- PRO Courses Guides New Tech Help Pro Expert Videos About wikiHow Pro Upgrade Sign In
- EDIT Edit this Article
- EXPLORE Tech Help Pro About Us Random Article Quizzes Request a New Article Community Dashboard This Or That Game Popular Categories Arts and Entertainment Artwork Books Movies Computers and Electronics Computers Phone Skills Technology Hacks Health Men's Health Mental Health Women's Health Relationships Dating Love Relationship Issues Hobbies and Crafts Crafts Drawing Games Education & Communication Communication Skills Personal Development Studying Personal Care and Style Fashion Hair Care Personal Hygiene Youth Personal Care School Stuff Dating All Categories Arts and Entertainment Finance and Business Home and Garden Relationship Quizzes Cars & Other Vehicles Food and Entertaining Personal Care and Style Sports and Fitness Computers and Electronics Health Pets and Animals Travel Education & Communication Hobbies and Crafts Philosophy and Religion Work World Family Life Holidays and Traditions Relationships Youth
- Browse Articles
- Learn Something New
- Quizzes Hot
- This Or That Game
- Train Your Brain
- Explore More
- Support wikiHow
- About wikiHow
- Log in / Sign up
- Computers and Electronics
- Operating Systems

How to Assign an IP Address on a Linux Computer
Last Updated: April 11, 2024 Tested
Debian, Ubuntu, & Linux Mint
Red hat, centos, & fedora.
This article was co-authored by wikiHow staff writer, Jack Lloyd . Jack Lloyd is a Technology Writer and Editor for wikiHow. He has over two years of experience writing and editing technology-related articles. He is technology enthusiast and an English teacher. The wikiHow Tech Team also followed the article's instructions and verified that they work. This article has been viewed 730,574 times. Learn more...
This wikiHow teaches you how to assign a new IP address to your computer when using Linux. Doing so can prevent connection issues for the item in question.
Assign an IP Address to a Debian, Ubuntu, or Linux Mint Computer
No matter what version of Linux you're running, you'll need to open the Terminal and switch to root. In Debian, Ubuntu, and Linux Mint, use the "ipconfig" command to view your Internet items. Find the item you want to assign an IP address to, then type "sudo ipconfig [name] [ipaddress] netmask 255.255.255.0 up".

- Press Ctrl + Alt + T or Ctrl + Alt + F1 (if you're on a Mac, substitute the ⌘ Command key for Ctrl .
- Click the text box at the top or bottom of the screen if possible.
- Open the Menu window and find the "Terminal" application, then click on it.

- A "root" account is the Linux equivalent of an Administrator account on a Windows or Mac computer.

- The top item should be your current router or Ethernet connection. This item's name is "eth0" (Ethernet) or "wifi0" (Wi-Fi) in Linux.

- In most cases, this is the "eth0" or "wifi0" item.

- To assign an IP of "192.168.2.100" to your ethernet connection ("eth0"), for example, you'd enter sudo ifconfig eth0 192.168.0.100 netmask 255.255.255.0 here.

- If you have a different DNS server address that you would rather use, enter that in the place of 8.8.8.8 .

- 5 Find the network connection that you want to change. This will normally be the Ethernet or Wi-Fi connection, which has an IP address currently listed on the right side of the window.

- For a network named "eno12345678", for example, you'd enter vi ifcfg-eno12345678 here.

- BOOTPROTO - Change dhcp to none
- Any IPV6 entry - Delete any IPV6 entries entirely by moving the cursor to the I on the left and pressing Del .
- ONBOOT - Change no to yes

- For example: to use "192.168.2.23" as your IP address, you'd type in IPADDR=192.168.2.23 and press ↵ Enter .
- Type in PREFIX=24 and press ↵ Enter . You can also enter NETMASK=255.255.255.0 here.
- Type in GATEWAY=192.168.2.1 and press ↵ Enter . Substitute your preferred gateway address if different.

Expert Q&A
- Some very specific Linux distributions will require you to go through a different process to assign an IP address. To see your specific distribution's specifications, check online. Thanks Helpful 0 Not Helpful 0

- Don't forget to switch back to the regular (non-root) user account when you're done. Thanks Helpful 1 Not Helpful 1
You Might Also Like

- ↑ https://danielmiessler.com/study/set_ip/
- ↑ https://www.youtube.com/watch?v=oQd5eG9BZXE&t=
About This Article
- Send fan mail to authors
Reader Success Stories
Buddy HaDagi
Jan 27, 2017
Is this article up to date?
Dmitry Ugay
Oct 10, 2017

Featured Articles

Trending Articles

Watch Articles

- Terms of Use
- Privacy Policy
- Do Not Sell or Share My Info
- Not Selling Info
wikiHow Tech Help Pro:
Level up your tech skills and stay ahead of the curve

How to Assign Static IP Address on Ubuntu Linux
Brief: In this tutorial, you’ll learn how to assign static IP address on Ubuntu and other Linux distributions. Both command line and GUI methods have been discussed.
IP addresses on Linux Systems in most cases are assigned by Dynamic Host Configuration Protocol (DHCP) servers. IP addresses assigned this way are dynamic which means that the IP address might change when you restart your Ubuntu system . It’s not necessary but it may happen.
Dynamic IP is not an issue for normal desktop Linux users in most cases . It could become an issue if you have employed some special kind of networking between your computers.
For example, you can share your keyboard and mouse between Ubuntu and Raspberry Pi . The configuration uses IP addresses of both system. If the IP address changes dynamically, then your setup won’t work.
Another use case is with servers or remotely administered desktops. It is easier to set static addresses on those systems for connection stability and consistency between the users and applications.
In this tutorial, I’ll show you how to set up static IP address on Ubuntu based Linux distributions. Let me show you the command line way first and then I’ll show the graphical way of doing it on desktop.
Method 1: Assign static IP in Ubuntu using command line
Note for desktop users : Use static IP only when you need it. Automatic IP saves you a lot of headache in handling network configuration.
Step 1: Get the name of network interface and the default gateway
The first thing you need to know is the name of the network interface for which you have to set up the static IP.
You can either use ip command or the network manager CLI like this:
In my case, it shows my Ethernet (wired) network is called enp0s25:
Next, you should note the default gateway IP using the Linux command ip route :
As you can guess, the default gateway is 192.168.31.1 for me.
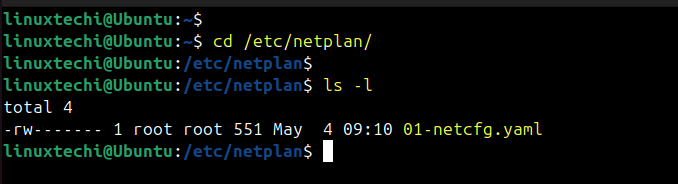
Step 2: Locate Netplan configuration
Ubuntu 18.04 LTS and later versions use Netplan for managing the network configuration. Netplan configuration are driven by .yaml files located in /etc/netplan directory.
By default, you should see a .yaml file named something like 01-network-manager-all.yaml, 50-cloud-init.yaml, 01-netcfg.yaml.
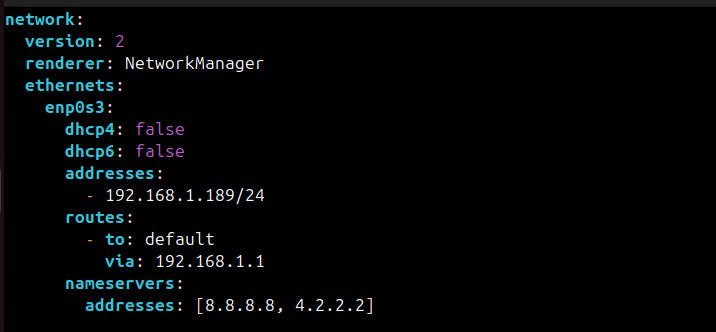
Whatever maybe the name, its content should look like this:
You need to edit this file for using static IP.
Step 3: Edit Netplan configuration for assigning static IP
Just for the sake of it, make a backup of your yaml file.
Please make sure to use the correct yaml file name in the commands from here onward.
Use nano editor with sudo to open the yaml file like this:
Please note that yaml files use spaces for indentation . If you use tab or incorrect indention, your changes won’t be saved.
You should edit the file and make it look like this by providing the actual details of your IP address, gateway, interface name etc.
In the above file, I have set the static IP to 192.168.31.16.
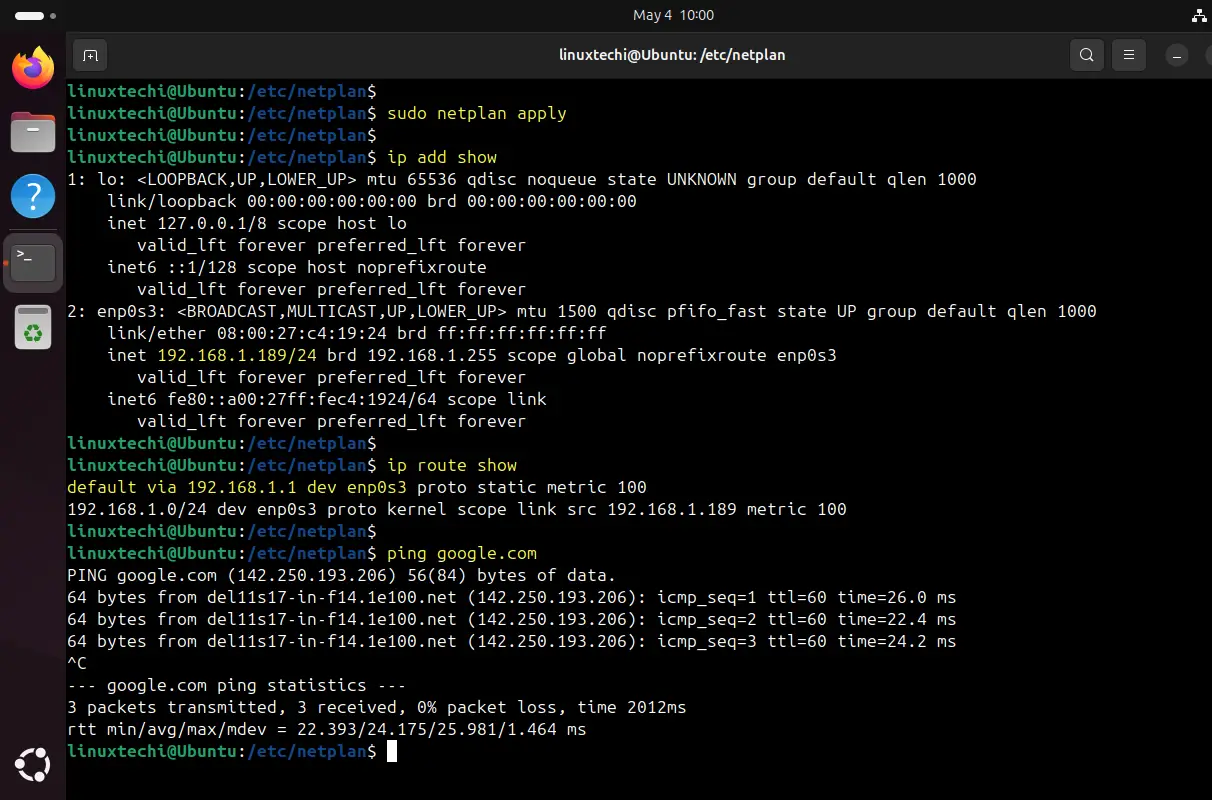
Save the file and apply the changes with this command:
You can verify it by displaying your ip address in the terminal with ‘ip a’ command.
If you don’t want to use the static IP address anymore, you can revert easily.
If you have backed up the original yaml file, you can delete the new one and use the backup one.
Otherwise, you can change the yaml file again and make it look like this:
Method 2: Switch to static IP address in Ubuntu graphically
If you are on desktop, using the graphical method is easier and faster.
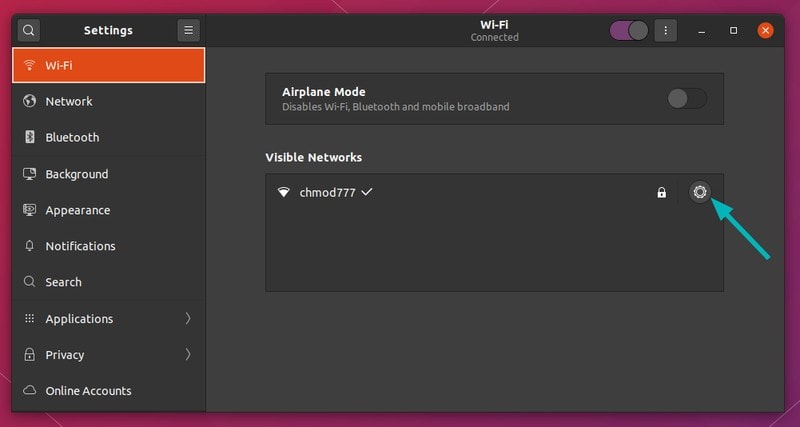
Go to the settings and look for network settings. Click the gear symbol adjacent to your network connection.
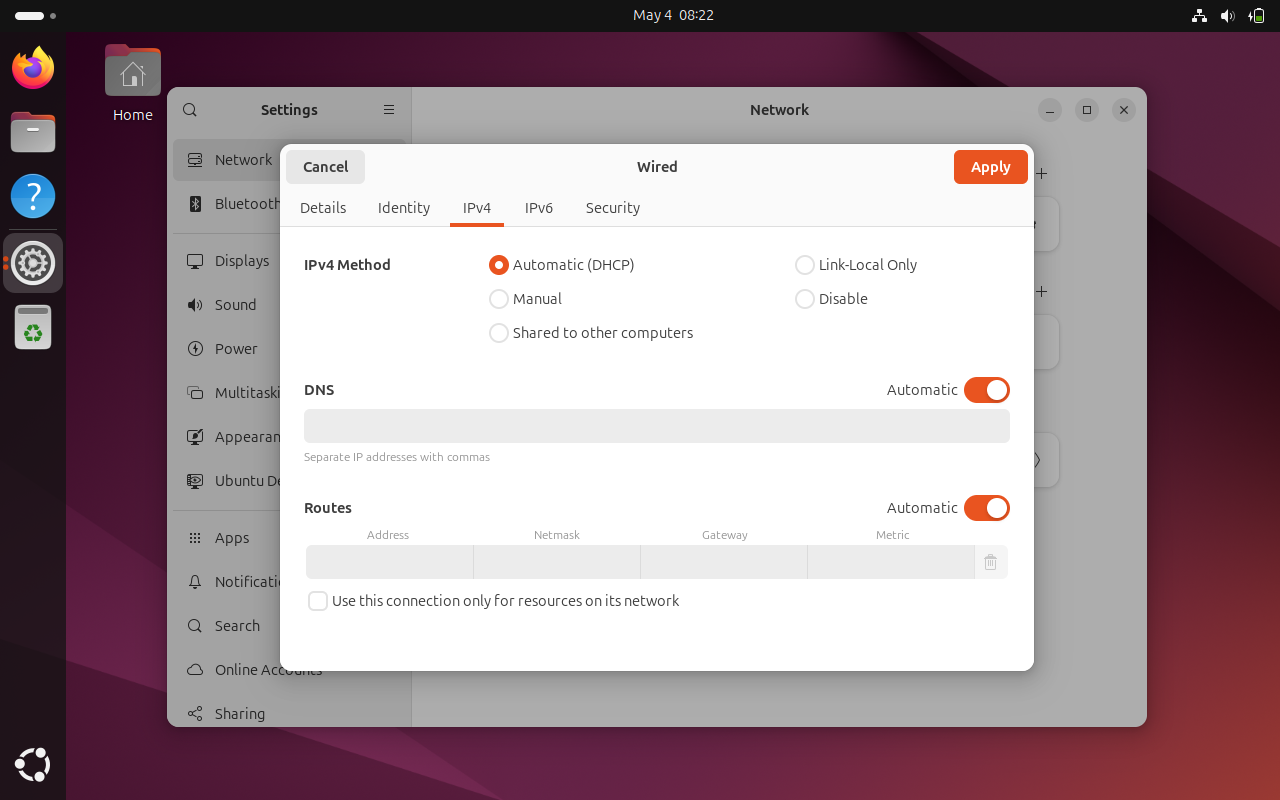
Next, you should go to the IPv4 tab. Under the IPv4 Method section, click on Manual.
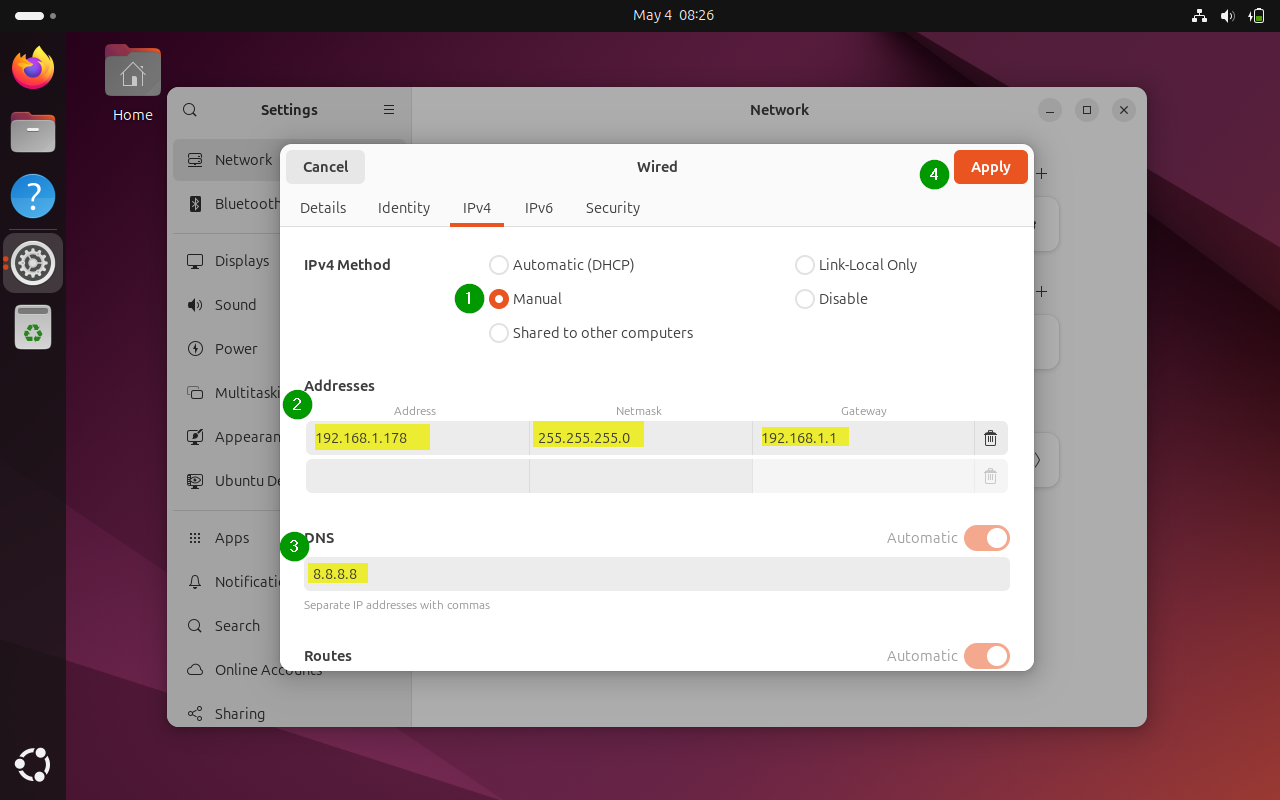
In the Addresses section, enter the IP static IP address you want, netmask is usually 24 and you already know your gateway IP with the ip route command.
You may also change the DNS server if you want. You can keep Routes section to Automatic.
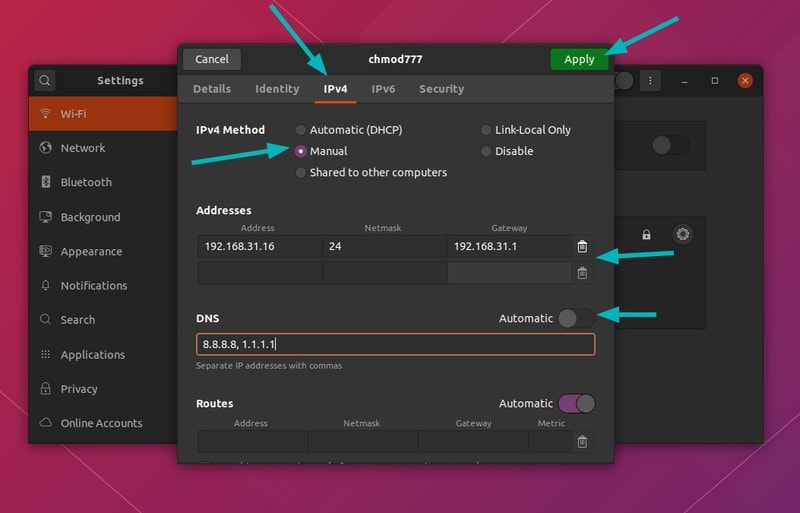
Once everything is done, click on Apply button. See, how easy it is to set a static IP address graphically.
If you haven’t read my previous article on how to change MAC Address , you may want to read in conjunction with this one.
More networking related articles will be rolling out, let me know your thoughts at the comments below and stay connected to our social media.
Dimitrios is an MSc Mechanical Engineer but a Linux enthusiast in heart. His machines are powered by Arch Linux but curiosity drives him to constantly test other distros. Challenge is part of his per
Meet DebianDog - Puppy sized Debian Linux
Reduce computer eye strain with this nifty tool in linux, install open source dj software mixxx version 2.0 in ubuntu, install adobe lightroom alternative rawtherapee in ubuntu linux, complete guide to installing linux on chromebook, become a better linux user.
With the FOSS Weekly Newsletter, you learn useful Linux tips, discover applications, explore new distros and stay updated with the latest from Linux world

Great! You’ve successfully signed up.
Welcome back! You've successfully signed in.
You've successfully subscribed to It's FOSS.
Your link has expired.
Success! Check your email for magic link to sign-in.
Success! Your billing info has been updated.
Your billing was not updated.
How-To Geek
How to set a static ip address in ubuntu.
When static is the way forward.
Quick Links
What is a static ip address, setting a static ip in ubuntu, set a static ip in ubuntu with the gui, connection convenience, key takeaways.
After gathering your connection name, subnet mask, and default gateway, you can set a static IP address in the terminal using the nmcli command. Or, in the GNOME desktop, open your connection settings and click the + icon, then enter the info for your static IP address there.
Your home network relies on IP addresses to route data between devices, and sometimes on reconnecting to the network a device's address can change. Here's how to give an Ubuntu Linux computer a permanent IP address that survives reboots.
Everything on your network home network, whether it's using a wired connection or Wi-Fi, has an IP address . IP stands for Internet Protocol. An IP address is a sequence of four numbers separated by three dots. Each IP address that is unique within that network.
IP addresses act as numeric labels. Your router uses these labels to send data between the correct devices. Usually, your router assigns IP addresses. It knows which IP addresses are in use and which are free. When a new device connects to the network, it requests an IP address and the router allocates one of the unused IP addresses. This is called DHCP, or dynamic host configuration protocol .
When a device is restarted or powered off and on, it may receive its old IP address once more, or it might be allocated a new IP address. This is normal for DHCP and it doesn't affect the normal running of your network. But if you have a server or some other computer that you need to be able to reach by its IP address, you'll run into problems if its IP address doesn't survive power downs or reboots.
Pinning a specific IP address to a computer is called allocating a static IP address . A static IP address, as its name suggests, isn't dynamic and it doesn't change even if the computer is power-cycled .
Nmcli is the command-line network manager tool , and can be used to change your IP address, configure network devices, and --- relevant to our purposes --- set up a static IP in Ubuntu.
We're demonstrating this technique on Ubuntu 22.04 LTS, but it ought to work on any Linux distribution, including Ubuntu 23.04. The nmcli tool was released in 2004, so it should be present on just about any standard distribution.
Let's take a look at the network connections that already exist on the computer. We're using the connection command with the show argument.
nmcli connection show
This displays some information about each connection. We only have a single connection configured.
The output is wider than the terminal window. This is the information that we're shown.
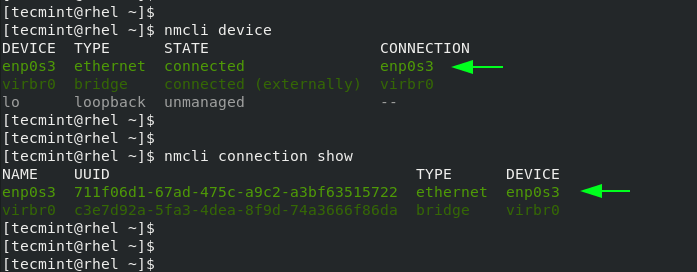
- Name : Our network connection is called "netplan-enp0s3."
- UUID : The universally unique identifier Linux uses to reference this connection internally.
- Type : This is an ethernet connection.
- Device : This connection is using the "enp0s3" network interface. It's the only network card in this computer.
We can use the ip command to discover the IP address this computer is using.
In the output we can see the "enp0s3" entry, and its current IP address, 192.168.86.117. The "/24" is a shorthand way of saying that this network uses a 255.255.255.0 subnet mask . Take a note of this number, we'll need to use it later.
We need to choose the IP address we're going to set as our static IP address. Obviously, you can't use an IP address that is already in use by another device. One safe way to proceed is to use the current IP address assigned to the Ubuntu system. We know for certain that nothing else is using that IP address.
If we want to use a different IP address, try pinging it. We're going to test whether IP address 192.168.86.128 is in use. If everything else on your network uses DHCP and you get no response to the ping command, it should be safe to use.
ping 192.168.86.128
Even if another device had previously used that IP address, it'll be given a new IP address when it next boots up. Nothing responds to the ping requests, so we're clear to go ahead and configure 192.168.86.128 as our new static IP.
We also need to know the IP address of your default gateway , which will usually be your broadband router. We can find this using the ip command and the route option, which we can abbreviate to "r."
The entry that starts with "default" is the route to the default gateway. Its IP address is 192.168.86.1. Now we can start to issue commands to set up our static IP address.
The first command is a long one.
sudo nmcli con add con-name "static-ip" ifname enp0s3 type ethernet ip4 192.168.86.128/24 gw4 192.168.86.1
Taken in small chunks, it's not as bad as it looks. We're using sudo . The nmcli arguments are:
- con : Short for "connection."
- add : We're going to add a connection.
- con-name "static-ip" : The name of our new connection will be "static-ip."
- ifname enp0s3 : The connection will use network interface "enp0s3."
- type ethernet : We're creating an ethernet connection.
- ip4 192.168.86.128/24 : The IP address and subnet mask in classless inter-domain routing notation . This is where you need to use the number you took note of earlier.
- gw4 192.168.86.1 : The IP address of the gateway we want this connection to use.
To make our connection a functioning connection, we need to provide a few more details. Our connection exists now, so we're not adding anything, we're modifying settings, so we use the mod argument. The setting we're changing is the IPv4 DNS settings. 8.8.8.8 is the IP address of Google's primary public DNS server , and 8.8.4.4 is Google's fallback DNS server.
Note that there is a "v" in "ipv4." In the previous command the syntax was "ip4" without a "v." The "v" needs to be used when you're modifying settings, but not when adding connections.
nmcli con mod "static-ip" ipv4.dns "8.8.8.8,8.8.4.4"
To make our IP address static, we need to change the method which the IP address obtains its value. The default is "auto" which is the setting for DHCP. We need to set it to "manual."
nmcli con mod "static-ip" ipv4.method manual
And now we can start or "bring up" our new connection.
nmcli con up "static-ip" ifname enp0s3
We didn't get any error messages which is great. Lets use nmcli to look at our connections once more.
nmcli con show
Here's the output:
Our static-ip connection is active and using device "enp0s3." The existing connection "netplan-enp0s3" is no longer associated with a physical network interface because we've pinched "enp0s3" from it.
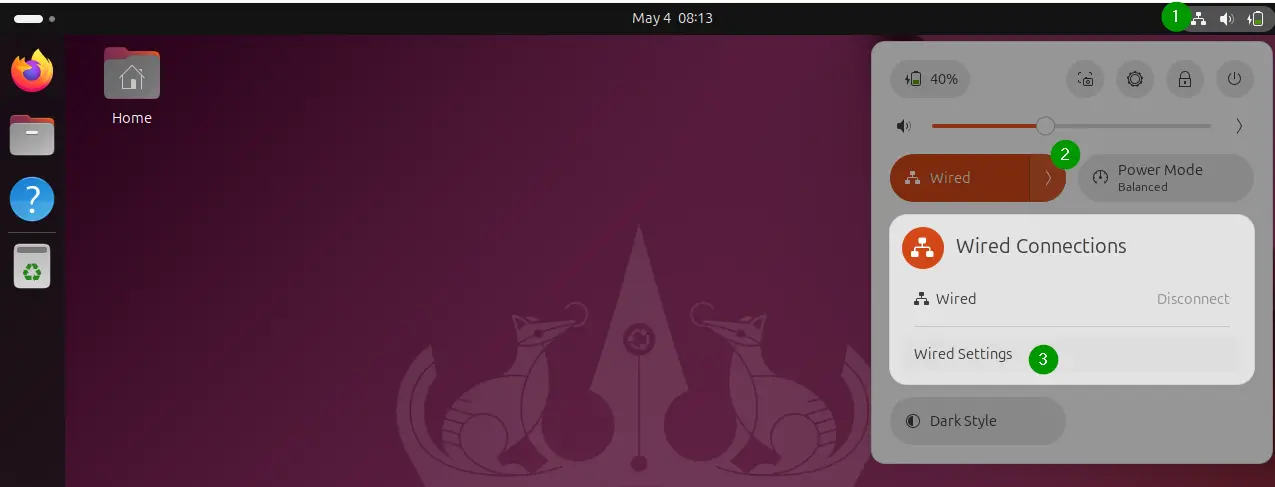
Click the icons at the far-right end of the system bar to show the system menu, then click on the "Wired Connected" menu option. If you're using a wireless connection, instead click the name of your Wi-Fi network.
The available connections are displayed. A dot indicates which is in use. Click the "Wired Settings" or "Wi-Fi Settings" menu option. The details of the active connection are displayed.
If you followed our previous instructions the new connection will be the active connection. We can see our new "static-ip" connection has the IP address, default gateway, and DNS servers that we set for it.
To create a new connection using the "Settings" application, click the " + " icon on the "Networks" page, above the list of wired connections.
A dialog appears. We need to provide a name for our new static IP connection.
We're calling our new connection "static-2." Click the "IPv4" tab.
Select the "Manual" radio button, and complete the "Address", "Netmask", and "Gateway" fields. Also complete the DNS field, and then click the green "Apply" button. Note the comma between the DNS entries.
Our new connection is listed in the "Wired" connections pane.
You can swap between the available connections by clicking directly on their names.
If you want to modify a connection after you create it, click the cog icon. In this case, we'll enter the settings for the "static-ip" connection.
A dialog box opens. Click on the "IPv4" tab.
Because we set our new IP address to be static, the "Manual" radio button is selected. You could change this back to DHCP by selecting the "Automatic (DHCP)" radio button, and clicking the green "Apply" button.
Using the nmcli command or the GNOME desktop and apps, you can hop between network connections very easily and very quickly.
It's more convenient to have a selection of connection profiles and move between them as you need to, rather than to have one that you keep editing. If something goes horribly wrong with the connection you're editing or adding, you can always fall back on one of the existing connections.

A Beginner’s Guide to Configuring IPv4 and IPv6 Addresses in Linux
As a systems administrator, you will occasionally be tasked with configuring or setting up the IP addresses of your servers to keep up with changing network requirements. As such, having fundamental skills in assigning IP addresses and configuring hostname resolution is crucial in ensuring that servers conform with the network topology.
Table of Contents
What is an IP Address?
An IP address, which stands for Internet Protocol , is a unique numerical identifier or address that identifies a device in a TCP/IP network. This could be a local area network ( LAN ) or the internet.
The IP address allows communication between devices in a network such as servers, routers, switches, and any other network device connected to the network.
Difference Between IPv4 vs IPv6
An IP address can be broadly categorized into two: IPv4 and IPv6 .
IPv4 Address
An IPv4 (IP version 4) address is a 32-bit number that is split into four octets, with each octet separated by a period or a decimal point. This is usually referred to as dotted-decimal format.
Each octet is made up of 8 bits which collectively represent a byte. An IPv4 address can further be divided into two sections. The first part represents the network section, while the remaining part defines the host section.
Network Section
The network section of an IP address identifies the class the IP address belongs. There are 3 distinct classes of IP addresses used in computer networks: Class A , Class B , and Class C .
What is IPv4 Class A
In Class A type of network, the first 8 bits (octet) define the network, while the remaining 24 bits are reserved for the hosts in the network.
- The Public IP addresses range from 1.0.0.0 to 127.0.0.0.
- The Private IP addresses range from 10.0.0.0 to 10.255.255.255.
Addresses 127.0.0.0 to 127.255.255.255 are reserved for loopback and other diagnostic purposes, and hence are not allocated to hosts in a network.
The default subnet mask of class A is 255.0.0.0 with the first 8 bits used to identify the network. The remaining 24 bits are designated for hosts. This class is used in networks that command a large number of hosts. It yields a maximum of 16,777,214 hosts and 126 networks.
What is IPv4 Class B
In Class B , the first two octets, or 16 bits are used to define the network ID.
- The Public IP addresses range from 128.0.0.0 to 191.255.0.0.
- The private IP range is from 172.16.0.0 to 172.31.255.255.
The default subnet mask is 255.255.0.0 where the first 16 bits define the network ID. This class of IP is typically used for medium-large networks and yields 65,534 hosts per network with a total of 16,382 networks.
What is IPv4 Class C
This class of IP is mostly used for small networks such as a home network or a small office or business.
In a Class C network, the first two network bits are set to 1 while the third is set to 0, i.e. 1 1 0. The remaining 21 bits of the first three octets define the network ID, and the last octet defines the number of hosts.
As such, Class C IP address produces the highest number of networks amounting to 2,097,150 , and the least number of hosts per network which is 254 hosts.
- The public IP addresses range from 192.0.0.0 to 223.255.255.0.
- The private IP range is from 192.168.0.0 to 192.168.255.255.
The subnet mast is 255.255.255.0.
Host Portion
The remaining section of the IP address is the host portion, which is the section that determines the number of hosts in a network. This part uniquely identifies a host in a network. All hosts in the same network share the same network portion.
For example, the following host IP addresses belong to the same network.
IPv6 Address
An IPv6 address is an alphanumeric address that is 128 bits long, arranged in eight groups, each of which contains 16 bits.
Like an IPv4 address, it is split into two parts: the network and host component. The network part makes up the first 64 bits and is used for routing purposes. The remaining 64 bits identified the address on the nodes.
Below is an example of a full IPv6 address.
This can be further shortened as follows.
IPv6 was developed as a solution to the imminent exhaustion of addresses in IPv4. As you know by now, IPv6 contains 128 bits which is four times more than the number of bits in IPv4 (32 bits). These extra bits provide more addressing space which will supplement the address provided by IPV4.
Although IPv6 is set to take over from IPv4 addressing in the near future, many organizations and ISPs still use and largely rely on IPv4 addresses.
In fact, you’ll hardly ever need to configure an IPv6 on your device to provide connectivity. The fact is, it will take a while before IPv6 replaces or phases out IPv4.
Dynamic (DHCP) and Static IP Configuration
IP allocation on client machines or any end-point devices connected to a network is done either using the DHCP protocol or manual configuration where IP addresses are statically allocated.
DHCP IP Address
DHCP ( Dynamic Host Configuration Protocol ) is a client-server protocol that dynamically allocates IP addresses to client systems on a network. The DHCP server, which in most cases is a router, contains a pool of addresses that it leases out to client devices on a network for a certain period of time. Thus, it simplifies and makes the configuration of IP addresses more efficient. Once the lease time lapses, the client acquires a new IP address.
Most systems, by default, are configured to obtain an IP automatically using the DHCP protocol. This eliminates the possibility of IP conflicts in a network where two devices share the same IP address.
The drawback of DHCP is that the IP addresses change once the lease expires. If a server is set to acquire an IP via DHCP, this will lead to connectivity issues once the IP address changes. And this is where static IP configuration comes in.
Static IP Address
In static IP configuration, IP addresses are manually configured on a client system, especially servers. Unlike dynamically allocated addresses, statically configured IP addresses remain the same and do not change.
However, the static configuration requires a lot of work from network admins. They have to manually log in and configure the static IP along with other details such as subnet mask, DNS servers, and gateway IP. In addition, they need to keep track of all the client systems with static IP addresses.
In this tutorial, we will focus on how to statically configure IP addresses on various systems.
How to Configure IPv4 Networking in Linux
In this section, we will shift focus and see how to configure an IPv4 address on Linux. We will look at how you can do this on Debian , Ubuntu , and later on RHEL and Red Hat distributions .
Configure IPv4 Address on Debian
To get started, it’s always a good idea to check your current IP configuration of the Linux system.
This displays the IP addresses and status of your network interfaces. From the output, we have two interfaces.

The first one is the lo interface which is a loopback address reserved for testing purposes only and is always designated the address 127.0.0.1 . The loopback address is not associated with any physical network interface.
The second interface is enp0s3 (this might be different in your case). This is the active network interface that maps to the physical network card on the server.
Its IPv4 address is denoted by the inet parameter, and in this case is 192.168.2.113 , which is assigned via the DHCP protocol.
In Debian, the network configuration is contained in the /etc/network/interfaces file. You can view it using the nano or vim editor .
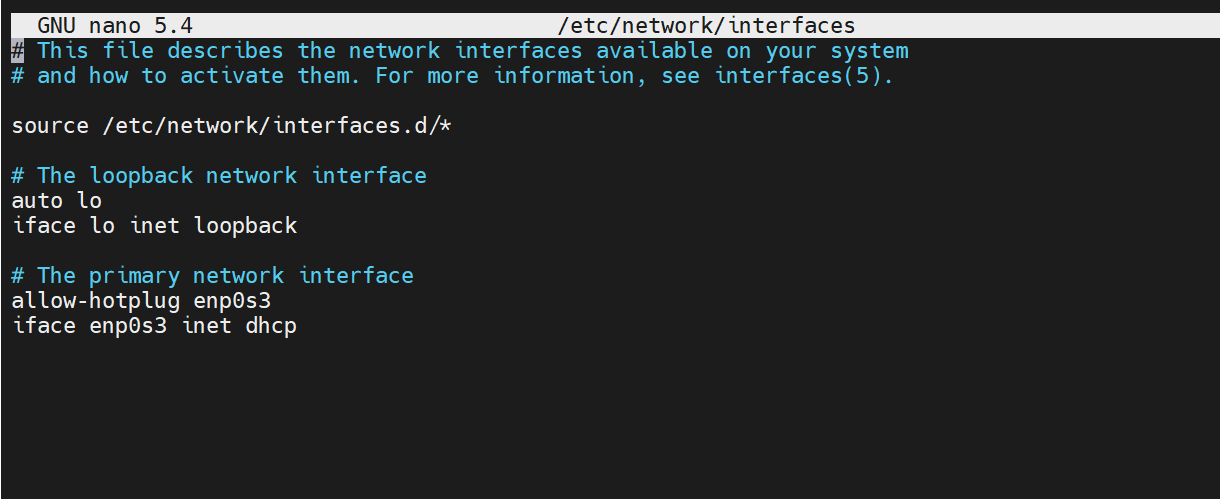
To configure a static IPv4 address, remove or comment the allow-hotplug and dhcp lines, Then add the following configuration.
In this configuration, 192.168.2.150 will be our new IPv4 address with a netmask or network subnet of 255.255.255.0. The default gateway, which also happens to be the router’s IP, is 192.168.2.1 while the DNS nameservers are 192.168.2.1 and 8.8.8.8 .
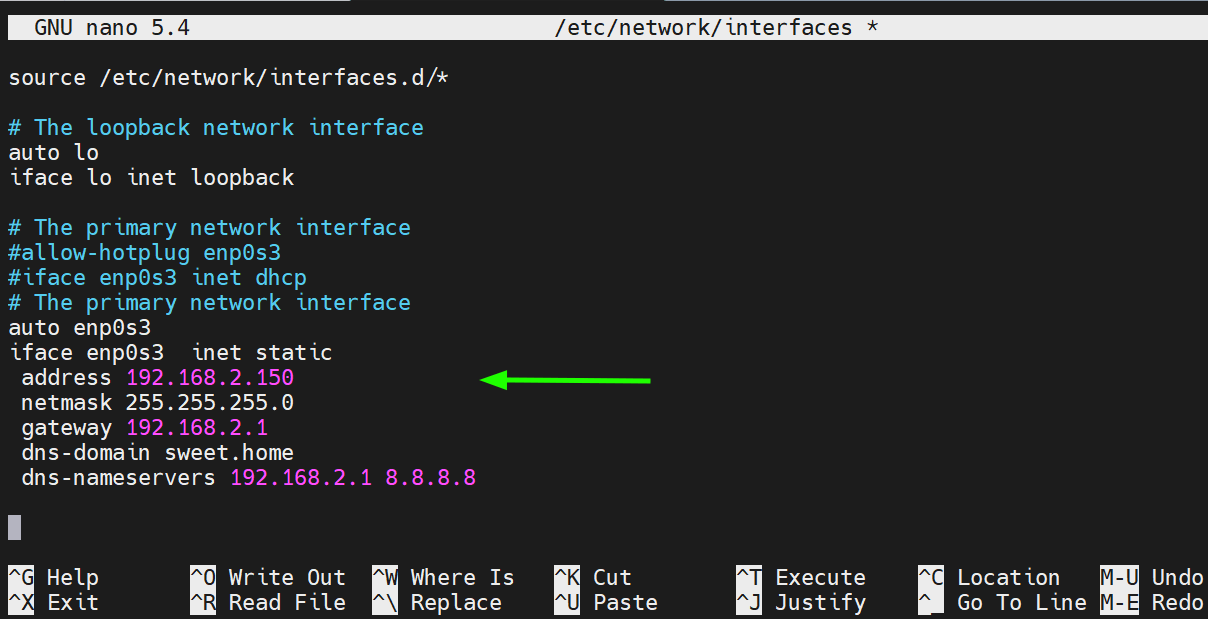
Save the changes and exit the file.
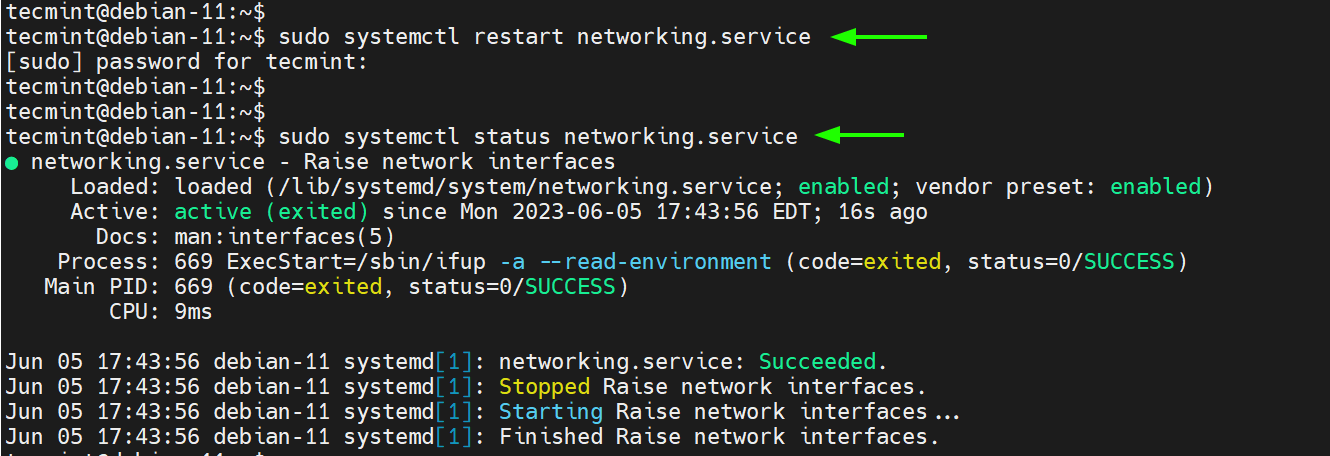
To apply the changes, restart the networking service.
Then confirm no errors were encountered
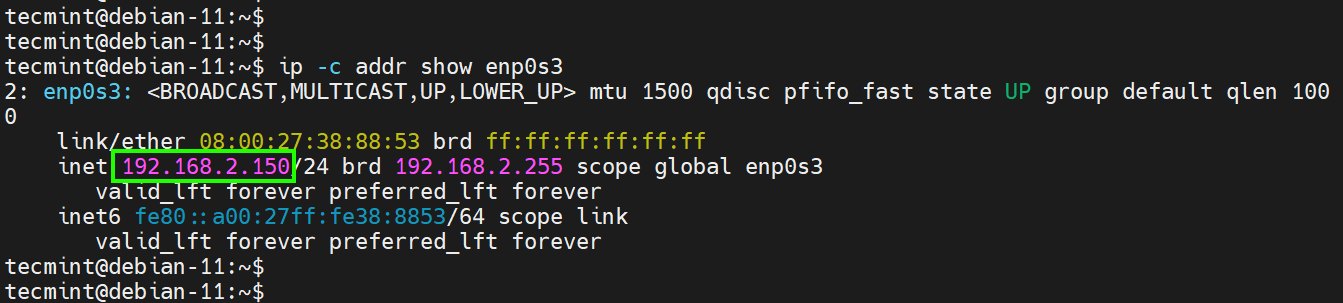
To confirm that the server has acquired the new IP, run the following command:
The output below confirms that we have successfully configured the static IPv4 address.
Configure IPv4 Address on Ubuntu
In Ubuntu 18.04 and later versions, Netplan is the default network configuration tool, which enables easy configuration of network settings via YAML files. According to Canonical, netplan processes the YAML files and generates network configurations for systemd-network or NetworkManager .
The network configuration file for modern Ubuntu distributions is located in the /etc/netplan directory. For the desktop system, the configuration file in this directory is 01-network-manager-all.yaml . For servers, the file is /etc/netplan/01-netcfg.yaml .
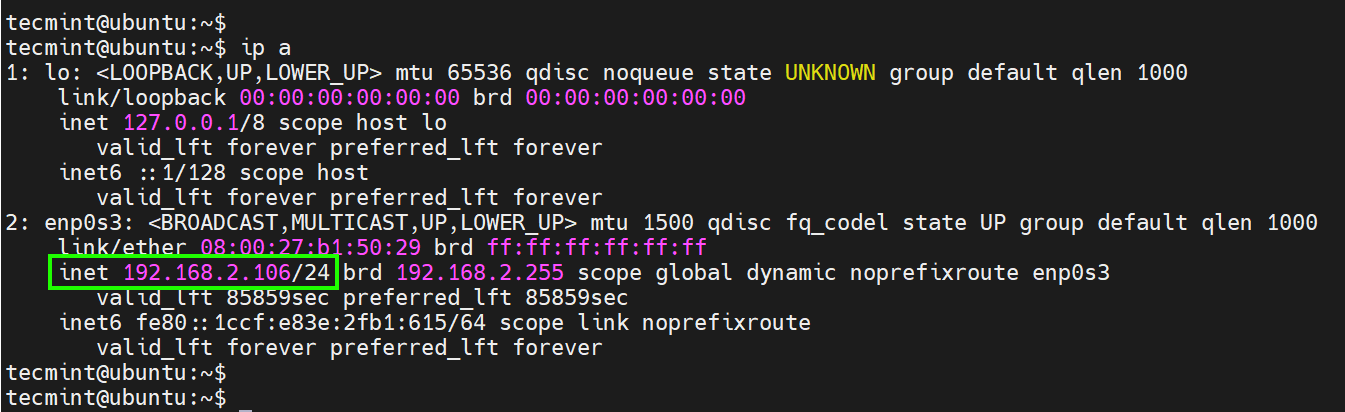
Once again, let’s check our current IP address which is auto-assigned by DHCP.
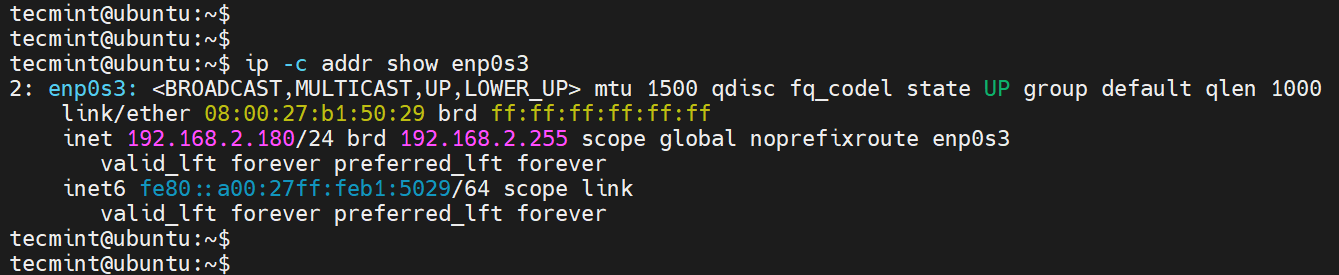
Our current IP is 192.168.2.106 . We will set this to 192.168.2.180 .
To assign an IPv4 address, we will open the network configuration file.
By default, the following lines automatically set the system to use DHCP for IP assignment.
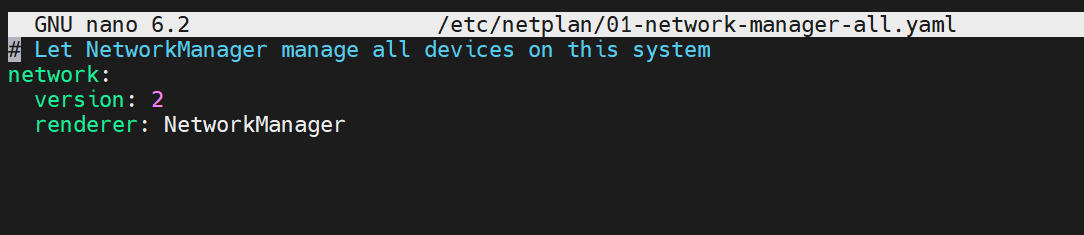
Add the following lines to assign a static IP.
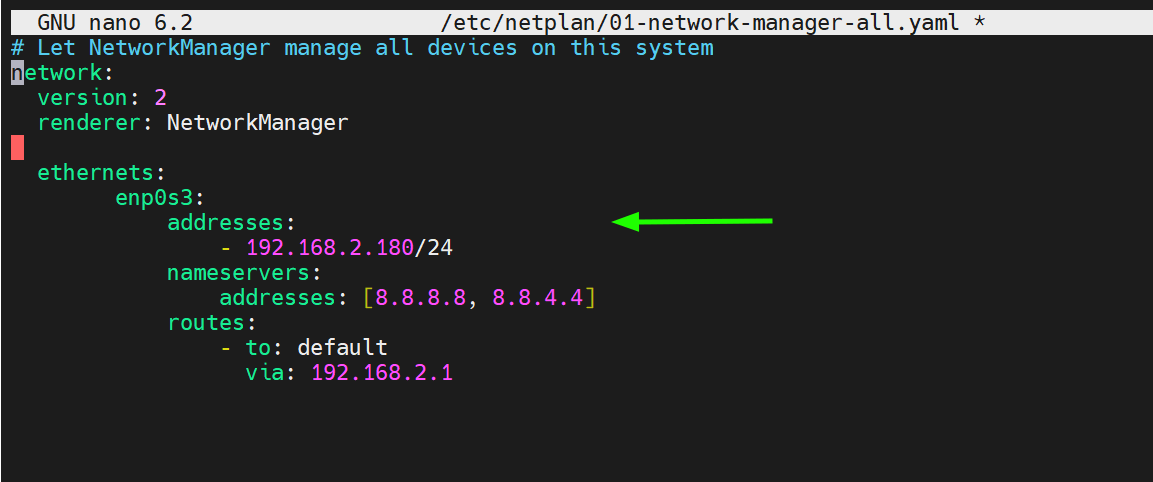
Let us break down the parameters used:
- enp0s3 – is the name of the network interface.
- addresses – This configures the IPv4 address on the interface. This is followed by the CIDR, in this case,/24 which implies a network subnet of 255.255.255.0.
- nameservers – This specifies the DNS servers to be used. In this case, we are using 8.8.8.8 and 8.8.4.4 which are Google’s name servers.
- routes – This sets the gateway on your system.
Remember to replace the interface name and IP configuration to match your network environment.
Save the changes and exit.
To apply the changes made, run the following command:
Once again, verify if the changes have been reflected as shown.
Configure IPv4 Address on RHEL
In Red Hat distributions , the nmcli (NetworkManager Command Line Interface) command-line tool is one of the most preferred ways of configuring an IPv4 address. It does so using the NetworkManager service.
To view the network interface name attached to your system, execute the command:
To display the active connection, run the command:
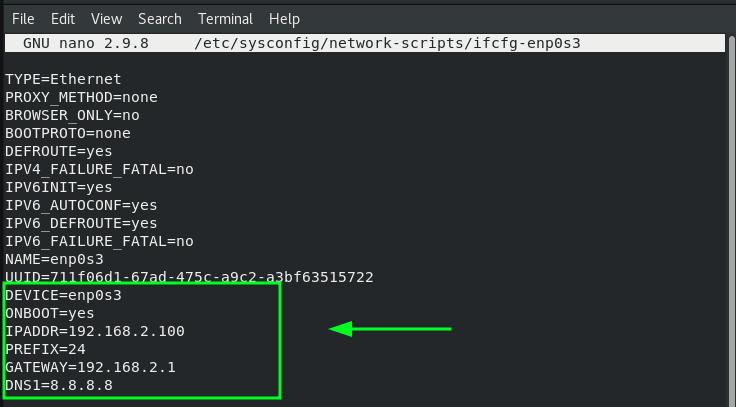
In RHEL 9 and other Red Hat distributions based on RHEL, the network configuration file resides in the /etc/sysconfig/network-scripts directory. In our case, the configuration file is ifcfg-enp0s3 .
We will assign a static IPv4 address on the interface ‘ enp0s3 ‘ as shown:
To do so, we will run the following commands:
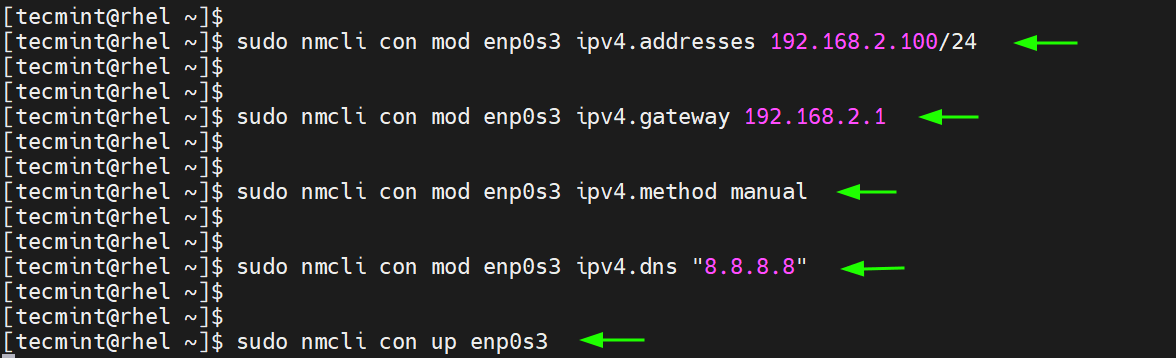
The commands save the changes inside the associated network configuration file. You can view the file using your preferred text editor
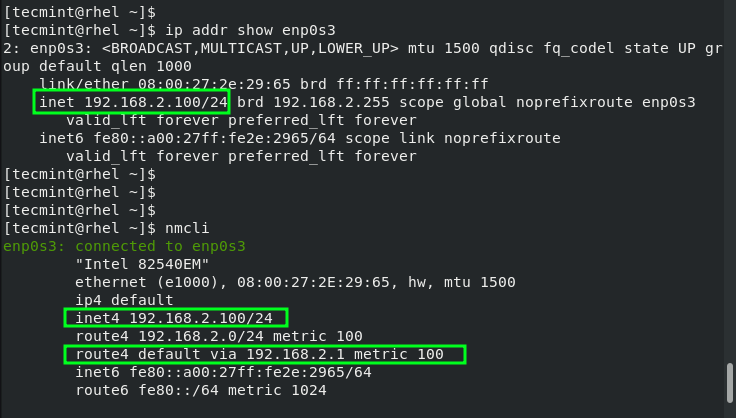
To confirm the new IP address, run the following command
You can also run the nmcli command without any command-line options and the active interface will be displayed at the top.
How to Configure Hostname in Linux
A well-configured system should be able to resolve its hostname or domain name to the IP address configured. Usually, the hostname and IP address mapping is done in the /etc/hosts file.
To configure hostname resolution, add a host’s entry to the /etc/hosts file. This entry includes the host’s IP address and the hostname as shown.
Be sure to update the /etc/hosts file on every Linux system that you intend to connect to the system on the same local network.
Once done, you can successfully ping the hostname of the Linux machine.
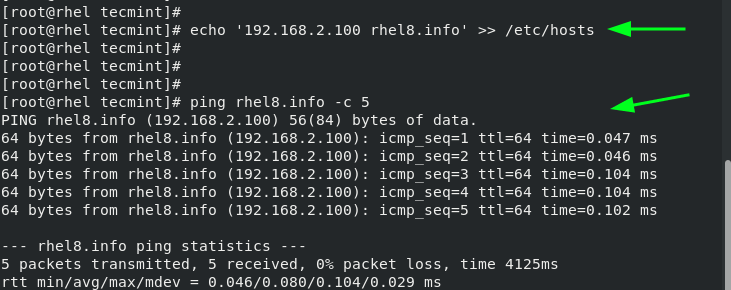
In this tutorial, we have covered IPv4 and IPv6 IP addresses and explored how you can configure IPv4 networking and hostname resolution on Linux.
Previous article:
Next article:
Each tutorial at TecMint is created by a team of experienced Linux system administrators so that it meets our high-quality standards.
Related Posts
Tasksel – Quickly Install Software Groups in Debian and Ubuntu

How to Install KDE Plasma in Ubuntu, Debian and Mint
How to Install ImageMagick 7 on Debian and Ubuntu

How to Install Postfix with Roundcube Webmail on Ubuntu and Debian

How to Install Wine on Debian, Ubuntu and Linux Mint
How to Install and Compile Kernel in Debian
Ah, it is working like this:
I only have to put into an init script.
I face the following situation: The Internet provider has switched to IPv6.
This means the first 4 blocks, e.g., a02:560:4c19:cd00……. are changing time by time.
The Internet router is able to configure “port forwarding” for IPv6. Indeed, it is not port forwarding, but routing to an IPv6 address in my network.
Unfortunately, the Internet router is not able to route the dynamic part of the IPv6 address of my internal server. I can only configure a fix postfix of the IPv6 address:
let it be: …….. 2001:db8:1234:abcd
While the prefix is changing by the internet provider, the postfix I set it to fix.
To make a service from my internal address available to the internet, I must configure the IPv6 address of my server with the dynamic prefix of the router and the fix postfix configured for routing.
Is it possible to configure it?
Clear, it is a bug in my internet router.
Another way, maybe I will try at the weekend, while the server is getting up, I can call via IPv4 DNS to get the current IPv6 address, put it into the configuration, and restart the network stack.
Title says “Configuring IPv4 and IPv6 Addresses”.
What happened to the “ configure IPv6 section ?”
The pool of IPv4 addresses has already been exhausted so we will have to use IPv6 from now on. I may “hardly ever need to configure an IPv6” but, nevertheless, there WILL be times that I will have to configure IPv6.
It would be handy to know how to do the configuration ahead of time unless IPv6 is self-configuring.
@Dragonmouth,
To assign an IPv6 address temporarily to the network interface, run the following command:
Replace <IPv6_ADDRESS> with the desired IPv6 address, <PREFIX_LENGTH> with the appropriate prefix length and <INTERFACE_NAME> should be replaced with the actual interface name.
For example:
To assign an IPv6 address permanently to the network interface, use the following instructions:
1. Open the configuration file for the desired network interface.
The file name will usually be in the format ifcfg-<INTERFACE_NAME> . For example, if the interface name is eth0 , the file would be ifcfg-eth0 .
Add the following lines to the configuration file.
Restart the network service to apply the changes.
You can confirm your IP address by running ip command.
How to configure IPv6 static IP address using Netplan?
To configure an IPv6 address using Netplan, you can follow these steps:
1. Open the Netplan configuration file using a text editor.
Add the following network configuration to configure an IPv6 address.
In the above example, the interface eth0 is configured with the static IPv6 address 2001:db8:1234:abcd::1 with a prefix length of /64 . The IPv6 gateway is set to 2001:db8:1234:abcd::a .
2. Apply the changes by running the following command:
Thank you, it may help users with old Ubuntu versions.
In newer versions, gateway6 is deprecated.
I don’t think the gateway6 parameter is deprecated in the netplan configuration. Any source you have please share…
Got Something to Say? Join the Discussion... Cancel reply
Thank you for taking the time to share your thoughts with us. We appreciate your decision to leave a comment and value your contribution to the discussion. It's important to note that we moderate all comments in accordance with our comment policy to ensure a respectful and constructive conversation.
Rest assured that your email address will remain private and will not be published or shared with anyone. We prioritize the privacy and security of our users.
Save my name, email, and website in this browser for the next time I comment.
16 Linux ip command examples to configure network interfaces (cheatsheet)
November 18, 2022
The ip is a very powerful utility that is used to perform many tasks. Multiple older utilities such as ifconfig and route command were earlier used to perform these functions. In this article I will share different examples to configure network interfaces and routes using ip command .
Install iproute rpm
By default iproute rpm is installed on all variants of RHEL/CentOS Linux , you can also find ip binary command in the rescue and emergency target.
The absolute path is /usr/sbin/ip
1. Show IP Address of all the available interfaces using ip command
Use ip addr show to show the IP Address of all the available network interfaces on your Linux system
Here I have three interfaces (including the loopback interface), wherein we can check the IP Address of individual interface as highlighted above.
2. Show IP Address of individual interface
You can use " dev " argument along with " ip addr show " to display information of provided interface only. Here we are displaying IP Address detail for enp0s9 interface only.
3. List interfaces based on interface type
There are various types of NIC which can be available on your Linux system such as vlan , bond, bridge, vxlan etc.
Now to list only bridge interfaces on your system:
To list bond interface from your system
4. Check if NIC's link state is enabled or disabled
" ip link " will manage and display the state of all network interfaces. To display the current state of all the interfaces
To check the link state of individual interface
5. Change NIC's Link state
Since our NIC interface is already in enabled state, let us turn down link state for enp0s9 interface
Check the link state again for enp0s9
Now since it is in DOWN state, let us change the link status for enp0s9 to UP
6. Assign/Add IPv4 and IPv6 address
To assign ipv4 address using you can use " ip addr add ". To demo this step I have already temporarily unassigned/removed IP address from enp0s9 interface.
To assign IPv4 address using ip command you would need netmask prefix value which here for me is "24". You can either calculate this prefix value or you can use other online network calculators which can help you get the prefix value depending upon your netmask.
To check the assigned IPv4 Address for enp0s9 interface
To assign IPv6 address using ip command you can use the same command as used for IPv4 address but with the IPv6 address and netmask
Verify the IPv6 address assigned to the provided interface
7. Un-Assign/Delete IPv4 and IPv6 address
You can un-assign or delete an assigned ip address from an interface using " ip addr del " argument. Here you must give the exact IP address along with the prefix value to un-assign the ip address.
Check and verify if the ip address was un-assigned sucessfully from the provided interface
You can un-assign or delete the IPv6 address for individual interface using the same command as used for IPv4 address above.
Next check the IPv6 Address of the interface to make sure it is un-assigned from the provided interface
8. Un-assign/delete all protocol addresses from individual interface
By using " ip addr del " we only remove the provided address assigned to the respective interface. But if you wish to remove all the protocol address assigned to individual interface then you must use flush
Next check the interface detail
As you see both IPv4 and IPv6 addresses are removed.
9. Display detailed statistics of interface
To get more detailed information on packet statistics for individual interface using " -s " argument
If the "-s" option appears twice or more, the amount of information increases.
10. List available routes
To list all the available routes on your Linux system
You can also use " ip route " or " ip route show " to get the list of available routes in the routing table
11. Add default route to routing table
To add default route (adding an entry in the routing table) use " ip route add default "
Verify the available default routes in the routing table
To add more details for the default route as we have for other routes
Verify the default route again using ip command
12. Delete default route from routing table
To delete the default route, instead of using " add ", use " delete ". Now here I have two default routes, where I wish to delete the route with 10.0.2.2 for enp0s3 interface
Delete the default route
Verify the available routes in the routing table
You can also remove the default route using interface name to delete all the default routes mapped to provided interface
13. Add additional route to the routing table
Now after adding default route, you can also add additional routes to the routing table. Here we will add a route to 192.168.168.0/24 via the route 192.168.0.1
14. Delete additional route from routing table
Here we had added a new route for 192.168.168.0/24 via 192.168.0.1 . so we will attempt to delete the same here
Verify the route list again
15. Replace existing routes from routing table
We can also replace certain directives from existing routes in the routing table. In our last example we added route 192.168.168.0/24 via 192.168.0.1 so we will change this to 192.168.168.0/24 via 10.0.2.2 gateway via a different interface (enp0s3)
My existing list of routes
Replace the route values
Verify the new route list
16. Display the route an address will take
Now we have added all the routes, but we would like to know the route which any address on the linux system will take
To know the route which will be used by 192.168.168.10 address
To know the route which will be used by 192.168.0.10 address
Linux ip command is a very handy tool for Linux Administrators. The only drawback with this tool is that the changes are non-persistent which means this will not survive a reboot. But in many cases such as in rescue mode or to verify temporary network changes we can use this tool to create and assign network to interfaces.
Lastly I hope this article with different ip command examples to perform network related activities (cheatsheet) on Linux was helpful. So, let me know your suggestions and feedback using the comment section.
I have used below external references for this tutorial guide man page for ip command

Deepak Prasad
He is the founder of GoLinuxCloud and brings over a decade of expertise in Linux, Python, Go, Laravel, DevOps, Kubernetes, Git, Shell scripting, OpenShift, AWS, Networking, and Security. With extensive experience, he excels in various domains, from development to DevOps, Networking, and Security, ensuring robust and efficient solutions for diverse projects. You can connect with him on his LinkedIn profile.
Can't find what you're searching for? Let us assist you.
Enter your query below, and we'll provide instant results tailored to your needs.
If my articles on GoLinuxCloud has helped you, kindly consider buying me a coffee as a token of appreciation.

For any other feedbacks or questions you can send mail to [email protected]
Thank You for your support!!
Leave a Comment Cancel reply
Save my name and email in this browser for the next time I comment.
Notify me via e-mail if anyone answers my comment.
We try to offer easy-to-follow guides and tips on various topics such as Linux, Cloud Computing, Programming Languages, Ethical Hacking and much more.
Recent Comments
Popular posts, 7 tools to detect memory leaks with examples, 100+ linux commands cheat sheet & examples, tutorial: beginners guide on linux memory management, top 15 tools to monitor disk io performance with examples, overview on different disk types and disk interface types, 6 ssh authentication methods to secure connection (sshd_config), how to check security updates list & perform linux patch management rhel 6/7/8, 8 ways to prevent brute force ssh attacks in linux (centos/rhel 7).
Privacy Policy
HTML Sitemap
Select Your Language
- Single-page
Language and Page Formatting Options
Red hat training.
A Red Hat training course is available for Red Hat Enterprise Linux
3.6. Configuring IP Networking with ip Commands
Assigning a static address using ip commands, configuring multiple addresses using ip commands, quick links.
- Subscriptions
- Support Cases
- Customer Service
- Product Documentation
- Contact Customer Portal
- Customer Portal FAQ
- Log-in Assistance
- Trust Red Hat
- Browser Support Policy
- Accessibility
- Awards and Recognition
Related Sites
- developers.redhat.com
- connect.redhat.com
- cloud.redhat.com
Systems Status
- Red Hat Subscription Value
- About Red Hat
- Red Hat Jobs
Red Hat legal and privacy links
- Contact Red Hat
- Red Hat Blog
- Diversity, equity, and inclusion
- Cool Stuff Store
- Red Hat Summit
- Privacy statement
- Terms of use
- All policies and guidelines
- Digital accessibility
Set static IP in Ubuntu using Terminal
Everything you need to know about setting static IP on an Ubuntu machine using the command line.
Dec 5, 2022 — Pratham Patel
Normally, the router's DHCP server handles assigning the IP address to every device on the network, including your computer.
The DHCP server may also give you a new IP address occasionally. This could cause a problem if you have a home lab or server setup that works on a fixed IP address.
You need to set a static IP address on your Ubuntu system to avoid problems.
Step 1: Identify the correct network interface
The first step is always to know the name of your network interface.
"But why?" you might ask. That is because since Ubuntu 20.04, the network interfaces are named using predictable network interface names . This means your one and only ethernet interface will not be named 'eth0'.
Ubuntu Server and Ubuntu Desktop use different renderers for 'netplan', they are 'systemd-networkd' and 'NetworkManager', respectively. So let's go over their differences.
Ubuntu Server
To see available network interfaces on Ubuntu Server, run the following command:
Doing so will show a similar result:
The output enumerates network interfaces with numbers.
From this, I can see that the ethernet interface is 'enp1s0'.
Ubuntu Desktop
The advantage (at least in my opinion) of having Ubuntu Desktop is having NetworkManager as the renderer for netplan .
It has a pretty CLI output :)
Run the following command to view the available network interfaces:
That will give you the device name, type, state and connection status.
Here is what it looks like on my computer:
This is more readable at first glance. I can make out that my ethernet interface is named 'enp1s0'.
Step 2: See current IP address
Now that you know which interface needs to be addressed, let us edit a file .
Before I change my IP address/set a static one, let us first see what my current IP address is .
Nice! But let's change it to '192.168.122.128' for demonstration purposes.
Step 3: See the gateway
A gateway is a device that connects different networks (basically what your all-in-one router is). To know the address of your gateway, run the following command:
The gateway address will be on the line that begins with "default via".
Below is the output of running the ip command on my computer:
On the line that starts with "default via", I can see that my gateway address '192.168.122.1'
Make a note of your gateway address.
Step 4: Set static IP address
Now that you have detail like interface name and gateway address, it is time to edit a config file.
Step 4-A: Disable cloud-init if present
The easiest way to know if cloud-init is present or not is to check if there is a package with that name.
Run the following command to check:
If you get an outupt, you have 'cloud-init' installed.
Now, to disable could-init, create a new file inside the /etc/cloud/cloud.cfg.d directory. The name does not matter, so I will call it '99-disable-cloud-init.cfg'.
Add the following line to it:
Please reboot your Ubuntu system now so that cloud-init does not interfere when we set our static IP address in the next step. :)
Back to Step 4
Once the 'cloud-init' related configuration is complete, we must now edit the netplan configuration to add our static IP address.
Go to the /etc/netplan directory. It is better if there is one file (easier to know which one to edit), but in some cases, there might also be more than one file with the extension '.yml' or '.yaml'.
When in doubt, grep for the name of your network interface. Use the following command if you are not comfortable with grep:
Since the name of network interface for my ethernet is 'enp1s0', I will run the following command:
running this command shows that the file I am looking for is '00-installer-config.yaml'. So let us take a look at it.
You might have noticed a line that says 'ethernet' and our network interface name under that. Under this is where we configure our 'enp1s0' network interface.
Since we do not want DHCP assigned IP address, let us change that field from true to no .
Add a field called addresses . Write the IP address you wish to assign your computer along with the network prefix. So I will write 192.168.122.128/24 in the addresses field.
Finally, we also need to specify DNS nameservers. For that, create a new field called nameservers and under that, create a field called addresses which contains the IP address for your DNS servers . I used Cloudflare's DNS servers but you can use whatever you want.
This is what my '00-installer-config.yaml' file looks like after editing it to my liking.
To apply the settings, run the following command:
This will take only a few seconds, and the IP address will be updated once it is done.
You can check the IP address using the hostname -I command.
Perfect! The IP address has now changed successfully.
I know that it feels complicated but this is the proper procedure when you are trying to assign static IP via the command line in Ubuntu.
Let me know if you are stuck at some point or encounter any technical issues.
Fell in love with Ubuntu the first time I tried it. Been distro-hopping since 2016.
On this page
- Shell Scripting
- Docker in Linux
- Kubernetes in Linux
- Linux interview question
- id command in Linux with examples
- if command in linux with examples
- How to Find Your IP Address in Linux | ifconfig Command
- iftop command in Linux with Examples
- ifup command in Linux with Examples
- import command in Linux with Examples
- info command in Linux with Examples
- insmod command in Linux with examples
- install command in Linux with examples
- iostat command in Linux with examples
- iotop Command in Linux with Examples
ip Command in Linux with Examples
- ipcrm command in Linux with examples
- 'IPCS' command in Linux with examples
- iptables command in Linux with Examples
- iptables-save command in Linux with examples
- iwconfig command in Linux with Examples
- join Command in Linux
- journalctl Command in Linux with Examples
- How to Kill a Process in Linux | Kill Command
- last command in Linux with Examples
- less command in Linux with Examples
- let command in Linux with Examples
- ln command in Linux with Examples
- locate command in Linux with Examples
The ip command in Linux is a powerful utility for network configuration and management. It allows users to interact with various networking components such as network interfaces, routing tables, addresses, and more. In this guide, we will delve into the ip command, covering each aspect with examples, code, and detailed explanations.
Introduction to the IP Command in Linux
The ip command is part of the iproute2 package and serves as a versatile replacement for older networking tools like ` ifconfig ` and ` route ` . It provides a unified interface for configuring and managing network settings in modern Linux distributions.
Basic Usage and Syntax of IP Command
The basic syntax of the ip command is as follows:
- OPTIONS : Additional options that modify the behavior of the command.
- OBJECT : The networking component you want to interact with (e.g., link, address, route).
- COMMAND : The action you want to perform on the specified object.
- help : Displays help information about the specified object or command.
IP Command Examples and Practical Implementation
Displaying Network Interfaces and IP Addresses Using IP Command
Configuring network interfaces using ip command, managing routing tables using ip command, changing interface state using ip command, displaying detailed interface statistics using ip command.
To view information about network interfaces and their associated IP addresses, use the following command:

displaying network interface
This command displays details such as interface names (` eth0` , ` wlan0` ), MAC addresses, IPv4 and IPv6 addresses, subnet masks, and more.
To configure a network interface, you can use the ` ip link` command followed by the action (e.g., ` set` , ` add` , ` delete` ).
For example : to set the IP address of an interface:
This command assigns the IP address ` 192.168.1.100` with a subnet mask of ` 24` (equivalent to 255.255.255.0 ) to the eth0 interface.
Example 1: Deleting a Route
To delete an existing route from the routing table, you can use the ` ip route delete` command. For example:
This command removes the route to the ` 10.0.0.0/24` network via the gateway ` 192.168.1.1` through the ` eth0` interface.
Example 2: Changing the Default Gateway
To change the default gateway for outgoing traffic, you can modify the default route using the ` ip route` command. For instance:
This command sets ` 192.168.1.254` as the new default gateway through the ` eth0` interface.
Example 1: Bringing an Interface Up
To bring an interface up (activate it), you can use the ` ip link` command with the ` set` action. For example:
This command brings the ` eth0` interface up, enabling it to send and receive network traffic.
Example 2: Changing MTU (Maximum Transmission Unit)
To change the MTU (maximum transmission unit) of a network interface, you can use the ` ip link` command with the ` set` action and the ` mtu` parameter. For instance:
This command sets the MTU of the ` eth0` interface to ` 1500` bytes.
Example 1: Monitoring Interface Traffic
To monitor real-time network traffic on a specific interface, you can use the ` ip -s link` command in combination with tools like ` watch ` or ` grep ` to filter the output. For example:
This command continuously monitors the receive (RX) traffic on the ` eth0` interface, updating every second.
Example 2: Displaying Interface Errors
To identify potential issues with a network interface, you can use the ip -s link command to display detailed statistics, including error counts. For instance:
This command shows statistics related to packet errors and dropped packets on the eth0 interface.
Options available in the IP command in Linux
This option is used to show all IP addresses associated with all network devices.
.webp)
This will show the information related to all interfaces available on our system.
It is used to display link layer information; it will fetch characteristics of the link layer devices currently available. Any networking device which has a driver loaded can be classified as an available device.
.webp)
This link option when used with -s option is used to show the statistics of the various network interfaces.
.webp)
And, to get information about a particular network interface, add an option show followed by the name of the particular network interface.
For Example:
.webp)
ip -s link show enp3s0

3. monitor:
This command can monitor and display the state of devices, addresses and routes continuously.
.webp)
4. neighbour:
This command is used to view the MAC address of the devices connected to your system.
.webp)
ip neighbour
- STABLE: This means that the neighbor is valid, but is probably already unreachable, so the kernel will try to check it at the first transmission.
- REACHABLE: This means that the neighbor is valid and reachable.
- DELAY: This means that a packet has been sent to the stable neighbor and the kernel is waiting for confirmation.
- Delete an ARP entry:
Add an ARP entry:
The `ip` command in Linux is a powerful tool that is used for performing administrative tasks. We can say that this command is the improved version of the deprecated `ifconfig` command. As we discussed, this command can be used to manipulate devices, routing and tunnels. This `ip` command can also monitor the state of devices, routes and addresses. Overall, we can say that this command is a versatile tool that can be helpful network administrators manage their networks more efficiently.
Please Login to comment...
Similar reads, improve your coding skills with practice.
What kind of Experience do you want to share?
How to Configure Static IP Address on Ubuntu 24.04 (Desktop)
In this article, we will show you how to configure static ip address on Ubuntu 24.04 desktop step by step.
When you want a persistent IP address on your Ubuntu 24.04 desktop, then you must a configure a static IP address. Whenever we install Ubuntu then DHCP is enabled by default, and it will try to fetch the IP address from DHCP server if it is available over the network.
In Ubuntu Desktop 24.04, there are two ways to configure static IP address:
- Graphical User Interface
- Command Line
We will cover both the methods in this article.
Prerequisites
- Pre-Install Ubuntu 24.04
- Regular user with sudo rights
- Basic understanding of networks
Configure Static IP Address on Ubuntu 24.04 Using GUI
Login to your desktop, click on the network icon and then choose Wired option as shown below:
We will get the following window, click on “ gearbox” icon
Go to IPv4 tab, there you will see that DHCP is enabled for automatic IP allocation.
Choose Manual option to configure static IP address and specify IP details (IP address, netmask, gateway and DNS IP) as show below:
Note: Change the IP details that suits to your network
Click on Apply .
Next, disable and enable the interface to make above changes into effect.
Above screen confirms that we have successfully configured static IP address on our Ubuntu 24.04 desktop.
Configure Static IP Address on Ubuntu 24.04 Using Command Line
We can use netplan utility and its configuration file to assign the static ip on the interface (like ep0s3 or eth0).
Netplan configuration file are placed in /etc/netplan directory. Under this directory there should be a file with name 01-netcfg.yaml , 50-cloud-init.yaml or may be else depending on your environment.
Edit netplan configuration file, in our case it is 01-netcfg.yaml
save and close the file.
Note: In above file, replace the IP address details and interface according to your setup. We have also used renderer as “ NetworkManager ” which instructs netplan to use NetworkManager as its backend. It is used for desktops and for the servers and headless environments use “ networkd ” instead of NetworkManager.
Set the permission on this file using chmod command,
To make above changes into the affect, run below netplan apply command.
Next, verify the IP address and network connectivity.
Perfect, output above shows that we have successfully configure static ip address using netplan utility.
That’s all from this article. We hope you have found it informative and useful, feel free to post your queries and feedback in below comments section.
Read Also : How to Install Git on Ubuntu 24.04
Leave a Comment Cancel reply
Establishing Remote Access to Linux Servers Behind Firewalls: A Guide
Accessing a Linux server behind a firewall remotely can seem like a daunting task, but it doesn’t have to be. In just a few steps, you can establish a secure connection that allows you to manage your server from anywhere. Whether you’re a system administrator or just someone who needs to access a server occasionally, this quick overview will help you understand the process.
Tutorial for Establishing Remote Access to Linux Servers Behind Firewalls
Before diving into the step-by-step guide, let’s understand what we’re aiming to achieve. Establishing remote access to a Linux server behind a firewall involves configuring the server to accept secure connections over the internet. This process ensures that you can access the server’s resources without exposing it to security threats.
Step 1: Check your firewall settings
Ensure that your firewall allows incoming connections on the port used for remote access (typically port 22 for SSH).
Firewalls are designed to block unauthorized access to your network, but they can also prevent legitimate remote connections. Before proceeding, you must ensure that your firewall settings allow incoming connections on the port used for SSH (Secure Shell), which is the standard method for secure remote login on Linux servers.
Step 2: Install and configure SSH server
Install an SSH server on your Linux server and configure it to accept remote connections.
SSH is a protocol that provides a secure channel over an unsecured network. By installing an SSH server, such as OpenSSH, you’re setting up a way for authorized users to remotely connect to your Linux server. Be sure to follow best practices for security, such as disabling root login and using key-based authentication.
Step 3: Set up port forwarding
Configure your router to forward incoming SSH connections to the Linux server’s local IP address.
When you’re behind a firewall, often a router, you’ll need to set up port forwarding to direct incoming connections to your server. This means that any connection requests on the port you specified will be sent to your Linux server’s local IP address, allowing remote access.
Step 4: Connect from a remote client
Use an SSH client on your remote device to establish a connection to your Linux server using its public IP address.
Once everything is set up on the server side, you can connect to your Linux server from a remote client. This could be a computer or even a mobile device with an SSH client installed. Enter your server’s public IP address and authenticate with your credentials to start managing your server remotely.
After completing these steps, you will have established a secure remote connection to your Linux server behind a firewall. This will allow you to manage your server from anywhere, as long as you have an internet connection. Remember, maintaining the security of your server is crucial, so always follow best practices and keep your system updated.
Tips for Establishing Remote Access to Linux Servers Behind Firewalls
- Always use strong, unique passwords for your SSH login to prevent unauthorized access.
- Consider using key-based authentication instead of password authentication for added security.
- Regularly update your SSH server software to patch any potential vulnerabilities.
- Limit the number of allowed login attempts to prevent brute-force attacks.
- Monitor your server logs to keep an eye on any suspicious activities or access attempts.
Frequently Asked Questions
What is ssh.
SSH, or Secure Shell, is a protocol that allows secure remote login and other secure network services over an unsecured network.
Is it safe to open a port on my firewall for SSH?
Yes, it is generally safe to open a port for SSH as long as you use strong authentication methods and keep your server software updated.
Can I use a different port other than the default for SSH?
Absolutely. Changing the default SSH port can add an extra layer of security by making it less predictable for potential attackers.
What is port forwarding?
Port forwarding is a network configuration that directs traffic to a specific IP address within your local network, allowing remote access to devices behind a router or firewall.
Do I need a static IP address for my server?
While it’s not strictly necessary, having a static IP makes it easier to connect consistently, as the address won’t change each time the server restarts.
- Check firewall settings for SSH connections.
- Install and configure an SSH server.
- Set up port forwarding on your router.
- Connect from a remote client using your server’s public IP.
Establishing remote access to Linux servers behind firewalls is a fundamental skill for anyone managing servers. It’s all about balancing accessibility with security. By following the steps outlined in this article, you’ve learned how to set up a secure connection that allows you to administer your server from anywhere.
Remember, the key to maintaining a secure remote access setup is keeping your system updated and monitoring for any unusual activity. Always use strong, unique passwords or, even better, key-based authentication. And don’t forget to limit login attempts and change the default SSH port if you’re feeling extra cautious.
Whether you’re a newbie or a seasoned sysadmin, remote access can simplify your workflow and enhance productivity. So, why not give it a try? And if you run into any roadblocks, there’s a wealth of information and helpful communities out there to support you on your journey. Happy remote accessing!

Kermit Matthews is a freelance writer based in Philadelphia, Pennsylvania with more than a decade of experience writing technology guides. He has a Bachelor’s and Master’s degree in Computer Science and has spent much of his professional career in IT management.
He specializes in writing content about iPhones, Android devices, Microsoft Office, and many other popular applications and devices.
Read his full bio here .
Share this:
- Click to share on Twitter (Opens in new window)
- Click to share on Facebook (Opens in new window)
- Click to email a link to a friend (Opens in new window)
- Click to share on LinkedIn (Opens in new window)
- Click to share on Reddit (Opens in new window)
- Click to share on Pinterest (Opens in new window)
- Click to share on Tumblr (Opens in new window)
Related posts:
- How to Remotely Access a Computer Behind a Firewall with SSH/VNC
- SSH Error Handling: Troubleshooting Authentication Agent Issues
- Solving SSH Authentication Issues: Fixing ‘Could Not Open a Connection’
- Setting Up a Free Remote SSH Connection for IoT on Windows 11 Guide
- Connecting to an IoT Device via SSH on Windows 11: A Step-by-Step Guide
- Accessing IoT Platforms Remotely via SSH for Free: A How-To Guide
- Securing IoT Devices with SSH: A Step-by-Step Guide
- Accessing IoT Devices Over Internet Using SSH: A Step-by-Step Guide
- Resolving GitHub SSH Key Issues: Fixing ‘Permission Denied (publickey)’ Error
- Accessing IoT Platforms Remotely Using SSH: A Step-by-Step Guide
- Accessing IoT Devices Remotely with SSH: A How-To Guide
- How to Disable the Firewall on a Mac in macOS High Sierra
- Choosing the Best Linux Distribution for Programming in 2021: Top Picks
- Setting Up an IoT Management Platform over SSH: A Step-by-Step Guide
- Git Essentials: Fixing ‘Remote Origin Already Exists’ Error
- How to Reset Google TV Remote: A Step-by-Step Guide
- How to Get Apple TV Remote on iPhone 13
- How to Pair Google TV Remote: A Step-by-Step Guide
- Setting Up Nginx for High-Performance Server and Reverse Proxy Needs
- Managing Buffered Client Requests: Optimizing Web Server Performance
Change the hostname of your AL2 instance
When you launch an instance into a private VPC, Amazon EC2 assigns a guest OS hostname. The type of hostname that Amazon EC2 assigns depends on your subnet settings. For more information about EC2 hostnames, see Amazon EC2 instance hostname types in the Amazon EC2 User Guide for Linux Instances .
A typical Amazon EC2 private DNS name for an EC2 instance configured to use IP-based naming with an IPv4 address looks something like this: ip-12-34-56-78.us-west-2.compute.internal , where the name consists of the internal domain, the service (in this case, compute ), the region, and a form of the private IPv4 address. Part of this hostname is displayed at the shell prompt when you log into your instance (for example, ip-12-34-56-78 ). Each time you stop and restart your Amazon EC2 instance (unless you are using an Elastic IP address), the public IPv4 address changes, and so does your public DNS name, system hostname, and shell prompt.
This information applies to Amazon Linux. For information about other distributions, see their specific documentation.
Change the system hostname
If you have a public DNS name registered for the IP address of your instance (such as webserver.mydomain.com ), you can set the system hostname so your instance identifies itself as a part of that domain. This also changes the shell prompt so that it displays the first portion of this name instead of the hostname supplied by AWS (for example, ip-12-34-56-78 ). If you do not have a public DNS name registered, you can still change the hostname, but the process is a little different.
In order for your hostname update to persist, you must verify that the preserve_hostname cloud-init setting is set to true . You can run the following command to edit or add this setting:
If the preserve_hostname setting is not listed, add the following line of text to the end of the file:
To change the system hostname to a public DNS name
Follow this procedure if you already have a public DNS name registered.
For AL2: Use the hostnamectl command to set your hostname to reflect the fully qualified domain name (such as webserver.mydomain.com ).
For Amazon Linux AMI: On your instance, open the /etc/sysconfig/network configuration file in your favorite text editor and change the HOSTNAME entry to reflect the fully qualified domain name (such as webserver.mydomain.com ).
Reboot the instance to pick up the new hostname.
Alternatively, you can reboot using the Amazon EC2 console (on the Instances page, select the instance and choose Instance state , Reboot instance ).
Log into your instance and verify that the hostname has been updated. Your prompt should show the new hostname (up to the first ".") and the hostname command should show the fully-qualified domain name.
To change the system hostname without a public DNS name
For AL2: Use the hostnamectl command to set your hostname to reflect the desired system hostname (such as webserver ).
For Amazon Linux AMI: On your instance, open the /etc/sysconfig/network configuration file in your favorite text editor and change the HOSTNAME entry to reflect the desired system hostname (such as webserver ).
Open the /etc/hosts file in your favorite text editor and change the entry beginning with 127.0.0.1 to match the example below, substituting your own hostname.
You can also implement more programmatic solutions, such as specifying user data to configure your instance. If your instance is part of an Auto Scaling group, you can use lifecycle hooks to define user data. For more information, see Run commands on your Linux instance at launch and Lifecycle hook for instance launch in the AWS CloudFormation User Guide .
Change the shell prompt without affecting the hostname
If you do not want to modify the hostname for your instance, but you would like to have a more useful system name (such as webserver ) displayed than the private name supplied by AWS (for example, ip-12-34-56-78 ), you can edit the shell prompt configuration files to display your system nickname instead of the hostname.
To change the shell prompt to a host nickname
Create a file in /etc/profile.d that sets the environment variable called NICKNAME to the value you want in the shell prompt. For example, to set the system nickname to webserver , run the following command.
Open the /etc/bashrc (Red Hat) or /etc/bash.bashrc (Debian/Ubuntu) file in your favorite text editor (such as vim or nano ). You need to use sudo with the editor command because /etc/bashrc and /etc/bash.bashrc are owned by root .
Edit the file and change the shell prompt variable ( PS1 ) to display your nickname instead of the hostname. Find the following line that sets the shell prompt in /etc/bashrc or /etc/bash.bashrc (several surrounding lines are shown below for context; look for the line that starts with [ "$PS1" ):
Change the \h (the symbol for hostname ) in that line to the value of the NICKNAME variable.
(Optional) To set the title on shell windows to the new nickname, complete the following steps.
Create a file named /etc/sysconfig/bash-prompt-xterm .
Make the file executable using the following command.
Open the /etc/sysconfig/bash-prompt-xterm file in your favorite text editor (such as vim or nano ). You need to use sudo with the editor command because /etc/sysconfig/bash-prompt-xterm is owned by root .
Add the following line to the file.
Log out and then log back in to pick up the new nickname value.
Change the hostname on other Linux distributions
The procedures on this page are intended for use with Amazon Linux only. For more information about other Linux distributions, see their specific documentation and the following articles:
How do I assign a static hostname to a private Amazon EC2 instance running RHEL 7 or Centos 7?

To use the Amazon Web Services Documentation, Javascript must be enabled. Please refer to your browser's Help pages for instructions.
Thanks for letting us know we're doing a good job!
If you've got a moment, please tell us what we did right so we can do more of it.
Thanks for letting us know this page needs work. We're sorry we let you down.
If you've got a moment, please tell us how we can make the documentation better.

How to Add Additional IPv4 and IPv6 to Linux VPS
Most Linux servers have a public IP address allowing remote connections.
Adding additional IPv4 and IPv6 serves various purposes, such as:
- Hosting multiple websites or services.
- Loading balancing, and high availability.
- Adopting IPv6 to future-proof your online presence.
To add additional IPv4 and IPv6 to Linux VPS , first, you need to have purchased Linux VPS to be able to order IPs through your VPS provider’s control panel.
The extra IP addresses must be added manually to the network interfaces since DHCP cannot be used to automatically add them to VPS.
So, the final step is to configure the network settings to manage new IP addresses.
Table of Contents
Steps to Configure IP Addresses in Linux VPS
The process of Adding additional IPv4 and IPv6 addresses involves obtaining the IPs from your VPS provider’s control panel and configuring your network settings.
This typically involves steps like logging into the control panel, requesting additional IPs, and then updating your Linux system’s network configuration file.
There are two main steps to finish this process:
Step 1: Obtain the Additional Addresses
This depends on your setup. If you’re using a cloud provider or VPS hosting, you’ll likely need to order them through their control panel.
For a local network, you might need to configure your router to assign additional addresses through DHCP or manually assign static IPs within a valid range.
To order an IPv4 and add an IPv6 address , follow the below path:
- Log in to your Linux VPS Control Panel using your account credentials.
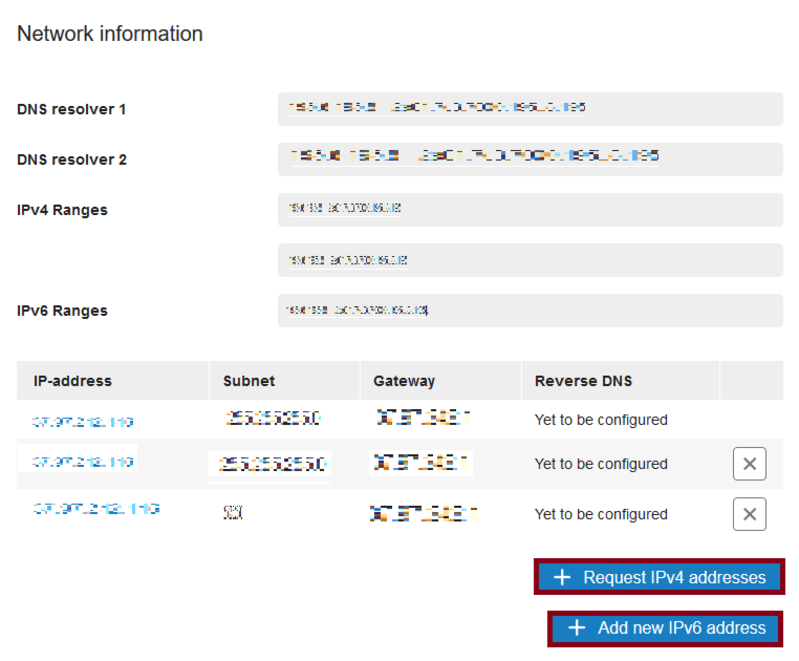
- Select ‘ Manage ‘ from the upper right corner, then select ‘ Network information ‘.
- A summary of your IP addresses is displayed to you. To order extra IP addresses, click “ Request IPv4 addresses .”
- In the same path as above, after clicking “Request IPv4 addresses”, click ” Add new IPv6 address ” to add an IPv6 address.
Note : If you send emails from your VPS using this IP address, after adding the IPv6 address, make sure you have set up your reverse DNS.
Step 2: Configure Extra IPv4 or IPv6 Addresses on Linux VPS
Once you have the additional addresses, you need to configure your Linux system to recognize and use them. The specific steps depend on your Linux distribution.
Here, we explain the way you can add an IPv4 address and an IPv6 address in Ubuntu 22.04.
Follow the below path to configure the Network Interface on Ubuntu 22.04:
- Connect to the VPS via the Ubuntu VPS console or SSH .
- Run the command below to view the current network interfaces:
- Open the network configuration file to add the extra IPv4 and IPv6 addresses in the network interfaces:
- Add the following values to the file ( For IPV4 ) ethernets: ens3: dhcp4: no dhcp6: yes addresses: - Your primary IPv4 and IPv6 addresses with the range /24 addition - Your primary IPv4 and IPv6 addresses with the range /24 addition routes: - to: default via: Your primary IP
Note : Do not enter additional gateways for secondary IPs.
For IPv6 , add:
- Save the changes and exit.
- Now, you are ready to use the new IP address. To do this, run:
- Again, by running the ip a command, you can check the newly added IPv4 and IPv6 addresses.
- If you do not see the new configuration, you must check if a file exists called 01-network-manager-all.yaml in /etc/netplan /. To do this, type:
- If yes, use the command below to rename the file:
You must see the correct configuration by running the sudo netplan apply and ls /etc/netplan/ commands.
When and Why Add Additional IPv4 and IPv6 to Linux VPS
Imagine your Linux VPS as a bustling apartment building. By default, it has one main address for everyone.
But what if you want to rent out additional units? That’s where extra IP addresses come in, acting like unique door numbers for each new tenant.
Here’s why you might want to add more “door numbers” to your VPS:
Multiple Websites or Businesses:
Running separate websites or online stores? Assigning individual IP addresses to each gives them their own “shopfront” online, improving security and allowing you to manage them independently.
Scaling Up and Sharing Resources:
Need to handle more traffic or want to host a game server? Adding IPs lets you distribute the workload across multiple “apartments” within your VPS, boosting performance and reliability.
With IPv4 addresses becoming scarce, IPv6 offers a future-proof solution with a vast number of unique addresses, ensuring your virtual building has room for all its potential tenants.
Additional Notes :
- Keep in mind to back up your network configuration files before making changes.
- Make sure the additional IP addresses are valid and within a usable range for your network.
- You might need to adjust firewall rules to allow incoming traffic on the new addresses.
How IPv4 and IPv6 are different?
IPv4, the current standard, faces an exhaustion problem due to its limited 32-bit address space.
IPv6, the next-generation protocol, offers a significantly larger 128-bit address space, ensuring an almost limitless pool of unique identifiers for future internet growth.
How do I obtain additional IP addresses?
This depends on your setup. Typically, you’ll order them through your VPS provider’s control panel.
How do I configure the additional IP addresses on my Linux VPS?
The process varies depending on your Linux distribution:
- Identifying your network interface.
- Editing the network configuration file (e.g., netplan config file in Ubuntu).
- Adding entries for the new IP addresses.
- Saving the changes and restarting the network service.
Are there any risks involved in adding additional IP addresses?
There are minimal risks if done correctly.
However, it’s important to:
- Back up your network configuration files before making changes.
- Ensure the additional IP addresses are valid and within a usable range for your network.
- Adjust firewall rules to allow incoming traffic on the new addresses.
What if I encounter problems Configuring the IP addresses?
If you have chosen OperaVPS as your VPS provider, you can contact us 24/7 to receive support resources or documentation.
You can also search online forums or communities for troubleshooting guides specific to your Linux distribution.
Similar to adding extra units in an apartment building, assigning additional IPv4 and IPv6 addresses to your Linux VPS allows you to host multiple websites or services independently.
By obtaining these IPs through your VPS provider’s control panel and configuring your network settings (steps provided for Ubuntu 22.04), you can distribute the workload for better performance and leverage the vastness of IPv6 for future scalability.
Remember to back up configurations and adjust firewall rules for the new addresses.
Leave a Reply Cancel reply
Your email address will not be published. Required fields are marked.
Save my name, email, and website in this browser for the next time I comment.

How To Set Up a Firewall in 8 Easy Steps + Best Practices
Maine Basan
eSecurity Planet content and product recommendations are editorially independent. We may make money when you click on links to our partners. Learn More .
Setting up a firewall is the first step in securing your network. A successful firewall setup and deployment requires careful design, implementation, and maintenance to effectively improve your network integrity and data security. Before performing a firewall configuration, consider factors such as security requirements, network architecture, and interoperability; avoid typical firewall setup errors; and follow the best practices below.
Table of Contents
8 Considerations Before Setting Up a Firewall
Some factors to consider before you configure a firewall include creating detailed requirements and a proof of concept. Take note of your security requirements, physical environment, and component interoperability. Assess your network design, management protocols, and your future needs to ensure an effective protection without bottlenecks while also aligning with company goals and security standards for a secure network strategy.
Be sure you have the following before getting started:
- Clearly-defined requirements: Understand the organization’s requirements, such as the type of firewall, performance requirements, compliance requirements, and minimum specifications. Check if the chosen solution is consistent with the organization’s goals and infrastructure.
- Proof of concept: Execute a proof of concept or environment simulation once you identify the potential firewall products to select the best-fit solution for the organization’s specific requirements. Verify that the chosen firewall can meet your security standards and functions.
- Firewall architecture design and environment: Finalize your architecture, harden configurations, identify location and dependencies, and define policy rules. Evaluate the network firewalls’ physical placement, security, space, power, cooling, and network requirements.
- Security needs and capabilities: Determine which types of firewall, such as packet filtering, stateful inspection, or application firewalls , are most suited to their traffic requirements. Consider your other security measures like intrusion detection, VPNs , and content filtering.
- Component interoperability: Verify the compatibility with your current network infrastructure, including hardware and software. Evaluate the interoperability with your logging systems, as well as prospective network upgrades. Confirm that all components integrate seamlessly.
- Network requirements: Understand your network’s capacity, maximum simultaneous connections, latency requirements, and future traffic demands. Consider load balancing, failover mechanisms, and your preference for hardware-based or software-based firewalls.
- Management: Evaluate the firewall’s remote management protocols, adherence to organizational regulations, and remote management access limits. Utilize centralized management capabilities across numerous devices, as well as future scalability.
- Future Needs: Assess if the chosen firewall solution can meet your organization’s predicted demands, such as IPv6 migration, anticipated bandwidth requirements, and compliance with new regulations. Ensure that your firewall investment is effective and scalable over time.
8 Steps to Set Up a Firewall
To set up a firewall, configure the tool by creating rules, network zones, and policies. Activate logging and alerts, and perform extensive testing and auditing. Finally, deploy the firewall and perform regular monitoring and maintenance to provide an ideal security posture and effective network protection.
1. Prepare for Installation
The first stage in setting up a firewall is to prepare for installation after evaluating the type of firewall you need via the risk assessment listed above. Gather the necessary equipment, evaluate the network layout, and become familiar with the firewall documentation.
Physically install the firewall and ensure appropriate connections. Install hardware, operating systems, and software, apply fixes, and harden the firewall to reduce vulnerabilities. Only the administrator should have the authority to control the firewall, deactivate superfluous services, and secure the physical environment. Synchronize firewall clocks with other systems to improve log analysis.
2. Set Secure Firewall Rules & ACLs
To prevent unwanted access and ensure effective traffic management, secure your firewall through updating firmware to resolve vulnerabilities and adopting proper configurations prior to installing firewalls in production. Disabling default accounts and changing passwords improve security, as does requiring strong passwords for administrator accounts.
The Simple Network Management Protocol (SNMP) should be disabled or set securely. Firewall rules , defined by access control lists (ACLs), control traffic based on IP addresses, port numbers, and protocols. To maximize security, thoroughly test configurations, including advanced features such as web category filtering and intrusion prevention, prior to deployment.
3. Establish Your Network Zones Structure
Establishing your network zone structure involves determining the sections of your network, known as network zones, that hold high-value assets and data and surrounding them with firewalls to regulate access and assure security. This technique complies with PCI-DSS rules and ensures strong security.
Carefully distribute resources to each zone, balancing security requirements with administrative complexity. Consider establishing a demilitarized zone for important servers to enable comprehensive traffic monitoring. Remember to create an IP address structure that efficiently connects firewall interfaces to their corresponding zones, hence improving network organization and security.
4. Configure Firewall Policies
Configuring policies is one of the most essential phases in effectively securing a network through firewalls. Firewall policies set network access conditions, including authorized ports, approved IP addresses, and security zones for network segmentation. Testing in a controlled environment confirms that the firewall performs as expected, blocking unwanted traffic based on ACL configurations.
Once tested, the firewall is ready for production, with a backup configuration safely preserved. Consider hiring a security specialist to check your configurations for maximum data protection. Tailor firewall capabilities such as network segmentation and application controls to specific network zones while sticking to formal policies to avoid implementation complications.
Need help in creating a firewall policy document? Check out our guide on firewall policy steps and download our free template .
5. Configure Logging & Alerts
Recording and monitoring firewall activity makes sure that security risks or operational concerns are detected in a timely manner. Logging captures critical information for failure prevention, recovery, and incident response. Determine what to log and how long to keep logs based on network requirements and resource limits.
Send logs to both local and centralized storage for complete monitoring. Create administrative accounts with read-only access to logs for auditing. Configure real-time notifications for critical events such as firewall rule updates or system status changes to provide a timely reaction to possible threats or operational difficulties. Customize logging and alert settings to meet your individual network needs and security priorities.
6. Test & Audit Your Firewall
Prior to deployment, conduct penetration testing and vulnerability scanning to find holes and improve defenses. Following deployment, plan regular audits to check firewall logs, verify ACLs and rules, and assure compliance. Changes should be documented and audit information stored for regulatory reporting purposes.
Implement procedures for updating firewall firmware and extensively testing additional features such as VPN and antimalware functionality. To accurately analyze firewall performance and effectiveness, ensure that the test network closely resembles production environments. Regular updates and thorough testing ensure a safe network environment.
7. Deploy the Firewall
Deploying a firewall means transitioning from testing to actual operations while adhering to organizational regulations. Notify the users who were affected and coordinate any necessary equipment upgrades. Integrate the firewall’s security policy with the entire organizational policy and manage configuration changes as they occur. Consider a staged rollout or pilot program to fix difficulties before full implementation.
Integrating the firewall into the network entails more than just insertion; it also needs routing integration and possible switch reconfiguration. If you use failover mechanisms, set up network switches accordingly. Careful design and coordination guarantee that the firewall integrates seamlessly and operates effectively within the network infrastructure.
Integrate your firewall with network monitoring tools for more efficient tracking of your network’s performance and security.
8. Manage & Maintain the Correct Firewall Configuration
Firewall configuration management and maintenance imply continual efforts to ensure maximum functionality and security. This includes testing and deploying patches , updating policy rules to accommodate new threats or changes in network requirements, and monitoring performance to identify possible resource issues. Continuously monitor logs and alerts to detect and respond to threats effectively.
Periodic testing validates firewall rules, and regular backups of policies and rule sets protect against data loss. Formal configuration management methods should govern ruleset modifications, with admin access limitations and detailed documentation for accountability. Every six months, perform firmware updates, vulnerability checks , and configuration reviews to make sure the firewall remains efficient and effectively protects the network.
6 Common Mistakes to Avoid When Setting Up a Firewall
Misconfigured firewalls pose serious risks, allowing attackers easy access and endangering organizational security. Common failures involve providing unrestricted outbound traffic, forgetting to detect internal threats, updating rules inconsistently, establishing overly broad policies, testing using production data, and failing to log appropriately. These flaws expose networks to vulnerabilities and breaches, weakening security protections.
Allowing Unrestricted Outbound Traffic
A typical mistake is configuring the firewall to enable unrestricted outbound traffic. While focusing on inbound threats, failing to monitor outgoing traffic allows malware or attackers to exfiltrate data, potentially leading to costly breaches. Controlling outgoing traffic prevents unauthorized data leaks and maintains network security .
Neglecting Internal Threats
Focusing primarily on external threats exposes networks to inside attacks, including compromised internal hosts. Internal firewalls and access restrictions should be built to reduce risks from insider attacks or externally compromised systems, ensuring complete network protection.
Performing Inconsistent Firewall Rule Updates
Adopting a “set it and forget it” approach to firewall rules results in obsolete setups that don’t meet current network requirements or security policies. Regularly monitor and update firewall rules to account for changes in network architecture, user access, and regulatory compliance, ensuring an effective security posture and minimizing vulnerabilities.
Creating Overly Broad Policy Configurations
Configuring firewalls with too permissive policies, which allow traffic from any source to any destination, broadens the attack surface and exposes the network to unnecessary risk. Minimize the potential for breaches by adhering to the concept of least privilege and ensuring that the firewall regulations restrict access to just necessary services and resources.
Testing Systems with Production Data
Using production data in test settings jeopardizes security and breaches governance guidelines. Test systems shouldn’t connect to production systems or collect critical data to avoid being exposed to low-security situations. Enforcing rigorous access controls to test data assures regulatory compliance while also maintaining data integrity.
Failing to Conduct Proper Logging & Monitoring
Failure to evaluate firewall log outputs or configure monitoring systems with adequate granularity reduces threat detection and incident response capabilities. Proper logging architecture and analysis quickly detect and investigate security occurrences, enabling proactive defense actions and lowering the risk of breaches.
10 Best Practices in Setting Up a Firewall
Any errors in the configuration of your systems may increase your vulnerability to security breaches. From ensuring compliance to creating multiple layers of security, adopt the best practices below to limit these risks and avoid typical errors while configuring a firewall.
Select the Correct Firewall Type
Choose the firewall type that best meets your network’s needs. Available options include packet-filtering firewalls , stateful inspection firewalls , and sophisticated proxies with intrusion detection and prevention. For example, for a small office network, a stateful inspection firewall with minimal traffic filtering features may suffice, providing protection without being overly complex.
Utilize Compatible Security Tools
Use logging tools and run frequent audits to evaluate firewall performance. Employ penetration and vulnerability testing to assess network security. When choosing a firewall, consider a solution that strikes a balance between critical features and performance considerations, avoiding needless complexity that may reduce network efficiency. Look for compatible network security tools , such as endpoint protection platforms or threat intelligence platforms .
Streamline Processes via Automation
Automation tools make firewall configuration easier, reducing manual labor and lowering the risk of misconfiguration. Automation scripts and orchestration systems, for example, improve efficiency and provide a consistent security posture by streamlining rule management and policy enforcement across varied network environments. There are also solutions available that automate rule management, policy analysis, and compliance auditing.
Establish a Centralized Logging & Monitoring System
Centralized logging and monitoring systems collect vital information about potential threats and security breaches. Implementing a centralized logging system enables the efficient gathering, analysis, and visualization of firewall data across the network. A centralized system provides rapid detection of security issues, effective incident response , and proactive security actions to protect the network from potential threats.
Consider the Cloud Traffic
When establishing firewalls , prioritize solutions that can handle cloud-based apps and remote users. Implement policies and procedures that go beyond the traditional on-premise approaches. Failure to update firewall configurations to enable cloud traffic not only reduces productivity but also exposes enterprises to increased dangers, emphasizing the importance of a hybrid security approach that includes cloud-native defenses.
Prevent False Positives when Blocking Traffic
Fine-tune firewall policies to prevent excessively strict rules or requirements. Implement bespoke setups and whitelists to allow legitimate communications while limiting dangerous risks. Expect some initial issues and complaints as users adjust, but refine arrangements based on traffic patterns to guarantee effective security without compromising productivity.
Ensure Compliance
Firewall protection is pivotal for compliance adherence like PCI-DSS and HIPAA. Implement strong firewalls around sensitive data and ensure configuration changes meet regulatory standards. For example, adhere to logging compliance, especially under PCI-DSS, by enabling automated logging and verifying audit accuracy for comprehensive data recording.
Document the Firewall’s Capabilities
Record the firewall’s capabilities for optimal planning and deployment. For example, if a firewall lacks advanced intrusion detection capabilities, your company may need to enhance its security plan. Each firewall model has distinct characteristics and limits that influence security policies and deployment methods. Include these details in the planning document so that the firewall’s capabilities match the organization’s security objectives and requirements.
Create a Defense-in-Depth
Defense-in-depth is a security technique that involves establishing multiple layers of defense to protect against diverse threats. For example, a business may install a next-gen firewall at several network points, supplemented with antivirus software and intrusion detection systems. This strategy ensures that if one security layer fails, others are in place to reduce the risk and prevent a successful attack.
Conduct Regular Updates
Establish a consistent timetable for firewall assessments and updates to maintain continuing security while avoiding crucial activities during busy IT operations. Regular updates are required for firewall maintenance. To avoid illegal access, access controls should be reviewed and adjusted on a regular basis. Keep up with vendor-provided firmware, software patches, and security upgrades to resolve vulnerabilities and improve protection.
Bottom Line: Set Up a Firewall to Boost Your Network Security
A firewall efficiently strengthens defenses against cyberthreats while preserving data integrity and network operation. Make sure you have a specific setup for each network, taking into account its unique requirements. A comprehensive firewall audit identifies particular requirements and assesses your current structure. Additionally, regular maintenance guarantees an optimized firewall configuration, resulting in effective security measures that last over time.
To gain insights into your company’s specific firewall needs and assess its current status, explore our guide on performing a comprehensive firewall audit .
Get the Free Cybersecurity Newsletter
Strengthen your organization’s IT security defenses by keeping up to date on the latest cybersecurity news, solutions, and best practices. Delivered every Monday, Tuesday and Thursday
Previous article
Next article

Subscribe to Cybersecurity Insider
Strengthen your organization’s IT security defenses by keeping abreast of the latest cybersecurity news, solutions, and best practices.
IT Security Resources
How to block a program in a firewall (windows & mac).

Vulnerability Recap 5/6/24 – Aruba, Dropbox, GitLab Bugs

2024 State of Cybersecurity: Reports of More Threats & Prioritization Issues

Red Team vs Blue Team vs Purple Team: Differences Explained

Top Cybersecurity Companies
Top 10 cybersecurity companies.
- 1 Uniqkey – Business Password Manager
See full list
Get the Free Newsletter!
Subscribe to Cybersecurity Insider for top news, trends & analysis
Related Articles

How To Set Up DMZ on Servers: 7-Step DMZ Configuration
Legacy versions
The legacy versions of the Compose file reference has moved to the V1 branch of the Compose repository . They are no longer being actively maintained.
The latest and recommended version of the Compose file format is defined by the Compose Specification . This format merges the 2.x and 3.x versions and is implemented by Compose 1.27.0+ . For more information, see the History and development of Docker Compose .
Select Product
Machine Translated
14.1 - Current Release
NetScaler Release Notes
Getting Started with NetScaler
Where Does a NetScaler Appliance Fit in the Network?
How a NetScaler Communicates with Clients and Servers
Introduction to the NetScaler Product Line
Install the hardware
Access a NetScaler
Configure the ADC for the first time
Secure your NetScaler deployment
Configure high availability
Change an RPC node password
Configuring a FIPS Appliance for the First Time
Understanding Common Network Topologies
System management settings
System settings
Packet forwarding modes
Network interfaces
Clock synchronization
DNS configuration
SNMP configuration
Verify Configuration
Load balance traffic on a NetScaler appliance
Load balancing
Persistence settings
Configure features to protect the load balancing configuration
A typical load balancing scenario
Use case - How to force Secure and HttpOnly cookie options for websites using the NetScaler appliance
Accelerate load balanced traffic by using compression
Secure load balanced traffic by using SSL
Features at a Glance
Application Switching and Traffic Management Features
Application Acceleration Features
Application Security and Firewall Features
Application Visibility Feature
NetScaler Solutions
Setting up NetScaler for Citrix Virtual Apps and Desktops
Global Server Load Balancing (GSLB) Powered Zone Preference
Anycast support in NetScaler
Deploy digital advertising platform on AWS with NetScaler
Enhancing Clickstream analytics in AWS using NetScaler
NetScaler in a Private Cloud Managed by Microsoft Windows Azure Pack and Cisco ACI
Creating a NetScaler Load Balancer in a Plan in the Service Management Portal (Admin Portal)
Configuring a NetScaler Load Balancer by Using the Service Management Portal (Tenant Portal)
Deleting a NetScaler Load Balancer from the Network
NetScaler cloud native solution
Kubernetes Ingress solution
Service mesh
Solutions for observability
API gateway for Kubernetes
Use NetScaler ADM to Troubleshoot NetScaler cloud native Networking
Deploy a NetScaler VPX instance
Support matrix and usage guidelines
Optimize NetScaler VPX performance on VMware ESX, Linux KVM, and Citrix Hypervisors
Support for increasing NetScaler VPX disk space
Apply NetScaler VPX configurations at the first boot of the NetScaler appliance in cloud
Improve SSL-TPS performance on public cloud platforms
Configure simultaneous multithreading for NetScaler VPX on public clouds
Install a NetScaler VPX instance on a bare metal server
Install a NetScaler VPX instance on Citrix Hypervisor
Configuring NetScaler Virtual Appliances to use Single Root I/O Virtualization (SR-IOV) Network Interfaces
Install a NetScaler VPX instance on VMware ESX
Configure NetScaler VPX to use VMXNET3 network interface
Configure NetScaler VPX to use SR-IOV network interface
Configure NetScaler VPX to use Intel QAT for SSL acceleration in SR-IOV mode
Migrating the NetScaler VPX from E1000 to SR-IOV or VMXNET3 network interfaces
Configure NetScaler VPX to use PCI passthrough network interface
Apply NetScaler VPX configurations at the first boot of the NetScaler appliance on VMware ESX hypervisor
Install a NetScaler VPX instance on VMware cloud on AWS
Install a NetScaler VPX instance on Microsoft Hyper-V servers
Install a NetScaler VPX instance on Linux-KVM platform
Prerequisites for installing NetScaler VPX virtual appliances on Linux-KVM platform
Provisioning the NetScaler virtual appliance by using OpenStack
Provisioning the NetScaler virtual appliance by using the Virtual Machine Manager
Configuring NetScaler virtual appliances to use SR-IOV network interface
Configure a NetScaler VPX on KVM hypervisor to use Intel QAT for SSL acceleration in SR-IOV mode
Configuring NetScaler virtual appliances to use PCI Passthrough network interface
Provisioning the NetScaler virtual appliance by using the virsh Program
Managing the NetScaler Guest VMs
Provisioning the NetScaler virtual appliance with SR-IOV on OpenStack
Configuring a NetScaler VPX instance on KVM to use OVS DPDK-Based host interfaces
Apply NetScaler VPX configurations at the first boot of the NetScaler appliance on the KVM hypervisor
Deploy a NetScaler VPX instance on AWS
AWS terminology
AWS-VPX support matrix
Limitations and usage guidelines
- Prerequisites
Configure AWS IAM roles on NetScaler VPX instance
How a NetScaler VPX instance on AWS works
Deploy a NetScaler VPX standalone instance on AWS
Scenario: standalone instance
Download a NetScaler VPX license
Load balancing servers in different availability zones
How high availability on AWS works
Deploy a VPX HA pair in the same AWS availability zone
High availability across different AWS availability zones
Deploy a VPX high-availability pair with elastic IP addresses across different AWS zones
Deploy a VPX high-availability pair with private IP addresses across different AWS zones
Deploy a NetScaler VPX instance on AWS Outposts
Protect AWS API Gateway using the NetScaler Web Application Firewall
Add back-end AWS auto scaling service
Deploy NetScaler GSLB on AWS
Deploy NetScaler VPX on AWS
Configure a NetScaler VPX instance to use SR-IOV network interface
Configure a NetScaler VPX instance to use Enhanced Networking with AWS ENA
Upgrade a NetScaler VPX instance on AWS
Troubleshoot a VPX instance on AWS
Deploy a NetScaler VPX instance on Microsoft Azure
Azure terminology
Network architecture for NetScaler VPX instances on Microsoft Azure
Configure a NetScaler standalone instance
Configure multiple IP addresses for a NetScaler VPX standalone instance
Configure a high-availability setup with multiple IP addresses and NICs
Configure a high-availability setup with multiple IP addresses and NICs by using PowerShell commands
Deploy a NetScaler high-availability pair on Azure with ALB in the floating IP-disabled mode
Deploy the NetScaler for Azure DNS private zone
Configure a NetScaler VPX instance to use Azure accelerated networking
Configure HA-INC nodes by using the NetScaler high availability template with Azure ILB
Configure HA-INC nodes by using the NetScaler high availability template for internet-facing applications
Configure a high-availability setup with Azure external and internal load balancers simultaneously
Install a NetScaler VPX instance on Azure VMware solution
Configure a NetScaler VPX standalone instance on Azure VMware solution
Configure a NetScaler VPX high availability setup on Azure VMware solution
Configure Azure route server with NetScaler VPX HA pair
Add Azure autoscale settings
Azure tags for NetScaler VPX deployment
Configure GSLB on NetScaler VPX instances
Configure GSLB on an active-standby high availability setup
Deploy NetScaler GSLB on Azure
Deploy NetScaler Web App Firewall on Azure
Configure address pools (IIP) for a NetScaler Gateway appliance
Configure multiple IP addresses for a NetScaler VPX instance in standalone mode by using PowerShell commands
Additional PowerShell scripts for Azure deployment
Create a support ticket for the VPX instance on Azure
Deploy a NetScaler VPX instance on Google Cloud Platform
Deploy a VPX high-availability pair on Google Cloud Platform
Deploy a VPX high-availability pair with external static IP address on Google Cloud Platform
Deploy a single NIC VPX high-availability pair with private IP address on Google Cloud Platform
Deploy a VPX high-availability pair with private IP addresses on Google Cloud Platform
Install a NetScaler VPX instance on Google Cloud VMware Engine
Add back-end GCP Autoscaling service
VIP scaling support for NetScaler VPX instance on GCP
Troubleshoot a VPX instance on GCP
Jumbo frames on NetScaler VPX instances
Automate deployment and configurations of NetScaler
Allocate and apply a license
Data governance
Console Advisory Connect
Upgrade and downgrade a NetScaler appliance
Before you begin
Upgrade considerations for configurations with classic policies
Upgrade considerations for customized configuration files
Upgrade considerations - SNMP configuration
Download a NetScaler release package
Upgrade a NetScaler standalone appliance
Downgrade a NetScaler standalone appliance
Upgrade a high availability pair
In Service Software Upgrade support for high availability
Downgrade a high availability pair
Troubleshooting
Solutions for Telecom Service Providers
Large Scale NAT
Points to Consider before Configuring LSN
Configuration Steps for LSN
Sample LSN Configurations
Configuring Static LSN Maps
Configuring Application Layer Gateways
Logging and Monitoring LSN
TCP SYN Idle Timeout
Overriding LSN configuration with Load Balancing Configuration
Clearing LSN Sessions
Load Balancing SYSLOG Servers
Port Control Protocol
LSN44 in a cluster setup
Dual-Stack Lite
Points to Consider before Configuring DS-Lite
Configuring DS-Lite
Configuring DS-Lite Static Maps
Configuring Deterministic NAT Allocation for DS-Lite
Configuring Application Layer Gateways for DS-Lite
Logging and Monitoring DS-Lite
Port Control Protocol for DS-Lite
Large Scale NAT64
Points to Consider for Configuring Large Scale NAT64
Configuring DNS64
Configuring Large Scaler NAT64
Configuring Application Layer Gateways for Large Scale NAT64
Configuring Static Large Scale NAT64 Maps
Logging and Monitoring Large Scale NAT64
Port Control Protocol for Large Scale NAT64
LSN64 in a cluster setup
Mapping Address and Port using Translation
Telco subscriber management
Subscriber aware traffic steering
Subscriber aware service chaining
Subscriber aware traffic steering with TCP optimization
Policy based TCP profile selection
Load Balance Control-Plane Traffic that is based on Diameter, SIP, and SMPP Protocols
Provide DNS Infrastructure/Traffic Services, such as, Load Balancing, Caching, and Logging for Telecom Service Providers
Provide Subscriber Load Distribution Using GSLB Across Core-Networks of a Telecom Service Provider
Bandwidth Utilization Using Cache Redirection Functionality
NetScaler TCP Optimization
Getting Started
Management Network
High Availability
Gi-LAN Integration
TCP Optimization Configuration
Analytics and Reporting
Real-time Statistics
Technical Recipes
Scalability
Optimizing TCP Performance using TCP Nile
Troubleshooting Guidelines
Frequently Asked Questions
NetScaler Video Optimization
Configuring Video Optimization over TCP
Video Optimization over UDP
NetScaler URL Filtering
URL Categorization
Authentication, Authorization, and Auditing
Admin Partition
Connection Management
Content Switching
Integrated Caching
Installing, Upgrading, and Downgrading
Load Balancing
NetScaler GUI
Authentication, authorization, and auditing application traffic
How authentication, authorization, and auditing works
Basic components of authentication, authorization, and auditing configuration
Authentication virtual server
Authorization policies
Authentication profiles
Authentication policies
Users and groups
Authentication methods
Multi-Factor (nFactor) authentication
SAML authentication
OAuth authentication
LDAP authentication
RADIUS authentication
TACACS authentication
Client certificate authentication
Negotiate authentication
Web authentication
Forms based authentication
401 based authentication
reCaptcha for nFactor authentication
Native OTP support for authentication
Push notification for OTP
Authentication, authorization, and auditing configuration for commonly used protocols
Single sign-on types
NetScaler Kerberos single sign-on
Enable SSO for Basic, Digest, and NTLM authentication
Content Security Policy response header support for NetScaler Gateway and authentication virtual server generated responses
Self-service password reset
Web Application Firewall protection for VPN virtual servers and authentication virtual servers
Polling during authentication
Session and traffic management
Rate Limiting for NetScaler Gateway
Authorizing user access to application resources
Auditing authenticated sessions
NetScaler as an Active Directory Federation Service proxy
Web Services Federation protocol
Active Directory Federation Service Proxy Integration Protocol compliance
On-premises NetScaler Gateway as an identity provider to Citrix Cloud
Support for active-active GSLB deployments on NetScaler Gateway
Configuration support for SameSite cookie attribute
Handling authentication, authorization and auditing with Kerberos/NTLM
Troubleshoot authentication and authorization related issues
Admin partition
NetScaler configuration support in admin partition
Configure admin partitions
VLAN configuration for admin partitions
VXLAN support for admin partitions
SNMP support for admin partitions
Audit log support for admin partitions
Display configured PMAC addresses for shared VLAN configuration
Action analytics
Configure a selector
Configure a stream identifier
View statistics
Group records on attribute values
Clear a stream session
Configure policy for optimizing traffic
How to limit bandwidth consumption for user or client device
AppExpert applications
How AppExpert application works
Customize AppExpert configuration
Configure user authentication
Monitor NetScaler statistics
Delete an AppExpert application
Configure application authentication, authorization, and auditing
Set up a custom NetScaler application
NetScaler Gateway Applications
Enable AppQoE
AppQOE actions
AppQoE parameters
AppQoE policies
Entity templates
HTTP callouts
How an HTTP callout works
Notes on the format of HTTP requests and responses
Configure an HTTP callout
Verify the configuration
Invoke an HTTP callout
Avoid HTTP callout recursion
Cache HTTP callout responses
Use Case: Filter clients by using an IP blacklist
Use Case: ESI support for fetching and updating content dynamically
Use Case: Access control and authentication
Use Case: OWA-Based spam filtering
Use Case: Dynamic content switching
Pattern sets and data sets
How string matching works with pattern sets and data sets
Configure a pattern set
Configure a data set
Use Pattern sets and data sets
Sample usage
Configure and use variables
Use case for caching user privileges
Use case for limiting the number of sessions
Policies and expressions
Introduction to policies and expressions
Configuring advanced policy infrastructure
Configure advanced policy expression: Getting started
Advanced policy expressions: Evaluating text
Advanced policy expressions: Working with dates, times, and numbers
Advanced policy expressions: Parsing HTTP, TCP, and UDP data
Advanced policy expressions: Parsing SSL certificates
Advanced policy expressions: IP and MAC Addresses, Throughput, VLAN IDs
Advanced policy expressions: Stream analytics functions
Advanced policy expressions: DataStream
Typecasting data
Regular expressions
Summary examples of advanced policy expressions
Tutorial examples of advanced policies for rewrite
Rewrite and responder policy examples
Rate limiting
Configure a stream selector
Configure a traffic rate limit identifier
Configure and bind a traffic rate policy
View the traffic rate
Test a rate-based policy
Examples of rate-based policies
Sample use cases for rate-based policies
Rate limiting for traffic domains
Configure rate limit at packet level
Enable the responder feature
Configure a responder action
Configure a responder policy
Bind a responder policy
Set the default action for a responder policy
Responder action and policy examples
Diameter support for responder
RADIUS support for responder
DNS support for the responder feature
MQTT support for responder
How to redirect HTTP requests
Content-length header behavior in a rewrite policy
Rewrite action and policy examples
URL transformation
RADIUS support for the rewrite feature
Diameter support for rewrite
DNS support for the rewrite feature
MQTT support for rewrite
String maps
Getting started
Advanced policy expressions for URL evaluation
Configure URL set
URL pattern semantics
URL categories
Configuring the AppFlow Feature
Exporting Performance Data of Web Pages to AppFlow Collector
Session Reliability on NetScaler High Availability Pair
API Security
Import API Specification
API Specification Validation
Advanced Policy Expressions using API Specification
API Traffic Visibility using API Specification Validation
Application Firewall
FAQs and Deployment Guide
Introduction to Citrix Web App Firewall
Configuring the Application Firewall
Enabling the Application Firewall
The Application Firewall Wizard
Manual Configuration
Manual Configuration By Using the GUI
Manual Configuration By Using the Command Line Interface
Manually Configuring the Signatures Feature
Adding or Removing a Signatures Object
Configuring or Modifying a Signatures Object
Protecting JSON Applications using Signatures
Updating a Signatures Object
Signature Auto Update
Snort rule integration
Exporting a Signatures Object to a File
The Signatures Editor
Signature Updates in High-Availability Deployment and Build Upgrades
Overview of Security checks
Top-Level Protections
HTML Cross-Site Scripting Check
HTML SQL Injection Checks
SQL grammar-based protection for HTML and JSON payload
Command injection grammar-based protection for HTML payload
Relaxation and deny rules for handling HTML SQL injection attacks
HTML Command Injection Protection
Custom keyword support for HTML payload
XML External Entity Protection
Buffer Overflow Check
Application Firewall Support for Google Web Toolkit
Cookie Protection
Cookie Consistency Check
Cookie Hijacking Protection
SameSite cookie attribute
Data Leak Prevention Checks
Credit Card Check
Safe Object Check
Advanced Form Protection Checks
Field Formats Check
Form Field Consistency Check
CSRF Form Tagging Check
Managing CSRF Form Tagging Check Relaxations
URL Protection Checks
Start URL Check
Deny URL Check
XML Protection Checks
XML Format Check
XML Denial-of-Service Check
XML Cross-Site Scripting Check
XML SQL Injection Check
XML Attachment Check
Web Services Interoperability Check
XML Message Validation Check
XML SOAP Fault Filtering Check
JSON Protection Checks
JSON DOS Protection
JSON SQL Protection
JSON XSS Protection
JSON Command Injection Protection
Managing Content Types
Creating Application Firewall Profiles
Enforcing HTTP RFC Compliance
Configuring Application Firewall Profiles
Application Firewall Profile Settings
Changing an Application Firewall Profile Type
Exporting and Importing an Application Firewall Profile
Detailed troubleshooting with WAF logs
File Upload Protection
Configuring and Using the Learning Feature
Dynamic Profiling
Supplemental Information about Profiles
Custom error status and message for HTML, XML, or JSON error object
Policy Labels
Firewall Policies
Auditing Policies
Importing and Exporting Files
Global Configuration
Engine Settings
Confidential Fields
Field Types
XML Content Types
JSON Content Types
Statistics and Reports
Application Firewall Logs
PCRE Character Encoding Format
Whitehat WASC Signature Types for WAF Use
Streaming Support for Request Processing
Trace HTML Requests with Security Logs
Application Firewall Support for Cluster Configurations
Debugging and Troubleshooting
Large File Upload Failure
Miscellaneous
Use case - Binding Web App Firewall policy to a VPN virtual server
Signatures Alert Articles
Signature update version 128
Signature update version 127
Signature update version 126
Signature update version 125
Signature update version 124
Signature update version 123
Signature update version 122
Signature update version 121
Signature update version 120
Signature update version 119
Signature update version 118
Signature update version 117
Signature update version 116
Signature update version 115
Signature update version 114
Signature update version 113
Signature update version 112
Signature update version 111
Signature update version 110
Signature update version 109
Signature update version 108
Signature update version 107
Signature update version 106
Signature update version 105
Bot Management
Bot detection
Configure bot profile setting
Configure bot signature setting
Bot signature auto update
Bot troubleshooting
Bot signature alert articles
Bot signature update version 5
Bot signature update version 6
Bot signature update version 7
Bot signature update version 8
Bot signature update version 9
Bot signature update version 10
Bot signature update version 11
Bot signature update version 12
Bot signature update version 13
Bot signature update version 14
Bot signature update version 15
Bot signature update version 16
Cache Redirection
Cache redirection policies
Built-in cache redirection policies
Configure a cache redirection policy
Cache redirection configurations
Configure transparent redirection
Configure forward proxy redirection
Configure reverse proxy redirection
Selective cache redirection
Enable content switching
Configure a load balancing virtual server for the cache
Configure policies for content switching
Configure precedence for policy evaluation
Administer a cache redirection virtual server
View cache redirection virtual server statistics
Enable or disable a cache redirection virtual server
Direct policy hits to the cache instead of the origin
Back up a cache redirection virtual server
Manage client connections for a virtual server
Enable external TCP health check for UDP virtual servers
N-tier cache redirection
Configure the upper-tier NetScaler appliances
Configure the lower-tier NetScaler appliances
Translate destination IP address of a request to origin IP address
NetScaler configuration support in a cluster
Cluster overview
Synchronization across cluster nodes
Striped, partially striped, and spotted configurations
Communication in a cluster setup
Traffic distribution in a cluster setup
Cluster nodegroups
Cluster and node states
Routing in a cluster
IP addressing for a cluster
Configuring layer 3 clustering
Setting up a NetScaler cluster
Setting up inter-node communication
Creating a NetScaler cluster
Adding a node to the cluster
Viewing the details of a cluster
Distributing traffic across cluster nodes
Using Equal Cost Multiple Path (ECMP)
Using cluster link aggregation
Using USIP mode in cluster
Managing the NetScaler cluster
Configuring linksets
Nodegroups for spotted and partially-striped configurations
Configuring redundancy for nodegroups
Disabling steering on the cluster backplane
Synchronizing cluster configurations
Synchronizing time across cluster nodes
Synchronizing cluster files
Viewing the statistics of a cluster
Discovering NetScaler appliances
Disabling a cluster node
Removing a cluster node
Removing a node from a cluster deployed using cluster link aggregation
Detecting jumbo probe on a cluster
Route monitoring for dynamic routes in cluster
Monitoring cluster setup using SNMP MIB with SNMP link
Monitoring command propagation failures in a cluster deployment
Graceful shutdown of nodes
Graceful shutdown of services
IPv6 ready logo support for clusters
Managing cluster heartbeat messages
Configure secure heartbeats
Configuring owner node response status
Monitor Static Route (MSR) support for inactive nodes in a spotted cluster configuration
VRRP interface binding in a single node active cluster
Cluster setup and usage scenarios
Creating a two-node cluster
Migrating an HA setup to a cluster setup
Transitioning between a L2 and L3 cluster
Setting up GSLB in a cluster
Using cache redirection in a cluster
Using L2 mode in a cluster setup
Using cluster LA channel with linksets
Backplane on LA channel
Common interfaces for client and server and dedicated interfaces for backplane
Common switch for client, server, and backplane
Common switch for client and server and dedicated switch for backplane
Different switch for every node
Sample cluster configurations
Using VRRP in a cluster setup
Monitoring services in a cluster using path monitoring
Backup and restore of cluster setup
Upgrading or downgrading the NetScaler cluster
Operations supported on individual cluster nodes
Support for heterogeneous cluster
Troubleshooting the NetScaler cluster
Tracing the packets of a NetScaler cluster
Troubleshooting common issues
Configuring Basic Content Switching
Customizing the Basic Content Switching Configuration
Content Switching for Diameter Protocol
Protecting the Content Switching Setup against Failure
Managing a Content Switching Setup
Managing Client Connections
Persistence support for content switching virtual server
Configure database users
Configure a database profile
Configure load balancing for DataStream
Configure content switching for DataStream
Configure monitors for DataStream
Use Case 1: Configure DataStream for a primary/secondary database architecture
Use Case 2: Configure the token method of load balancing for DataStream
Use Case 3: Log MSSQL transactions in transparent mode
Use Case 4: Database specific load balancing
DataStream reference
Domain Name System
Configure DNS resource records
Create SRV records for a service
Create AAAA Records for a domain name
Create address records for a domain name
Create MX records for a mail exchange server
Create NS records for an authoritative server
Create CNAME records for a subdomain
Create NAPTR records for telecommunications domain
Create PTR records for IPv4 and IPv6 addresses
Create SOA records for authoritative information
Create TXT records for holding descriptive text
Create CAA records for a domain name
View DNS statistics
Configure a DNS zone
Configure the NetScaler as an ADNS server
Configure the NetScaler as a DNS proxy server
Configure the NetScaler as an end resolver
Configure the NetScaler as a forwarder
Configure NetScaler as a non-validating security aware stub-resolver
Jumbo frames support for DNS to handle responses of large sizes
Configure DNS logging
Configure DNS suffixes
DNS ANY query
Configure negative caching of DNS records
Caching of EDNS0 client subnet data when the NetScaler appliance is in proxy mode
Domain name system security extensions
Configure DNSSEC
Configure DNSSEC when the NetScaler is authoritative for a zone
Configure DNSSEC for a zone for which the NetScaler is a DNS proxy server
Configure DNSSEC for GSLB domain names
Zone maintenance
Offload DNSSEC operations to the NetScaler
Admin partition support for DNSSEC
Support for wildcard DNS domains
Mitigate DNS DDoS attacks
Use case - configure the automatic DNSSEC key management feature
Use Case - configure the automatic DNSSEC key management on GSLB deployment
Use Case - how to revoke a compromised active key
Firewall Load Balancing
Sandwich Environment
Enterprise Environment
Multiple-Firewall Environment
Global Server Load Balancing
GSLB deployment types
Active-active site deployment
Active-passive site deployment
Parent-child topology deployment using the MEP protocol
GSLB configuration entities
GSLB methods
GSLB algorithms
Static proximity
Dynamic round trip time method
Configure static proximity
Add a location file to create a static proximity database
Add custom entries to a static proximity database
Set location qualifiers
Specify proximity method
Synchronize GSLB static proximity database
Configure site-to-site communication
Configure metrics exchange protocol
Configure GSLB by using a wizard
Configure active-active site
Configure active-passive site
Configure parent-child topology
Configure GSLB entities individually
Configure an authoritative DNS service
Configure a basic GSLB site
Configure a GSLB service
Configure a GSLB service group
Configure a GSLB virtual server
Bind GSLB services to a GSLB virtual server
Bind a domain to a GSLB virtual server
Example of a GSLB setup and configuration
Synchronize the configuration in a GSLB setup
Manual synchronization between sites participating in GSLB
Real-time synchronization between sites participating in GSLB
View GSLB synchronization status and summary
SNMP traps for GSLB configuration synchronization
GSLB dashboard
Monitor GSLB services
How domain name system works with GSLB
Priority order for GSLB services
Upgrade recommendations for GSLB deployment
Use case: Deployment of domain name based autoscale service group
Use case: Deployment of IP address based autoscale service group
How-to articles
Customize your GSLB configuration
Configure persistent connections
Manage client connections
Configure GSLB for proximity
Protect the GSLB setup against failure
Configure GSLB for disaster recovery
Override static proximity behavior by configuring preferred locations
Configure GSLB service selection using content switching
Configure GSLB for DNS queries with NAPTR records
Configure GSLB for wildcard domain
Use the EDNS0 client subnet option for GSLB
Example of a complete parent-child configuration using the metrics exchange protocol
Link Load Balancing
Configuring a Basic LLB Setup
Configuring RNAT with LLB
Configuring a Backup Route
Resilient LLB Deployment Scenario
Monitoring an LLB Setup
How load balancing works
Set up basic load balancing
Load balance virtual server and service states
Support for load balancing profile
Load balancing algorithms
Least connection method
Round robin method
Least response time method
LRTM method
Hashing methods
Least bandwidth method
Least packets method
Custom load method
Static proximity method
Token method
Least request method
Configure a load balancing method that does not include a policy
Persistence and persistent connections
About Persistence
Source IP address persistence
HTTP cookie persistence
SSL session ID persistence
Diameter AVP number persistence
Custom server ID persistence
IP address persistence
SIP Call ID persistence
RTSP session ID persistence
Configure URL passive persistence
Configure persistence based on user-defined rules
Configure persistence types that do not require a rule
Configure backup persistence
Configure persistence groups
Share persistent sessions between virtual servers
Configure RADIUS load balancing with persistence
View persistence sessions
Clear persistence sessions
Override persistence settings for overloaded services
Insert cookie attributes to ADC generated cookies
Customize a load balancing configuration
Customize the hash algorithm for persistence across virtual servers
Configure the redirection mode
Configure per-VLAN wildcarded virtual servers
Assign weights to services
Configure the MySQL and Microsoft SQL server version setting
Multi-IP virtual servers
Limit the number of concurrent requests on a client connection
Configure diameter load balancing
Configure FIX load balancing
MQTT load balancing
Protect a load balancing configuration against failure
Redirect client requests to an alternate URL
Configure a backup load balancing virtual server
Configure spillover
Connection failover
Flush the surge queue
Manage a load balancing setup
Manage server objects
Manage services
Manage a load balancing virtual server
Load balancing visualizer
Manage client traffic
Configure sessionless load balancing virtual servers
Redirect HTTP requests to a cache
Enable cleanup of virtual server connections
Rewrite ports and protocols for HTTP redirection
Insert IP address and port of a virtual server in the request header
Use a specified source IP for backend communication
Set a time-out value for idle client connections
Manage RTSP connections
Manage client traffic on the basis of traffic rate
Identify a connection with layer 2 parameters
Configure the prefer direct route option
Use a source port from a specified port range for backend communication
Configure source IP persistency for backend communication
Use IPv6 link local addresses on server side of a load balancing setup
Advanced load balancing settings
Gradually stepping up the load on a new service with virtual server–level slow start
The no-monitor option for services
Protect applications on protected servers against traffic surges
Enable cleanup of virtual server and service connections
Enable or disable persistence session on TROFS services
Direct requests to a custom web page
Enable access to services when down
Enable TCP buffering of responses
Enable compression
Maintain client connection for multiple client requests
Insert the IP address of the client in the request header
Retrieve location details from user IP address using geolocation database
Use source IP address of the client when connecting to the server
Use client source IP address for backend communication in a v4-v6 load balancing configuration
Configure the source port for server-side connections
Set a limit on the number of client connections
Set a limit on number of requests per connection to the server
Set a threshold value for the monitors bound to a service
Set a timeout value for idle client connections
Set a timeout value for idle server connections
Set a limit on the bandwidth usage by clients
Redirect client requests to a cache
Retain the VLAN identifier for VLAN transparency
Configure automatic state transition based on percentage health of bound services
Static proximity based on NetScaler location
Built-in monitors
TCP-based application monitoring
SSL service monitoring
HTTP/2 service monitoring
Proxy protocol service monitoring
FTP service monitoring
Secure monitoring of servers by using SFTP
Set SSL parameters on a secure monitor
SIP service monitoring
RADIUS service monitoring
Monitor accounting information delivery from a RADIUS server
DNS and DNS-TCP service monitoring
LDAP service monitoring
MySQL service monitoring
SNMP service monitoring
NNTP service monitoring
POP3 service monitoring
SMTP service monitoring
RTSP service monitoring
ARP request monitoring
Citrix Virtual Desktops Delivery Controller service monitoring
Citrix StoreFront stores monitoring
Oracle ECV service monitoring
Custom monitors
Configure HTTP-inline monitors
Understand user monitors
How to use a user monitor to check web sites
Understand the internal dispatcher
Configure a user monitor
Understand load monitors
Configure load monitors
Unbind metrics from a metrics table
Configure reverse monitoring for a service
Configure monitors in a load balancing setup
Create monitors
Configure monitor parameters to determine the service health
Bind monitors to services
Modify monitors
Enable and disable monitors
Unbind monitors
Remove monitors
View monitors
Close monitor connections
Ignore the upper limit on client connections for monitor probes
Manage a large scale deployment
Ranges of virtual servers and services
Configure service groups
Manage service groups
Configure a desired set of service group members for a service group in one NITRO API call
Configure automatic domain based service group scaling
Service discovery using DNS SRV records
Translate the IP address of a domain-based server
Mask a virtual server IP address
Configure load balancing for commonly used protocols
Load balance a group of FTP servers
Load balance DNS servers
Load balance domain-name based services
Load balance a group of SIP servers
Load balance RTSP servers
Load balance remote desktop protocol (RDP) servers
Priority order for load balancing services
Use case 1: SMPP load balancing
Use case 2: Configure rule based persistence based on a name-value pair in a TCP byte stream
Use case 3: Configure load balancing in direct server return mode
Use case 4: Configure LINUX servers in DSR mode
Use case 5: Configure DSR mode when using TOS
Use case 6: Configure load balancing in DSR mode for IPv6 networks by using the TOS field
Use case 7: Configure load balancing in DSR mode by using IP Over IP
Use case 8: Configure load balancing in one-arm mode
Use case 9: Configure load balancing in the inline mode
Use case 10: Load balancing of intrusion detection system servers
Use case 11: Isolating network traffic using listen policies
Use case 12: Configure Citrix Virtual Desktops for load balancing
Use case 13: Configure Citrix Virtual Apps and Desktops for load balancing
Use case 14: ShareFile wizard for load balancing Citrix ShareFile
Use case 15: Configure layer 4 load balancing on the NetScaler appliance
Load balancing FAQs
IP Addressing
Configuring NetScaler-Owned IP Addresses
How the NetScaler Proxies Connections
Enabling Use Source IP Mode
Configuring Network Address Translation
Configuring Static ARP
Setting the Timeout for Dynamic ARP Entries
Configuring Neighbor Discovery
Configuring IP Tunnels
Class E IPv4 packets
Monitor the free ports available on a NetScaler appliance for a new back-end connection
Configuring MAC-Based Forwarding
Configuring Network Interfaces
Configuring Forwarding Session Rules
Understanding VLANs
Configuring a VLAN
Configuring NSVLAN
Configuring Allowed VLAN List
Configuring Bridge Groups
Configuring Virtual MACs
Configuring Link Aggregation
Redundant Interface Set
Binding an SNIP address to an Interface
Monitoring the Bridge Table and Changing the Aging time
NetScaler Appliances in Active-Active Mode Using VRRP
Using the Network Visualizer
Configuring Link Layer Discovery Protocol
Jumbo Frames
NetScaler Support for Microsoft Direct Access Deployment
Access Control Lists
Simple ACLs and Simple ACL6s
Extended ACLs and Extended ACL6s
MAC Address Wildcard Mask for ACLs
Blocking Traffic on Internal Ports
Configuring Dynamic Routes
Configuring Static Routes
Route Health Injection Based on Virtual Server Settings
Configuring Policy-Based Routes
Traffic distribution in multiple routes based on five tuples information
Troubleshooting Routing Issues
Internet Protocol version 6 (IPv6)
Traffic Domains
Inter Traffic Domain Entity Bindings
Virtual MAC Based Traffic Domains
Geneve tunnels
Best practices for networking configurations
Configure to source NetScaler FreeBSD data traffic from a SNIP address
Observability
Integration with Prometheus
Monitor NetScaler and applications using Prometheus
Integration with Splunk
Export metrics directly from NetScaler to Splunk
Export transaction logs directly from NetScaler to Splunk
Export management logs directly from NetScaler to Splunk
Export audit logs and events directly from NetScaler to Splunk
Integration with Elasticsearch
Export transaction logs directly from NetScaler to Elasticsearch
NetScaler advanced analytics
Sample dashboards for endpoints
Sample dashboards on Grafana
Sample dashboards on Splunk
NetScaler metrics reference
Priority Load Balancing
NetScaler Extensions
NetScaler extensions - language overview
Simple types
Expressions
Control structures
NetScaler extensions - library reference
NetScaler extensions API reference
Protocol extensions
Protocol extensions - architecture
Protocol extensions - traffic pipeline for user defined TCP client and server behaviors
Protocol extensions - use cases
Tutorial – Add MQTT protocol to the NetScaler appliance by using protocol extensions
Tutorial - Load balancing syslog messages by using protocol extensions
Protocol extensions command reference
Troubleshoot protocol extensions
Policy extensions
Configure policy extensions
Policy extensions - use cases
Troubleshooting policy extensions
Optimization
Client Keep-Alive
HTTP Compression
Configure selectors and basic content groups
Configure policies for caching and invalidation
Cache support for database protocols
Configure expressions for caching policies and selectors
Display cached objects and cache statistics
Improve cache performance
Configure cookies, headers, and polling
Configure integrated cache as a forward proxy
Default Settings for the Integrated Cache
Front End Optimization
Media Classification
IP Reputation
SSL offload and acceleration
SSL offloading configuration
Support for TLS 1.3 protocol
SSL certificates
Create a certificate
Install, link, and update certificates
Generate a server test certificate
Import and convert SSL files
Bind an SSL certificate to a virtual server on the NetScaler appliance
SSL profiles
SSL profile infrastructure
Secure front-end profile
Appendix A: Sample migration of the SSL configuration after upgrade
Appendix B: Default front-end and back-end SSL profile settings
Legacy SSL profile
Migrate the SSL configuration to the enhanced SSL profile
Certificate revocation lists
Monitor certificate status with OCSP
OCSP stapling
Ciphers available on the NetScaler appliances
ECDHE ciphers
Diffie-Hellman (DH) key generation and achieving PFS with DHE
Cipher redirection
Leverage hardware and software to improve ECDHE and ECDSA cipher performance
ECDSA cipher suites support
Configure user-defined cipher groups on the ADC appliance
Server certificate support matrix on the ADC appliance
Client authentication
Server authentication
SSL actions and policies
SSL policies
SSL built-in actions and user-defined actions
SSL policy binding
SSL policy labels
Selective SSL logging
Support for DTLS protocol
Support for Intel Coleto SSL chip based platforms
MPX 14000 FIPS appliances
SDX 14000 FIPS appliances
- Limitations
Terminology
Initialize the HSM
Create partitions
Provision a new instance or modify an existing instance and assign a partition
Configure the HSM for an instance on an SDX 14030/14060/14080 FIPS appliance
Create a FIPS key for an instance on an SDX 14030/14060/14080 FIPS appliance
Upgrade the FIPS firmware on a VPX instance
Support for Thales Luna Network hardware security module
Configure a Thales Luna client on the ADC
Configure Thales Luna HSMs in a high availability setup on the ADC
Additional ADC configuration
NetScaler appliances in a high availability setup
Support for Azure Key Vault
Content inspection
ICAP for remote content inspection
Inline Device Integration with NetScaler
Integration with IPS or NGFW as inline devices
IDS Integration
IDS Layer 3 Integration
Content Inspection Statistics for ICAP, IPS, and IDS
SSL forward proxy
Getting started with SSL forward proxy
Proxy modes
SSL interception
User identity management
URL filtering for SSL forward proxy
URL categorization
URL reputation score
Analytics for SSL forward proxy
Using ICAP for remote content inspection
Surge protection
Disable and reenable surge protection
Set thresholds for surge protection
DNS security options
Basic operations
Unified configuration file
Authentication and authorization for System Users
Configuring Users, User Groups, and Command Policies
User Account and Password Management
Resetting the Default Administrator (nsroot) Password
Configuring External User Authentication
SSH Key-based Authentication for NetScaler Administrators
Two Factor Authentication for System Users
Restricted Management Interface Access
TCP Configurations
HTTP Configurations
Configuring HTTP/2 on the NetScaler Appliance
HTTP/2 DoS mitigation
HTTP/3 over QUIC
HTTP/3 Configuration
HTTP/3 Policy Configuration
HTTP/3 Service Discovery
gRPC End-to-End Configuration
gRPC Bridging
gRPC Reverse Bridging
gRPC Call Termination
gRPC with Rewrite Policy Configuration
gRPC with Responder Policy Configuration
gRPC Health Monitor
QUIC bridge configuration
Proxy Protocol
Client IP Address in TCP Option
Configuring the NetScaler to Generate SNMP Traps
Configuring the NetScaler for SNMP v1 and v2 Queries
Configuring the NetScaler for SNMPv3 Queries
Configuring SNMP Alarms for Rate Limiting
Configuring SNMP in FIPS Mode
Audit Logging
Configuring the NetScaler Appliance for Audit Logging
Installing and Configuring the NSLOG Server
Running the NSLOG Server
Customizing Logging on the NSLOG Server
SYSLOG Over TCP
Default Settings for the Log Properties
Sample Configuration File (audit.conf)
Web Server Logging
Configuring the NetScaler for Web Server Logging
Installing the NetScaler Web Logging (NSWL) Client
Configuring the NSWL Client
Customizing Logging on the NSWL Client System
Reporting Tool
CloudBridge Connector
Monitoring CloudBridge Connector Tunnels
Configuring a CloudBridge Connector Tunnel between two Datacenters
Configuring CloudBridge Connector between Datacenter and AWS Cloud
Configuring a CloudBridge Connector Tunnel Between a NetScaler Appliance and Virtual Private Gateway on AWS
Configuring a CloudBridge Connector Tunnel Between a Datacenter and Azure Cloud
Configuring CloudBridge Connector Tunnel between Datacenter and SoftLayer Enterprise Cloud
Configuring a CloudBridge Connector Tunnel Between a NetScaler Appliance and Cisco IOS Device
Configuring a CloudBridge Connector Tunnel Between a NetScaler Appliance and Fortinet FortiGate Appliance
CloudBridge Connector Tunnel Diagnostics and Troubleshooting
CloudBridge Connector Interoperability – StrongSwan
CloudBridge Connector Interoperability – F5 BIG-IP
CloudBridge Connector Interoperability – Cisco ASA
Points to Consider for a High Availability Setup
Configuring High Availability
Configuring the Communication Intervals
Configuring Synchronization
Synchronizing Configuration Files in a High Availability Setup
Configuring Command Propagation
Restricting High-Availability Synchronization Traffic to a VLAN
Configuring Fail-Safe Mode
Configuring Virtual MAC Addresses
Configuring High Availability Nodes in Different Subnets
Configuring Route Monitors
Limiting Failovers Caused by Route Monitors in non-INC mode
Configuring Failover Interface Set
Understanding the Causes of Failover
Forcing a Node to Fail Over
Forcing the Secondary Node to Stay Secondary
Forcing the Primary Node to Stay Primary
High Availability FAQs
Troubleshooting High Availability Issues
Managing High Availability Heartbeat Messages on a NetScaler Appliance
Remove and Replace a NetScaler in a High Availability Setup
Request retry
Request retry if back-end server resets TCP connection
Request retry if back-end server resets TCP connection during connection establishment
Request retry if back-end server response times out
TCP Optimization
How to record a packet trace on NetScaler
How to free space on /var directory
How to download core or crashed files from NetScaler appliance
How to collect performance statistics and event logs
How to configure log file rotation
How to free space on /flash directory
Reference Material
Document History
This content has been machine translated dynamically.
Dieser Inhalt ist eine maschinelle Übersetzung, die dynamisch erstellt wurde. (Haftungsausschluss)
Cet article a été traduit automatiquement de manière dynamique. (Clause de non responsabilité)
Este artículo lo ha traducido una máquina de forma dinámica. (Aviso legal)
此内容已经过机器动态翻译。 放弃
このコンテンツは動的に機械翻訳されています。 免責事項
이 콘텐츠는 동적으로 기계 번역되었습니다. 책임 부인
Este texto foi traduzido automaticamente. (Aviso legal)
Questo contenuto è stato tradotto dinamicamente con traduzione automatica. (Esclusione di responsabilità))
This article has been machine translated.
Dieser Artikel wurde maschinell übersetzt. (Haftungsausschluss)
Ce article a été traduit automatiquement. (Clause de non responsabilité)
Este artículo ha sido traducido automáticamente. (Aviso legal)
この記事は機械翻訳されています. 免責事項
이 기사는 기계 번역되었습니다. 책임 부인
Este artigo foi traduzido automaticamente. (Aviso legal)
这篇文章已经过机器翻译. 放弃
Questo articolo è stato tradotto automaticamente. (Esclusione di responsabilità))
Translation failed!
Configure a NetScaler VPX on ESX hypervisor to use Intel QAT for SSL acceleration in SR-IOV mode
The NetScaler VPX instance on the VMware ESX hypervisor can use the Intel QuickAssist Technology (QAT) to accelerate the NetScaler SSL performance. Using Intel QAT, all heavy-latency crypto processing can be offloaded to the chip thus freeing up one or more host CPUs to do other tasks.
Previously, all NetScaler data path crypto processing was done in the software using host vCPUs.
Note: Currently, NetScaler VPX supports only the C62x chip model under Intel QAT family. This feature is supported starting from NetScaler release 14.1 build 8.50.
- The ESX host is provisioned with one or more Intel C62x (QAT) chips.
- NetScaler VPX meets the VMware ESX hardware requirements. For more information, see Install a NetScaler VPX instance on VMware ESX .
There’s no provision to reserve crypto units or bandwidth for individual VMs. All the available crypto units of any Intel QAT hardware are shared across all VMs using the QAT hardware.
- Set up the host environment for using Intel QAT
Download and install the Intel-provided VMware driver for the C62x series (QAT) chip model in the VMware host. For more information on the Intel package downloads and installation instructions, see Intel QuickAssist Technology Driver for VMware .
Enable SR-IOV on the ESX host.
Create virtual machines. When creating a VM, assign the appropriate number of PCI devices to meet the performance requirements.
Note: Each C62x (QAT) chip can have up to three separate PCI endpoints. Each endpoint is a logical collection of VFs, and shares the bandwidth equally with other PCI endpoints of the chip. Each endpoint can have up to 16 VFs that show up as 16 PCI devices. You can add these devices to the VM to do the crypto acceleration using the QAT chip.
- Points to note
- If the VM crypto requirement is to use more than one QAT PCI endpoint/chip, it’s recommended to pick the corresponding PCI devices/VFs in a round-robin fashion to have a symmetric distribution.
It’s recommended that the number of PCI devices picked is equal to the number of licensed vCPUs (without including the management vCPU count). Adding more PCI devices than the available number of vCPUs does not necessarily improve the performance.
Consider an ESX host with one Intel C62x chip that has 3 endpoints. While provisioning a VM with 6 vCPUs, pick 2 VFs from each endpoint, and assign them to the VM. This kind of assignment ensures an effective and equal distribution of crypto units for the VM. From the total available vCPUs, by default, one vCPU is reserved for the management plane, and the rest of the vCPUs are available for the data plane PEs.
- Assign QAT VFs to VPX using the vSphere web client
In the vSphere web client, navigate to the ESX host where the virtual machine is located and click Power off .
Navigate to Actions > Edit settings > Add other device , and select PCI device.
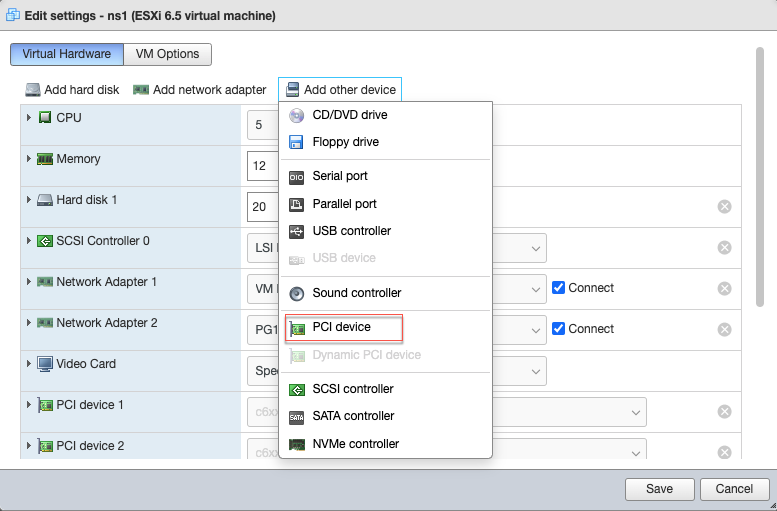
For the newly added PCI device, assign the c6xx QAT VF, and save the configuration.
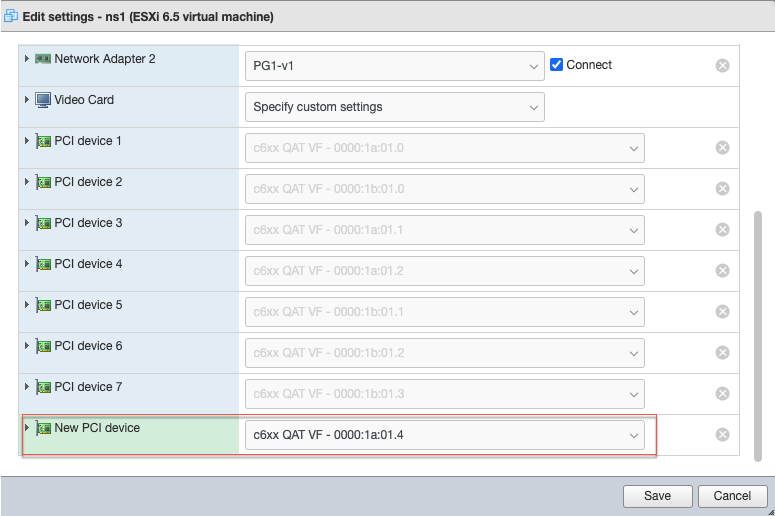
Power on the VM again.
Run the stat ssl command in the NetScaler CLI to display the SSL summary, and verify the SSL cards after assigning QAT VFs to VPX.

- About the deployment
This deployment was tested with the following component specifications:
- NetScaler VPX version and build: 14.1–8.50
- VMware ESXi version: 7.0.3 (build 20036589)
- Intel C62x QAT driver version for VMware: 1.5.1.54
In this article
This Preview product documentation is Cloud Software Group Confidential.
You agree to hold this documentation confidential pursuant to the terms of your Cloud Software Group Beta/Tech Preview Agreement.
The development, release and timing of any features or functionality described in the Preview documentation remains at our sole discretion and are subject to change without notice or consultation.
The documentation is for informational purposes only and is not a commitment, promise or legal obligation to deliver any material, code or functionality and should not be relied upon in making Cloud Software Group product purchase decisions.
If you do not agree, select I DO NOT AGREE to exit.
Machine Translation Feedback Form
Do you want to switch to the website in your browser preferred language?
Edit Article

IMAGES
VIDEO
COMMENTS
Change the item's IP address. Type in sudo ifconfig name ipaddress netmask 255.255.255. up—making sure to replace name with your item's name and ipaddress with your preferred IP address—and press ↵ Enter.. To assign an IP of "192.168.2.100" to your ethernet connection ("eth0"), for example, you'd enter sudo ifconfig eth0 192.168..100 netmask 255.255.255. here.
The ip command has replaced the older ifconfig command in modern versions of Linux. The ip command allows you to configure IP addresses, network interfaces, and routing rules on the fly without rebooting. Run "ip addr" in the Terminal to get your PC's local IP address. You can configure IP addresses, network interfaces, and routing rules on the ...
In this tutorial, we look at standard low-level files and tools to configure our IP address settings. We start off by briefly discussing dynamic and static addresses. After picking static IP network configuration as an example, we look at a universal way to perform it under Linux. Next, we explore network managers in detail.
The ip command is available on most Linux distributions. For setting an IP address, use it like this: ip addr add [ip_address] dev [interface] For example, add an IP address to the eth1 interface as: sudo ip addr add 192.168.56.21/24 dev eth1. You now have two IP addresses: one from the old configuration and one from the new command:
Unlike desktop machines where you can use dynamic IP addresses, on a server infrastructure, you will need to setup a static IP address (at least in most cases). Read Also: How to Set or Change System Hostname in Linux</p. This article is meant to show you how to configure static IP address on most frequently used Linux distributions.
Method 2: Switch to static IP address in Ubuntu graphically. If you are on desktop, using the graphical method is easier and faster. Go to the settings and look for network settings. Click the gear symbol adjacent to your network connection. Next, you should go to the IPv4 tab.
Set a Static IP in Ubuntu with the GUI. Click the icons at the far-right end of the system bar to show the system menu, then click on the "Wired Connected" menu option. If you're using a wireless connection, instead click the name of your Wi-Fi network. The available connections are displayed.
For example, to bring the interface eth0 online, you would type:. ip link set eth0 up. And to bring if offline. ip link set eth0 down Displaying and Altering the Routing Table #. To assign, remove, and display the kernel routing table use the route object. The most commonly used commands when working with the routes objects are: list, add, and del. Display routing table #
To assign an IP address to a specific network interface, use the addr add flag as shown here: sudo ip addr add <IP/subnet> dev <Interface>. For example, here, I added 192.168.1.100/24 IP address for the enp1s0 interface: sudo ip addr add 192.168.1.100/24 dev enp1s0.
Depending on the interface you want to modify, click either on the Network or Wi-Fi tab. To open the interface settings, click on the cog icon next to the interface name. In "IPV4" Method" tab, select "Manual" and enter your static IP address, Netmask and Gateway. Once done, click on the "Apply" button.
To change your IP address on Linux, use the "ifconfig" command followed by the name of your network interface and the new IP address to be changed on your computer. To assign the subnet mask, you can either add a "netmask" clause followed by the subnet mask or use the CIDR notation directly.
dns-nameservers 192.168.2.1 8.8.8.8. In this configuration, 192.168.2.150 will be our new IPv4 address with a netmask or network subnet of 255.255.255.. The default gateway, which also happens to be the router's IP, is 192.168.2.1 while the DNS nameservers are 192.168.2.1 and 8.8.8.8. Set Static IP Address in Debian.
Configuring IP addresses and routes from the command line is a mandatory skill that every Linux administrator should learn. In this article, we will review how we can assign a static IP address using ip and ifconfig commands.. In addition, we will discuss how we can use the ip route command to create a static route to change the default gateway for the Linux system.
To assign IPv6 address using ip command you can use the same command as used for IPv4 address but with the IPv6 address and netmask. bash. # ip addr add 2001:0001:0001:1443::0411/122 dev eno55. Verify the IPv6 address assigned to the provided interface. bash.
Query the status of a IP interface. 3. Configure the local loop-back, Ethernet and other IP interfaces. 4. Mark the interface as up or down. 5. Configure and modify default and static routing. 6. Set up tunnel over IP. 7. Show ARP or NDISC cache entry. 8. Assign, delete, set up IP address, routes, subnet and other IP information to IP ...
With the ifconfig command, you can assign an IP address and netmask to a network interface. Use the following syntax to assign the IP address and netmask: ifconfig [interface-name] [ip-address] netmask [subnet-mask] For example, to assign the IP address 192.168..101 and netmask 255.255.. to the interface eth0, you would run:
As the ip utility supports assigning multiple addresses to the same interface it is no longer necessary to use the alias interface method of binding multiple addresses to the same interface. The ip command to assign an address can be repeated multiple times in order to assign multiple address. For example: ~]# ip address add 192.168.2.223/24 dev enp1s0 ~]# ip address add 192.168.4.223/24 dev ...
To change the IP address of the "enp1s0" interface with a direct nmcli command, we run: $ sudo nmcli connection modify enp1s0 IPv4.address 192.168.122.66/24. Notice that we specified the routing prefix together with the IP using the so called CIDR notation (Classes Inter-Domain Routing). We use a similar syntax to change the gateway and the ...
Write the IP address you wish to assign your computer along with the network prefix. So I will write 192.168.122.128/24 in the addresses field. Finally, we also need to specify DNS nameservers. For that, create a new field called nameservers and under that, create a field called addresses which contains the IP address for your DNS servers. I ...
Example 1: Bringing an Interface Up. To bring an interface up (activate it), you can use the `ip link` command with the `set` action. For example: sudo ip link set eth0 up. This command brings the `eth0` interface up, enabling it to send and receive network traffic.
NAME=eth0. DEVICE=eth0. ONBOOT=yes // starts on boot. You can then apply this configuration by running: /etc/init.d/network restart. Ok, that will get you up and running with a static IP on the two most common Linux distros. Now let's take a deeper look at the new ip command.
Verify new IP settings using the ip command for the NIC named eth0: # ip a s eth0 Verify new routing settings: # ip r Next, verify DNS servers settings using the cat command or grep command to query the /etc/resolv.conf file as follows: # cat /etc/resolv.conf Finally verify the internet connectivity using the ping command: # ping -c 3 cyberciti ...
When you want a persistent IP address on your Ubuntu 24.04 desktop, then you must a configure a static IP address. Whenever we install Ubuntu then DHCP is enabled by default, and it will try to fetch the IP address from DHCP server if it is available over the network. In Ubuntu Desktop 24.04, there are two ways to configure static IP address:
IP aliasing in Linux allows assigning multiple IP addresses to a single network interface. ... We'll then configure eth0 to obtain IP addresses through DHCP for internet access and eth1 as a private network. In this tutorial, we'll use three computers: a Linux machine as the router, a Linux machine as the first client, and a Windows machine ...
While it's not strictly necessary, having a static IP makes it easier to connect consistently, as the address won't change each time the server restarts. Summary. Check firewall settings for SSH connections. Install and configure an SSH server. Set up port forwarding on your router. Connect from a remote client using your server's public IP.
Change the system hostname. If you have a public DNS name registered for the IP address of your instance (such as webserver.mydomain.com), you can set the system hostname so your instance identifies itself as a part of that domain.This also changes the shell prompt so that it displays the first portion of this name instead of the hostname supplied by AWS (for example, ip-12-34-56-78).
Steps to Configure IP Addresses in Linux VPS. The process of Adding additional IPv4 and IPv6 addresses involves obtaining the IPs from your VPS provider's control panel and configuring your network settings. This typically involves steps like logging into the control panel, requesting additional IPs, and then updating your Linux system's ...
Firewall rules, defined by access control lists (ACLs), control traffic based on IP addresses, port numbers, and protocols. To maximize security, thoroughly test configurations, including advanced ...
The legacy versions of the Compose file reference has moved to the V1 branch of the Compose repository.They are no longer being actively maintained. The latest and recommended version of the Compose file format is defined by the Compose Specification.This format merges the 2.x and 3.x versions and is implemented by Compose 1.27.0+.For more information, see the History and development of Docker ...
Insert the IP address of the client in the request header . Retrieve location details from user IP address using geolocation database . Use source IP address of the client when connecting to the server . Use client source IP address for backend communication in a v4-v6 load balancing configuration . Configure the source port for server-side ...