Chapter: Mobile Networks : Cellular Wireless Network
Frequency allocation.
FREQUENCY ALLOCATION:
Radio transmission can take place using many different frequency bands. Each frequency band exhibits certain advantages and disadvantages. Figure gives a rough overview of the frequency spectrum that can be used for data transmission. The figure shows frequencies starting at 300 Hz and going up to over 300 THz. Directly coupled to the frequency is the wavelength λ via the equation: λ = c/f , where c ≅ 3·108 m/s (the speed of light in vacuum) and f the frequency. For traditional wired networks, frequencies of up to several hundred kHz are used for distances up to some km with twisted pair copper wires, while frequencies of several hundred MHz are used with coaxial cable (new coding schemes work with several hundred MHz even with twisted pair copper wires over distances of some 100 m).
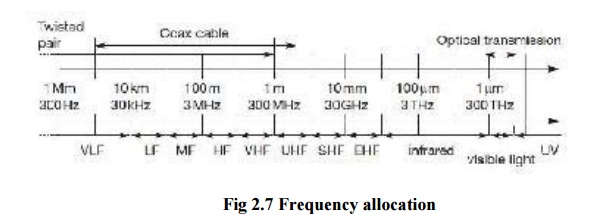
Fiber optics are used for frequency ranges of several hundred THz, but here one typically refers to the wavelength which is, e.g., 1500 nm, 1350 nm etc. (infra red). Radio transmission starts at several kHz, the very low frequency (VLF) range. These are very long waves. Waves in the low frequency (LF) range are used by submarines, because they can penetrate water and can follow the earth‟s surface. Some radio stations still use these frequencies, e.g., between
148.5 kHz and 283.5 kHz in Germany. The medium frequency (MF) and high frequency (HF) ranges are typical for transmission of hundreds of radio stations either as amplitude modulation (AM) between 520 kHz and 1605.5 kHz, as short wave (SW) between 5.9 MHz and 26.1 MHz, or as frequency modulation (FM) between 87.5 MHz and 108 MHz. The frequencies limiting these ranges are typically fixed by national regulation and, vary from country to country. Short waves are typically used for (amateur) radio transmission around the world, enabled by reflection at the ionosphere
. Transmit power is up to 500 kW – which is quite high compared to the 1 W of a mobile phone. As we move to higher frequencies, the TV stations follow. Conventional analog TV is transmitted in ranges of 174–230 MHz and 470–790 MHz using the very high frequency (VHF) and ultra high frequency (UHF) bands. In this range, digital audio broadcasting (DAB) takes place as well (223–230 MHz and 1452–1472 MHz) and digital TV is planned or currently being installed (470– 862 MHz), reusing some of the old frequencies for analog TV. UHF is also used for mobile phones with analog technology (450–465 MHz), the digital GSM (890–960 MHz, 1710–1880 MHz), digital cordless telephones following the DECT standard (1880–1900 MHz), 3G cellular systems following the UMTS standard (1900–1980 MHz, 2020–2025 MHz, 2110–2190 MHz) and many more. VHF and especially
UHF allow for small antennas and relatively reliable connections for mobile telephony. Super high frequencies (SHF) are typically used for directed microwave links (approx. 2–40 GHz) and fixed satellite services in the C-band (4 and 6 GHz), Ku-band (11 and 14 GHz), or Ka-band (19 and 29 GHz). Some systems are planned in the extremely high frequency (EHF) range which comes close to infra red. All radio frequencies are regulated to avoid interference, e.g., the German regulation covers 9 kHz–275 GHz. The next step into higher frequencies involves optical transmission, which is not only used for fiber optical links but also for wireless communications. Infra red (IR) transmission is used for directed links, e.g., to connect different buildings via laser links. The most widespread IR technology, infra red data association (IrDA), uses wavelengths of approximately 850–900 nm to connect laptops, PDAs etc. Finally, visible light has been used for wireless transmission for thousands of years. While light is not very reliable due to interference, but it is nevertheless useful due to built-in human receivers. Powered by
Related Topics
Privacy Policy , Terms and Conditions , DMCA Policy and Compliant
Copyright © 2018-2024 BrainKart.com; All Rights Reserved. Developed by Therithal info, Chennai.

Computer Network

Mobile Communication
- Computer Fundamentals
Control System
- Interview Q
Satellite Systems
Basically the table stores description of all possible paths reachable by node A, along with the hop, number of hops, sequence number and install time.
- Destination sequenced distance vector routing was one of the early algorithms available. It is suitable for creating ad-hoc networks with small no. of nodes.
Disadvantage
- Destination sequenced distance vector routing requires a regular update of its routing tables, which uses more battery power and a small amount of bandwidth even when the network is idle.
- This algorithm is not suitable for highly dynamic networks.
- The cluster head (CH) gateway switch routing (CGSR) protocol is different from the destination sequenced distance vector routing in the type of addressing and the network organization scheme employed.
- Instead of a flat network, CGSR uses cluster heads, which control a group of ad hoc nodes and hence achieve a hierarchical framework for code separation among clusters, routing, channel access, and bandwidth allocation.
- Identification of appropriate clusters and selection of cluster heads is quite complex. Once clusters have been defined, it is desirable to use a distributed algorithm within the cluster to elect a node as the cluster head.
- The disadvantage of using a cluster head scheme is that frequent changes adversely affect performance as nodes spend more time selecting a cluster head rather than relaying packets. Hence, the least cluster change (LCC) clustering algorithm is used rather than CH selection every time the cluster membership changes. Using LCC, CHs change only when two CHs come into contact, or when a node moves out of contact with all other CHs.
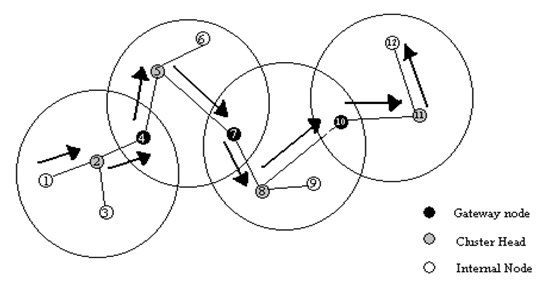
- In this scheme, each node must maintain a cluster member table (CMT), which stores the destination CH for each node in the network. The cluster member tables are broadcast periodically by the nodes using the DSDV algorithm.
- When a node receives such a table from a neighbor, it can update its own information. As expected, each node also maintains a routing table to determine the next hop required to reach any destination.
Wireless routing protocol (WRP)
The wireless routing protocol is a proactive unicast routing protocol for MANETs. It uses an enhanced version of the distance vector routing protocol, which uses the Bellman - Ford algorithm to calculate paths.
For the wireless routing protocol (WRP) each node maintains 4 tables:
- Distance table
- Routing table
- Link cost table
- Message retransmission list (MRL) table
Each entry in the message retransmission list has a sequence number of the update message, a retransmission counter, an acknowledgment required flag vector with one entry per neighbor, and a list of updates sent in the update message. When any node receives a hello message from a new node, it adds the new node to its routing table and sends the new node a copy of its routing table. A node must send a message to its neighbors within a certain time to ensure connectivity.
- The advantage of WRP is similar to DSDV. In addition, it has faster convergence and adds fewer table updates.
- The complexity of maintenance of multiple tables demands a large amount of memory and greater processing power from nodes in the MANET.
- Since it suffers from limited scalability therefore WRP is not suitable for highly dynamic and for a very large ad hoc wireless network.
2. Source initiated on -demand protocols
- Source - initiated on demand routing is reactive in nature, unlike table driven routing. This type of protocols generates routes only when a source demands it.
- In other words, when a source node requires a route to a destination, the source initiates a route discovery process in the network. This process finishes when a route to the destination has been discovered or all possible routes have been examined without any success.
- The discovered route is maintained by a route maintenance procedure, until it is no longer desired or the destination becomes inaccessible.
The source initiated on demand routing is categorized as follows:
Ad hoc on demand distance vector routing (AODV)
- AODV is a routing protocol for MANETs (mobile ad hoc networks) and other wireless ad hoc networks.
- It is a reactive routing protocol; it means it establishes a route to a destination only on demand.
- AODV routing is built over the DSDV algorithm. It is a significant improvement over DSDV.
- The devices that are not on a particular path do not maintain routing information, nor do they participate in the routing table exchanges.
- When a source requires sending a message to a destination and does not have a valid route to the latter, the source initiates a route discovery process.
- Source sends a route request (RREQ) packet to all its neighbors, the latter forward the request to all their neighbors, and so on, until either the destination or an intermediate mobile (node) with a "fresh enough" route to the destination is reached.
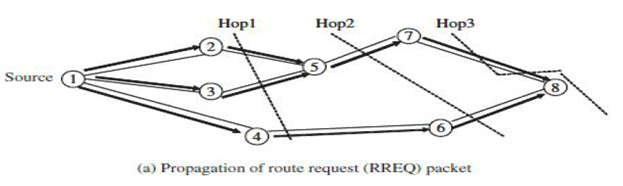
The above figure illustrates the propagation of the broadcast request (RREQs) across the network. Since in DSDV, destination sequence numbers are used to ensure that all routes are loop free and contain the most recent route information. Each node has a unique sequence number and a broadcast ID, which is incremented each time the node, initiates RREQ.
The broadcast ID, together with the IP address of node, uniquely identifies every RREQ.
Intermediate mobile reply only if they have a route to the destination with a sequence number greater than or at least equal to that contained in the RREQ. To optimize the route performance, intermediate nodes record the address.
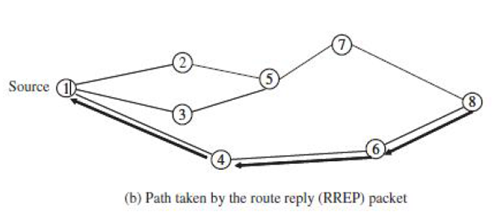
From the above figure, since RREP (route reply packet) travels back on the reverse path, the nodes on this path set up their forward route entries to point to the node from which RREP had just been received. These forward route records indicate the active forward route. The RREP continues traveling back along the reverse path till it reaches the initiator of the route discovery. Thus, AODV can support only the use of symmetric links.
Dynamic Source Routing (DSR)
- Dynamic source routing is an on-demand routing protocol which is based on source routing.
- It is very similar to AODV in that it forms a route on demand when a transmitting computer requests one. But, it uses source routing instead of relying on the routing table at each intermediate device. Many successive refinements have been made to dynamic source routing.
- Route discovery
- Route maintenance
- When a node has a message to send, it contacts to the route cache to determine whether is it has a route to the destination. If an active route to the destination exists, it is used to send a message.
- Otherwise a node initiates a route discovery by broadcasting a route request packet. The route request stores the destination address, the source address, and a unique identification number.
- Each device that receives the route request checks whether it has a route to the destination. If it does not, it adds its own address to the route record of the packet and then rebroadcasts the packet on its outgoing links.
- To minimize the no. of broadcasts, a mobile rebroadcasts a packet only if it has not seen the packet before and its own address was not already in the route record.

- Send your Feedback to [email protected]
Help Others, Please Share

Learn Latest Tutorials
Transact-SQL
Reinforcement Learning
R Programming
React Native
Python Design Patterns
Python Pillow
Python Turtle
Preparation

Verbal Ability

Interview Questions

Company Questions
Trending Technologies
Artificial Intelligence
Cloud Computing
Data Science
Machine Learning
B.Tech / MCA
Data Structures
Operating System
Compiler Design
Computer Organization
Discrete Mathematics
Ethical Hacking
Computer Graphics
Software Engineering
Web Technology
Cyber Security
C Programming
Data Mining
Data Warehouse

- Increase Font Size
23 Wireless Local Area Network:IEEE802.11
Suchit Purohit
Learning Objectives
- Introduction to Wireless Local Area Network
Advantages of WLAN
Types of WLAN
- IEEE 802.11 standards
- Modes of wireless networks
- Introduction to 802.11 architecture
Introduction
Wireless Local Area Networks (WLAN)is a term used to define network of spatially and temporally dispersed elements which transmit and receive on air using different bands of Electromagnetic spectrum like Infrared, visible, radio and microwaves. According to CISCO,
“A Wireless Local Area Network (WLAN) implements a flexible data communication system frequently augmenting rather than replacing a wired LAN within a building or campus”.
Every technology needs standardization. IEEE 802.11 standard was published in 1997 for the provision of network access and resources to different network elements on move. Since its inception, the standard is under continuous updation and amendment for the purpose of providing new services and capabilities and overcoming the limitations of previous amendments. This module marks the beginning of our learning towards IEEE 802.11. In this module, we will learn about the evolution, modes and architecture of IEEE 802.11 and in next modules we will learn about layers and the security mechanisms of this standard.
WLAN is a local area data network which provides access of information and resources to devices without wires. It is not a replacement but is implemented as an extension to a wired LAN. As compared to wired infrastructure, it has many advantages listed as follows:
- Mobility: It provides “Anywhere Anytime” access of data and information. It provides support of real time information facilitating decision making in time critical events like Stock updates.
- Low implementation costs : As compared to wired LAN the implementation costs in terms of manpower, time, complexity of installation is less. It is easy to setup, relocate, change and manage a WLAN. Initial costs for hardware may be higher than wired networks, but overall installation expenses and life cycle costs are lower.
- Installation Speed: It does not involve setting up cables and other components and arranging in form of required topology. Just configure a router and connect devices. It’s that simple.
- Network Expansion: “Wireless can go where wires cannot”. It can be laid where it is not possible to lay down a wired network like under the sea. The transmission can penetrate through buildings and walls.
- Higher Capacity: More users can be accommodated as compared to wired. For example in wired, a separate cable needs to be laid for each subscriber but for a cellular WLAN the capacity is increased manifold as per the channel availability. For eg. If a channel caters 10 subscribers and 100 channels are available, 1000 subscribers can be accommodated.
- Reliability: No fear of downtime due to cable failure which is the primary cause of failure in wired network,
- Scalability: It is easy to scale a WLAN to increase number of users as configurations can be easily changed as no fixed topology exists.
- ISM band: It operates on license free band whether it is infra-red band or ISM band.
- Robustness: The WLAN can survive disasters eg. Earthquakes. If the devices are not damaged, network won’t be affected.
- Planning: Don’t need additional plan of wires, plugs, switches etc. The WLANs can be adhocly setup with the use of devices following same standard.
As per the type of EM waves used for transmission, the WLAN can be divided into two categories:
- Infra-red WLAN: Infrared LAN uses LED, LASER, diffused bulbs as sources of energy and the receivers are photoreceptors sensitive to light. Operates on 900nm band. Eg. IrDA (Infrared data association)
- Radio based LAN: The antennas used in radio based LANs work on 2.4 GHz ISM band.
Eg. Bluetooth, Wi-fi etc.
The strengths and limitations of both the forms have been summarized in the given table:
Table 1: Infra red vs Radio WLAN
Flavours of WLAN Some of the popular flavours of WLAN are:
- HiperLAN: “HiperLAN is a set of wireless local area network communication standards primarily used in European countries. There are two specifications: HiperLAN/1 and HiperLAN/2. Both have been adopted by the European Telecommunications Standards Institute (ETSI). HiperLAN/1 provides communications at up to 20 Mbps in the 5-GHz range of the radiofrequency (RF) spectrum. HiperLAN/2 operates at up to 54 Mbps in the same RF band. HiperLAN/2 is compatible with 3G (third-generation) WLAN systems for sending and receiving data, images, and voice communications.
- IEEE 802.11: IEEE 802.11 is a standard for Local Area Networks using the ISM band from 2.4-2.5 GHz.
- HomeRF: This is a standard providing interoperability between PC and electronic devices at home.
- Bluetooth : It is standardized as a personal area network for interconnecting devices in ad hoc fashion.
- MANET: MANET is a working group within IETF to investigate and develop standards for Mobile ad hoc networks.
Evolution of IEEE 802.11
It all started in 1985, when Federal communications Commission (FCC) deregulated the spectrum from 2.4-2.5 GHz for use by Industrial, Scientific and Medical Communities which meant that Spectrum was available for individual non-licensed applications. It was an excellent opportunity for wireless application developer because they could develop without investing on licensing. This triggered many developments that were proprietary, expensive, slow and lacked widespread availability /adaption. In the early 1990s, IEEE established an executive committee, as part of the IEEE 802 standard for Local and Metropolitan Area Networks to focus on developing a wireless LAN solution that could grow into a standard with widespread acceptance, using the deregulated ISM band from 2.4-2.5 GHz. The standard was aimed to provide a reliable, fast, inexpensive, robust wireless communication. The first version of IEEE 802.11 was published in 1997.It gained success due to its compatibility with current IEEE networks particularly 802.3 Ethernet. The maximum data rate was 2 Mbps. It included forward error correction, direct sequence and frequency hopping as spread spectrum methods. It also included a specification for infrared wireless communications, still operating at up to 2 Mbps.
Since its ratification, it has been under continuous amendment and updation many other standards were released as amendments to original form and they were named IEEE 802.11a……to almost every letter of English. These standards differ from each other in many aspects like bandwidth, modulation technique, physical media, security, roaming etc. In 2007, IEEE published standard 802.11-2007 standard which is consolidated set of specifications for amendments published till 2007(a, b, d, e, g, h, j).They were rolled up into one common standard. The standard was called IEEE 802.11-20o7.Next consolidated standard was released in March 2012 that includes amendments (k, n, p, r, s, u, v, w, y and z). It was referred to as IEEE 802.11-2012.Latest release is standard including amendments ae, aa, ad, ac and af in December 2016 . IEEE 802.11-2016 is a revision based on IEEE 802.11-2012. Most recent in process are amendments ax, ay and az. More detailed description of standards can be found at standards.ieee.org.
Modes of operation of WLAN
Wireless LANs work in two modes. They are:
- Infrastructure mode: Devices communicate with each other via access point which is a wireless router
- Adhoc mode: No infrastructure or access point. Devices cluster communicate with
Figure 1: Infrastructure vs. Adhoc LAN
Infrastructure LAN
It is a cellular architecture. System is divided into cells or clusters. Each cell is called Basic service set (BSS). Each BSS is controlled by one base station called access point. Cell consists of Stations and access points. Stations are IEEE 802.11 compliant NICs (Network interface cards). The AP and all local wireless clients must be configured to use the same network name or SSID. Data packets to be transmitted from any systems (PCs) connected with LAN to wireless station will go through AP. Topology is similar to star network where all devices are attached to a central hub and communicate to each other through it. Multiple BSS form extended service set (ESS). ESS is connected to the backbone LAN or distribution system. AP provides connectivity between wireless network and hardwired LAN network. Backbone can be Ethernet or wireless itself. It converts protocol from wireless 802.11 packets to 802.3 Ethernet packets and vice versa. One 802.11 LAN can be connected to another 802 LAN via a portal.
Figure 2: Infrastructure LAN
Advantages of Infrastructure LAN
- An access point allows to easily expand a wired network with wireless capability
- Wired and wirelessly networked computers can communicate with each other
- If there are multiple access points to the network, as in an office or large home, users can roam between interlocking access point cells, without ever losing a connection to the network
- If access point is with a built-in router and firewall, the router allows to share Internet access between all computers, and the firewall hides the network
- The design of infrastructure-based wireless networks is simpler because most of the network functionality lies within the access point, whereas the wireless clients can remain quite simple
Wireless network is composed of only stations (802.11 compliant NICs). There will not be any access point in the network. The networked systems i.e. stations communicate directly with one another. It is also referred as IBSS (Independent Basic Service Set) or peer to peer mode. Here communication is directly over wireless radio waves and compliant to 802.11 packets.
Advantages of ADHOC LAN
- Ad-hoc networks are simple to set up
- Ad-hoc networks are inexpensive as the cost of purchasing an access point is reduced
- Ad-hoc networks are fast. Throughput rates between two wireless network adapters are twice as fast as when an access point is used.
- Adhoc mode is suitable for quick wireless connection setup in office rooms, hotels or in places where wired infrastructure is not available
Cell design in IEEE 802.11
Neighboring cells are allocated different non-overlapping frequencies so that wireless LAN cards of the cells do not interfere with each other while transmitting the signal. For DSSS 13 channels have been defined whereas for FHSS 79 channels are defined. For efficient use of Spectrum, frequency reuse is done by allocating the same frequency to the cell which is radio isolated. It can be seen in figure 3 that different frequencies (color coded) have been used in neighboring cells A, B,C and D. But E has been assigned same frequency as A. This is because A and E are far from each other. Figure 4 depicts a scenario where a WLAN has to be setup in a 3 storey building. For each floor 3 BSS are there. Total 9 routers would be deployed. The channel allocation is done in such a way the vertical as well as horizontal interference can be minimized.
Figure 3: Frequency allocation to different cells
Figure 4: Usage of different channel during setup of WLAN in a 3 storey building
- Wireless LANs have many advantages over wired LANS as in providing support for mobility, robustness, cost of installations, increased capacity, scalability, expansion and above all license free
- Infrared and radio waves are commonly used for WLANs. IrDA is simple , cheap can be easily integrated but requires line-of-sight and has shorter range whereas radio based networks have large range, can penetrate through walls and buildings but suffers from interference from nearby devices.
- IEEE 802.11 was developed to provide a cheap, easy and adaptable standard for WLANs in 1997 and has been undergoing amendments since then.
- WLANs work in infrastructure as well as ad hoc mode. Infrastructure LANs comprises of a central access point through which devices communicate while ad hoc not have a access point.
- In infrastructure LAN there are cells containing access points and devices known as BSS. Different BSS connect to form a ESS. Each access point is connected to a backbone which may be wired or wireless. Neighboring cells are allocated non- overlapping channels.
Suggested Reading:
- Mobile Communication 2nd edition by Jochen Schiller, Pearson education
- Mobile Computing by Asoke Talukder, Roopa Yavagal (Tata McGraw Hill)
- “Wireless communication and networking” by William Stallings
- Mobile Cellular Telecommunications — W.C.Y. Lee, Mc Graw Hill
- Wireless Communications – Theodore. S. Rapport, Pearson Education
- Reza B’Far (Ed), “Mobile Computing Principles”, Cambridge University Press.
Advertisement
Multi-objective resource allocation in mobile edge computing using PAES for Internet of Things
- Published: 02 July 2020
Cite this article

- Qi Liu 1 , 2 , 3 ,
- Ruichao Mo ORCID: orcid.org/0000-0003-3402-3182 1 ,
- Xiaolong Xu 4 &
683 Accesses
16 Citations
Explore all metrics
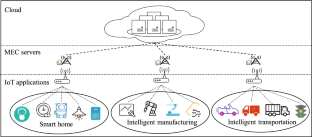
In recent years, mobile edge computing (MEC), as a powerful computing paradigm, provides sufficient computing resources for Internet of Things (IoT). Generally, the deployment of MEC servers closer to mobile users has effectively reduced access delays and the cost of using cloud services. However, the multi-objective resource allocation for IoT applications to meet service requirements (i.e., the shortest completion time of IoT applications, the load balance and lower energy consumption of MEC servers, etc.) still faces severe challenges. To address this challenge, a multi-objective resource allocation method, named MRAM, is proposed in this paper for IoT. Technically, the pareto archived evolution strategy is leveraged to optimize the time cost of IoT applications, load balance and energy consumption of MEC servers. Furthermore, the multiple criteria decision making and the technique for order preference by similarity to ideal solution are utilized to obtain the optimal multi-objective resource allocation strategy. Ultimately, the comprehensive analysis of MRAM is introduced in detail.
This is a preview of subscription content, log in via an institution to check access.
Access this article
Price includes VAT (Russian Federation)
Instant access to the full article PDF.
Rent this article via DeepDyve
Institutional subscriptions
Similar content being viewed by others
Service placement in fog–cloud computing environments: a comprehensive literature review
Task scheduling in edge-fog-cloud architecture: a multi-objective load balancing approach using reinforcement learning algorithm
Real-Time Task Scheduling Algorithm for IoT-Based Applications in the Cloud–Fog Environment
Mach, P., & Becvar, Z. (2017). Mobile edge computing: A survey on architecture and computation offloading. IEEE Communications Surveys and Tutorials , 19 (3), 1628–1656.
Google Scholar
Xiaolong, X., Zhang, X., Khan, M., Dou, W., Xue, S., & Shui, Y. (2020). A balanced virtual machine scheduling method for energy-performance trade-offs in cyber-physical cloud systems. Future Generation Computer Systems , 105 , 789–799.
Gong, W., Qi, L., & Yanwei, X. (2018). Privacy-aware multidimensional mobile service quality prediction and recommendation in distributed fog environment. Wireless Communications and Mobile Computing , 2018 , 1–8.
Hsieh, H.-C., Chen, J.-L., & Benslimane, A. (2018). 5g virtualized multi-access edge computing platform for iot applications. Journal of Network and Computer Applications , 115 , 94–102.
Qi, L., Zhang, X., Li, S., Wan, S., Wen, Y., & Gong, W. (2020). Spatial-temporal data-driven service recommendation with privacy-preservation. Information Sciences , 515 , 91–102.
Pan, J., & McElhannon, J. (2017). Future edge cloud and edge computing for internet of things applications. IEEE Internet of Things Journal , 5 (1), 439–449.
Chen, X., Shi, Q., Yang, L., & Jie, X. (2018). Thriftyedge: Resource-efficient edge computing for intelligent iot applications. IEEE Network , 32 (1), 61–65.
Xiaolong, X., Xihua, L., Zhanyang, X., Chuanjian, W., Shaohua, W., & Xiaoxian, Y. (2019). Joint optimization of resource utilization and load balance with privacy preservation for edge services in 5g networks. Mobile Networks and Applications , 25 , 713–724.
Yanwei, X., Qi, L., Dou, W., & Jiguo, Y. (2017). Privacy-preserving and scalable service recommendation based on simhash in a distributed cloud environment. Complexity , 2017 , 1–9.
Lianyong, Q, Yi, C., Yuan, Y., Shucun, F., Xuyun, Z., & Xiaolong X. (2019). A QoS-aware virtual machine scheduling method for energy conservation in cloud-based cyber-physical systems. World Wide Web , pp. 1–23.
Xu, X., He, C., Xu, Z., Qi, L., Wan, S., & Bhuiyan, M. Z. A. (2019). Joint optimization of offloading utility and privacy for edge computing enabled IoT. IEEE Internet of Things Journal , 7 , 2622–2629.
Xu, X., Zhang, X., Liu, X., Jiang, J., Qi, L., & Bhuiyan, M. Z. A. (2020). Adaptive computation offloading with edge for 5G-envisioned internet of connected vehicles. IEEE Transactions on Intelligent Transportation Systems . https://doi.org/10.1109/TITS.2020.2982186 .
Article Google Scholar
Ning, Z., Huang, J., Wang, X., Rodrigues, J. J., & Guo, L. (2019). Mobile edge computing-enabled internet of vehicles: Toward energy-efficient scheduling. IEEE Network , 33 (5), 198–205.
Xu, X., Cao, H., Geng, Q., Liu, X., Dai, F., & Wang, C. (2020). Dynamic resource provisioning for workflow scheduling under uncertainty in edge computing environment . Concurrency and Computation: Practice and Experience. https://doi.org/10.1002/cpe.5674 .
Book Google Scholar
Zhang, T., Xu, Y., Loo, J., Yang, D., & Xiao, L. (2019). Joint computation and communication design for UAV-assisted mobile edge computing in IoT. IEEE Transactions on Industrial Informatics , 16 , 5505–5516.
Xu, X., Zhang, X., Gao, H., Xue, Y., Qi, L., & Dou, W. (2019). Become: Blockchain-enabled computation offloading for IoT in mobile edge computing. IEEE Transactions on Industrial Informatics , 16 , 4187–4195.
Knowles, J. D., & Corne, D. W. (2000). Approximating the nondominated front using the Pareto archived evolution strategy. Evolutionary Computation , 8 (2), 149–172.
Wang, F., Jiang, D., Qi, S., Qiao, C., & Shi, L. (2020). A dynamic resource scheduling scheme in edge computing satellite networks. Mobile Networks and Applications , pp. 1–12.
Xu, X., Fu, S., Yuan, Y., Luo, Y., Qi, L., Lin, W., et al. (2019). Multiobjective computation offloading for workflow management in cloudlet-based mobile cloud using NSGA-II. Computational Intelligence , 35 (3), 476–495.
MathSciNet Google Scholar
Zhang, J., Zhou, Z., Li, S., Gan, L., Zhang, X., Qi, L., et al. (2018). Hybrid computation offloading for smart home automation in mobile cloud computing. Personal and Ubiquitous Computing , 22 (1), 121–134.
Xu, X., Shen, B., Yin, X., Khosravi, M. R., Wu, H., Qi, L., et al. (2020). Edge server quantification and placement for offloading social media services in industrial cognitive IoV. IEEE Transactions on Industrial Informatics . https://doi.org/10.1109/TII.2020.2987994 .
Kuang, Z., Li, L., Gao, J., Zhao, L., & Liu, A. (2019). Partial offloading scheduling and power allocation for mobile edge computing systems. IEEE Internet of Things Journal , 6 (4), 6774–6785.
Li, X., Wan, J., Dai, H.-N., Imran, M., Xia, M., & Celesti, A. (2019). A hybrid computing solution and resource scheduling strategy for edge computing in smart manufacturing. IEEE Transactions on Industrial Informatics , 15 (7), 4225–4234.
Wang, K., Yu, X., Lin, W., Deng, Z., & Liu, X. (2019). Computing aware scheduling in mobile edge computing system. Wireless Networks . https://doi.org/10.1007/s11276-018-1892-z .
Wang, Q., Guo, S., Liu, J., & Yang, Y. (2019). Energy-efficient computation offloading and resource allocation for delay-sensitive mobile edge computing. Sustainable Computing: Informatics and Systems , 21 , 154–164.
Abbas, N., Zhang, Y., Taherkordi, A., & Skeie, T. (2017). Mobile edge computing: A survey. IEEE Internet of Things Journal , 5 (1), 450–465.
She, C., Duan, Y., Zhao, G., Quek, T. Q. S., Li, Y., & Vucetic, B. (2019). Cross-layer design for mission-critical IoT in mobile edge computing systems. IEEE Internet of Things Journal , 6 (6), 9360–9374.
Tang, J., Tay, W. P., & Quek, T. Q. S. (2015). Cross-layer resource allocation with elastic service scaling in cloud radio access network. IEEE Transactions on Wireless Communications , 14 (9), 5068–5081.
Lyu, X., Tian, H., Jiang, L., Vinel, A., Maharjan, S., Gjessing, S., et al. (2018). Selective offloading in mobile edge computing for the green internet of things. IEEE Network , 32 (1), 54–60.
Zhao, J., Li, Q., Gong, Y., & Zhang, K. (2019). Computation offloading and resource allocation for cloud assisted mobile edge computing in vehicular networks. IEEE Transactions on Vehicular Technology , 68 (8), 7944–7956.
Liu, J., Mao, Y., Zhang, J., & Letaief, K. B. (2016). Delay-optimal computation task scheduling for mobile-edge computing systems. In 2016 IEEE international symposium on information theory (ISIT) (pp. 1451–1455). IEEE.
You, C., Huang, K., Chae, H., & Kim, B. (2017). Energy-efficient resource allocation for mobile-edge computation offloading. IEEE Transactions on Wireless Communications , 16 (3), 1397–1411.
Zhang, K., Leng, S., He, Y., Maharjan, S., & Zhang, Y. (2018). Mobile edge computing and networking for green and low-latency internet of things. IEEE Communications Magazine , 56 (5), 39–45.
Chunlin, L., Yanpei, L., & Youlong, L. (2017). Energy-aware cross-layer resource allocation in mobile cloud. International Journal of Communication Systems , 30 (12), e3258.
Wang, C., Liang, C., Yu, F. R., Chen, Q., & Tang, L. (2017). Computation offloading and resource allocation in wireless cellular networks with mobile edge computing. IEEE Transactions on Wireless Communications , 16 (8), 4924–4938.
Tran, T. X., & Pompili, D. (2018). Joint task offloading and resource allocation for multi-server mobile-edge computing networks. IEEE Transactions on Vehicular Technology , 68 (1), 856–868.
Wang, F., Jie, X., Wang, X., & Cui, S. (2017). Joint offloading and computing optimization in wireless powered mobile-edge computing systems. IEEE Transactions on Wireless Communications , 17 (3), 1784–1797.
Download references
Acknowledgements
This research is supported by the Basic Researc Programs (Natural Science Foundation) of Jiangsu Province (BK20191398), the National Natural Science Foundation of China under Grant No. 61702277. Besides, this work is also supported by the Fundamental Research Funds for the Central Universities, No. 30918014108 and the Priority Academic Program Development of Jiangsu Higher Education Institutions (PAPD) fund.
Author information
Authors and affiliations.
School of Computer and Software, Nanjing University of Information Science and Technology, Nanjing, 210044, People’s Republic of China
Qi Liu & Ruichao Mo
Jiangsu Engineering Center of Network Monitoring, Nanjing University of Information Science and Technology, Nanjing, 210044, People’s Republic of China
Engineering Research Center of Digital Forensics, Ministry of Education, Nanjing, People’s Republic of China
Key Laboratory of Intelligent Perception and Systems for High-Dimensional Information of Ministry of Education, Nanjing University of Science and Technology, Nanjing, 210094, People’s Republic of China
Xiaolong Xu
School of Software, Qufu Normal University, Qufu, 273165, People’s Republic of China
You can also search for this author in PubMed Google Scholar

Corresponding author
Correspondence to Xu Ma .
Ethics declarations
Conflict of interest.
The authors declare that they have no conflict of interest.
Additional information
Publisher's note.
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Reprints and permissions
About this article
Liu, Q., Mo, R., Xu, X. et al. Multi-objective resource allocation in mobile edge computing using PAES for Internet of Things. Wireless Netw (2020). https://doi.org/10.1007/s11276-020-02409-w
Download citation
Published : 02 July 2020
DOI : https://doi.org/10.1007/s11276-020-02409-w
Share this article
Anyone you share the following link with will be able to read this content:
Sorry, a shareable link is not currently available for this article.
Provided by the Springer Nature SharedIt content-sharing initiative
- Resource allocation
- Find a journal
- Publish with us
- Track your research
- Engineering Mathematics
- Discrete Mathematics
- Operating System
- Computer Networks
- Digital Logic and Design
- C Programming
- Data Structures
- Theory of Computation
- Compiler Design
- Computer Org and Architecture
GSM in Wireless Communication
- Fading in Wireless Communication
- Wireless Communication | Set 2
- Wireless Communication | Set 1
- Wireless Communication | Set 3
- Generations of wireless communication
- GPRS architecture in wireless communication
- Traditional wireless mobile communication
- Structure of Wireless Communication Link
- Types of Beamforming in Wireless Communication
- Data Communication Terminologies
- The Power Of 5G WISDOM Wireless Communication
- Spatial Filtering (Beamforming) in Wireless Communications
- Advantages and disadvantages of Wireless Communication
- Network and Communication
- Modes of Radio Wave Propagation in Wireless Communication
- Wireless Encryption Methods in Cisco
- Wired Communication Media
- Types of Communications in IOT
- Different Types of Wireless Communication Media
GSM stands for Global System for Mobile Communication. GSM is an open and digital cellular technology used for mobile communication. It uses 4 different frequency bands of 850 MHz, 900 MHz, 1800 MHz and 1900 MHz . It uses the combination of FDMA and TDMA. This article includes all the concepts of GSM architecture and how it works.
GSM is having 4 different sizes of cells:
- Macro : In this size of cell, Base Station antenna is installed.
- Micro : In this size of cell, antenna height is less than the average roof level.
- Pico : Small cells’ diameter of few meters.
- Umbrella : It covers the shadowed (Fill the gaps between cells) regions.
Features of GSM are :
- Supports international roaming
- Clear voice clarity
- Ability to support multiple handheld devices.
- Spectral / frequency efficiency
- Low powered handheld devices.
- Ease of accessing network
- International ISDN compatibility.
- Low service cost.
- New features and services.
GSM is nothing but a larger system which is divided into further 3 subsystems.
- BSS : BSS stands for Base Station Subsystem. BSS handles traffic and signaling between a mobile phone and the network switching subsystem. BSS having two components BTS and BSC.
- NSS : NSS stands for Network and Switching Subsystem. NSS is the core network of GSM. That carried out call and mobility management functions for mobile phone present in network. NSS have different components like VLR, HLR and EIR.
- OSS : OSS stands for Operating Subsystem. OSS is a functional entity which the network operator monitor and control the system. OMC is the part of OSS. Purpose of OSS is to offer the customer cost-effective support for all GSM related maintenance services.
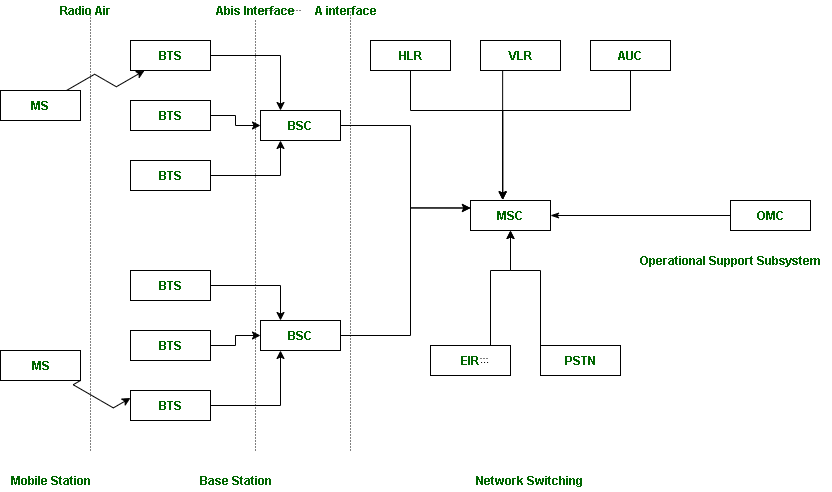
Suppose there are 3 Mobile stations which are connected with the tower and that tower is connected to BTS through TRX, then further connected to BSC and MSC. Let’s understand the functionality of different components.
1. MS : MS stands for Mobile System. MS comprises user equipment and software needed for communication with a mobile network. Mobile Station (MS) = Mobile Equipment(ME) + Subscriber Identity Module (SIM). Now, these mobile stations are connected to tower and that tower connected with BTS through TRX. TRX is a transceiver which comprises transmitter and receiver. Transceiver has two performance of sending and receiving.
2. BTS : BTS stands for Base Transceiver Station which facilitates wireless communication between user equipment and a network. Every tower has BTS.
3. BSC : BSC stands for Base Station Controller. BSC has multiple BTS. You can consider the BSC as a local exchange of your area which has multiple towers and multiple towers have BTS.
4. MSC : MSC stands for Mobile Switching Center. MSC is associated with communication switching functions such as call setup, call release and routing. Call tracing, call forwarding all functions are performed at the MSC level. MSC is having further components like VLR, HLR, AUC, EIR and PSTN.
- VLR : VLR stands for Visitor Location Register. VLR is a database which contains the exact location of all mobile subscribers currently present in the service area of MSC. If you are going from one state to another state then your entry is marked into the database of VLR.
- HLR : HLR stands for Home Location Register. HLR is a database containing pertinent data regarding subscribers authorized to use a GSM network.. If you purchase SIM card from in the HLR. HLR is like a home which contains all data like your ID proof, which plan you are taking, which caller tune you are using etc.
- AUC : AUC stands for Authentication Center. AUC authenticates the mobile subscriber that wants to connect in the network.
- EIR : EIR stands for Equipment Identity Register. EIR is a database that keeps the record of all allowed or banned in the network. If you are banned in the network then you can’t enter the network, and you can’t make the calls.
- PSTN : PSTN stands for Public Switched Telephone Network. PSTN connects with MSC. PSTN originally a network of fixed line analog telephone systems. Now almost entirely digital in its core network and includes mobile and other networks as well as fixed telephones. The earlier landline phones which places at our home is nothing but PSTN.
5.OMC : OMC stands for Operation Maintenance Center. OMC monitor and maintain the performance of each MS, BSC and MSC within a GSM system.
Three subsystem BSS, NSS and OSS are connected with each other via some interfaces. Total three interfaces are there:
- Air Interface : Air interface is also known as UM interface. Interface between MS and BTS is called as UM interface because it is mobile analog to the U interface of ISDN.
- Abis Interface : It is a BSS internal interface linking with BTS and BSC.
- A interface : It provides communication between BSS and MSC.
Services of GSM:
- Bearer services/ data services:
GSM specifies different mechanism for data transmission, The original GSM allowing for data rates of up to 9600 bits/s
Bearer services permit transparent or non transparent data transmission.
- Transparent bearer services:
Transparent bearer services only use the physical layer to transmit data. Data transmission has a constant delay at throughput if no transmission error occurs.
- Non-transparent bearer services:
Non-transparent bearer services use protocols of layer two and three two three to implement error correction and flow control.(data link layer and network layer).
2. Tele services :
Tele services are nothing but we use now as at also.
- Video calls.
- Video text and face emoji.
- short text message(SMS).
3. Supplementary services:
Supplementary services it means advanced services.
- Conference calls.
- Call waiting.
- Call forwarding.
GSM security:
- GSM offers several security using confidential information stored in the AUC and in the individual SIM.
- The SIM stores personal secret data and is protected with a pin against unauthorized use.
Advantages:
Compatibility: GSM is widely used around the world, so it is compatible with many different networks and devices.
Security: GSM offers enhanced security features such as authentication, encryption and confidentiality, which helps to protect the user’s privacy and data.
Efficient use of bandwidth: GSM uses a time-division multiplexing (TDM) technique which enables many users to share the same frequency channel at different times, making it an efficient use of the available bandwidth.
Roaming: GSM allows users to roam internationally and use their mobile phones in other countries that use the same GSM standard.
Wide range of features: GSM supports a wide range of features, including call forwarding, call waiting, voicemail, conference calling, and more.
Disadvantages:
Limited coverage: GSM networks may have limited coverage in some remote areas, which can make it difficult for users to make calls or access the internet.
Network congestion: GSM networks may become congested during peak hours, which can lead to dropped calls or poor call quality.
Security vulnerabilities: Although GSM offers enhanced security features, it is still vulnerable to certain types of attacks, such as eavesdropping and spoofing.
Data transfer speed: GSM networks offer relatively slow data transfer speeds compared to newer technologies such as 3G and 4G.
Limited capacity: GSM networks have a limited capacity for handling large volumes of data, which can be a disadvantage for users who require high-speed internet access or other data-intensive applications.
Hence, this is the complete architecture and functionalities of GSM components.
Please Login to comment...
Similar reads.
- Technical Scripter
Improve your Coding Skills with Practice
What kind of Experience do you want to share?
- February 2024
- January 2024
- December 2023
- November 2023
- October 2023
- September 2023
- August 2023
- February 2023
- January 2023
- December 2022
- January 2022
- November 2021
- August 2021
- February 2021
- November 2019
- Academic Performance
- AU Syllabus
- Duplicate Certificate
- Internal Marks
- Malpractice
- Notes & QP
- Recent Notifications
- Transcripts
- WH (With-Held)
- Entries feed
- Comments feed
- WordPress.org

CS8601 – Mobile Computing – Regulation 2017 Syllabus
Cs8601 – notes & qp, cs8601 – syllabus, unit i introduction .
Introduction to Mobile Computing — Applications of Mobile Computing- Generations of Mobile Communication Technologies- Multiplexing — Spread spectrum -MAC Protocols — SDMA- TDMA- FDMA- CDMA
UNIT II MOBILE TELECOMMUNICATION SYSTEM
Introduction to Cellular Systems — GSM — Services & Architecture — Protocols — Connection Establishment — Frequency Allocation — Routing — Mobility Management — Security — GPRS- UMTS — Architecture — Handover — Security
UNIT III MOBILE NETWORK LAYER
Mobile IP — DHCP — AdHoc– Proactive protocol-DSDV, Reactive Routing Protocols — DSR, AODV , Hybrid routing –ZRP, Multicast Routing- ODMRP, Vehicular Ad Hoc networks ( VANET) –MANET Vs VANET — Security.
UNIT IV MOBILE TRANSPORT AND APPLICATION LAYER
Mobile TCP– WAP — Architecture — WDP — WTLS — WTP –WSP — WAE — WTA Architecture — WML
UNIT V MOBILE PLATFORMS AND APPLICATIONS
Mobile Device Operating Systems — Special Constraints & Requirements — Commercial Mobile Operating Systems — Software Development Kit: iOS, Android, BlackBerry, Windows Phone — MCommerce — Structure — Pros & Cons — Mobile Payment System — Security Issues
GE3251 – Engineering Graphics – Regulation 2021 Syllabus
Be3252 – basic electrical, electronics and instrumentation engineering [beeie] – regulation 2021 syllabus, ee3251 – electric circuit analysis [eca] – regulation 2021 syllabus.
Stay Connected with STUCOR App
Dynamic Allocation of Computing and Communication Resources in Multi-Access Edge Computing for Mobile Users
Ieee account.
- Change Username/Password
- Update Address
Purchase Details
- Payment Options
- Order History
- View Purchased Documents
Profile Information
- Communications Preferences
- Profession and Education
- Technical Interests
- US & Canada: +1 800 678 4333
- Worldwide: +1 732 981 0060
- Contact & Support
- About IEEE Xplore
- Accessibility
- Terms of Use
- Nondiscrimination Policy
- Privacy & Opting Out of Cookies
A not-for-profit organization, IEEE is the world's largest technical professional organization dedicated to advancing technology for the benefit of humanity. © Copyright 2024 IEEE - All rights reserved. Use of this web site signifies your agreement to the terms and conditions.

- CDMA Tutorial
- CDMA - Home
- CDMA - Introduction
- CDMA - Channels
- CDMA - Multiple Access Methods
- CDMA - FDMA Technology
- CDMA - TDMA Technology
- CDMA - Technology
- CDMA - Network
- CDMA - Techniques
- CDMA - Spread Spectrum
- CDMA - Fading
- CDMA - Near-Far Problem
- CDMA - Power Control
CDMA - Frequency Allocation
- CDMA - Handoff
- CDMA - Interferences
- CDMA Questions & Answers
- CDMA - Questions & Answers
- CDMA Useful Resources
- CDMA - Quick Guide
- CDMA - Useful Resources
- CDMA - Discussion
- Selected Reading
- UPSC IAS Exams Notes
- Developer's Best Practices
- Questions and Answers
- Effective Resume Writing
- HR Interview Questions
- Computer Glossary
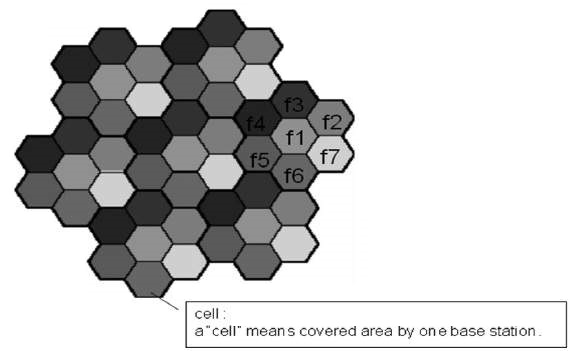
The major capacity advantage of CDMA is that it reuses the same allocated frequency in every sector of every cell. In IS-136 and analog cellular systems, there is a seven cell repeat factor, with three sectors. This means that only one out of every 21 channels is available to each sector. CDAM is designed to share the same frequency in each sector of each cell. For each user that uses cdma2000 coding rather than IS-95, the system is more efficient.
In FDMA or TDMA, radio resource is allocated not to interfere among neighbor cells −
- Neighbor cells cannot use the same (identical) frequency band (or timeslot).
- The left figure shows the simple cell allocation with seven bands of frequency.
In actual situation, because of complicated radio propagation and irregular cell allocation, it is not easy to allocate frequency (or timeslot) appropriately.
In a CDMA system against this, since all users share the same frequency, the arrangement of the frequency is not an issue. This is the biggest advantage of CDMA technology.
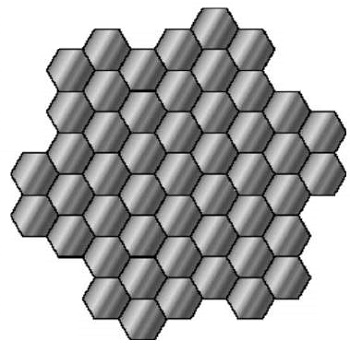
In CDMA, identical radio resource can be used among all cells, because CDMA channels use same frequency simultaneously.
- Frequency allocation in CDMA is not necessary.
- In this sense, CDMA cellular system is easy to design.
To Continue Learning Please Login

IMAGES
VIDEO
COMMENTS
As we move to higher frequencies, the TV stations follow. Conventional analog TV is transmitted in ranges of 174-230 MHz and 470-790 MHz using the very high frequency (VHF) and ultra high frequency (UHF) bands. In this range, digital audio broadcasting (DAB) takes place as well (223-230 MHz and 1452-1472 MHz) and digital TV is planned ...
Routing. Routing is the process of finding the best path for traffic in a network, or across multiple networks. The role of routing is similar to the road map for a hotel. In both cases, we need to deliver messages at proper location and in an appropriate way. Routing in a mobile ad-hoc network depends on many factors such as:
CS8601:MOBILE COMPUTING Department of CSE ... GSM - Services & Architecture - Protocols - Connection Establishment - Frequency Allocation - Routing - Mobility Management - Security - GPRSUMTS - Architecture - Handover - Security. INTRODUCTION TO CELLULAR NETWORKS
Call Routing in GSM Network 22. GPRS 23. Wireless Local Area Network:IEEE802.11 24. Layers description of IEEE 802.11 ... the most popular ones are GSM 900, GSM 1800 and GSM 1900. The different versions of GSM and the frequency allocations are as follows: TABLE 1 FREQUENCY. GSM band: ƒ (MHz) ... Mobile Computing by Asoke Talukder, Roopa ...
Fixed Channel Allocation (FCA): Fixed Channel Allocation is a strategy in which fixed number of channels or voice channels are allocated to the cells. Once the channels are allocated to the specific cells then they cannot be changed. In FCA channels are allocated in a manner that maximize Frequency reuse. In cell A 20 Channels or Voice channels ...
Mobile Terminating Call. Let us see the steps which are performed when a call is made from a landline network to a mobile phone in GSM network which may or may not be in its home network. Step 1: GMSC is identified and call is forwarded to GMSC. The number is dialed from a fixed landline number; it goes to the PSTN network.
CS8601 MOBILE COMPUTING. Dec 17, 2019 •. 7 likes • 2,329 views. Kathirvel Ayyaswamy. UNIT II MOBILE TELECOMMUNICATION SYSTEM 9 Introduction to Cellular Systems - GSM - Services & Architecture - Protocols - Connection Establishment - Frequency Allocation - Routing - Mobility Management - Security - GPRS- UMTS - Architecture ...
IEEE 802.11: IEEE 802.11 is a standard for Local Area Networks using the ISM band from 2.4-2.5 GHz. HomeRF: This is a standard providing interoperability between PC and electronic devices at home. Bluetooth: It is standardized as a personal area network for interconnecting devices in ad hoc fashion.
1. Introduction. Mobile edge computing (MEC) as an emerging paradigm [1] enables latency-critical and computation-intensive applications from the edge of mobile network in proximity to end-users, at small-scale server clusters called micro cloud, or edge cloud [2], [3].Since the main feature of this paradigm lies in leveraging computation and storage resources in network edges, without long ...
Mobile Computing, Springer, New York, 2003. 6 ... Establishment - Frequency Allocation - Routing - Mobility Management - Security - GPRS. PREREQUISTIES DISCUSSION: In this unit introduces the field of mobile and wireless communication, presents a short history
Abstract. This paper addresses a combinatorial optimization problem in the context of a robotic mobile fulfillment system deployed in a warehouse that consists of movable racks, a picker, and a fleet of mobile robots. The objective is to efficiently prepare a set of orders with specified due dates by bringing the racks to a picking station in a ...
The intensive mobile data traffic poses a great challenge for energy-constrained mobile devices. In the mobile edge environment, effective computing offloading and resource allocation can improve the service performance of edge computing systems. Therefore, a dynamic computation offloading model based on genetic algorithm is proposed in this paper. In this strategy, a task weight cost model ...
Internet of Things (IoT) systems are characterized by highly automated operating environments, which comprise several IoT end devices (IDs) that generate vast amounts of data with strict real-time communication and high data rate requirements. Edge computing facilities are an alternative to traditional cloud computing and support massive data processing in IoT systems while reducing the burden ...
Mobile edge computing (MEC) which enables communication, computation and storage capabilities at the network edge, is an emerging paradigm for 5G and beyond 5G networks. Resource-limited mobile devices can offload their tasks to the MEC server to reduce computation latency and save energy consumption. However, limited wireless spectrum resources make it hard for MEC to guarantee low latency ...
In recent years, mobile edge computing (MEC), as a powerful computing paradigm, provides sufficient computing resources for Internet of Things (IoT). Generally, the deployment of MEC servers closer to mobile users has effectively reduced access delays and the cost of using cloud services. However, the multi-objective resource allocation for IoT applications to meet service requirements (i.e ...
Efficient use of bandwidth: GSM uses a time-division multiplexing (TDM) technique which enables many users to share the same frequency channel at different times, making it an efficient use of the available bandwidth. Roaming: GSM allows users to roam internationally and use their mobile phones in other countries that use the same GSM standard. Wide range of features: GSM supports a wide range ...
Network routing in a cellular network deals with the challenges of traditional telephony such as switching and call setup. [1] Most cellular network routing issues in different cells can be attributed to the multiple access methods used for transmission. The location of each mobile phone must be known to reuse a given band of frequencies in ...
In this paper, we propose an optimization framework of offloading from a single mobile device (MD) to multiple edge devices. We aim to minimize both total tasks' execution latency and the MD's energy consumption by jointly optimizing the task allocation decision and the MD's central process unit (CPU) frequency. This paper considers two cases for the MD, i.e., fixed CPU frequency and elastic ...
Finally, this paper designs an optimal computing offloading and resource allocation strategy based on Deep Deterministic Policy Gradient (DDPG) algorithm to maximize the total system energy. The proposed algorithm is able to collect the state and action information of whole system and make better decisions based on the global information, so it ...
Anna University Mobile Computing - CS8601 (MC) syllabus for all Unit 1,2,3,4 and 5 B.E/B.Tech - UG Degree Programme. ... Introduction to Cellular Systems — GSM — Services & Architecture — Protocols — Connection Establishment — Frequency Allocation — Routing — Mobility Management — Security — GPRS- UMTS — Architecture ...
The Multi-Access Edge Computing (MEC) constitutes computing over virtualized resources distributed at the edge of mobile network. For mobile users, an optimal allocation of communication and computing resources changes over time and space, and the resource allocation becomes a complex problem. Moreover, for delay constrained applications, the resource allocation to mobile users cannot be ...
CDMA - Frequency Allocation - The major capacity advantage of CDMA is that it reuses the same allocated frequency in every sector of every cell. In IS-136 and analog cellular systems, there is a seven cell repeat factor, with three sectors. This means that only one out of every 21 channels is available to each sector. CDAM is de