagnosis of patients with suspected thrombophilia), has been significantly changed or modified in design, components, method of manufacture, or intended use (21 CFR 807.81(a)(3)). For a device requiring premarket approval, the notification required by section 510(k) is deemed satisfied when a PMA is pending before the agency [21 CFR 807.81(b)]. The kind of information that your firm needs to submit in order to obtain approval or clearance for the device is described on the Internet at http://www.fda.gov/MedicalDevices/DeviceRegulationandGuidance/HowtoMarketYourDevice/default.htm. The FDA will evaluate the information that your firm submits and decide whether the product may be legally marketed.
Our inspection also revealed that your firm’s iPLEX HS Colon Panel is misbranded under section 502(t)(2) of the Act, 21 U.S.C. § 352(t)(2), in that your firm failed or refused to furnish material or information respecting the device that is required by or under section 519 of the Act, 21 U.S.C. § 360i, and 21 CFR Part 806 – Medical Devices; Reports of Corrections and Removals. Significant violations include, but are not limited to, failure to submit a written report to FDA of any correction or removal of a device initiated to reduce a risk to health posed by the device, as required by 21 CFR Part 806.10. For example:
On June 1, 2021, your firm issued a Customer Notification alerting customers that certain lots of your iPLEX HS Colon v1.0 Panel did not include the A nucleotide termination in Well #8 which your firm determined could result in false negative results for three target variant alleles. Your firm instructed customers to not use the results for the impacted variants and that your firm would reformulate and verify the termination mix and provide further updates on availability. Your firm did not submit a written report of this removal to the agency, as required by 21 CFR 806.10.
We request that your firm immediately cease any activities that result in the misbranding or adulteration of your devices. Your firm should take prompt action to address any violations. Failure to adequately address the matters discussed in this letter may result in legal action being initiated by the FDA without further notice. These actions may include, but are not necessarily limited to, seizure, injunction, and civil money penalties.
Other federal agencies may take your compliance with the FD&C Act and its implementing regulations into account when considering the award of federal contracts. Additionally, should FDA determine that you have Quality System regulation violations that are reasonably related to premarket approval applications for Class III devices, such devices will not be approved until the violations have been addressed. Should FDA determine that your devices or facilities do not meet the requirements of the Act, requests for Certificates to Foreign Governments (CFG) may not be granted.
Please notify this office in writing within fifteen business days from the date you receive this letter of the specific steps your firm has taken to address the concerns noted in this letter. Include documentation of any corrections and/or corrective actions (which must address systemic problems) that your firm has taken. If your firm’s planned corrections and/or corrective actions will occur over time, please include a timetable for implementation of those activities. If corrections and/or corrective actions cannot be completed within fifteen business days, state the reason for requiring additional time and the time within which these activities will be completed. Your firm’s response should be comprehensive and address any violations. If you believe that your products are not in violation of the FD&C Act, include your reasoning and any supporting information for our consideration as part of your response.
Your firm’s response should be sent to both: Jessica Mu, Director of Compliance Branch, at [email protected] and to [email protected]. Refer to CMS # 665159 when replying. If you have any questions about the contents of this letter, please contact: Jeff R. Wooley, Compliance Officer, at 214-253-5251 or [email protected].
Finally, you should know that this letter is not intended to be an all-inclusive list of any deficiencies at your firm’s facility or associated with your firm’s devices. It is your firm’s responsibility to ensure compliance with applicable laws and regulations administered by FDA. The specific concerns noted in this letter may be symptomatic of serious problems in your firm’s manufacturing and quality management systems. Your firm should investigate and determine the causes of any violations and take prompt actions to address any violations and bring the products into compliance.
Sincerely, /S/
Courtney Lias, Ph.D. Acting Director OHT 7: Office of In Vitro Diagnostics Office of Product Evaluation and Quality Center for Devices and Radiological Health
Shari J. Shambaugh Program Division Director, Division 3 Office of Medical Device and Radiological Health Office of Regulatory Affairs
CC: Glen Wise Director, Quality and Regulatory [email protected]
- Skip to main content
- Skip to primary sidebar
Criminal Justice
IResearchNet
Academic Writing Services
Profiling in sexual offense cases.
This article delves into the pivotal role of profiling within the criminal justice system, focusing specifically on its application in sexual offense cases within the United States. The introduction offers a contextual overview of sexual offenses and underscores the significance of profiling as an investigative tool in this domain. The first section comprehensively explores the concept of profiling, tracing its historical roots, delineating its various types, and elucidating the theoretical foundations that underpin its application in sexual offense cases. The subsequent section scrutinizes the characteristics of sexual offenders, the evolution of profiling techniques, and the attendant challenges and controversies. The third section employs case studies to illustrate the practical application of profiling in solving sexual offense cases, drawing insights from both successful and unsuccessful instances. The penultimate section delves into future directions and innovations, examining emerging technologies and ethical considerations. In conclusion, the article synthesizes key findings, emphasizes the ongoing importance of profiling, and advocates for continued research and refinement in profiling techniques within the ever-evolving landscape of sexual offense investigations.
Introduction
Sexual offenses constitute a profound challenge within the criminal justice system, demanding meticulous investigation and innovative approaches to ensure justice for victims and the prosecution of offenders. This article commences with a brief yet comprehensive overview of sexual offenses within the criminal justice framework, highlighting their pervasive nature and the associated complexities in handling such cases. Subsequently, the focus shifts to the paramount importance of profiling as a strategic tool in the investigative arsenal when addressing sexual offenses. Profiling, with its multidisciplinary approach, not only aids law enforcement agencies in understanding the behavioral patterns of sexual offenders but also plays a pivotal role in narrowing down suspects and guiding investigations. Lastly, the article’s primary objective is introduced: to explore and elucidate the crucial role of profiling in sexual offense cases. By delving into its historical development, theoretical underpinnings, and practical applications, this article aims to contribute to a nuanced understanding of how profiling shapes and enhances the criminal justice process in the context of sexual offenses.
The Concept of Profiling in Criminal Investigations
Profiling, as applied in criminal investigations, has a rich historical backdrop that traces its origins to the early 20th century. Its conceptualization can be linked to the work of forensic pioneers such as Dr. James A. Brussel, who gained prominence for assisting law enforcement in the “Mad Bomber” case in New York during the 1950s. Brussel’s insights marked a pivotal moment in the evolution of criminal profiling, setting the stage for its integration into modern investigative practices.
The evolution of profiling within the criminal justice system reflects a dynamic interplay between advances in forensic science, psychology, and law enforcement practices. From its nascent stages, where intuition and experience played a central role, to contemporary methodologies grounded in empirical research and technological advancements, profiling has undergone a significant transformation. This evolution is marked by an increasing emphasis on interdisciplinary collaboration and the integration of diverse profiling techniques.
Criminal profiling, often synonymous with offender profiling, involves creating a behavioral and psychological profile of an unknown offender based on crime scene analysis, victimology, and forensic evidence. This technique aims to provide investigators with insights into the characteristics, motivations, and potential actions of the perpetrator.
Geographic profiling focuses on analyzing the spatial aspects of criminal activities, emphasizing the geographic locations of crime scenes to discern patterns and predict the likely area where an offender resides. This approach has proven particularly effective in cases with a series of linked crimes.
Psychological profiling delves into the offender’s psyche to understand the underlying motives, personality traits, and behavioral patterns. Drawing on psychological theories and empirical research, this type of profiling contributes valuable information for investigators aiming to apprehend individuals involved in sexual offenses.
Psychological theories form a cornerstone of profiling in sexual offense cases, exploring the linkages between an offender’s psychological makeup and their criminal behavior. Examining factors such as paraphilias, trauma, and psychopathology provides valuable insights into the motives and risk factors associated with sexual offenses.
Behavioral theories complement psychological perspectives by focusing on observable actions and patterns exhibited by sexual offenders. This includes studying modus operandi, victim selection, and escalation patterns, all of which contribute to constructing a comprehensive behavioral profile for investigative purposes.
Linkage analysis involves establishing connections between seemingly disparate crimes, recognizing commonalities in offender behavior or signature aspects. This approach aids investigators in identifying serial offenses and understanding the progression or evolution of an offender’s criminal activities.
Understanding the multifaceted nature of profiling and its theoretical underpinnings provides a solid foundation for its application in the investigation of sexual offenses within the criminal justice system.
Understanding the diverse typologies of sexual offenders is essential for effective profiling in sexual offense cases. This section explores various typologies, including power-assertive, power-reassurance, anger-retaliatory, and anger-excitation, shedding light on the distinct motives and behaviors associated with each. By categorizing offenders based on their characteristics, investigators can tailor profiling strategies to enhance the accuracy of suspect identification.
Profiling sexual offenders involves identifying shared traits and behaviors that may manifest in different cases. This subsection examines commonalities such as ritualistic behaviors, victim selection patterns, and escalation dynamics. A nuanced exploration of these traits aids investigators in constructing more precise and informed offender profiles, facilitating proactive investigative approaches.
Investigative successes in historical sexual offense cases, notably those where profiling played a pivotal role, highlight the evolution and effectiveness of profiling techniques. Case studies, such as the profiling contributions to the apprehension of infamous offenders like the “East Area Rapist” or the “BTK Killer,” illustrate the practical application of profiling in solving complex sexual offense cases. Analyzing these historical cases informs contemporary investigative strategies.
Technological innovations have significantly transformed profiling methodologies in sexual offense cases. This section explores the impact of advances in DNA analysis, forensic psychology, and digital forensics on profiling accuracy and efficiency. The integration of technology allows for more sophisticated crime scene analysis, enhanced victim profiling, and the development of predictive models, ushering in a new era in sexual offense investigations.
The application of profiling in sexual offense cases raises ethical considerations that warrant careful examination. This subsection delves into the ethical challenges surrounding privacy, potential bias, and the psychological well-being of both victims and offenders. Striking a balance between the utility of profiling and ethical considerations is crucial for maintaining the integrity of the criminal justice process.
Profiling, despite its advancements, is not immune to criticism regarding its reliability and validity. This section critically assesses the limitations of profiling techniques, addressing concerns related to confirmation bias, subjective interpretation, and the need for ongoing validation and standardization. Acknowledging these challenges is imperative for refining and improving profiling methodologies in sexual offense investigations.
In exploring the characteristics of sexual offenders, the evolution of profiling techniques, and the associated challenges and controversies, this section aims to provide a comprehensive understanding of the intricacies involved in profiling within the context of sexual offense cases.
Case Studies: Applying Profiling in Sexual Offense Investigations
The application of profiling in sexual offense investigations has played a pivotal role in solving high-profile cases that have captured public attention. This section provides an overview of selected notable sexual offense cases, each presenting unique challenges and complexities. Examples may include cases like the “Green River Killer,” “Ted Bundy,” or other cases that have involved serial sexual offenders. These cases serve as illustrative platforms to showcase the effectiveness and evolving nature of profiling techniques in real-world scenarios.
Delving into specific cases, this subsection examines the intricate ways in which profiling contributed to the resolution of sexual offense investigations. By analyzing the methodologies employed by profilers, the section demonstrates how behavioral, psychological, and geographic profiling techniques were instrumental in narrowing down suspects, providing leads, and ultimately aiding law enforcement in apprehending the perpetrators. Insights gained from these case studies offer valuable lessons for refining and advancing profiling strategies.
Profiling in sexual offense cases is not devoid of challenges and limitations. This subsection critically examines both successful and unsuccessful profiling attempts, highlighting lessons learned from each. By scrutinizing cases where profiling led to accurate suspect identification and subsequent convictions, as well as cases where profiling fell short of expectations, investigators can glean insights into refining methodologies, addressing potential pitfalls, and advancing the reliability of profiling techniques. This critical analysis contributes to an ongoing process of improvement and adaptation within the field of criminal profiling.
Through a detailed exploration of case studies, this section aims to underscore the practical applications of profiling in sexual offense investigations. By showcasing real-world examples, the article provides a tangible understanding of how profiling techniques have been employed, adapted, and refined over time, ultimately contributing to the resolution of complex sexual offense cases.
Future Directions and Innovations in Profiling Sexual Offenses
As the landscape of criminal justice evolves, so too do the technologies that underpin profiling methodologies. This section explores emerging technologies that hold promise for advancing the field of criminal profiling in sexual offense cases. Innovative tools such as artificial intelligence, machine learning, and advanced data analytics offer opportunities for more sophisticated analysis of behavioral patterns, crime scene characteristics, and offender profiles. The integration of cutting-edge technologies aims to enhance the accuracy and efficiency of profiling, providing investigators with powerful tools for deciphering complex cases.
The intersection of genetics and neuroscience represents a frontier in the future of profiling sexual offenses. This subsection delves into the potential of genetic profiling to identify predispositions and traits associated with sexual offenders. Additionally, advancements in neuroscience offer insights into the neurobiological underpinnings of criminal behavior, contributing to a more comprehensive understanding of offender motivations and decision-making processes. The integration of genetic and neuroscientific data into profiling practices poses both opportunities and challenges, necessitating careful consideration of ethical implications and scientific validity.
As profiling techniques continue to advance, ethical considerations become increasingly pertinent. This subsection critically examines the ethical dimensions of future profiling practices in sexual offense cases. Issues such as privacy concerns, potential misuse of genetic information, and the impact of technological advancements on civil liberties are explored. Balancing the need for effective law enforcement tools with ethical safeguards is crucial to ensuring that profiling practices align with legal and moral standards. Ethical considerations also extend to the potential biases embedded in algorithms and the responsible use of profiling data in legal proceedings.
By exploring emerging technologies, the integration of genetics and neuroscience, and the ethical considerations inherent in the future of profiling sexual offenses, this section aims to provide a forward-looking perspective on the evolution of profiling methodologies. As these innovations continue to shape the landscape of criminal justice, it is imperative to strike a balance between leveraging technological advancements for investigative efficacy and safeguarding the rights and ethical principles that underpin a just and equitable legal system.
In conclusion, this article has illuminated the crucial role of profiling in sexual offense cases within the criminal justice system. Profiling stands as a multifaceted tool that aids investigators in understanding the behavioral nuances of sexual offenders, providing valuable insights for effective and targeted investigative strategies. The significance of profiling cannot be overstated, as it serves as a bridge between the complexities of sexual offenses and the imperative to apprehend offenders, seek justice for victims, and safeguard communities.
Throughout the exploration of profiling in sexual offense cases, key findings and insights have emerged. The article delved into the historical background and evolution of profiling, examining various types such as criminal, geographic, and psychological profiling. Theoretical foundations, including psychological and behavioral theories, were explored to illuminate the intricate processes involved in constructing offender profiles. Case studies showcased the practical application of profiling, providing tangible examples of its contributions to solving sexual offense cases. Challenges, including ethical considerations and reliability concerns, were critically examined. Looking forward, the integration of emerging technologies, genetics, and neuroscience into profiling practices was discussed, highlighting both opportunities and ethical complexities.
As we navigate an era of technological advancements and evolving societal norms, it is imperative to recognize that the field of profiling in sexual offense cases is dynamic and in constant flux. This article concludes with a call to action for continued research and improvement in profiling techniques. The challenges and opportunities presented by emerging technologies, genetic insights, and ethical considerations underscore the need for ongoing refinement and adaptation. Researchers, practitioners, and policymakers are urged to collaborate in advancing profiling methodologies, ensuring that they align with evolving legal, ethical, and scientific standards. By fostering a commitment to innovation and ethical practice, the criminal justice system can harness the full potential of profiling to enhance the investigation and resolution of sexual offenses.
In summary, this article has explored the multifaceted landscape of profiling in sexual offense cases, emphasizing its pivotal role in the pursuit of justice. The synthesis of historical perspectives, current methodologies, and future considerations underscores the importance of profiling as a dynamic and indispensable tool within the criminal justice system.
References:
- Canter, D. V., & Heritage, R. (1990). A multivariate model of sexual offense behavior: Developments in offender profiling. Journal of Forensic Sciences, 35(1), 103-122.
- Douglas, J. E., Burgess, A. W., Burgess, A. G., & Ressler, R. K. (1992). Crime classification manual. Lexington Books.
- Holmes, R. M., & Holmes, S. T. (2002). Profiling violent crimes: An investigative tool (3rd ed.). Sage Publications.
- Keppel, R. D., & Walter, R. D. (1999). Profiling killers: A revised classification model for understanding sexual murder. International Journal of Offender Therapy and Comparative Criminology, 43(4), 417-437.
- Kocsis, R. N. (2006). Criminal profiling: Principles and practice. Humana Press.
- Lombroso, C., & Ferrero, W. (2006). Criminal man. Duke University Press.
- MacKay, T., & Hazelwood, R. R. (2001). The utility of criminal profiling: A cross-validated meta-analysis. Criminal Justice and Behavior, 28(2), 203-225.
- Meloy, J. R., & Gothard, S. (1995). Demographic and clinical comparison of obsessional followers and offenders with mental disorders. American Journal of Psychiatry, 152(2), 258-263.
- Pinizzotto, A. J., & Finkel, N. J. (1990). Criminal personality profiling: An outcome and process study. Law and Human Behavior, 14(3), 215-233.
- Ressler, R. K., Burgess, A. W., & Douglas, J. E. (1988). Sexual homicide: Patterns and motives. Lexington Books.
- Rossmo, D. K. (2000). Geographic profiling. CRC Press.
- Snook, B., Eastwood, J., Gendreau, P., Goggin, C., & Cullen, R. M. (2007). Taking stock of criminal profiling: A narrative review and meta-analysis. Criminal Justice and Behavior, 34(4), 437-453.
- Turvey, B. E. (2012). Criminal profiling: An introduction to behavioral evidence analysis (4th ed.). Academic Press.
- Woodhams, J., & Labuschagne, G. (2016). Profiling sexual murderers: A comprehensive review. Springer.
- Wortley, R., & Beauregard, E. (2008). Towards criminal intelligence-led policing? A comparative analysis of environmental criminology and the new police management model. British Journal of Criminology, 48(6), 846-873.

IMAGES
VIDEO
COMMENTS
Considering the validity issues regarding criminal profiling, the present article is a systematic review that aims to analyse the current relevant conclusions and issues on CP's validity. With this, new guidelines will be suggested to help future studies to evaluate criminal profiling as a scientific forensic tool. 2.
In the contemporary landscape of criminal justice, the practice of criminal profiling and behavioral analysis has evolved to incorporate a diverse array of methods, blending traditional techniques with cutting-edge technologies to enhance investigative precision. Traditional psychological profiling involves the analysis of offender behavior ...
Criminal Profiling would be of value to psychiatrists in two respects: 1) as a humbling experience in terms of recognizing the limitations of a psychiatrist in a criminal investigation and 2) as an intellectual expansion for those with polymathic proclivities. By Brent Turvey, M.S. San Diego, Academic Press, 1999, 451 pp., $79.95.
This article explores the integral role of forensic psychology in criminal profiling within the framework of the United States criminal justice system. Commencing with an historical overview, the narrative navigates through the evolution of profiling techniques, elucidating the theoretical foundations grounded in psychological principles.
Criminal profiling is used in complex investigations, and, in a number of jurisdictions, as expert evidence in criminal trials. This article seeks to move beyond the many anecdotal accounts of success by profilers and examine the evidence available as to the discipline's validity. As it stands, profiling is based on theories that are uncertain ...
Research on potential explanations is in its infancy but assumes that people receive and adopt incorrect messages favoring the accuracy and utility of criminal profiling.
Some psychologists have been conducting their own criminal profiling research, and they've developed several new approaches: Offender profiling. Much of this work comes from applied psychologist David Canter, PhD, who founded the field of investigative psychology in the early 1990s and now runs the Centre for Investigative Psychology at the ...
In profiling, deduction relies upon the scientific method which is a 'reasoned step by step procedure involving observations and experimentation in problem solving' (Bevel, 2001, p. 154).Induction, abduction and deduction relying on the scientific method go hand-in-hand in criminal profiling: theories are developed based on research and experience (induction), which are then examined in ...
Criminal profiling is a useful investigative technique that combines art and science. This article provides a brief overview of profiling that includes discussions of definitions of profiling, the training and expertise necessary to do profiling, how profiling can be helpful in criminal investigations, the types of crimes that lend themselves to profiling, and the profiling process.
Criminal profiling has evolved chiefly because researchers and comm- tators from around the globe have spent many years examining the perpetrators of serious crimes such as murder, rape, and arson. In particular, they have concentrated their efforts on studying the motivations and actions of violent offenders while seeking to document the ...
Criminal profiling is often misrepresented in the media, which introduced the public to careers in profiling and other forensic professions. It seems reasonable, therefore, for forensic psychiatrists to have access to a scholarly resource that describes the state of the practice of criminal profiling.
Criminal and Behavioral Profiling, by well-established authors Curt and Anne Bartol, presents a realistic and empirically-based look at the theory, research, and practice of modern criminal profiling. Designed for use in a variety of criminal justice and psychology courses, the book delves into the process of identifying behavioral tendencies ...
Criminal profiling is an investigative technique employed to develop a psychological and behavioral profile of an unknown perpetrator based on the characteristics of the crime and the available evidence (Turvey, 2017). It seeks to uncover potential traits, motivations, and behavioral patterns of the offender, aiding law enforcement in narrowing ...
Criminal profiling is the inferring of an offender's cha racteristics from hi s or he r crime scene. behaviour. According to Douglas and Olshaker (1995)"Criminal pr ofiling is the development of a ...
Our article was essentially critical of the role of 'embedded profiling' where experts, such as Douglas, use emotive aspects of cases to help develop profiles of active offenders, especially in the context of serial murder investigations. Our central contention was that such profiling, where Douglas and Dodd (2007) claim to 'delve inside ...
What is unique about criminal profiling is that practitioners can serve as intermediaries between organizations in law enforcement. While they are not a substitute for skilled detective work, profilers can provide detectives with interrogation techniques or a profile of a suspect. In local and state law enforcement, profilers can also be hired ...
For several decades now, clinical and forensic psychologists have been conducting research in order to assess the scientific rigor and validity of criminal profiling techniques. In that regard, a ...
Offender Profiling In Psychology. When police have very little evidence to go on, they will sometimes enlist the help of a forensic psychologist. The forensic psychologist will use prior knowledge and evidence gathered from the scene to build an offender profile. Offender profiling is an investigative tool that aid the identification ...
Criminal profiling, defined as the systematic analysis of behavioral and psychological characteristics to identify patterns and predict criminal behavior, has a rich history that has evolved over the decades. This subsection provides a comprehensive definition of criminal profiling and traces its historical development from its roots in the mid ...
Perceptions of Black individuals as being more likely to engage in criminal or terrorist activities are often influenced by stereotypes and biases, perpetuating racial profiling and systemic discrimination. Nonetheless, in the chart provided below, it is evident that whites exhibit the highest rates of terrorism.
There is a need for more specific validity research, especially when profiling is generalized beyond its original purpose of providing leads and focusing investigations. ... Criminal profiling from crime scene analysis. Behavioral Sciences and the Law, 4, 401-421. Google Scholar. Easteal, P. W., & Wilson, P. (1991). Preventing crime on ...
Assumptions are often erroneously made about the behaviour of youth by their ethnicity. Gang identities are frequently described by police and media in racial terms. Our new research debunks the myths. Our paper in the Journal of Youth Studies shows that after separating ethnicity from other "youth crime" risk factors (family, neighbourhood ...
Criminal profiling, a method employed in the investigative process, involves the analysis of behavioral and evidentiary patterns to create a profile of an unknown offender. ... This conclusion serves as a call to action, urging for sustained research and open discourse on the ethical issues inherent in criminal profiling. By fostering an ...
Psychological profiling of hackers via machine learning toward sustainable cybersecurity. This research addresses a challenge of the hacker classification framework based on the "big five personality traits" model (OCEAN) and explores associations between personality traits and hacker types.
Vice President and General Manager of Clinical Genomics. Agena Bioscience, Inc. 4755 Eastgate Mall. San Diego, CA 92121. United States. [email protected]. Issuing Office: Center for Devices ...
The application of profiling in sexual offense cases raises ethical considerations that warrant careful examination. This subsection delves into the ethical challenges surrounding privacy, potential bias, and the psychological well-being of both victims and offenders. Striking a balance between the utility of profiling and ethical ...