~ My CCIE Wireless Journey & More…..


Configuring DCA
16 Saturday Mar 2013
Posted by nayarasi in RRM
≈ 27 Comments
Dynamic Channel Assignment (DCA) handled by RF group leader for a particular RF group. DCA algorithm takes following information into account
1. Load Measurement (Every AP measure the % total time occupied by Tx or Rx 802.11 frames) 2. Noise (APs calculate noise value on all serviced channels) 3. Interference (APs report on % medium taken up by interfering 802.11 transmission) 4. Signal strength ( RSSI of neighbor messages are heard)
Based on these metrics, if the worst performing AP will benefit by at least 5dB or more a channel change (DCA) will take place. The decision of change channel is also weighted to prevent mass change within RF group. Less client AP will more likely to change channel.
When a AP first boot up (out of the box) it transmit on CH1 in 802.11b/g radio and CH36 on 802.11a radio. Even AP reboots afterwards it will remain on the same channel until DCA occurs.
There are two scenarios in DCA could impact wireless network negatively. “ Pinning ” & “ Cascading ” are those two.
Pinning occurs when DCA algorithm could find a better channel plan for some radios in RF group, but is prevented from pursuing such a channel plan because worst radio in the network does not have any better channel options. The worst radio in RF group potentially prevent other radios in the group from seeking better channel plan. The larger the network, the more likely pinning becomes.
Cascading occurs when one radio’s channel change results in successive channel changes to optimize remaining radios in the RF neighborhood.Optimizing these radio could lead to their neighbors and their neighbor’s neighbors having a suboptimal channel plan and triggering their channel optimization. This could leads to a network instability.
Since WLC code 6.0 DCA algorithm redesigned to address both pinning & cascading.
1. Multiple local seaches DCA serach algorithm perform multiple local seraches initiated by different radios rather than performing a single global search driven by a single radio) 2. Multiple Channel Plan Change Initiators (CPCI) Previously , the single worst radio was the sole initiator of a channle plan change. Now each radio within RF group is evaluated and prioratized as potential initiators. Intelligent randomization of the resulting list eliminates the potential for pinning. 3. Localization For each CPCI radio, the DCA algorithm performs a local search for a better channel plan, but only CPCI radio itself and its one-hop neighboring AP are actually allowed to change the current Tx channels 4. Non RSSI based cost metric. A cumulative cost metric measures how well an entire region, neighborhood or network perfrom with respect to given channel plan.
You can configure DCA in 3 ways, “Automatic” , “Freeze (on-demand)”, “Off”

Automatic is the default setting where DCA runs every 10 min for 10 times once controller boots up. Then you can anchor it to certain time of the day & repeat specified time interval.
In Freeze mode no RF changes will made until you click “Invoke Channel Update Now” button. You need to remember it will not run immediately & it will run next 10 min interval.
Here are the other settings in the menu.
1. Avoid Foreign AP interference: Enabled by default. When enabled the co-channel interference metric is included in DCA calculations. For 802.11a this is good to enable as there are multiple non overlapping channels to change. But in 802.11b/g there are only 3 non overlapping channels and always there will be co-channel interference. So you need to careful when to tick this box for b/g.
2. Avoid Cisco AP Load: Disabled by default. When enabled, the client load on an AP is taken into consideration before making a channel change. It is good idea to tick this in order to prevent channel change for large client associated AP.
3. Avoid non-802.11 noise: Enabled by default. When enabled non-802.11 interference is taken into consideration.

5. Channel Width: If you are using channel bonding in 5GHz select 40MHz. In 2.4 GHz it should be always 20MHz
6. Avoid check for non-DFS channel: Disabled by default. When enabled controller avoid checks for non-DFS channels. (dynamic frequency channels). Config guide (7.0.116.0) state this only required for outdoor mesh deployment. So we can leave this disabled
7. DCA Channel List : You can select/de-select channels you want to consider for DCA algorithm. If you want to include Extend UNII-2 channels tick that box as well.
Make sure you disable the radio band before make changes & enable it once you do that.
Related Posts
1. RRM Basics 2. Configuring RRM 3. Configuring TPC 4. Configuring CHD 5. Configuring ClientLink 6. Override RRM 7. 8. Rogue Access Point Detection
Share this:
27 thoughts on “configuring dca”.
August 19, 2015 at 9:01 pm
I have noticed that your DCA channel sensitivity table shows values for 7.0.98 WLC software version. When looking into 7.0.116.0 (7.0MR1) I can see that values for Medium are 10dB for 2.4GHz and 15 for 5GHz. Values for Low sensitivity are 20dB.
September 1, 2015 at 3:05 pm
Go with what 7.0MR1 says with respect to CCIEv2.0 exam.
November 5, 2015 at 9:14 am
anyone ever see an issue where a specific DCA channel will not disable? I am trying to turn off channel 64 using PI 2.2.0 and when i uncheck the channel and save it is automatically re-checked after save….. thanks!
November 7, 2015 at 6:15 pm
Make sure to turn off 802.11a radio by going to the wireless tab. Select wireless tab on left expand bold text “802.11a/n/ac” select “Network” below that. Under General uncheck 802.11a Network Status Enabled Checkbox. Do remember this turns off all of the 5Ghz radios. Now you can change DCA channels. After change check the box back for enabled on 802.11a Network Status.
August 23, 2016 at 8:14 am
Many thanks for your blog , I really enjoy it and is very helpfull for my job. Regarding RRM and DCA channel List, is there any recomendation to use (select/desect) some channel plan like not overlapping channels?
August 23, 2016 at 8:42 am
Thanks for kind words.
Yes. In 2.4GHz – CH 1, 6 & 11 only for most part of the world (ref your local regulatory restriction, if any)
In 5GHz, UNII-1, UNII-2 and UNII-3 channels for sure. These will be supported by almost all clients.
If you need more channels (for VHD), you can select UNII-2e as well, but be aware certain end points may not support these channels.
Here is a good reference for client types and what channels they support clients.mikealbano.com
August 24, 2016 at 2:42 am
Thanks for your response Rasika. I was wondering if anyone knows any reference or paper where expressly indicated that DCA channel list may or may only recommends the use of these three channels (2.4) and not all available. This also applies to 5 GHz. After multiple – though perhaps not enough – searches have not found anywhere to clearly make this recommendation.
August 26, 2016 at 8:32 am
If you choose all channels in 2.4GHz, your AP can choose any of them to operate.
As you know if you choose any other CH other than 1,6,11, that AP will interfere with two of CH1,6,11 AP. So it make your situation worse.
Hence it is only recommend to use CH1, 6 and 11 in 2.4GHz as those are non overlapping.
September 15, 2016 at 4:48 pm
Hi , I have problem with DCA Channel list of WLC 2504 (software version 7.6.130.0), it cannot choose DCA channel beyond 140 (even though check box for Extended UNII-2 channels ). Could you please help me check ?
September 17, 2016 at 5:53 am
Did you try with different software code (like 8.0 ) ?
September 20, 2016 at 12:17 am
Hello Nayarasi, This blog has helped me numerous times, it’s great! Keep up the good work. I came here looking for what would be the best practices setting to configure DCA as far as running re-occurrence (time). I understand that the bigger the network the bigger the chances of seeing pinning or cascading issues, but having it configured at 12 hours on all radios doesn’t seem practical to me.
September 27, 2016 at 12:47 pm
I have set it for 8 hrs in my environment
November 23, 2016 at 7:19 pm
Hello Nayarasi, how does one change the DCA update interval time, I have my wireless networks disabled, but when I try to chnage it from 10 minutes to 8 hrs I get an error message “DCA Channel intervalk cannot be set”
November 25, 2016 at 5:21 am
did you try it via GUI or CLI ? If only one method used, try other method & see
November 25, 2016 at 6:37 am
I have discovered that it may be a code related (8.2.130.0) bug, worked ok on 8.0.140 code, but can only set dca interval to max of 1hr on 8.2.130.0 code, only tried via guide, will try by cli tomorrow
November 26, 2016 at 6:04 am
Hi Richard, Look at this thread, as in newer codes, there is a new feature FRA, which is set to 1 hour.
You can change DCA interval only if you change it with FRA interval. See below post
https://supportforums.cisco.com/discussion/13171366/error-message-cisco-controller
November 26, 2016 at 4:48 am
Guys, just found this out:
In 8.2, we have a new feature called FRA (Flexible Radio Assignment) for those newer APs 2800/3800, which is by default is disabled: http://www.cisco.com/c/en/us/td/docs/wireless/controller/technotes/8-3/b_RRM_White_Paper/b_RRM_White_Paper_chapter_01000.html
this FRA interval that you set has direct dependency on your DCA interval FRA interval must not be lesser than the DCA interval. The default FRA interval is 1hour (even it is disabled) and this is the reason why we cannot set the DCA Interval for more than 1 hour.
in order for us to enable the DCA Assignment interval: – We need to enable FRA and set the sensitivity and interval (Wireless>Advanced>RF Management>Flexible Radio Assignment) – Then, go back to the DCA interval and set it lesser than what you set in FRA.
Thanks, did not see this response when I replied to earlier comment.
January 30, 2017 at 9:40 am
Hi Raskia, Informative post as always.
I am planning to enable UNII 2 extended channels and it’s recommended to have DFS in place for that. Does it mean that above channels shouldn’t be set statically on AP’s rather WLC should use them with “auto RRM” being set ?
January 30, 2017 at 2:46 pm
Even if you set it to static, when radar event detected AP has to change the channel.
I would leave it to RRM to handle it rather make it static.
January 30, 2017 at 3:55 pm
Can AP change it’s channel upon detecting radar if channel is set statically ?
April 5, 2017 at 6:13 am
Great blog!
Question for you. I’m wondering how DCA gets information on off-channels when not using a monitor mode AP or a WSM module (for the 3600 or 3700ap).
Without either I notice the WLC only shows cleanair statistics for the serving channels. When using a monitor mode AP or the WSM module AQ statistics are shown for all channels.
Does this mean when not using a monitor mode or WSM module, DCA is essentially guessing on which channel to jump to, at which point after it jumps it will then have an AQ score for the future?
April 7, 2017 at 10:32 am
I do not know these details, probably direct it to Cisco and you will get a response.
April 12, 2018 at 12:25 am
Your blog regarding wireless technology is really amazing and thanks for that. I have a question, I have 84 Cisco light weight access points and 5508 WLC running 8.0.140.0. I wonder can I put all my AP (84 APs) in one channel i.e. 2.4GHz to be on Chanel 1 and 5GHz on 149? what would be the consequences for this action? Thanks Nebay
April 21, 2018 at 7:33 am
Hi Nebay, If you want to make your wireless unusable, you can try that 🙂
As you know wireless operate in CSMA-CA (CA-collision avoidance) any station or AP need to sense medium before transmitting. By having different frequency in each AP, you can make this contention domain small. Once you put all your AP in same channel, it will become very large contention domain, so no body will get a free medium to tx (as you will hear large number of devices in your channel)
So it is big NO NO to put all your AP into same channel.
Hope that clear
Regards Rasika
April 21, 2018 at 11:14 pm
Thanks very much Rasika, I really appreciate your response and Thanks for your time and patience. Nebay
August 17, 2018 at 10:35 pm
Would be able to provide the cli commands to disable and enable the radio ? Also the cli to add/remove channels from the DCA Channel List?
Leave a comment Cancel reply
My CCIE Wireless Journey & More.....
CCNP to CCIE level wireless tricks & training
Not Another Wireless Blog
Path to CCIE

- Already have a WordPress.com account? Log in now.
- Subscribe Subscribed
- Copy shortlink
- Report this content
- View post in Reader
- Manage subscriptions
- Collapse this bar
Thank you for visiting nature.com. You are using a browser version with limited support for CSS. To obtain the best experience, we recommend you use a more up to date browser (or turn off compatibility mode in Internet Explorer). In the meantime, to ensure continued support, we are displaying the site without styles and JavaScript.
- View all journals
- My Account Login
- Explore content
- About the journal
- Publish with us
- Sign up for alerts
- Open access
- Published: 24 January 2023
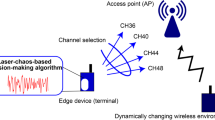
Efficient dynamic channel assignment through laser chaos: a multiuser parallel processing learning algorithm
- Zengjing Chen 1 ,
- Lu Wang 1 &
- Chengzhi Xing 1
Scientific Reports volume 13 , Article number: 1353 ( 2023 ) Cite this article
678 Accesses
1 Citations
Metrics details
- Electrical and electronic engineering
- Fibre optics and optical communications
- Information technology
As laser chaos has been proven to be a robust tool to solve the multi-armed bandit (MAB) problem, this study investigates the problem of multiuser dynamic channel assignment using laser chaos in cognitive radio networks with K -orthogonal channels and M secondary users. A novel dynamic channel assignment algorithm with laser chaos series for multiple users, named parallel processing learning with laser chaos (PPL-LC) algorithm, is proposed to efficiently address two main objectives: stable channel assignment and fuzzy stable channel assignment. The latter objective accounts for the realistic scenario where users have fuzzy preferences and do not necessarily pursue the best preference. The PPL-LC algorithm uses the randomness properties of laser chaos to learn the assignment of channels to multiple users without any limitations on the number of channels, which has not been considered in existing laser chaos algorithms. Moreover, the PPL-LC is equipped with parallel processing channel selections, resulting in higher throughput and stronger adaptability with environmental changes over time than comparison algorithms, such as distributed stable strategy learning and coordinated stable marriage MAB algorithms. Finally, numerical examples are presented to demonstrate the performance of the PPL-LC algorithm.
Similar content being viewed by others
Dynamic channel selection in wireless communications via a multi-armed bandit algorithm using laser chaos time series
Shungo Takeuchi, Mikio Hasegawa, … Makoto Naruse
Mitigation pilot contamination based on matching technique for uplink cell-free massive MIMO systems
Abdulrahman Al Ayidh, Yusuf Sambo & Muhammad Ali Imran
Proactive approach for preamble detection in 5G-NR PRACH using supervised machine learning and ensemble model
Syeda Sundus Zehra, Maurizio Magarini, … Faiza Farooq
Introduction
Since cognitive radio networks (CRNs) were proposed 1 , multiuser dynamic channel assignment has been a significant focus. Advances in terminology suggest improvements in the performance of CRNs based on resource utilization and other factors. As primary users have priority over secondary users in spectrum utilization, secondary users should be aware of primary users’ behaviors. For efficient resource utilization, corresponding issues, such as which channel primary users choose and what time to sense, should be considered by secondary users. Existing spectrum allocation and sharing approaches are discussed in detail 2 . Zhao and Sadler 3 reviewed various models with dynamic spectrum access. Using the Gale–Shapley stable matching algorithm, the stable marriage problem of multiuser dynamic channel assignment was first solved under the assumption that the expected rates are known and a distributed opportunistic CSMA protocol that solves the problem was proposed 4 . This approach has been shown to have a range of advantages and has received significant attention recently.
The combination of the multi-armed bandit (MAB) problem and cognitive radio access was initially studied with independent channels 5 . Channel selection is considered as a type of MAB problem; that is, the amount of information passed through a channel is considered as the gain obtained by a robot arm. Lai, Jiang, and Poor 6 discussed the solution to the cognitive media access problem and considered various scenarios using the upper confidence bound (UCB) algorithm to explore the optimal choice of numerous users and channels in this problem. Further, they proved that the UCB algorithm achieves an expected sum of regrets of near- \(O(\log T)\) . Avner and Mannor 7 proposed the concept of stable marriage configuration (SMC) and proposed the coordinated stable marriage MAB (CSM-MAB) algorithm to reach the SMC state. The CSM-MAB algorithm requires communication and exchange of channels between different users, but it does not give the approximate order achieved by the regret. Bistritz and Leshem 8 proposed The game of thrones (GoT) algorithm, which does not require user communication, and proved that it achieves an expected sum of regrets of near- \(O(\log ^{2}T)\) . Gafni and Cohen 9 introduced a fully distributed algorithm—distributed stable strategy learning (DSSL)—to solve a multiuser channel assignment problem and achieved a stable state through a large number of exchanges between users with the upper boundary of the regret given in the theoretical proof.
Several recent observations on laser chaos motivate its application to dynamic channel assignment 10 . In physics, chaos has always been closely related to randomness and is extremely sensitive to the initial parameter values. The chaotic oscillation of a laser signal level is generated by the injection of delayed light into the cavity of a diode laser emitter, which is accomplished by directing the output of the semiconductor laser through a beam splitter toward a laser reflector. The resulting chaotic oscillation of the laser signal level can be harnessed for various applications, such as secure communication, chaos-based sensing, and chaos-based control. Based on this, random numbers are obtained by the fast sampling of the signal level 11 . Random numbers generated by laser chaos are generally in the GHz or higher level, indicating the high quality of these random numbers. They seem natural and have passed the National Institute of Standards and Technology (NIST) random number test. Considering these advantages, research has been conducted on potential applications of laser chaos. Naruse et al. 12 proposed a MAB algorithm using chaotically oscillating waveforms. Subsequently, the algorithm was further improved to consider the order correct probability of MAB 13 . The major work inspiring this study is the use of a laser chaos algorithm to solve the problem of dynamic channel selection for a single user 14 .
Although laser chaos has been proven to be effective in the aforementioned literature, there still exists some engaging questions that need to be addressed. One of these questions is whether laser chaos can perform well in CRNs with multiple users. In other words, it is worth investigating whether it is possible to achieve higher throughput by laser chaos to attain a suitable stable configuration. Focusing on stable configuration, it should be noted that the preferences of different users in the real world are not consistently precise, which prompts contemplation on how to dynamically select channels in CRNs based on the fuzzy preferences of users. Therefore, this study investigates dynamic channel selection in CRNs using laser chaos series based on a proper stable aim.
Based on the above starting points, a novel dynamic channel assignment algorithm with laser chaos series for multiple users, named parallel processing learning with laser chaos (PPL-LC) algorithm, is proposed to enhance throughput and improve operational efficiency. To increase the verisimilitude of the proposed model, consider a CRN comprising multiple users and multiple channels. The probability of a given channel may differ among the various users, adding a layer of complexity and realism to the model. The stable channel assignment (SCA) has aroused widespread interest. As a result, a new definition for the stable arrangement of channels based on users’ fuzzy preferences, called fuzzy stable channel assignment (FSCA), has been proposed. This described the reality of situations where users have their recognition interval 15 , 16 , and all channels in this interval are equally possible to be chosen. Therefore, the channel selection problem is studied to achieve SCA and FSCA separately. The PPL-LC algorithm includes two stages with the users’ channel preference updating process, and the parallel channel exchange process. As MAB problems require a balance between exploration and exploitation, laser chaos provides an efficient tool for sufficient exploration. Based on this, in the process of updating users’ preferences, the PPL-LC algorithm applies laser chaos to achieve equilibrium for multiple users. During the channel exchange process, a parallel method that selected users simultaneously perform the procedure is employed.
In the following, detailed comparisons with related results are provided. First, the previous work only proposed a stable state similar to SMC, whereas this paper considers FSCA state. The performance of the proposed algorithm is evaluated by targeting these two states. Based on the experiment, the PPL-LC algorithm has a higher throughput than the CSM-MAB and DSSL algorithms. Second, the restriction of existing laser chaos algorithms based on channels (arms) that are integer powers of 2 is eliminated and the algorithm is generalized to support an arbitrary number of channels. Third, to the best of our knowledge, this is the first time laser chaos is applied to dynamic channel selection with multiple users. In addition, to attain higher throughput and perform more processes, this work introduces a parallel channel exchange processing to reach two target stable states. The principles of this processing approach are presented in detail below.
Characteristics of CRNs
This paper considers the following scenario to investigate the CRN problem. In an information communication network system with K channels and N users, it is assumed that each user can only use one channel and that each channel allows only a single user to transmit information. If two or more users occupy the same channel simultaneously, the information passed through the channel becomes null. Users can communicate with each other to exchange channels. Without loss of generality, the assumption \(K \le N\) is taken in this study. Otherwise, the number of users transmitting information concurrently can be restricted through the use of split time to satisfy the condition \(K \le N\) .
When user n selects the channel k for information transmission, two random outcomes may occur: complete transmission or rejection. Complete transmission signifies that all information passes through channel k , whereas rejection denotes the state in which no information passes through channel k . For convenience, the symbols used in this paper are defined as follows.
\(\mathcal {U}=\{1,2,\ldots , N\}\) indicates the set of users and \(\mathcal {C}=\{1,2,\ldots , K\}\) is the set of channels.
\(X_{n,k}\) indicates the binary random variable of whether user n can completely transmit 1 bit of information using channel k , which is consistent regardless of time step.
\(\mu _{n,k}\) indicates the expectation of \(X_{n,k}\) , i.e., \(\mathbb {E}[X_{n,k}]\) .
\(\pi _{n,t}\) indicates the channel assignment of the user n at time t .
\(T_{t}^{n,k}\) indicates the number of times the user n selects the channel k before time t .
\(R_{t}^{n,k}\) indicates the total benefit of the user n choosing channel k before time t .
\(\hat{\mu }_{t}^{n,k}\) indicates the average benefit of the user n choosing channel k before time t , i.e,
As mentioned in Introduction, the existing laser chaos algorithms usually assume that the number of arms (channels) satisfies the condition \(K= 2^{M}\) for \(M \in \mathbb {N}^{*}\) . However, real situations rarely satisfy this assumption. To be coincident with reality, this study removes this restriction such that K can take any number. For any number of channels \(K>1\) , a positive integer M can be found such that \(2^M<K \le 2^{M+1}\) . A sequence of binary codes \(\{S_{1}S_{2} \ldots S_{M+1}\}\) can be used to represent each channel \(k\in \mathcal {C}\) with \(S_{i} \in \{0,1\}\) for \(i = 1,\ldots ,M+1\) . The laser chaos algorithm uses \(2^{M+1}\) as the number of channels and sets \(\mu _{n,k_{a}}\) to zero for all \(k_{a}\) among the last \(2^{M+1} -N\) channels with \(n = 1,\ldots ,N\) . For example, consider the case where \(K=5\) and all channels can be represented as a set of binary codes \(\{000,001,\ldots ,111\}\) . The last three channels \(\{101,110,111\}\) are designated as virtual channels (Fig. 1 ).
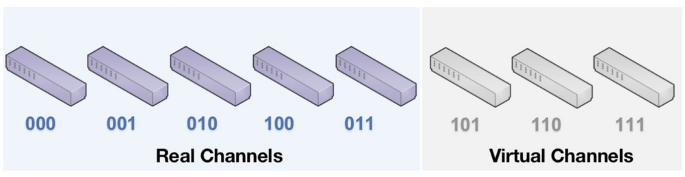
Extension of number of channel by adding virtual channels with five channels as an example.
For channel distributions, a general model is considered where reward differs for various users in the same channel. In other words, the probability that a channel exhibits a fully transmitted state depends on the users. This assumption fits the situation, in complex electromagnetic environments, that the channel environment changes according to distinct users. Each user has B bits information waiting to be delivered. According to the additivity of distribution, the amount of information that user n transmits from the B bits information through channel k is \(BX_{n,k}\) . If two or more users choose the same channel simultaneously, the collision results in \(X_{n,k}=0\) . An allocation strategy \(\pi _n\) for user n is defined as a vector of time \(\{\pi _{n,t},n\in {\mathcal {U}}, t=1,2,\ldots \}\) . Therefore, the total amount of information \(R_t\) transmitted by all users at time t is defined as
Unlike the single-user model, optimal decisions of multiuser dynamic channel selection are determined by target state setting. This study consider two matching objectives: SCA 4 , which is widespread in existing literature, and FSCA, which takes vague choice preferences into account. The following provides detailed descriptions of these two definitions.
Definition 1
SCA indicates the strategy mapping \(\mathcal {M}_S\) from \(\mathcal {U}\) to \(\mathcal {C}\) that for any \(n \in \mathcal {U}\) and \(k \in \mathcal {C}\) satisfying \(\mathcal {M}_S(n)\ne k\) , if \(\mu _{n,k}-\mu _{n,\mathcal {M}_S(n)}>0\) , then there exists some user \(n_0\in \mathcal {U}\) such that \(\mathcal {M}_S(n_0)=k\) and \(\mu _{n_0,k}-\mu _{n,k}>0\) .
Definition 2
FSCA indicates the strategy mapping \(\mathcal {M}_F\) from \(\mathcal {U}\) to \(\mathcal {C}\) that for any \(n \in \mathcal {U}\) and \(k \in \mathcal {C}\) satisfying \(\mathcal {M}_F(n)\ne k\) , if \(|\mu _{n,k}-\mu _{n,\mathcal {M}_F(n)}|\le \delta\) , then there exists some user \(n_0\in \mathcal {U}\) such that \(\mathcal {M}_F(n_0)=k\) , \(|\mu _{n_0,\mathcal {M}_F(n)}-\mu _{n_0,k}| >\delta\) or \(|\mu _{n_0,k}-\mu _{n,k}|> \delta\) .
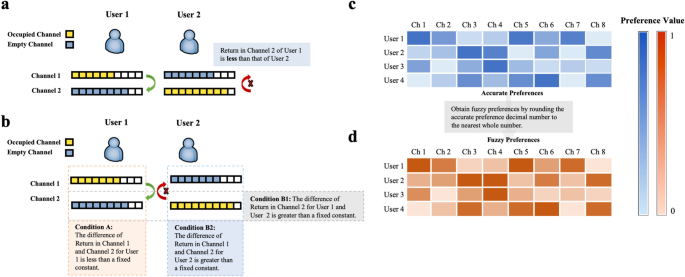
SCA and FSCA instructions for two users and eleven channels. ( a ) The SCA state where user 1 is willing to exchange, and user 2 is reluctant to exchange. ( b ) The SCA state where Conditions A and B1 are satisfied but Condition B2 is not. ( c ) The users’ preferences with specific cognition ranging from 0 to 1. ( d ) The users’ preferences with vague cognition obtained from (c) .
The difference between SCA (Fig. 2 a) and FSCA (Fig. 2 b) is users’ subjective choice, which reflects that FSCA is a weaker match than SCA. From the definitions, it is noticed that a strategy is FSCA if it satisfies Conditions A and B, including the two alternatives Condition B1 and B2 (Fig. 2 b). In other words, FSCA will be reached if one of Condition B is satisfied. A more intuitive representation of fuzzy preferences is presented in Fig. 2 c,d. If the user has a very clear acknowledgment of a channel, the good or bad preference can be seen through the shade of blue. The darker the color, the more satisfied the user is. It can be seen that, in this case, the color of blue changes a lot, and many level divisions exist (Fig. 2 c). With the same data in Fig. 2 c, the user’s preferences are blurred and orange has less color change and less grading (Fig. 2 d). In the next subsection, a brief overview of the laser chaos algorithm is presented.
Laser chaos algorithm
In previous research, the laser chaos algorithm was experimentally proven to have a correct higher-order probability compared with other algorithms 12 . A correct higher-order probability helps the selection preference to be close to the true channel gain order, which is vital for the subsequent channel exchange. This is also the main reason the laser chaos algorithm is used in this study. As shown in Fig. 3 , the semiconductor laser emits laser light through the beam splitter to the laser reflector, and the delayed light injects into the diode laser emitter cavity. Laser chaos is a result of delayed laser feedback, converted to an electrical signal by a photodetector and illustrated by an oscilloscope. Through ultrafast frequency sampling, high-quality random numbers are generated.
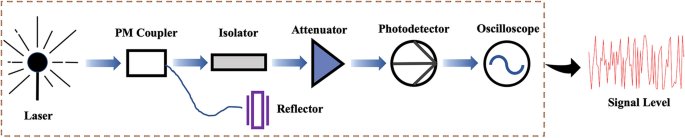
The generation process of laser chaos where a semiconductor laser emits laser light through the beam splitter to a laser reflector, and the delayed light injects into a diode laser emitter cavity.
Previous studies used the laser chaos algorithm to find the optimal arm (channel) in MAB problems, whereas this study only uses the laser chaos algorithm to update selection preference instead of channel selection. Updating a user’s preference with the laser chaos algorithm is divided into three steps as follows.
Step 1: Select the channel according to the random number generated by laser chaos.
Throughout the previous discussions, any channel number can be converted into \(2^{M}\) . Thus, use \(\{S_{1}S_{2} \ldots S_{M}\}\) to represent all channels. The channel can be selected by M -times comparisons between the signal levels at different times and the corresponding threshold. Denote \(s(t_{i})\) as the signal level value generated by the laser chaos at time \(t_{i}\) and \(t_{1}\) as the initial time point of the first channel selection. \(T^{H}_{i,S_{1}\ldots S_{i-1}}\) indicates the threshold of selecting \(S_{i}\) on the basis that \(S_{1}\ldots S_{i-1}\) has been determined.
If \(s(t_{i})\) is no less than \(T^{H}_{i,S_{1}\ldots S_{i-1}}\) , set \(S_{i}\) to 1. Otherwise, \(S_{i}\) is set to 0 for \(i = 1,\ldots ,M\) . In this round of channel selection, \(\Delta _{S}\) is the time interval to select \(S_{i}\) for \(i = 1,\ldots , M\) in sequence. Naturally, the initial time point is \(t_{1}+\Delta _{S}\) in the next round of channel assignment and a similar procedure can be performed in the subsequence.
Step 2: Send a message and receive feedback.
Send the message through the channel \(k' = S'_{1}\ldots S'_{M}\) selected in the previous step and obtain the feedback. The feedback value is equivalent to the observation of random variables. Then, record \(T_{t}^{n,k'}\) and \(R_{t}^{n,k'}\) and update \(\hat{\mu }_{t}^{n,k'}\) of channel \(k^{'}\) at time slot t .
Step 3: Adjust the threshold according to the feedback obtained in Step 2 .
This last step is to adjust the threshold according to the input obtained in the previous step. If the return is greater than 0, the threshold is adjusted to the direction that \(k'\) is more likely to be chosen. Otherwise, the threshold is adjusted to the direction where \(k'\) is less likely to be chosen. The adjustment of the threshold is performed by adding and subtracting the two parameters \(\Lambda\) and \(\Omega\) . The parameter which will be adjusted is determined by the size of the arm gain. If the arm gain is greater than 0, the threshold is adjusted using the parameter \(\Lambda\) and vice versa. The parameters are divided into fixed and flexible types. The values of \(\Lambda\) and \(\Omega\) under the fixed type are both 1. For the flexible type, \(\Lambda\) is set to be 1 and \(\Omega\) is continuously adjusted according to the selection as follows 17 :
where \(L_{i,S_{1}S_{2}\ldots S_{i}=j}\) indicates the selection times of observing positive return when \(S_{1}S_{2}\ldots S_{i-1}\) have been determined with \(S_{i} = j, j\in \{0,1\}\) and \(T_{j,S_{1}S_{2}\ldots S_{i}=j}\) indicates the selection times when \(S_{1}S_{2}\ldots S_{i-1}\) have been determined, and \(S_{i}=j\) . The two parameter types are suitable for different distribution situations; thus, an appropriate parameter type is chosen according to the channel distribution. In more detail, we present the process of using laser chaos series to select a channel with \(M=2\) (Fig. 4 ).
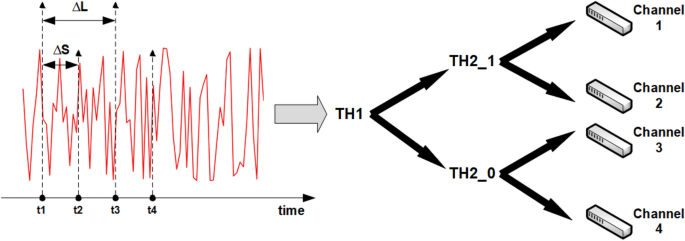
The process of using the laser chaos series to select the corresponding channel when M =2.
Parallel exchange process
The basic thought of this exchange model is derived from the marriage matching model, which can be described by the following scenario (Fig. 5 ). Suppose that there are two sets A , B , each of which contains L individuals. Every person has his/her unique preferences. Considering \(L=3\) as example, the sets of individuals are given by \(A:=\{a,b,c\}\) and \(B:=\{e,f,g\}\) . The selection preference of individuals in A is given by the strictly ordered sequence [ f , e , g ], in which the level of attraction decreases constantly. At the beginning of the first round, the individuals in A sequentially select their preferred individual from B . If an individual in B is chosen by a single individual in A , the combination is tentatively established. If an individual in B is chosen by multiple individuals in A , the individual with higher priority, as determined by the preference of the individual in B , is selected. The remaining individuals in A proceed to the next round and repeat the process until each individual in A is paired with a single individual in B .
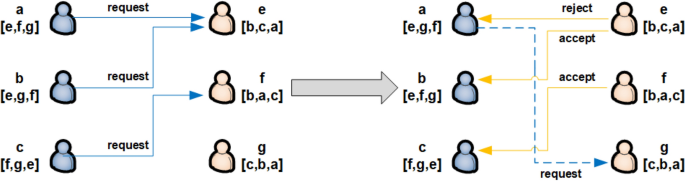
Users \(\{a,b,c\}\) and users \(\{e,f,g\}\) are paired based on the marriage matching model with their selection preference.
The multiuser channel selection model is similar to the marriage matching model. The individuals in A can be analogized to users, whereas the individuals in B can be likened to channels. The phenomenon that one person in A can only be paired with an unmatched person in B agrees with previous assumptions in dynamic channel selection issues. Therefore, this study uses this principle to handle each user’s selection. In addition, this paper proposes a parallel processing method where all users perform channel selection (stable marriage model) simultaneously. Compared with a single initiator at a given time, the simultaneous operation of multiple users intends to get more effective information throughput. The detailed parallel exchange process is discussed below.
The exchange phase at every time slot t is divided into two parts. First, initiators are selected randomly from users, which differs from the marriage matching model with only initiators exchanging channels, not all users. Second, the randomly selected initiators will launch requests to channels in parallel. Notably, the exchange steps are closely related to the target states. For the exchange step with SCA as the target state, the selected initiators send requests to channels cyclically according to their preferences. If a channel is empty and no other requests are received, the channel is occupied by the request sender. If channel \(k_{1}\) receives multiple requests from initiators, compare all \(\hat{\mu }_{t}^{init, k_{1}}\) (including \(\hat{\mu }_{t}^{n_1, k_{1}}\) if user \(n_1\) occupies channel \(k_{1}\) at time slot t ), where init indicates all initiators sending requests to channel \(k_{1}\) . The user with the largest value occupies channel \(k_1\) . In addition, if the largest one is the initiator, the channels are exchanged with user \(n_1\) and the current preference cycle is terminated. Otherwise, the cycle continues. For the exchange step with FSCA as the target state, the process is similar to that of SCA, with the major difference being the exchange condition. The detailed steps for SCA and FSCA are shown in Fig. 6 and 7, respectively.
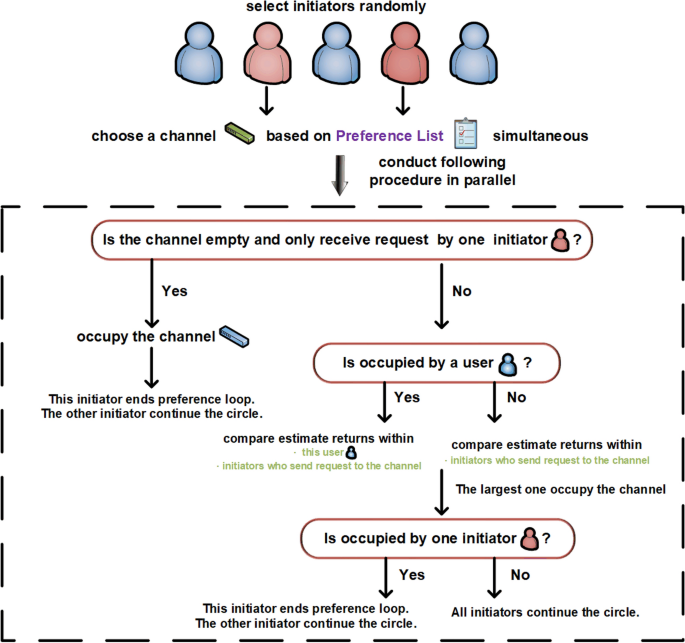
Exchange steps with SCA as the target state.
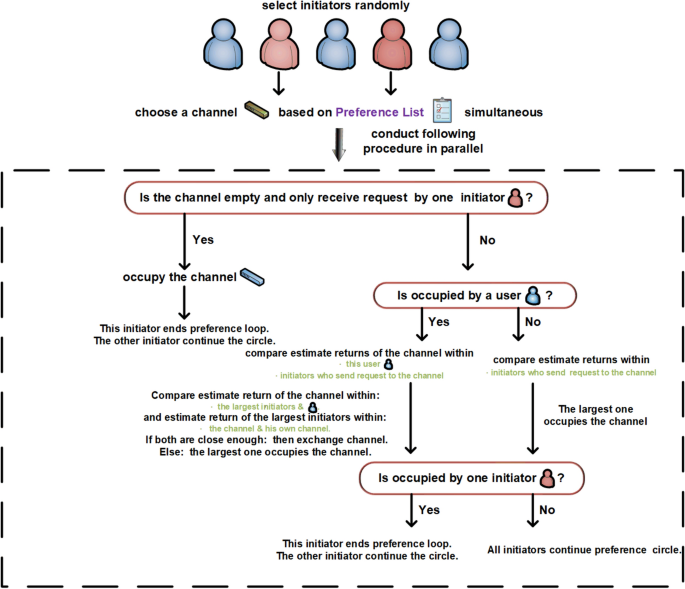
Exchange steps with FSCA as the target state.
The performance of PPL-LC with SCA
The PPL-LC algorithm is initially tested using SCA as the target state. Ten channels and eight users, designated as \(\{a, b,\ldots ,h\}\) , are configured. The initial and subsequent channel distributions of each user are set as follows (Fig. 8 ). The size of each black block represents the initial channel distribution set by each user. In other words, the larger the black block, the greater the user’s satisfaction with the channel and the higher the probability of successful data transmission. Notably, these data settings will be used throughout the experiments.
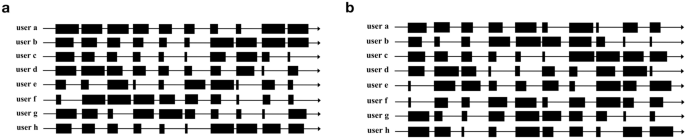
Initial channel distribution settings. ( a ) The distributions of users for each channel during 0–3000 iterations. ( b ) The distributions after 3000 iterations.
A small number of channel exchanges may prevent the algorithm from achieving the maximum information throughput. When there is a small number of channel exchanges, the information throughput may reach equilibrium more quickly, resulting in a local optimum and an inability to achieve the maximum information throughput. However, an excessive number of channel exchanges can also cause resource waste between users. Therefore, it is crucial to balance the relationship between the number of channel exchanges and throughput with two aspects. On the one hand, it is necessary to ensure sufficient exchange times so that the information throughput achieved by all users will not fall into the local optimum. On the other hand, it is also necessary to control the number of channel exchanges so as not to waste resources.
When the channel distribution does not change over time t , the relationship between the exchange amount and time, as well as the transmitted information bits and time, are examined separately. In Fig. 9 , the performances of the PPL-LC, DSSL, and CSM-MAB algorithms with respect to the aforementioned metrics are compared. Fig. 9 a shows that the DSSL and CSM-MAB algorithms reach equilibrium faster, but the information throughput under the SCA state is lower (namely, the SCA state is not reached). Although it takes the PPL-LC algorithm longer (around 100 time slots) to reach the SCA state, it ultimately achieves higher information throughput. From Fig. 9 b, the number of channel exchanges for the CSM-MAB algorithm is extremely lower than that of the DSSL algorithm, close to the exchange times of the PPL-LC algorithm, which may contribute to its inability to reach the SCA state. In addition, the number of channel exchanges for the DSSL algorithm is significantly higher than those of the other two algorithms, resulting in inefficient resource utilization in practical implementation.
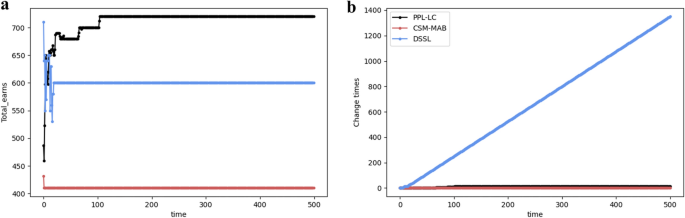
The performance comparison of the PPL-LC, DSSL, and CSM algorithms. ( a ) The trend of transmitted information bits over time. ( b ) The performance exchange times over time.
After 3000 iterations, the channel distribution environment changes. As shown in Fig. 10 , the SCA state has been achieved before the 3000th iteration. However, the information throughput experiences a sharp decline after the 3000th iteration. As a result, the channel exchange process is restarted, re-establishing of the SCA state under the new distribution. In conjunction with this, the number of channel exchanges, which had remained stable, also increased after the 3000th iteration.
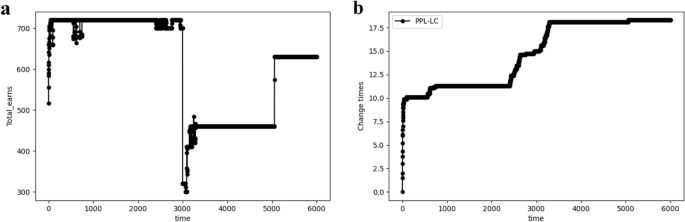
The performance of PPL-LC. ( a ) The relationship between transmitted information bits and time when distribution changes. ( b ) The relationship between the number of channel exchanges and the time when distribution changes.
The performance of PPL-LC with FSCA
In the following, the FSCA state is considered the target state. Similar to the SCA state, the performances of the three algorithms in terms of throughput and change times are considered (Fig. 11 ). Under the FSCA target, the PPL-LC algorithm fluctuates after reaching a high information throughput, corresponding to the user’s overall selection switching back and forth between several fuzzy states. With more observations, the PPL-LC algorithm can result in the throughput tending to be stable. Meanwhile, the DSSL and CSM-MAB algorithms still cannot reach the FSCA state, and the number of channel exchanges of the CSM-MAB algorithm quickly reaches equilibrium, whereas the number of channel exchanges of the DSSL algorithm gradually increases as users continue to exchange between empty channels.
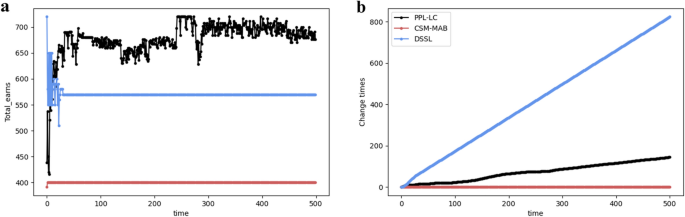
The performance of PPL-LC with FSCA. ( a ) The relationship between total information transmitted and time, which also exhibits the comparison with the DSSL and CSM algorithms. ( b ) The relationship between exchanges and time.
Previous research has demonstrated that laser chaos is effective at random number generation and can have a good effect on MAB problems. Considering these facts, the usefulness of ultrafast chaos sequences for real wireless applications was confirmed 14 . Despite this, there is inadequate research on the potential applications of the laser chaos series. In this study, we explored the high performance of ultrafast laser chaos for CRNs with multiple users. We proposed a parallel processing algorithm using laser chaos to attain two stable states: the classical SCA and FSCA. We discovered that the proposed algorithm provides improved performance, specifically in terms of throughput, in dynamic spectrum access. In addition, the algorithm demonstrates good adaptability to changing environments, which is a key feature in dynamic spectrum access scenarios where the channel conditions may vary over time. These combined capabilities make the proposed algorithm a valuable tool for improving the performance of CRNs with multiple users.
These findings of this study extend those of Takeuchi 14 with multiple users and unlimited channel numbers, confirming that ultrafast laser chaos gives high performance in wireless communication networks. In addition, this study expands the classical SCA and describes the circumstance where users have vague preferences. Therefore, this study indicates that laser chaos has positive effects on wireless communication networks. Particularly, to the best of our knowledge, the proposed algorithm is the first to apply laser chaos to channel selection with multiple users. Although this study uses laser-chaos-based decision-making for dynamic channel selection, future work can focus on more general channel assignment scenarios.
In this section, the proposed PPL-LC algorithm is presented, along with the parameter adjustment of the laser chaos algorithm.
Brief description of the PPL-LC algorithm
With detailed discussions in previous sections, the PPL-LC algorithm is described in detail (Fig. 12 ). It comprises three parts: initializing, updating and exchanging. In the initializing part, it employs the Communication-free learning (CFL) algorithm 18 to reach an initial orthogonal configuration (line 1). The CFL algorithm convergence quickly to an orthogonal configuration, allowing users to proceed with the updating and exchanging parts.
Next, in the updating part, users select the channel according to the random number generated by laser chaos (lines 5–10). Then,users send a message and obtain feedback. Based on this, the return and corresponding parameters are adjusted (lines 11–12). The above steps are all supported by the principle introduced in the laser chaos algorithm. Therefore, users obtain a list of channels they prefer over their current action.
Upon arriving at the exchanging part, randomly select initiators among users (line 15). All the initiators choose a channel based on their preference list simultaneously. Every initiator will then observe whether the channel is empty and only receiving one initiator’s request (line 19). If this occurs, he/she can occupy this channel immediately (lines 20–21). Otherwise, further observations are reqquired for the selection. The initiator proceeds to signal whether the desired channel is being occupied by a user who is not an initiator. If it is, this responding user will consider whether exchanging channels with the initiator will improve his/her osituation based on his/her preference ranking. If the responder agrees to the swap, it will be done (lines 24–26). If the responder refuses, the initiator will approach the next best channel on the list.
If the desired channel is not occupied by a user, but initiators, all the initiators who have sent requests to this channel will compare their estimated returns. The initiator with the largest estimated return will occupy the channel. If multiple initiators have the same highest estimated return, they will all move on to the next best channel on their list. All users will continue the process of seeking a partner who is willing to exchange channels with them until they either find one or exhaust their list of potential swaps. This part of the algorithm is illustrated in Fig. 10 .

The PPL-LC algorithm.
Parameter adjustment
When user n occupies channel k to transmit information and receives a positive return, the parameters of the laser chaos algorithm are adjusted as follows:
If the feedback return is equal to zero, it is updated with
Data analysis
For laser chaos generation, there are two ways to simulate: optical system and computer simulation. This study adopts computer simulation to obtain random numbers and the simulation with real optical systems will be studied in later papers. This simulation is mainly completed through the example-DiodeWithFeedbackSimulation in Matlab Simulate and the chaotic waveform is sampled to form a random sequence. Compared with building an optical system, this method is more convenient. The simulation is performed on a personal computer (R9000X 2021, R7 5800H 3.2GHz, 16GB RAM, Windows 11, Matlab R2016b).
Parameters setting
In this study, the initial parameters of the laser chaos algorithm are selected as follows: \(\Lambda = 1,\Omega = 1,\alpha = 0.99\) . The values of \(\Delta _{S}\) and \(\Delta _{L}\) are the same as in the previous experiments, and we convert the signal level value obtained by laser chaos to 8 bits, namely, \(-128 \le s(t) \le 127\) 19 .

Data availability
The datasets generated during this study are available from the corresponding author upon reasonable request.
Mitola, J. & Maguire, G. Cognitive radio: Making software radios more personal. IEEE Pers. Commun. 6 (4), 13–18 (1999).
Article Google Scholar
Wang, B. & Liu, K. J. R. Advances in cognitive radio networks: A survey. IEEE J. Sel. Top. Signal Process. 5 (1), 5–23 (2011).
Article ADS Google Scholar
Zhao, Q. & Sadler, B. A survey of dynamic spectrum access. IEEE Signal Process. Mag. 24 (3), 79–89 (2007).
Leshem, A., Zehavi, E. & Yaffe, Y. Multichannel opportunistic carrier sensing for stable channel access control in cognitive radio systems. IEEE J. Sel. Areas Commun. 30 (1), 82–95 (2012).
Motamedi, A., & Bahai, A. Dynamic channel selection for spectrum sharing in unlicensed bands. European Transactions on Telecommunications and Related Technologies, 2007.
Lai, L., Jiang, H. & Poor, H. Cognitive medium access: Exploration, exploitation, and competition. IEEE Trans. Mobile Comput. 10 (2), 239–253 (2011).
Avner, O., & Mannor, S. Multi-user lax communications: A multi-armed bandit approach. IEEE INFOCOM 2016-The 35th Annual IEEE International Conference on Computer Communications, 1–9 (2016).
Bistritz, I. & Leshem, A. Distributed multi-player bandits-a game of thrones approach. Adv. Neural Inf. Process. Syst. 1 , 7222–7232 (2018).
Google Scholar
Gafni, T. & Cohen, K. Distributed learning over Markovian fading channels for stable spectrum access. IEEE Access 10 , 46652–46669 (2022).
Naruse, M., Terashima, Y., Uchida, A. & Kim, S. Ultrafast photonic reinforcement learning based on laser chaos. Sci. Rep. 7 (1), 1–10 (2017).
Article ADS CAS Google Scholar
Uchida, A. et al. Fast physical random bit generation with chaotic semiconductor lasers. Nat. Photon. 2 (12), 728–732 (2008).
Naruse, M. et al. Scalable photonic reinforcement learning by time-division multiplexing of laser chaos. Sci. Rep. 8 (1), 1–16 (2018).
Narisawa, N., Chauvet, N., Hasegawa, M. & Makoto, N. Arm order recognition in multi-armed bandit problem with laser chaos time series. Sci. Rep. 11 (1), 1–11 (2021).
Takeuchi, S., Hasegawa, M., Kanno, K., Uchida, A. & Naruse, M. Dynamic channel selection in wireless communications via a multi-armed bandit algorithm using laser chaos time series. Sci. Rep. 10 (1), 1–7 (2020).
Chen, Z. Strong laws of large numbers for sub-linear expectations. Sci. China Math. 59 , 945–954 (2016).
Article MATH Google Scholar
Peng, S. Nonlinear expectation and stochastic calculus under uncertainty, (Springer, 2019).
Kim, S., Aono, M. & Nameda, E. Efficient decision-making by volume-conserving physical object. New J. Phys. 17 (8), 083023 (2014).
Leith, D., Clifford, P., Badarla, V. & Malone, D. WLAN channel selection without communication. Comput. Networks 56 (4), 1424–1441 (2012).
Berry, D. & Fristedt, B. Bandit problems: Sequential allocation of experiments. J. Oper. Res. Soc. Ser. A (Gen.) 149 (3), 271–271 (1986).
Download references
Acknowledgements
The authors would like to thank two anonymous referees for the extensive and constructive suggestions that helped to improve this paper considerably. The work is supported by National Key R &D Program of China (No. 2018YFA0703900), Shandong Provincial Natural Science Foundation (No.ZR2021MA098).
Author information
Authors and affiliations.
Zhongtai Securities Institute for Financial Studies, Shandong University, Jinan, 250100, China
Zengjing Chen, Lu Wang & Chengzhi Xing
You can also search for this author in PubMed Google Scholar
Contributions
Z.J.C., L.W. and C.Z.X. designed and conducted the experiments, and wrote the paper.
Corresponding author
Correspondence to Lu Wang .
Ethics declarations
Competing interests.
The authors declare no competing interests.
Additional information
Publisher's note.
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Open Access This article is licensed under a Creative Commons Attribution 4.0 International License, which permits use, sharing, adaptation, distribution and reproduction in any medium or format, as long as you give appropriate credit to the original author(s) and the source, provide a link to the Creative Commons licence, and indicate if changes were made. The images or other third party material in this article are included in the article's Creative Commons licence, unless indicated otherwise in a credit line to the material. If material is not included in the article's Creative Commons licence and your intended use is not permitted by statutory regulation or exceeds the permitted use, you will need to obtain permission directly from the copyright holder. To view a copy of this licence, visit http://creativecommons.org/licenses/by/4.0/ .
Reprints and permissions
About this article
Cite this article.
Chen, Z., Wang, L. & Xing, C. Efficient dynamic channel assignment through laser chaos: a multiuser parallel processing learning algorithm. Sci Rep 13 , 1353 (2023). https://doi.org/10.1038/s41598-023-28282-z
Download citation
Received : 13 September 2022
Accepted : 16 January 2023
Published : 24 January 2023
DOI : https://doi.org/10.1038/s41598-023-28282-z
Share this article
Anyone you share the following link with will be able to read this content:
Sorry, a shareable link is not currently available for this article.
Provided by the Springer Nature SharedIt content-sharing initiative
This article is cited by
Multi-dimensional resource allocation strategy for leo satellite communication uplinks based on deep reinforcement learning.
- Feipeng Qiu
- Jilong Zhao
Journal of Cloud Computing (2024)
By submitting a comment you agree to abide by our Terms and Community Guidelines . If you find something abusive or that does not comply with our terms or guidelines please flag it as inappropriate.
Quick links
- Explore articles by subject
- Guide to authors
- Editorial policies
Sign up for the Nature Briefing newsletter — what matters in science, free to your inbox daily.
Dynamic Channel Assignment in Wireless LANs
Ieee account.
- Change Username/Password
- Update Address
Purchase Details
- Payment Options
- Order History
- View Purchased Documents
Profile Information
- Communications Preferences
- Profession and Education
- Technical Interests
- US & Canada: +1 800 678 4333
- Worldwide: +1 732 981 0060
- Contact & Support
- About IEEE Xplore
- Accessibility
- Terms of Use
- Nondiscrimination Policy
- Privacy & Opting Out of Cookies
A not-for-profit organization, IEEE is the world's largest technical professional organization dedicated to advancing technology for the benefit of humanity. © Copyright 2024 IEEE - All rights reserved. Use of this web site signifies your agreement to the terms and conditions.
- Skip to content
- Skip to search
- Skip to footer
Cisco Catalyst 9800 Series Wireless Controller Software Configuration Guide, Cisco IOS XE Amsterdam 17.3.x
Bias-free language.
The documentation set for this product strives to use bias-free language. For the purposes of this documentation set, bias-free is defined as language that does not imply discrimination based on age, disability, gender, racial identity, ethnic identity, sexual orientation, socioeconomic status, and intersectionality. Exceptions may be present in the documentation due to language that is hardcoded in the user interfaces of the product software, language used based on RFP documentation, or language that is used by a referenced third-party product. Learn more about how Cisco is using Inclusive Language.
- Overview of Cisco 9800 Series Wireless Controllers
- System Configuration
- Wireless Management Interface
- BIOS Protection
- Management over Wireless
- Smart Licensing
- Smart Licensing Using Policy
Best Practices
- Upgrading the Cisco Catalyst 9800 Wireless Controller Software
- In-Service Software Upgrade
- Software Maintenance Upgrade
- Efficient Image Upgrade
- Predownloading an Image to an Access Point
- N+1 Hitless Rolling AP Upgrade
- NBAR Dynamic Protocol Pack Upgrade
- Wireless Sub-Package for Switch
- Country Codes
- Sniffer Mode
- Monitor Mode
- AP Priority
- FlexConnect
- Converting Autonomous Access Points to Lightweight Mode
- AP Crash File Upload
- Access Point Plug-n-Play
- 802.11 Parameters for Cisco Access Points
- 802.1x Support
- CAPWAP Link Aggregation Support
- DHCP and NAT Functionality on Root Access Point
- OFDMA Support for 11ax Access Points
- AP Audit Configuration
- AP Support Bundle
- Cisco Flexible Antenna Port
- LED States for Access Points
- Secure Data Wipe
- Radio Resource Management
- Coverage Hole Detection
- Optimized Roaming
- Cisco Flexible Radio Assignment
- XOR Radio Support
- Cisco Receiver Start of Packet
- Client Limit
- Unscheduled Automatic Power Save Delivery
- Target Wake Time
- Enabling USB Port on Access Points
- Dynamic Frequency Selection
- Cisco Access Points with Tri-Radio
- Cisco Catalyst Center Assurance Wi-Fi 6 Dashboard
- AP Packet Capture
- DHCP Option82
- RADIUS Realm
- RADIUS Accounting
- Cisco StadiumVision
- Persistent SSID Broadcast
- Network Monitoring
- Lobby Ambassador Account
- Guest User Accounts
- Network Mobility Services Protocol
- Application Visibility and Control
- Cisco Hyperlocation
- FastLocate for Cisco Catalyst Series Access Points
- IoT Services Management
- IoT Module Management in the Controller
- Cisco Spaces
- EDCA Parameters
- 802.11 parameters and Band Selection
- NBAR Protocol Discovery
- Conditional Debug, Radioactive Tracing, and Packet Tracing
- Aggressive Client Load Balancing
- Accounting Identity List
- Wireless Multicast
- Map-Server Per-Site Support
- Volume Metering
- Enabling Syslog Messages in Access Points and Controller for Syslog Server
- Login Banner
- Wi-Fi Alliance Agile Multiband
- DNS-Based Access Control Lists
- Allowed List of Specific URLs
- Policy Enforcement and Usage Monitoring
- Web-Based Authentication
- Central Web Authentication
- ISE Simplification and Enhancements
- Authentication and Authorization Between Multiple RADIUS Servers
- AAA Dead-Server Detection
- RADIUS Server Load Balancing
- Secure LDAP
- RADIUS DTLS
- Internet Protocol Security
- MAC Filtering
- IP Source Guard
- Managing Rogue Devices
- Classifying Rogue Access Points
- Configuring Secure Shell
- Private Shared Key
- Multi-Preshared Key
- Multiple Authentications for a Client
- Cisco TrustSec
- SGT Inline Tagging and SXPv4
- Controller Self-Signed Certificate for Wireless AP Join
- Locally Significant Certificates
- Certificate Management
- Cisco Umbrella WLAN
- Device Analytics
- Advanced WIPS
- Wi-Fi Protected Access 3
- Transport Layer Security Tunnel Support
- Local Extensible Authentication Protocol
- Disabling IP Learning in FlexConnect Mode
- NAT Support on Mobility Groups
- Static IP Client Mobility
- Mobility Domain ID - Dot11i Roaming
- 802.11r Support for Flex Local Authentication
- Opportunistic Key Caching
- High Availability
- Quality of Service
- Wireless Auto-QoS
- Native Profiling
- Air Time Fairness
- IPv6 Non-AVC QoS Support
- QoS Basic Service Set Load
- IPv6 Client IP Address Learning
- IPv6 Client Mobility
- IPv6 Support on Flex and Mesh
- IPv6 CAPWAP UDP Lite Support
- Neighbor Discovery Proxy
- Address Resolution Protocol Proxy
- Cisco CleanAir
- Bluetooth Low Energy
- Persistent Device Avoidance
- Spectrum Intelligence
- Spectrum Analysis
- Spectrum Expert Mode
- Mesh Access Points
- VideoStream
- Software-Defined Access Wireless
- Passive Client
- Encrypted Traffic Analytics
- Fabric in a Box with External Fabric Edge
- Embedded Wireless on Cisco Catalyst 9000 Series Switches for Single Secure Site Deployment (Non-SDA)
- VLAN Groups
- Remote LANs
- RLAN External Module
- Client Roaming Across Policy Profile
- Network Access Server Identifier
- DHCP for WLANs
- WLAN Security
- Workgroup Bridges
- Peer-to-Peer Client Support
- Wireless Guest Access
- Wired Guest Access
- 802.11r BSS Fast Transition
- BSS Coloring
- Assisted Roaming
- Management Frame Protection
- Deny Wireless Client Session Establishment Using Calendar Profiles
- Ethernet over GRE
- Link Aggregation Group
- Hotspot 2.0
- User Defined Network
- Express Wi-Fi by Facebook
- Aironet Extensions IE (CCX IE)
- BSSID Counters
- Cisco Catalyst Center Service for Bonjour Solution Overview
- Configuring Local Area Bonjour for Wireless Local Mode
- Configuring Local Area Bonjour for Wireless FlexConnect Mode
- Configuration Example for Local Mode - Wireless and Wired
- Configuration Example for FlexConnect Mode - Wireless and Wired
- Multicast Domain Name System

Chapter: Best Practices
Disable aironet ie, disable management over wireless, configuring https to use a specific trustpoint, load balancing, virtual gateway ip, local profiling, vrf and routing protocol, wlan with wpa3, wpa2 or 802.1x, client exclusion, user login policies, auto coverage hole detection, auto dynamic channel assignment, auto transmit power control, cleanair detection, event driven rrm, wifi interference, dca cisco ap load, best channel width, flexible radio assignment, high ssid counts, client band select, 5ghz low data rates, 2.4ghz low data rates, wlan configuration, optimized roaming disabled, 5ghz edca fastlane, 5ghz enabled, 5ghz mcs rates.
Infrastructure
Description— Aironet IE is a Cisco proprietary attribute used by Cisco devices for better connectivity. It contains information, such as the access point name, load, number of associated clients, and so on sent out by the access point (AP) in the beacon and probe responses of the Cisco Catalyst 9800 Series Wireless Controller . The Cisco Client Extensions (CCX) clients use this information to choose the best AP with which to associate.
The CCX software is licensed to manufacturers and vendors of third-party client devices. The CCX code resident on these clients enables them to communicate wirelessly with Cisco APs and to support Cisco features that other client devices do not. The features are related to increased security, enhanced performance, fast roaming, and power management.
Aironet IE is optional for CCX based clients, however it can cause compatibility issues with some types of wireless clients. The recommendation is to enable for WGB and Cisco voice, but for general production network, it can be beneficial to disable Aironet IE after testing.
CCX Aironet IE feature should be disabled.
Selected— CCX Aironet IE must be disabled on one or more *ACTIVE* WLANs.
Unselected— CCX Aironet IE enabled on all *ACTIVE* WLANs.
CLI Option—Enable support for Aironet IEs for a particular WLAN by entering this command:
Device# conf t
Device(config)# wlan <profile-name> <wlan-id> <ssid>
Device(config-wlan)# ccx aironet-iesupport
CLI Option—Disable support for Aironet IEs for a particular WLAN by entering this command:
Device(config-wlan)# no ccx aironet-iesupport
Description—The Cisco WLAN solution Disable Management over Wireless feature allows Cisco WLAN solution operators to monitor and configure local controller using a wireless client.
Management over wireless should be disabled for security reasons. Clicking Fix it Now disables management over wireless.
Selected—Enabled
Unselected—Disabled
CLI Option—Disable management over wireless by entering this command:
CLI Option—Enable management over wireless by entering this command:
HTTPs for Management
Description—HTTPs for management provides greater security by allowing secure access.
Secure Web Access (HTTPS) should be enabled for managing the Cisco Catalyst 9800 Series Wireless Controller . Web Access (HTTP) should be disabled.
Selected—HTTPS enabled; HTTP disabled
Unselected—HTTPS enabled, HTTP enabled or HTTPS disabled, HTTP enabled
CLI Options:
Disable the web mode to deny users to access the controller GUI using http://ip-address, by entering this command:
Enable Secure Web Access mode to allow users to access the controller GUI using https://ip-address, by entering this command:
If a device is configured with more than one crypto trustpoint (which could be for a self-signed or identity certificate), enter the following CLI command to use a specific trustpoint for HTTPS communication:
If the preceding CLI is not configured, HTTPS can use any configured trustpoint. HTTPS chooses the trustpoint in the following order:
Identity certificate
Self-signed certificate
CA certificate
Description—In dense production networks, controllers have been verified to function optimally with load balancing ON and window size set at 5 or higher. In practical, this means load balancing behavior is only enabled when, for example, a large group of people congregate in a conference room or open area (meeting or class). Load balancing is very useful to spread these users between various available APs in such scenarios.
Load balancing should be enabled. For time sensitive application such as voice, it can cause roaming issues. Therefore, it is recommended to test before enabling load balancing on the Cisco Catalyst 9800 Series Wireless Controller . Clicking Restore Default enables load balancing on the Cisco Catalyst 9800 Series Wireless Controller , which may impact service at the time.
Selected— Load balancing disabled on all active WLANs.
Unselected— Load balancing enabled on one or more active WLANs.
CLI Option—Enable load balancing on a WLAN by entering this command:
CLI Option—Disable load balancing on a WLAN by entering this command:
Description—Network Time Protocol (NTP) is very important for several features. It is mandatory to use NTP synchronization on the Cisco Catalyst 9800 Series Wireless Controller if you use any of these features: Location, SNMPv3, access point authentication, or MFP. The controller supports synchronization with NTP.
The NTP server is used to sync the Cisco Catalyst 9800 Series wireless controller's time.
Selected—NTP is configured on the Cisco Catalyst 9800 Series wireless controller.
Unselected—NTP is not configured on the Cisco Catalyst 9800 Series wireless controller.
Enable NTP server by entering this command:
Description: Virtual gateway IP should be enabled. Clicking Fix it Now enables virtual gateway IP .
Selected: Enabled
Unselected: Disabled
Description—The controller in Cisco Catalyst 9800 series -enabled APs can determine the client type from the information received when a client device associates with the controller. This controller acts as the collector of the information, and either displays the information directly on the Cisco Catalyst 9800 Series Wireless Controller GUI dashboard or sends required data to the ISE optimally.
Local profiling (DHCP/HTTP) should be enabled on the Cisco Catalyst 9800 Series wireless controller.
CLI Option—Enable local profiling (DHCP/HTTP) on all WLANs by entering this command:
Cisco Catalyst 9800 Series Wireless Controller does not support VRFs or routing protocols. The controller should not be used as a router for wireless clients.
The only exception is the mgmt-vrf on the management port on physical appliances.
We recommend that you use a custom site-tag instead of the default-site-tag for APs.
For APs in local mode (or local site-tag), we recommend that you limit the number of APs per site-tag to 500. For example, if you have more than 500 APs in a building, use two site-tags for the building. Seamless and fast-roaming is supported across site-tags. You can configure more or less APs per site-tag, but the recommendation is not to exceed these numbers:
For FlexConnect APs and related remote site-tags, if seamless roaming is required, the limit is 100 APs per site-tag.
Description—WLAN should be using 802.1x or WPA2 or WPA3 security. You can enable this from the linked WLAN page. The default day 0 setting does not mandate configuring 802.1x.
Status—If disabled, click Manual Configuration to specify the security setting of the WLAN.
Selected—Either 802.1x or WPA2 is enabled on at least one WLAN.
Unselected—Neither security is enabled on any WLAN.
CLI option—Enable WLAN with WPA2 or 802.1x security by entering this command:
Description—When the client fails to authenticate, the controller excludes the client. The client cannot connect to the network until the exclusion timer expires or is manually overridden by the administrator.
Client exclusion detects authentication attempts made by a single device. When the device exceeds a maximum number of failures, that MAC address is not allowed to associate any longer to the controller.
Client exclusion is enabled by default on the primary AP allowing it to exclude clients from joining the controller during the above events.
When you click Fix it , the following components are enabled:
Excessive 802.11 Association Failures
Excessive 802.1X Authentication Failures
Excessive 802.1X Authentication Timeout
IP Theft or IP Reuse
Excessive Web Authentication Failures
Selected—Client exclusion is enabled for all events
Unselected—Client exclusion is disabled for all events
CLI Option—Enable client exclusion for all events by entering this command:
CLI Option—Disable client exclusion for all events by entering this command:
You must use the wireless exclusion list client mac address to manually add clients to the exclusion list and use the no form of the command to remove the client from the exclusion list. However; the no form of the command does not remove the clients that are dynamically added to the exclusion list.
Description—The user login policies are provided to limit the number of concurrent logins to the controller. You can limit the number of concurrent logins, and the recommendation is greater than default of 0 (unlimited).
Selected— User login policies enabled only if the login count is set to either 0 or 8.
Unselected— User login policies disabled only if the login count is set to either 0 or 8.
CLI Option:
Verify the user login policies by entering this command:
Configure user login policies by entering this command:
RF Management
Description—Auto CHD should be enabled.
The controller uses the quality of client signal levels reported by the APs to determine if the power level of that AP needs to be increased. Coverage Hole Detection (CHD) is controller independent, so the RF group leader is not involved in those calculations. The controller knows how many clients are associated with a particular AP and what are the signal-to-noise ratio (SNR) values for each client.
If a client SNR drops below the configured threshold value on the controller, the AP increases its power level to try to compensate for the client. The SNR threshold is based on the transmit power of the AP and the coverage profile settings on the controller.
For instructions on how to configure auto CHD, see the Cisco Catalyst 9800 Seriess Wireless Controller Software Configuration Guide, Cisco IOS XE Gibraltar 16.12.x .
Selected—CHD enabled
Unselected— None or one enabled
CLI Option—Enable auto CHD by entering this command:
CLI Option—Disable auto CHD by entering this command:
Description—Auto DCA should be enabled to allow RRM to select best channels for each radio.
When a wireless network is first initialized, all radios participating require a channel assignment to operate without interference - optimizing the channel assignments to allow for interference free operation is DCA's job. Wireless network does this using the air metrics reported by each radio on every possible channel, and providing a solution that maximizes channel bandwidth and minimizes RF interference from all sources - Self (signal), other networks (foreign interference), Noise (everything else).
DCA is enabled by default and provides a global solution to channel planning for your network.
Selected—DCA is enabled for 2.4 / 5 GHz
Unselected—None or one is enabled
CLI Option—Enable auto DCA by entering this command:
CLI Option—Disable auto DCA by entering this command:
Description—The controller dynamically controls the access point transmit power based on real-time wireless LAN conditions. You can choose between two versions of transmit power control: TPCv1 and TPCv2. With TPCv1, power can be kept low to gain extra capacity and reduce interference. With TPCv2, transmit power is dynamically adjusted with the goal of minimum interference. TPCv2 is suitable for dense networks. In this mode, there could be higher roaming delays and coverage hole incidents.
Auto TPC is enabled by default to allow RRM to select best transmit power for each radio.
Selected—TPC enabled for 2.4 / 5 GHz
Unselected—None or one enabled
CLI Option—Enable Auto TPC by entering this command:
Description—CleanAir should be enabled.
To effectively detect and mitigate RF interference, enable CleanAir whenever possible. There are recommendations to various sources of interference to trigger security alerts, such as generic DECT phones, jammer, and so on.
Verify CleanAir configuration on a network by entering this command:
(Cisco Controller) > show 802.11{a|b} cleanair config
Enables CleanAir functionality on a network by entering this command:
Enables interference detection specifically for jammer by entering this command:
Description—Spontaneous interference is interference that appears suddenly on a network, perhaps jamming a channel or a range of channels completely. The Cisco CleanAir spectrum event-driven radio resource management (RRM) feature allows you to set a threshold for air quality (AQ) that, if exceeded, triggers an immediate channel change for the affected access point. Most RF management systems can avoid interference, but this information takes time to propagate through the system. Cisco CleanAir relies on AQ measurements to continuously evaluate the spectrum and can trigger a move within 30 seconds. For example, if an access point detects interference from a video camera, it can recover by changing channels within 30 seconds of the camera becoming active. Cisco CleanAir also identifies and locates the source of interference so that more permanent mitigation of the device can be performed at a later time.
Event driven RRM is enabled by default.
Selected— Event driven RRM is disabled on both 5GHz and 2.4GHz.
Unselected— Event driven RRM is enabled on either 5GHz or 2.4GHz.
CLI Option—Enable Cisco CleanAir spectrum event-driven RRM by entering this command:
Description—To improve handling of WiFi Interference, Rogue Severity was added to the ED-RRM metrics. If a rogue access point is generating interference above a given threshold, this feature changes channels immediately instead of waiting until the next DCA cycle.
This should be used when ED-RRM is enabled. It should be avoided on buildings with very large number of collocated WiFi networks (multi-tenant buildings) that are 100% overlapping.
Selected—WiFi interference is enabled.
Unselected—WiFi interference is disabled.
Verify the WiFi interference by entering this command:
To enable WiFi interference, you need to perform the following:
Configure duty cycle by entering this command:
Enable EDRRM by entering this command:
Enable Rogue contribution by entering this command:
Description—Avoid using this option to avoid frequent changes in DCA due to varying load conditions, this is disabled by default.
Selected—AP Load is disabled.
Unselected—AP Load is enabled.
Verify the current status by entering this command:
Enable DCA Cisco AP Load by entering this command:
Disable DCA Cisco AP Load by entering this command:
Description—Dynamic bandwidth selection selects the widest channel width with the highest client data rates and lowest channel utilization per radio. This minimizes data retries and CRC errors on the 5 GHz band while avoiding rogue APs and CleanAir Interferers.
Selected—Channel width is selected as Best on both bands.
Unselected—Channel width is not selected as Best on both bands.
CLI Option—Enable best channel width by entering this command:
Description—Flexible radio assignment (FRA) enables automatic assignment of the XOR 2.4GHz radios to other roles such as 5 GHz and Monitor.
We recommend that you enable FRA when you have APs such as the Cisco Aironet 2800 and 3800 Series that support XOR operation.
Selected— FRA is disabled.
Unselected— FRA is enabled.
CLI Option: Enable FRA by entering this command:
Description—Number of WLANs should be less than 4.
We recommend limiting the number of service set identifiers (SSIDs) configured at the controller. You can configure 16 simultaneous SSIDs (per radio on each AP), but as each WLAN/SSID needs separate probe responses and beaconing, the RF pollution increases as more SSIDs are added. Furthermore, some smaller wireless stations like PDA, WiFi Phones, and barcode scanners cannot cope with a high number of basic SSID (BSSID) information. This results in lockups, reloads, or association failures. Also the more SSIDs, the more beaconing needed, so less RF time is available for real data transmits. Cisco recommends one to three SSIDs for corporate, and one SSID for high-density designs. AAA override can be leveraged for per user VLAN/ settings on a single SSID scenario.
The AP must beacon at the lowest mandatory speed set for each WLAN, in order to be able to reach the farthest stations irrespective of their location. This reduces available air time for client traffic.
Status—Click Manual Configuration to manually configure the number of service set identifiers (SSIDs) configured at the controller.
Selected—Active SSID count is 4 or less.
Unselected—Active SSID count is more than 4.
Verify the number of WLANs by entering this command:
(Cisco Controller) > show wlan summary
Disable unwanted WLANs by entering this command:
Description—Band selection should be enabled. However, if there is interactive traffic such as voice or video on the WLAN, do not use band selection. Clicking Enable turns band selection on.
Band selection enables client radios that are capable of dual-band (2.4 and 5 GHz) operation to move to a less congested 5 GHz AP. The 2.4 GHz band is often congested. Clients on this band typically experience interference from Bluetooth devices, microwave ovens, and cordless phones as well as co-channel interference from other APs because of the 802.11b/g limit of three non-overlapping channels. To prevent these sources of interference and improve overall network performance, you can configure band selection on controller:
Band selection is enabled globally by default.
Band selection works by regulating probe responses to clients. It makes 5 GHz channels more attractive to clients by delaying probe responses to clients on 2.4 GHz channels.
Evaluate band selection for voice, particularly focusing on roaming performance. See below for further explanation.
Most newer model clients prefer 5 GHz by default if the 5 GHz signal of the AP is equal to or stronger than the 2.4-GHz signal.
Band select should be enabled for high-density designs
Also, in high-density designs, the study of available UNII-2 channels should be made. Those channels that are unaffected by Radar and also usable by the client base should be added to the RRM DCA list as usable channels.
Dual-band roaming can be slow depending on the client. If a majority of the base of voice clients exhibits a slow roaming behavior, it is more likely that the client sticks to 2.4 GHz. In this case, it has scanning issues on 5 GHz. Generally when a client decides to roam, it scans its current channel and band first. The clients generally scan for an AP that has a significantly better signal level, maybe as much as 20 dB and/or a significantly better SNR. Failing such available connection, the client may remain with its current AP. In this case, if the CU on 2.4 GHz is low and the call quality is not poor, then disabling the selected band is acceptable. However, the preferred design is to enable band selection on 5 GHz with all data rates enabled and 6 Mbps as mandatory. Then, set the 5 GHz RRM minimum Tx power level 6 dBm higher than the average 2.4 GHz power level set by RRM.
The goal of this configuration recommendation is to enable the client to obtain a band and channel with better SNR and Tx power initially. As already stated, generally when a client decides to roam, it scans its current channel and band first. So, if the client initially joins the 5 GHz band, then it is more likely to stay on the band if there are good power levels on 5 GHz. SNR levels on 5 GHz are generally better than 2.4 GHz because 2.4 GHz has only three Wi-Fi channels and is more susceptible to interference such as Bluetooth, iBeacons, and microwave signals.
802.11k is recommended to be enabled with dual-band reporting. This enables all 11k enabled clients to have the benefit of assisted roaming. With dual-band reporting enabled, the client receives a list of the best 2.4-GHz and 5-GHz APs upon a directed request from the client. Here, the client most likely looks at the top of the list for an AP on the same channel, and then on the same band as the client is currently on. This logic reduces scan times and saves battery power. Having 802.11k enabled on the WLC does not have a downside effect for non-802.11k clients.
Selected— Client band select disabled on all active WLANs.
Unselected— Client band select enabled on one or more active WLANs.
Verify Band Select by entering this command:
Device# show wlan all
Enable Band Select on a WLAN by entering this command:
Description—We recommend that low data rates of 6 and 9 Mbps are disabled on 5GHz for better performance.
Selected—Low data rates of 6 and 9 Mbps are disabled on 5GHz.
Unselected—Low data rates of 6 and 9 Mbps are enabled on 5GHz.
Disable 6Mbps on 5GHz by entering this command:
Disable 9Mbps on 5GHz by entering this command:
Description—Low data rates of 1, 2, and 5.5 Mbps should be disabled on 2.4Ghz and 11 Mbps set to not mandatory on 2.4Ghz for better performance.
Selected—Low data rates of 1, 2 or 5.5 Mbps are disabled on 2.4GHz or 11 Mbps is set to not mandatory .
Unselected—Low data rates of 1, 2 or 5.5 Mbps are enabled on 2.4GHz or 11 Mbps is set to mandatory .
Disable 1Mbps on 2.4GHz by entering this command:
Disable 2Mbps on 2.4GHz by entering this command:
Disable 5.5Mbps on 2.4GHz by entering this command:
Configure or disable 11Mbps on 2.4GHz by entering this command:
Apple Devices
Description—Allows you to identify if the WLAN is configured with recommended L2 security, QoS, and Advanced settings for Apple devices. Application Visibility should be enabled.
Status—Click Detailed to manually configure the L2 security, QoS, and advanced settings for Apple devices for individual, active WLANs.
Selected—At least one WLAN is compliant with all the recommended WLAN configurations for Apple devices.
Unselected—None of the active WLANs are compliant with all the recommended WLAN configurations for Apple devices.
Recommended configurations:
Security—Fast Transition should be adaptive enabled or enabled. If Fast transition is enabled, the Authentication Key Management should be psk or dot1x . Layer 3 security should be none. Over the DS needs to be disabled.
QOS—WMM policy should be set to required.
Advanced—11k Neighbor List or Dual Band should be enabled. 11v BSS Transition should be enabled. WLAN Radio policy should be all or 802.11a or 802.11 a/g. mDNS should be set to gateway mode.
Policy—Fastlane should be set in AutoQOS. Egress and Ingress QOS SSID policy should be set to platinum.
Description—Optimized roaming should be disabled because Apple devices use the newer 802.11r, 802.11k, or 802.11v roaming improvement.
Selected—Optimized roaming is disabled.
Unselected—Optimized roaming is enabled.
Enable optimized roaming by entering this command:
Disable optimized roaming by entering this command:
Description—Configuring the EDCA Profile as Fastlane improves Apple device performance on 5GHz networks.
Selected—The 5GHz EDCA Profile is configured as Fastlane.
Unselected—The 5GHz EDCA Profile is not configured as Fastlane.
Enable Fastlane by entering this command:
Disable Fastlane by entering this command:
Description—Enable the 5GHz radio to provide a faster and less interfering network for Apple devices.
Selected—5GHz radio is enabled on the network.
Unselected—5GHz radio is disabled on the network.
Description—All the MCS Rates (0-31) should be enabled on the 5GHz networks to help improve the performance of Apple client devices.
Selected—All the MCS rates are enabled on the 5GHz network.
Unselected—Some of the MCS rates are disabled on the 5GHz network.
Was this Document Helpful?

Contact Cisco
- (Requires a Cisco Service Contract )

IMAGES
VIDEO
COMMENTS
The Dynamic Channel Assignment (DCA) Algorithm. The Group Leader maintains the neighbor lists for all AP's in the RF Group, and organizes these neighbors into RF Neighborhoods. ... The Best Practice for most organizations today is to use no more than 40 MHz in enterprise deployments. However it really comes down to how many channels you have ...
Dynamic Channel Assignment (DCA) handled by RF group leader for a particular RF group. DCA algorithm takes following information into account 1. Load Measurement (Every AP measure the % total time occupied by Tx or Rx 802.11 frames) 2. ... Keep up the good work. I came here looking for what would be the best practices setting to configure DCA ...
Configures Dynamic Channel Assignment (DCA) algorithm parameters for the 802.11 band. add channel-number-Enter a channel number to be added to the DCA list. The range is between 1 to 14. anchor-time-Configures the anchor time for the DCA. The range is between 0 and 23 hours. global-Configures the DCA mode for all 802.11 Cisco APs
Abstract. Channel assignment techniques are used extensively in frequency reuse systems to assign time-frequency resources to each user. There are many methods of allocating a channel upon a new call arrival or handoff attempt. A good channel allocation algorithm is the one that yields high spectral efficiency for a specified quality of service ...
We design a dynamic channel assignment algorithm for IEEE 802.11 wireless networks. Our algorithm assigns channels dynamically in a way that minimizes channel interference generated by neighboring access points (APs) on a reference access point, resulting in higher throughput. We implement and simulate our algorithm using two versions (I: pick rand and II: pick first) and different number of ...
This paper addresses the channel assignment problem and specifically investigates the dynamic assignment of channels in a wireless mesh network. We present a routing-based dynamic channel assignment algorithm called R-CA that employs multiple radio channels simultaneously by equipping each node with multiple interfaces. The algorithm
An effective channel assignment algorithm for a WMN is necessary to increase the utilization rate of space and nonoverlapped channels. Static channel assignment algorithms can improve network throughput, but their accuracies are not satisfactory in common scenarios. Dynamic channel assignment algorithms can allocate channels according to the ...
A novel dynamic channel assignment algorithm with laser chaos series for multiple users, named parallel processing learning with laser chaos (PPL-LC) algorithm, is proposed to efficiently address ...
We propose a new Cochannel information based Dynamic Channel Assignment (CDCA) strategy for small and microcell systems and a new Group Dynamic Channel Assignment (GDCA) ... 6 M. Sengoku, K. Itoh and T. Matsumoto, A dynamic frequency assignment algorithm in mobile radio communication systems, Trans. TEICE, Japan, E61, No. 7, 527-533, July 1978.
This paper presents a Dynamic Channel Assignment (DCA) algorithm implemented in Matlab. It uses a cross-correlation of power spectral density (PSD) estimations of individual WLAN channels. Estimations are based on Received Signal Strength Indicator (RSSI) level from different channels of individual clients in the IEEE 802.11 WLAN. Based on RSSI and current clients' needs for channel bandwidth ...
Last Channel Assignment—The DCA algorithm runs every 600 seconds (10 minutes). This field only indicates the time (in seconds) since the algorithm last ran and not necessarily the last time a new channel assignment was made. Figure 11: Dynamic Channel Assignment Algorithm Configuration. Tx Power Level Assignment Settings via the WLC GUI
The continuous growth of IoT devices that use the 2.4 GHz radio spectrum has motivated research about spectrum occupancy, mainly the dynamic assignment optimization problem of the ISM band. For example, IEEE 802.11-based networks are easily interfered with, due to coexistence with other 2.4 GHz wireless networks, such as IEEE, 802.15.1 and IEEE 802.15.4-basednetworks. This problem causes a ...
A novel approach to solving the dynamic channel assignment (DCA) problem by using a form of realtime reinforcement learning known as Q-learning in conjunction with neural network representation, capable of achieving a performance similar to that achieved by the MAXIAVIAL, but with a significantly reduced computational complexity. One of the fundamental issues in the operation of a mobile ...
The Dynamic Channel Assignment (DCA) Algorithm. The Group Leader maintains the neighbor lists for all AP's in the RF Group, and organizes these neighbors into RF Neighborhoods. The following metrics are also tracked for each AP in the RF Group. Same Channel Contention—other AP's/clients on the same channel - also known as Co-Channel ...
Review of channel assignment approaches in multi-radio multi-channel wireless mesh network. Hassen A. Mogaibel, ... Nor Asilah Wati Abdul Hamid, in Journal of Network and Computer Applications, 2016. 4.2.1 Node connectivity in dynamic channel assignment. The dynamic channel assignment assigns the channels to interfaces for a period of time and a node can switch to a new channel according to ...
In this paper, we propose a dynamic channel-assignment algorithm which minimizes the total interferences between access points (APs) of a Wireless Local Area Network (WLAN), while maintaining the Signal to Interferences Ratio (SIR) bigger than a certain threshold for all users. The algorithm initializes the channel assignment at the APs, and calculates the SIR for each user using Integer ...
The Dynamic Channel Assignment (DCA) Algorithm. The Group Leader maintains the neighbor lists for all AP's in the RF Group, and organizes these neighbors into RF Neighborhoods. The following metrics are also tracked for each AP in the RF Group. Same Channel Contention —other AP's/clients on the same channel - also known as Co-Channel ...
We would like to show you a description here but the site won't allow us.
In the recent past, the frequency distribution in wireless networks was known to be a major issue that resulted in the unfair utilization of wireless channels. The channel assignment becomes extremely complex due to the restricted number of accessible channels for wireless local area network (WLAN) operation. Because WLAN access points (APs) are widely distributed, they begin to interfere with ...
Abstract: A traffic-aware and client-aware algorithm for dynamically assigning channels to access points (APs) in wireless local access networks (WLANs) is proposed. Traffic loads and received signal strength (RSS) values are used to characterize interference. The problem of selecting channels to minimize total interference then reduces to the Max k-Cut problem, which we efficiently solve with ...
Auto Dynamic Channel Assignment Description—Auto DCA should be enabled to allow RRM to select best channels for each radio. When a wireless network is first initialized, all radios participating require a channel assignment to operate without interference - optimizing the channel assignments to allow for interference free operation is DCA's job.