techlauve.com – a knowledge base for IT professionals.
Inhale problems, exhale solutions..
- Nick’s Blog
- Active Directory
- Privacy Policy
« Outlook: “Sending and Receiving reported error (OX80040600)”
Terminal Server Does Not Accept Enough Client Connections »

Adding Sites to Internet Security Zones Using Group Policy
Sometimes it is useful to leverage the power of Group Policy in Active Directory to add sites to certain security zones in Internet Explorer. This can save the network admin the trouble of managing the security zone lists for each computer (or user) separately. In the following example, each user on the network needs to have a specific site added to the Trusted Sites list.
This tutorial assumes that group policy is in good working order on the domain and that all client users and computers can access the directory.
- Open the Group Policy Management MMC console.
- Right-click the organization unit (OU) that the policy should apply to, taking special care to consider whether the policy should apply to computers or users on this particular network.
- Select “Create and Link a GPO Here…” to create a new group policy object.
- In the “New GPO” window, enter a good, descriptive name for this new policy and click “OK”. (ex. “Trusted Sites Zone – Users” or something even more descriptive)
- Locate the newly created GPO in the left-side navigation pane, right-click it and select “Edit…”
- Expand “Administrative Templates” under either “Computer Configuration” or “User Configuration” depending on which type of OU the new policy was linked to in step 2.
- The path to the settings that this example will be using is: Administrative Templates -- Windows Components -- Internet Explorer -- Internet Control Panel -- Security Page
- In the right-hand pane, double-click “Site to Zone Assignment List”.
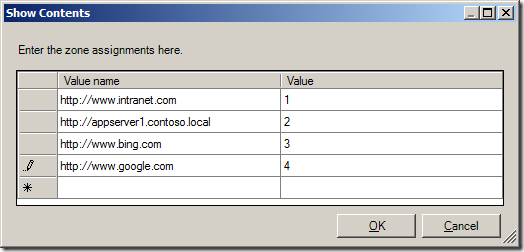
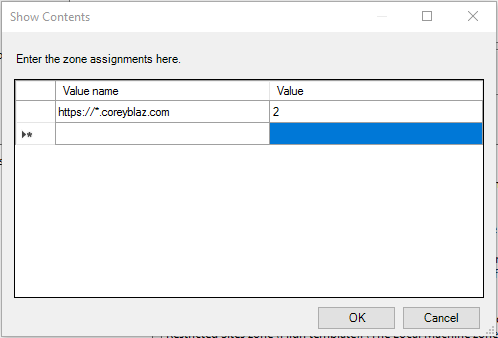
- Enable the policy and click the “Show…” button next to “Enter the zone assignments here.” This will pop up the “Show Contents” window.
- Click the “Add…” button. This will pop up the “Add Item” window.
- In the first box, labeled “Enter the name of the item to be added:”, enter the URL to the site. (ex. https://secure.ourimportantwebapp.com) . Keep in mind that wildcards can be used. (ex. https://*.ourimportantdomain.com) . Leave off any trailing slashes or sub-folders unless that type of specific control is called for.
- 1 – Intranet Zone
- 2 – Trusted Sites Zone
- 3 – Internet Zone
- 4 – Restricted Sites Zone
- Once the zone assignment has been entered, click “OK”. This will once again show the “Show Contents” window and the new entry should be present.
- Click “OK” and “OK” again to get back to the Group Policy Management Console.
The new policy will take effect at the next group policy refresh interval, which is usually 15 minutes. To test immediately, run a gpupdate /force on a user/computer that falls into the scope of the new policy and go to “Tools -> Internet Options -> Security -> Trusted Sites -> Sites”. The site(s) added should be in the list. If the sites do not show up, check the event logs for any group policy processing errors.
Related content:
- How To: Time Sync Across Windows Network
- Group Policy Not Applied To Remote VPN Users
- QuickBooks Payroll Opens/Saves the Wrong W2 Form
- Microsoft Virtual Server Web Console Constantly Asks For Password
- Group Policy: Applying Different User Policies to the Same User for Workstations and Terminal Server
No comment yet
Juicer breville says:.
November 26, 2012 at 12:11 am (UTC -5)
Hurrah, that’s what I was looking for, what a information! existing here at this web site, thanks admin of this web page.
Leave a Reply Cancel reply
Your email address will not be published.
You may use these HTML tags and attributes: <a href="" title=""> <abbr title=""> <acronym title=""> <b> <blockquote cite=""> <cite> <code> <del datetime=""> <em> <i> <q cite=""> <s> <strike> <strong>
Submit Comment
This site uses Akismet to reduce spam. Learn how your comment data is processed .
Remember Me
Connect With Us
Connect with us.
Social Connect by NewsPress
Not finding the answer that you're looking for? Need more help with a problem that is addressed in one of our articles?
techlauve.com is affiliated with Rent-A-Nerd, Inc. in New Orleans, LA.
- DFS Replication (1)
- Group Policy (1)
- Microsoft Exhange (3)
- Microsoft Outlook (11)
- Copiers (1)
- Multi Function Devices (1)
- Printers (2)
- Scanners (1)
- Blackberry (1)
- Firewalls (2)
- Wireless (2)
- Hard Drives (1)
- SAN Systems (1)
- Hyper-V (3)
- Virtual Server (1)
- WordPress (1)
- Security (7)
- QuickBooks (2)
- Quicken (1)
- Antivirus/Antimalware (4)
- Backup Exec (2)
- Internet Explorer (5)
- Microsoft SQL (1)
- Licensing (2)
- Steinberg Nuendo (1)
- Mac OS X (1)
- Server 2003 (12)
- Server 2008 (14)
- Small Business Server 2003 (7)
- Terminal Server (6)
- Updates (2)
- Windows 7 (9)
- Windows XP (11)
- Reviews (1)
- Rent-A-Nerd, Inc.
Except where otherwise noted, content on this site is licensed under a Creative Commons Licence .
Valid XHTML 1.0 Strict Valid CSS Level 2.1
techlauve.com - a knowledge base for IT professionals. uses Graphene theme by Syahir Hakim.
Group Policy Central
News, Tips and Tutorials for all your Group Policy needss
How to use Group Policy to configure Internet Explorer security zone sites
As you know Group Policy Preferences are these fantastic new settings that allow IT administrators perform any configuration they want on a users group using Group Policy… well almost.. In this tutorial I will show you how to configured one of the few settings that are not controlled by preferences but can be configured using a native Group Policy.
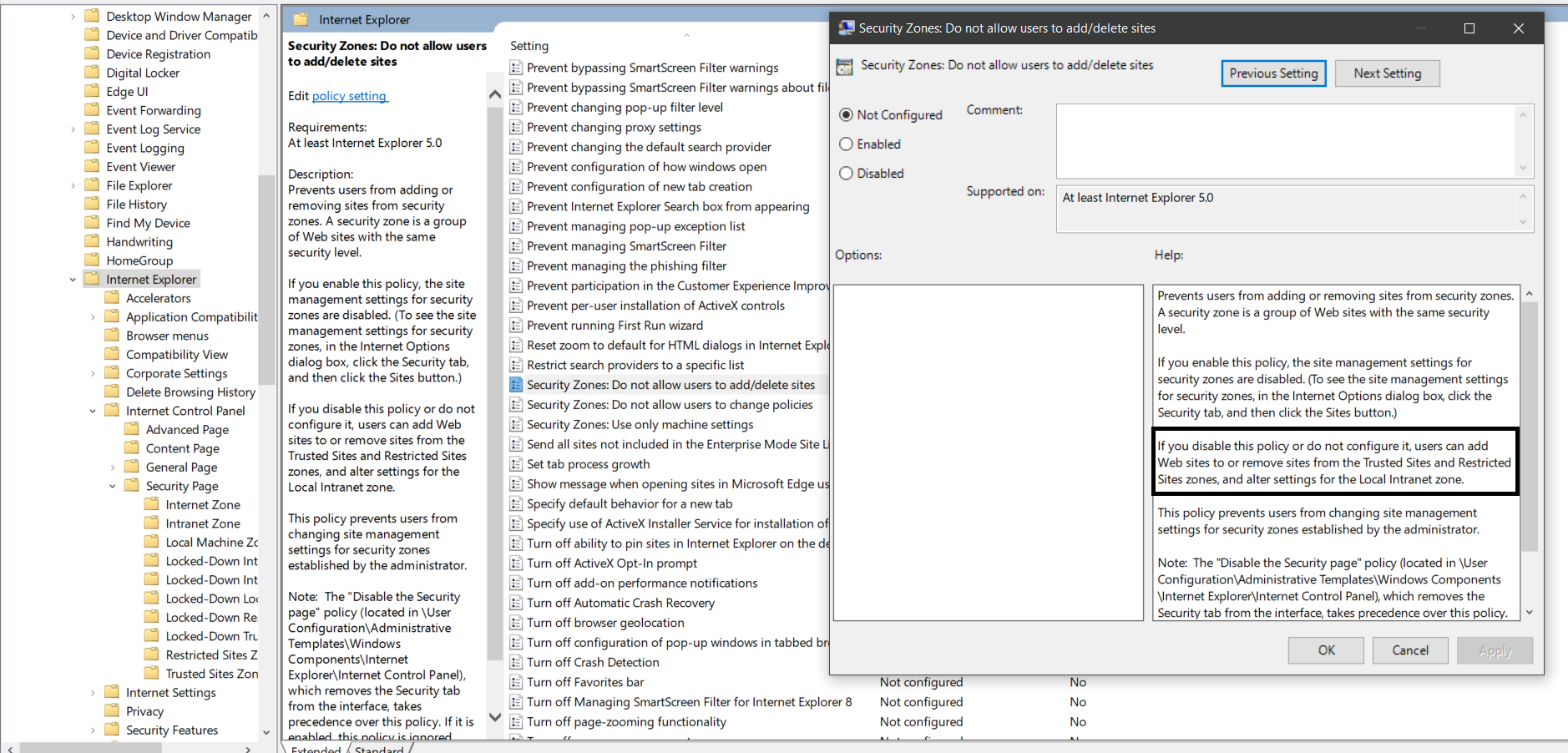
The Internet Explore site zone assignment is one of the few settings you specifically can’t configured using preferences, as you can see (image below) the User Interface to this options has been disabled.
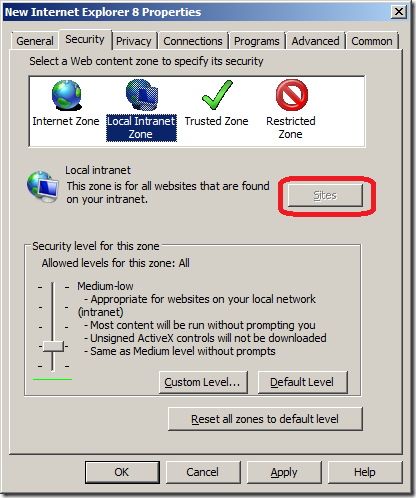
There is a native Group Policy that allows you to control Internet Explorer site zone list is called “Site to Zone Assignment List†which I will go thought below how to use.
Step 1. Edit the Group Policy Object that is targeted to the users you whish this setting to be applied.
Step 2 . Navigate to User Configuration > Administrative Templates > Windows Components > Internet Explorer > Internet Control Panel > Security Page and double click on the “Site to Zone Assignment List†and check the “Enable†option then click on the “Show..†button.
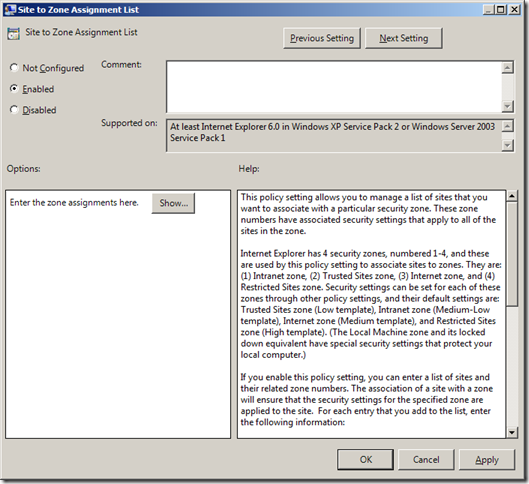
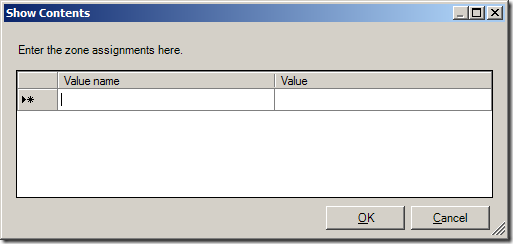
Step 3. Now type the URL in the “Value name†field with the >* on the far left and then type the zone number (see table below) you want to assign to that zone.
Internet Explorer Group Policy Zone Number Mapping
As soon as you start typing the URL a new line will appear for the next URL.
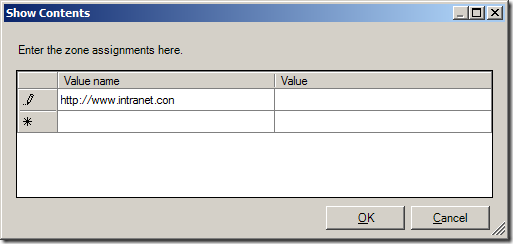
Step 4. One you have finished assigning adding the URL’s and site zone number click OK
Tip: If you want to delete a row click on the button on the far left to select the row you want to delete (see image below) and then press the “Delete†key.
(sites in above list are example only)
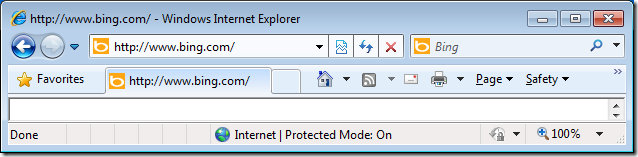
Now the Internet Explorer Site zone list will now be populated with the zone you configured above and as you can see in the images below the Internet Explorer status bar now show the correct zone based on the that the URL’s in the address bar.
Author: Alan Burchill
Related articles.

34 thoughts on “ How to use Group Policy to configure Internet Explorer security zone sites ”
Blog Post: How to use Group Policy to configure Internet Explorer security zone sites http://bit.ly/bNHowK
How to use Group Policy to configure Internet Explorer security zone sites http://bit.ly/bNHowK
- Pingback: Group Policy Center » Blog Archive » Group Policy Setting of the Week 18 – Allow file downlaod (Internet Explorer)
- Pingback: Group Policy Center » Blog Archive » How to use Group Policy to mitigate security issue KB981374
Yup, that is right and excately how we do it, however there is one problem that is of slight concern 🙁
Once the Zones are set via this GP the user can not add his own and as banks etc. today rely on Trusted Zones this is a slight problem. Our IT policy allow for users to use their PC for personal business as well as work and thus it is a slight problem that they cant add Zones for eg. their bank etc.
I have been thinking, maybe one could make a script to set Zones and deploy this via SCCM 2007.
I have not tried this for a while but i believe you can still do this if you configure it under the Internet Explorer Maintainence section of Group Policy…
The configuration for regular zones works fine. Bu the real pain starts when trying to cover zones for “Enahanced Security Configuration” which require other hives in the registry (e.g. “HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap\ESCDomains\MyDomain”). I have not seen a Microsoft solution for that so far. If anybody knows a smart solution and would share it, I’d really appreciate that.
You will not have to resort to a script and SCCM. Contrary to what this blog entry says can’t be done, we do use GPP to set sites into speicfic security zones. But we don’t set it as a GPP Internet Setting. We use GPP to assign the sites to their proper zones in HKLM\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap\Domains. Doing it this way we configure the sites we need configured for the organization but do not block the users’ ability to add sites they need set for their individual machines.
Ditto. This was my conclusion a few years ago when researching the various IE management methods. Have been scripting the site/zone assignment manually since then. Primarily with GPP which is fairly simple to manage Colin
GPP is server 2008 only and requires client side software correct? Anyway to do achieve the same results (managed IE Zones without disabling user access) in a 2003 AD environment?
Is there somebody who know how to do the same but with Cookies ?
Because of that, I still have to use IEM which sucks…
@AdamFowler_IT this is how you do IE zones http://t.co/uKug8h9h /cc @auteched
@alanburchill @auteched Worth noting that IE zones via this method http://t.co/qiaLSFK7 will wipe out settings from the old method!!!
with this GPO can we block all internet traffic except google and some other sites to users in the domain??
- Pingback: Best Practice: Roaming Profiles and Folder Redirection (a.k.a. User State Virtualization) : The Digital Jedi's Blog
If I understand GPOs properly, configuring this policy setting will centrally manage this setting without allowing the user to add/delete/modify any of the site to zone settings. Wouldn’t it be preferable to configure these directly in the user’s registry by use of “Preference” registry settings? I.e. creating records in “User Configuration\Preferences\Windows Settings\Registry”.
Hi, Quick question. Is it possible to have multiple sites assigned to “Intranet Zone”? If I try and add additional sites with the same zone number it states that this is not allowed. Can the links be broken up with ; , or something similar? Thanks,
you add each url in separate lines and repeat the zone number code on the right as many times in the list as you like for that zone. Each url will appear listed in that zone then.
I have a question, when you apply this group policy, users cannot add trusted website anymore by themselves. Did you know how to manage that ?
For those trying to find the answer for the above this post may be useful: http://blog.thesysadmins.co.uk/group-policy-internet-explorer-security-zones.html
It covers two methods. The first method will remove the option for the end user to edit or change the security zones, the second will allow the user to add or remove sites.
- Pingback: How to configure Roaming Profiles and Folder Redirection
- Pingback: genuine uggs
Is there a trick to copy/pasting in multiple Value names at once? I have like 100+ IP addresses to insert… Do I have to enter them in 1 at a time?!?
I found this extremely helpful and thank you for posting this. However, for some reason, on my PC when I test the GPO, my trusted sites are affected by the GPO but the only thing that happens is that I can no longer add them; the list is empty. I added about 10 sites to the list using the method above but they are not showing up. I checked to make sure the policy was being applied correctly and it is being applied; it is making it impossible to add to my trusted sites, but the list is empty. With IE 9, the GPO would do the opposite, it would add the sites but the end-user could still add more. I used IEAK for IE 9 years ago and never had a problem, but when I installed IEAK 10 or 11, it never worked.
OK, never mind! To answer my own question, in IE 10, it no longer displays the security zone on the status bar, which stinks, but one can right-click + properties (in an empty space in the body of the webpage) and it will tell the zone you are in. Looks like the zones I added are at least showing in trusted sites. That is good enough for me I guess. Thanks for the original post once again!
I too miss the security bar on IE 10. Will be interesting to review the browser user growths next year.
any news on the copying and pasting I have 100 ips to add need help with the distribution T
Computer specialists are often called IT experts/ advisors or business development advisors, and the division of a corporation or institution of higher education that deals with software technology is often called the IT sector. Countless IT service providers such as The Roots International are offering different facilities like real estate, IT solutions and many more.
I think I have a weird question/request. I want to include my whole domain such as http://www.domain.com as a trusted site. Although, I want to exclude a single web page such as http://www.my.domain.com .
I have *www.domain.com, can http://www.my.domain.com be excluded in any way?
Well, it will provide the internet user user better experience to use internet and surfing websites through internet explorer.
Invaluable discussion ! Coincidentally , if your company has been searching for a a form , my business discovered a blank version here http://goo.gl/eJ3ETg
دم شما گرم.
- Pingback: Allow Previously Unused ActiveX Controls To Run Without Prompt - PC Moment
- Pingback: Internet Options to add Trusted Site Greyed Out - SysPreped Windows 10 LTSB - Boot Panic
Leave a Reply Cancel reply
Site sponsor, featured post.
Popular Posts

- Best Practice (40)
- Group Policy FAQ (3)
- KB Focus (5)
- Other Site Links (15)
- Podcast (2)
- ScreenCast (4)
- Security (33)
- Setting of the Week (41)
- Site News (19)
- TechEd (35)
- Tutorials (117)
- Uncategorized (6)
- RSS - Posts
- RSS - Comments

How To Add Sites to Internet Explorer Restricted Zone

In this post we will see the steps on how to add sites to Internet Explorer restricted zone.
To configure Internet Explorer security zones there are multiple ways to do it, in this post we will configure a group policy for the users and use Site to Zone assignment list policy setting to add the websites or URL to the restricted site zone.
This policy setting allows you to manage a list of sites that you want to associate with a particular security zone. Internet Explorer has 4 security zones, numbered 1-4, and these are used by this policy setting to associate sites to zones.
- Intranet zone
- Trusted Sites zone
- Internet zone
- Restricted Sites zone
The zone numbers have associated security settings that apply to all of the sites in the zone. Using the Site to Zone assignment list policy setting we will see how to add sites to the Internet Explorer restricted zone.
Please note that Site to Zone Assignment List policy setting is available for both Computer Configuration and User Configuration.
Launch the Group Policy Management Tool, right click on the domain and create a new group policy. Right the policy and click Edit .
In the Group Policy Management Editor navigate to User Configuration > Administrative Templates > Windows Components > Internet Explorer > Internet Control Panel > Security Page.
If you want to apply the group policy for the computers then navigate to – Computer Configuration > Administrative Templates > Windows Components > Internet Explore r > Internet Control Panel > Security Page.
On the right hand side, right click the policy setting Site to Zone Assignment List and click Edit .
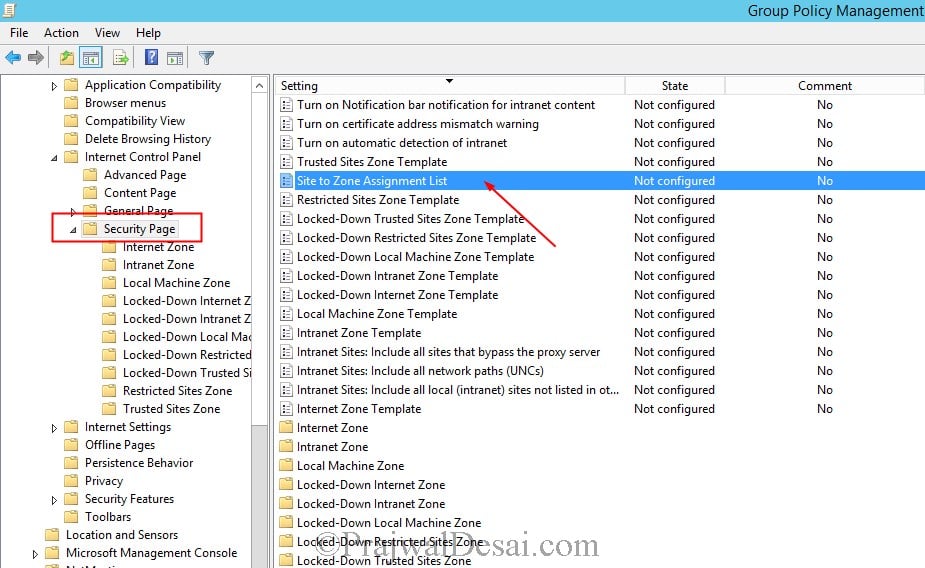
Click Enabled first and then under the Options click Show . You need to enter the zone assignments. As stated earlier in this post Internet Explorer has 4 security zones and the zone numbers have associated security settings that apply to all of the sites in the zone.
We will be adding a URL to the Restricted Sites Zone . So enter the value name as the site URL that to Restricted Sites zone and enter the value as 4 . Click OK and close the Group Policy Management Editor.
We will be applying the group policy to a group that consists of users. In the Security Filtering section, click Add and select the group .

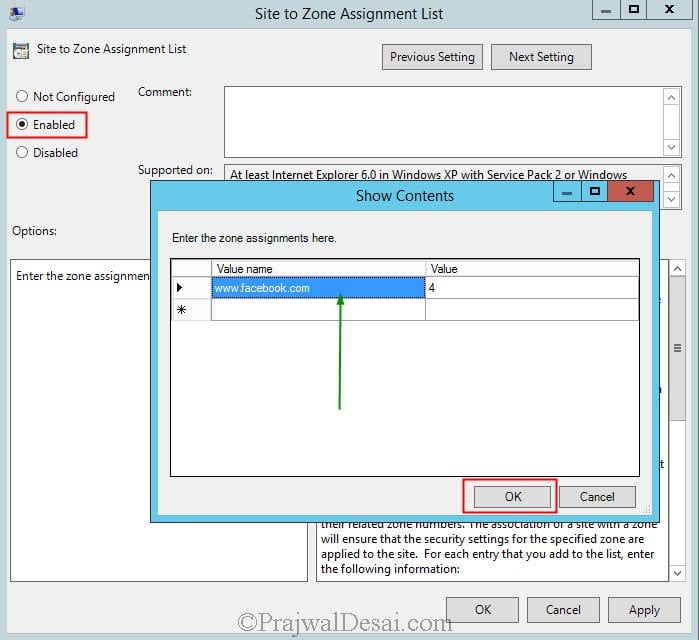
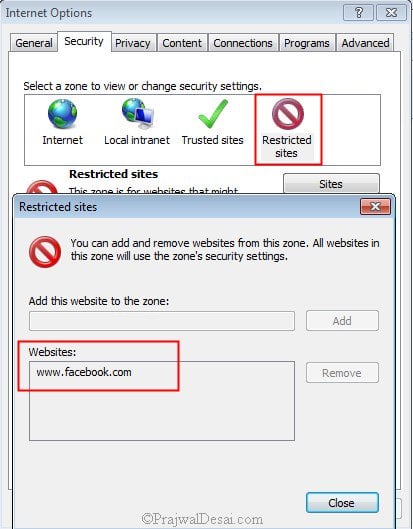
Login to the client computer and launch the Internet Explorer . Click on Tools > Internet Options > Security Tab > Restricted Sites > Click Sites .
Notice that the URL is added to the Restricted Sites zone and user cannot remove it from the list.
Sign Up For Newsletter
Join our newsletter to stay updated and receive all the top articles published on the site get the latest articles delivered straight to your inbox..
Good article Prajwal .Detailed Explanation on how to add sites to internet explorer restricted zone .Keep it up .I seen your videos also in YouTube its really great.Thanks for sharing this info.
Hi Prajwal, Thank you for your article. Is there any way to block sites in all browsers.
Block all sites ?. Why would you do that ?.
I think you misunderstood the user’s question. The user was asking if there was a way to block any particular website in ALL browsers. Not just Internet Explorer.
Leave a Reply Cancel reply
Your email address will not be published. Required fields are marked *
Save my name, email, and website in this browser for the next time I comment.
PatchMyPC Sponsored AD

Recast Sponsored AD

Popular Articles

SCCM 2012 R2 Step by Step Guide

How To Deploy Software Updates Using SCCM ConfigMgr

How to Install WSUS for SCCM | SUP Role | ConfigMgr

Fix Skype for Business Recording Shows Pending Status
Recent articles.

8 Ways to Fix Windows 11 Upgrade Error 0x800F0830-0x20003

How to Enable or Disable Copilot Vision in Microsoft Edge

Manage Windows 11 Readiness dashboard using SCCM

Top 10 ConfigMgr 2403 New Features

Subscribe Newsletter
Subscribe to our newsletter to get our newest articles instantly!

Managing Internet Explorer Trusted Sites with Group Policy
Internet Explorer Maintenance is dead. We all have our regrets, missed chances, and memories. But we have to move on. Depending on your love for power, you have two options. You can take the totalitarian route (known as Administrative Templates) or the benevolent method (known as Group Policy Preferences). Here are the two ways that you can configure Internet Explorer Trusted Sites with Group Policy.
Configuring IE Trusted Sites with Administrative Templates
Site to Zone Mapping allows you to configure trusted sites with Group Policy Administrative Templates. This setting can be found at:
- Computer Configuration/Policies/Administrative Templates/Windows Components/Internet Explorer / Internet Control Panel/Security Page/Site to Zone Assignment List
- User Configuration/Policies/Administrative Templates/Windows Components/Internet Explorer / Internet Control Panel/Security Page/Site to Zone Assignment List
When possible, use the computer configuration option as it will not impact user logons. When you enable the setting, you will be prompted for a value name (the website) and a value (the zone list). Here are the possible values and the zone that they correspond to:
- 1 = Intranet/Local Zone
- 2 = Trusted Sites
- 3 = Internet/Public Zone
- 4 = Restricted Sites

The screenshot above shows one trusted site and one restricted site. There is a potential downside to managing trusted sites with Administrative Templates. You will not be able to edit the trusted sites list within Internet Explorer. If you have more than four items listed, you won’t be able to see the entire list in the IE Trusted Sites window. If you view the site properties (Alt – File – Properties), you can check a specific site’s zone though. Remember this trick as it will help you when troubleshooting! You can view the entire list in the Registry by navigating to HKLM\Software\Policies\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap\Domains. If you are an administrator, you can edit/add/remote items from this list for testing. Just be sure to run a GPUpdate /force to undo your changes.
Bonus Points : Leave a comment below explaining why a GPUpdate /force is required to undo your changes. Super Bonus Points if you answer in a haiku.
Configuring IE Trusted Sites with Group Policy Preferences Registry
You would think that Group Policy Preferences Internet Settings could set trusted sites. Unfortunately, that setting is greyed out.

You can still configure IE site mappings with Group Policy Registry Preferences though.* The benefit of this is that your users can edit the zone lists and view all of the added sites. To set this up, create a new user side registry preference. This trick will not work under computer configuration. Enter in the following details:
- Keypath: Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap\Domains\WEBSITENAME
- Value Name: http
- Value Type: REG_DWORD
- Value Data: 2
Here is an example showing DeployHappiness being set as a trusted site with registry preferences:

If your site isn’t being placed in the Trusted Sites list, add it manually and then navigate to the registry location above. Ensure that the manual addition exactly matches your registry preference. You will also need to ensure that no Administrative Template Site to Zone settings are applied. If they are, they will wipe out your preference settings. Remember that Policies always win!
You can search your domain for site to zone settings by using this Group Policy Search script. Alan Burchill taught me this trick.
To see additional ways to configure site to zone mappings, read this very in depth example guide.
24 thoughts on “ Managing Internet Explorer Trusted Sites with Group Policy ”
I hope to replace our Site to Zone list to allow our users to enter their own in but I am not sure how to enter our entries that don’t specify a specific protocal such as http or https. So can someone tell me how I would create an entry for this:
*://*.sharepoint.com
and what about something like this – how would this be entered?
https://192.192.192.192 .:9443 (example only)
As for your first question, this info should help: https://community.spiceworks.com/topic/326140-add-trusted-sites-via-gpo-but-still-allow-users-to-add-trusted-sites?page=1#entry-2849140
As for the second question, I don’t know of a way to handle ports. In reference to your example, a link like that would be entered like this: *://192.192.192.192
This is excellent – I have used the GP preferences to add trused sites without locking users out of the setting if they need to add a site. But what about this – a program in the startup group – it is a shortcut to a file on a server – a member server of the local domain – domain.local. I want to prevent this program from prompting end-users to run it, and make sure it will run without prompting. Can this be accomplished with a GP preference as well? If so, do I need to add it to trusted sites, or to the local intranet zone or local machine zone? It would seem to be a local intranet or local machine zone I am working with here. I am not sure how to add it – whether I just need to add the local domain, or the computer name FQDN, or the path to the shared folder and the file. thanks!
This sounds like two different problems: 1. How do I get an app to run without prompting? 2. How do I make it run on startup with group policy?
The latter is easy, create it as a scheduled task that runs on startup. The former depends on what type of script it is. If it’s a vbscript then run it with cscript /b “name.vbs”.
With the old approach we had a file under trusted sites to allow the file to run. It has stopped working under 2012. Could I use this with a file? The old setting was:
file:\\Domain.com\netlogon\AsmallExe.exe
See this article on what you can configure with trusted sites: http://evilgpo.blogspot.com/2016/03/internet-explorer-site-to-zone.html
Just the ticket. Thanks a lot.
I have double-checked that the site to zone assignment policy is not configured, both under user and computer settings. We used group policy preferences because we do not want to lock down the trusted sites – only to push out the sites we want to be trusted. But for some absurd reason, the trusted sites are locked down and greyed out half the time – one day I will look and the sites are not dimmed out and will let me add or remove them. Then the next day they will be greyed out again. It is amazingly ridiculous. I am the only admin; no one else knows how to mess with the settings even if they had the admin credentials. So I have no clue why it keeps reverting back to the wrong settings. I thing our active directory needs to have dcdiag run on it a few times. Any ideas will be sincerely appreciated.
If it is locked down, it is a GP policy that is doing it (the site to zone assignment one) or a registry key that is enabling that site to zone assignment.
When you see one that does it, run a GPResult /h report.htm /f and look through that report.htm. You will see any GP settings that would block it then.
A reply to my own post – the problem was corrupted group policy on the Windows 7 computers – some of the computers were working fine. The ones that were not working, we had to delete the corrupt policy (it was preventing the updated policy settings from being applied). It was in the path C:\ProgramData\Microsoft\Group Policy\History\{policy GUID}. After deleting the corrupt policy and rebooting, it fixed the problem!
Thanks for the update Sam!
You’re welcome! I am still having some issues with the trusted sites being greyed out in IE, even though I made certain not to use site to zone assignment in the policy, and only used GP preferences to add registry items for the sites in the trusted zone. Do you know what registry key I need to be looking for, that might be causing this issue?
Many thanks! Sam S.
Are you making sure that you’re applying it under HKCU, and not under HKLM? If you configure it under HKCU, users will still have the ability to add their own entries. But if you configure it under HKLM, the option to add entries will be greyed out.
Yes, I definitely deployed the preferences under the Users GP Preferences and not computer policy/preferences. However, there are some policy settings that I set in both computer and user settings in the GPO. None of these are site to zone assignments though. These settings are for all the security settings within the zones, like, download signed activeX controls – enable, download unsigned activeX controls, Prompt… etc.. – these settings are set in the computer policy and the user policy which is probably what is wrong. I should probably just disable the computer policies in the GPO. I will try that and see if it helps. Why are all these settings available in the computer side and the user side both? Is there a reason someone would set these settings in one policy over the other?
A computer side policy is available for every user that logs in already. These are generally faster to apply and are my preferred way to configure something. However, times like this are when a user side policy would be the best route for you. Remove the computer side settings and try John’s suggestions. Let us know what you find out.
Sam, another thing you can try is to access the GPO from a Windows 7 workstation running IE 9 (and make sure that there are no current Internet Explorer policies being applied to the workstation; put it in an OU that is blocking inheritance if you have to), then drill down to “User Config\Policies\Windows Settings\Internet Explorer Maintenance\Security\Security Zones and Content Ratings”. Double-click on “Security Zones and Content Ratings”, then choose “Import…” under “Security Zones and Privacy’, click “Continue” when prompted, then click “Modify Settings, then “Trusted Sites”, then the “Sites” button. You can then make whatever changes you want (add a site, remove a site, remove the check from the https box, etc). This should give you the freedom you’re looking for :).
i`ve add multiple Sites to the Site to Zone assigment list (Trusted Sites). After a new logon, i`ve check my settings, start IE11, visit the site i`ve add to the list, press Alt – File – Properties and check the Zone. Some of the sites are correct, shown in the trusted site zone, some of them not, they are in an unkown zone (mixed). I want to check the registry path Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap\Domains but this key is empty, for HKLM and HKCU. What`s wrong?
Thanks and Regards Patrick
Are you deploying the trusted sites with Policies or registry preferences?
> comment below explaining why GPUpdate /force is required to undo your changes.
For Group Policy to apply efficiently changes trigger it.
Exceptions apply. GPUPDate force is one. Security too.
Less obtusely said: “Group Policy will normally only reprocess client side extensions that have at least one policy element that changed. The exceptions to this are Security Option settings which reapply every ~16 hours on most machines and every 5 minutes on Domain Controllers. The other exceptions are when you run a gpupdate /force, and any CSEs you configure to auto-reapply. You can view this decision tree by enabling UserEnv logging as described in http://technet.microsoft.com/en-us/library/cc775423%28v=ws.10%29.aspx ” … But not as haiku.
Hi, Is it possible to select the users you want that this GPO applies? It is because I need to add a web to trusted sites, but only to two users. Any idea?
You would need to configure these settings under user configuration. Then change the scope of the GPO from authenticated users to a group containing those two users.
With regards to deploying trusted sites via GPO, while allowing users to add their own entries, see if this post helps: http://community.spiceworks.com/topic/post/2849140
I’m finding that when I deploy Trusted Sites using GPP and the registry, users aren’t able to add entries themselves (it allows them to add to the list, but the entries don’t stick and are gone as soon as you reopen the dialog). Any ideas?
You sir, have a good last name! 🙂
Do you have any delete preferences configured to that registry key? If you manually browse to that key, do you see what the user added?
Leave a Reply Cancel reply
- Security Essentials
- Deploying Windows 10 (without touching a client)
- Group Policy – Preferences to Software and Everything In Between
- OneNote Can Centralize Your Documentation
- Lunch and Learn: PowerShell 3
- Lunch and Learn: Software Extraction
- Disclosure Policy
- Privacy Policy
- Rebuild the Administrative Start Menu
- Guest Posting
- What’s This? Q&A on Sponsored Posts
- Blogs that I Follow – 2018 Edition
- Books to Boost Your Career!
- Top Articles to Teach You Now!
- Top Gadgets to be more Productive!
- Software Tools
- Other – eBooks, Virtual labs, etc
- My Articles
- Clients and Desktops
- Group Policy
- Deployment/MDT
- About DeployHappiness
- February 2024
- October 2023
- January 2023
- October 2021
- November 2020
- October 2020
- February 2020
- January 2020
- November 2019
- October 2019
- February 2019
- January 2019
- December 2018
- November 2018
- October 2018
- August 2018
- February 2018
- January 2018
- December 2017
- October 2017
- September 2017
- August 2017
- February 2017
- January 2017
- October 2016
- September 2016
- August 2016
- February 2016
- January 2016
- December 2015
- October 2015
- September 2015
- August 2015
- February 2015
- January 2015
- December 2014
- November 2014
- October 2014
- September 2014
- August 2014
- February 2014
- January 2014
- December 2013
- November 2013
- October 2013
- September 2013
- August 2013
- Group Policy (85)
- Best Practice (90)
- Hardware (9)
- Management (100)
- Networking (3)
- Office 365 (8)
- Performance (23)
- Quick Tip (26)
- PowerShell (87)
- Security (28)
- Server (16)
- Thinking about IT (14)
- Training (6)
- TroubleShooting (36)
- Uncategorized (29)
- Walkthrough (109)
- Entries (RSS)
- Comments (RSS)
Stack Exchange Network
Stack Exchange network consists of 183 Q&A communities including Stack Overflow , the largest, most trusted online community for developers to learn, share their knowledge, and build their careers.
Q&A for work
Connect and share knowledge within a single location that is structured and easy to search.
How to view all IE Trusted Sites when security settings are managed?
If the Security Zones for Internet Explorer are managed by my system administrator, the list of Trusted Sites is disabled and I cannot scroll through the list. Is there a way I can view the full list of Trusted Sites?

- internet-explorer
- security-policy
- Not a duplicate, but somewhat related: serverfault.com/questions/612903/… - "IE11: How to check into which zone a URL falls?" – T S Apr 23 at 9:21
11 Answers 11
In the registry , perform a search for a URL that is known to be trusted. This should get you to the relevant key where you can see all of the others.
On my Windows 7 installation, the path appears to be HKEY_CURRENT_USER\Software\Policies\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMapKey , which is slightly different from this answer .
The key should contain several string values with a name indicating the URL and numeric data indicating the zone, one of the following by default.
- 0 = My Computer
- 1 = Local Intranet Zone
- 2 = Trusted sites Zone
- 3 = Internet Zone
- 4 = Restricted Sites Zone
- 8 Mine are all under HKEY_LOCAL_MACHINE – Richard Collette Sep 26, 2014 at 18:03
Depends upon your firm whether the list is under HKLM or HKCU. Here's a quick Powershell command to get the list
- 3 +1: This is the only solution which worked for me! Thanks! – Kidburla Mar 18, 2015 at 15:41
- 3 Remove the ".property" on the end of each line to see which zone the site is configured for: 1 = Local Intranet, 2 = Trusted Sites, 3 = Restricted Sites – BateTech Jul 10, 2019 at 12:25
From powershell:
- 1 Can you explain this answer/flesh it out a bit more for those who don't know PS as well? – studiohack Feb 10, 2015 at 16:13
- Start -> type gpedit.msc -> hit Enter
- navigate to Computer Configuration -> Administrative Templates -> Windows Components -> Internet Explorer -> Internet Control Panel -> Security Page
- in the right-hand panel, double-click on the Site to Zone Assignment List option, then click Show...
- trusted sites are the ones with 2 in the Value column (1 = Intranet, 3 = Internet, 4 = Restricted)
If that doesn't work (that option is set to "Not Configured" or the list is empty), try the same, except instead of Computer Configuration, start with User Configuration.
- 3 Both of these settings are "Not Configured" and the lists are empty. – JustinStolle Apr 18, 2012 at 22:33
- "You do not have permission to perform this action" - gpedit also locked down – LJT Apr 13, 2016 at 0:10
I came up with the following solution, I hope others will find it useful as well.
I have limited rights, only local, not enough to open and view GPEDIT on AD level.
So, what I did, and works, is to open a command prompt (as Admin) and run the command:
C:\WINDOWS\system32>GPResult /V /SCOPE Computer /H c:\temp\stuff.txt
Then perform a search e.g. for the "ZoneMapKey"
C:\WINDOWS\system32>find "ZoneMapKey" c:\temp\stuff.txt >> c:\temp\sites.txt
Keep in mind there are other keys that might require your attention, like the "approvedactivexinstalsites"...
You will have an output like:
KeyName: Software\Policies\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMapKey\https://www.wesayso.com
Clean it up (I use Excel, use the \ as seperator and be done with it) and you will have a great list.
- 4 I tried this but got an error "ERROR: Invalid Syntax. Options /U, /P, /R, /V, /Z cannot be specified along with /X, /H." – Kidburla Mar 18, 2015 at 15:39
- C:\WINDOWS\system32>GPResult /V /SCOPE COMPUTER >> c:\temp\stuff.txt generate the file for me. "COMPUTER" in caps per the help file. Use >> to write to file instead of /H – MrChrister Feb 4, 2019 at 22:58
This one works on my Windows 7 machine. It was set by my company's domain controller.
Here is an enhanced version of the script that translates the zone type number in the registry to its name as seen in the IE explorer settings dialog box.
Above we see how to gather the registry value names in a registry key and then get the data of each of those values. As each enter separates the value name and the value data with a comma, it could be further enhanced to output to a file with the csv extension and then opened in Excel. Many more possibilities if you want an actual report. But if just need to know what is the site list this will show most of them.
on windows 10 The URL are saved in Computer\HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMapKey
to get the values you can brows to the above key or via PowerShell
My key was located here (in HKEY_LOCAL_MACHINE, not HKEY_CURRENT_USER)
I could right-click "ZoneMapKey" and choose "Export"
This .reg file can be opened in Notepad to view (and search) the text contents.
This PowerShell script provides a list from both registry keys if they are populated and uses the out-gridview cmdlet to provide a search capability using the out-gridview filter field.
Stick this in Powershell for a list of the trusted sites:
1 = Intranet zone – sites on your local network. 2 = Trusted Sites zone – sites that have been added to your trusted sites. 3 = Internet zone – sites that are on the Internet. 4 = Restricted Sites zone – sites that have been specifically added to your restricted sites.
Answer taken from: https://blogs.sulross.edu/gfreidline/2017/06/20/show-ie-trusted-sites-from-powershell/
You must log in to answer this question.
Not the answer you're looking for browse other questions tagged internet-explorer security-policy managed ..
- The Overflow Blog
- Reshaping the future of API platforms
- Between hyper-focus and burnout: Developing with ADHD
- Featured on Meta
- Our Partnership with OpenAI
- Imgur image URL migration: Coming soon to a Stack Exchange site near you!
Hot Network Questions
- Would you correct grading mistakes downwards if there is a mistake in grading?
- Can I swap a gravel wheel with 1x10 cassette for a new road wheel with 1x12?
- *Trivial* near-repdigit perfect powers
- Origin and grammaticality of "I like me ..."
- Is it a bad idea to design a purposefully inconsistent magic system?
- Is the largest root of a random polynomial more likely to be real than complex?
- Shortest battleship game, to find number of battleships
- Text Based Game about Synthesizing Fuel from Scratch?
- Find the length of a line segment in a triangle
- Can I travel to the UK with a child accompanied visa without the adult named on my visa but with the consent from that adult to another adult?
- code format and steps web scraping using beautiful soup
- What major advances in theoretical and computational chemistry have been made in recent decades?
- Could Android go on PC?
- What is the least number of circles with radius r is required to cover a circumference of a circle with radius R?
- How to make this kind of list 1., 1.1, 1.1.1, ... and 1.2, 1.2.1, 1.2.1.1, ...?
- Windows War Strategy Game
- Is there any explanation or discussion regarding the change in the Bard class from its AD&D1ed orignal implementation?
- How can I save a dating relationship when I am promoted and she will be in my vertical reporting chain?
- Understanding ていた/ていなかった with もう/まだ
- How accurate is the model 42179 Planet Earth and Moon in Orbit?
- Is science value-free?
- Has there ever been a transfer of occupants from one aircraft to another while airborne?
- How does Russia exactly define Russian territory in its state policy?
- What wires needed for my basement circuits?
Home » Regroove Blog » What Is Seamless Single Sign On (And How to Set It up in Microsoft 365)
What Is Seamless Single Sign On (And How to Set It up in Microsoft 365)
Single sign on (SSO) is an authentication method that lets you use a single username and password to access multiple applications. Seamless SSO occurs when a user is automatically signed into their connected applications when they’re on corporate desktops connected to the corporate network.
The benefits of seamless SSO are many. Not only does seamless SSO limit the number of times your end users need to enter their login credentials, it also helps improve your overall security posture by implementing authentication systems beyond a username and password.
The best use case for seamless SSO is a hybrid environment, where your team is working on applications both in the cloud and on-premises. To establish a trust between the on-premises and cloud environments, you’ll need to use Azure AD Connect.
In this blog, we’ll walk through how to implement SSO in Microsoft 365.
Before You Start
Before you implement SSO in Microsoft 365, ensure your system meets the prerequisites. We recommend reviewing Microsoft’s documentation , but here’s a brief overview of what you’ll need:
- An Azure AD tenant, with the domain you plan to use added and verified
- On-premises Active Directory (schema version and forest functional level must be Windows Server 2003 or later, and domain controller must be writeable)
- PowerShell execution policy must allow running scripts (recommended policy is “RemoteSigned”)
- Azure AD Connect must be installed on a domain-joined Windows Server 2016 or later (can’t be installed on Small Business Server, Windows Server Essentials before 2019, or Windows Server core)
Configuring Azure AD Connect
When you have everything on the prerequisites list checked off, its time to spin up Azure AD Connect installation wizard. Select the customize option instead of express settings. Click through the user sign-in step – this step will give you the option to enable SSO, but only if you choose Password Synchronization or pass-through authentication as the sign on method. Choose one of these methods, as the use cases for the other options are relatively specific (for instance, if you’re a large organization with many domain controllers and a requirement for your own federation, you should select Federation with AD FS as a sign on method). Don’t forget to ‘Enable SSO’ before you leave this step!
Next, you’ll connect Azure AD Connect to Azure AD:
- Log in with your global or hybrid identity admin credentials
- Connect your on-premises directories or forests
- Configure Azure AD sign-in (typically use “userPrincipalName”)
Now you need to decide what you want to sync by way of domains and OUs. Its doubtful you’d want to sync everything from on-premises into the cloud, and it can get messy fast if you select items to sync that it turns out later you don’t need.
- Select ‘Sync selected domains and OUs’ and check off what you need to sync.
- Identifying users, filtering, and optional features can be left for now.
Enabling SSO
Now you’ll need to enable SSO. You’ll need your domain administrator credentials to configure your on-premises forest for use with SSO.
If everything looks good to this point, click “Install”. Note that synchronization has not been enabled here; there’s additional configuration to complete before adding users.
When you receive the “Configuration is complete” message, Azure AD Connect is installed and configured! Take a look within Azure AD:
Editing Your Group Policy
Next, log into the server manager and open the Group Policy Management editor. You’ll need to edit the group policy that’s applied to some or all of your users, which handles where users are sent (Intranet or Internet) when they navigate to URLs from the browsers.
You can find more information about editing your group policy here , but we’ll outline the steps below:
- Go to “User Configuration”, then “Policies”, then “Administrative Templates”, “Windows Components”, “Internet Explorer”, “Internal Control Panel”, and finally “Security Page”
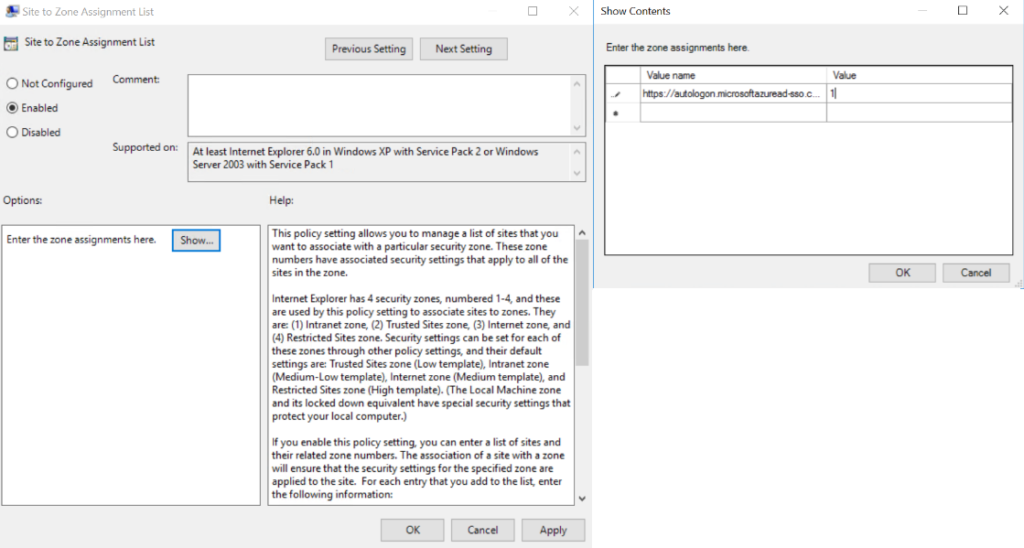
- Select site to “Zone Assignment List” and enable the policy
- Enter the following values:
- Value name: https://autologon.microsoftazuread-sso.com
- Value (data): 1
- Click “OK”, then “OK” again
- Go to “User Configuration”, then “Policies”, “Administrative Templates”, “Windows Components”, “Internet Explorer”, “Internet Control Panel”, “Security Pages”, then “Intranet Zone”
- Select “Allow updates to status bar via script”
- Enable the policy setting
- Click “OK”
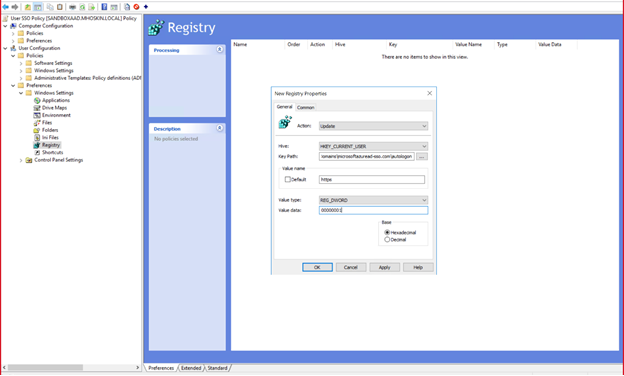
- Go to “User Configuration”, then “Preferences”, “Windows Settings”, “New”, then “Registry item”
- Enter the following information:
- Key Path: Key Path: Software\Microsoft\Windows\CurrentVersion\Internet\Settings\ZoneMap\Domains\microsoftazuread-sso.com\autologon
- Value name: https
- Value type: REG_DWORD
- Value data: 00000001
- Click “OK”
Enabling Sync
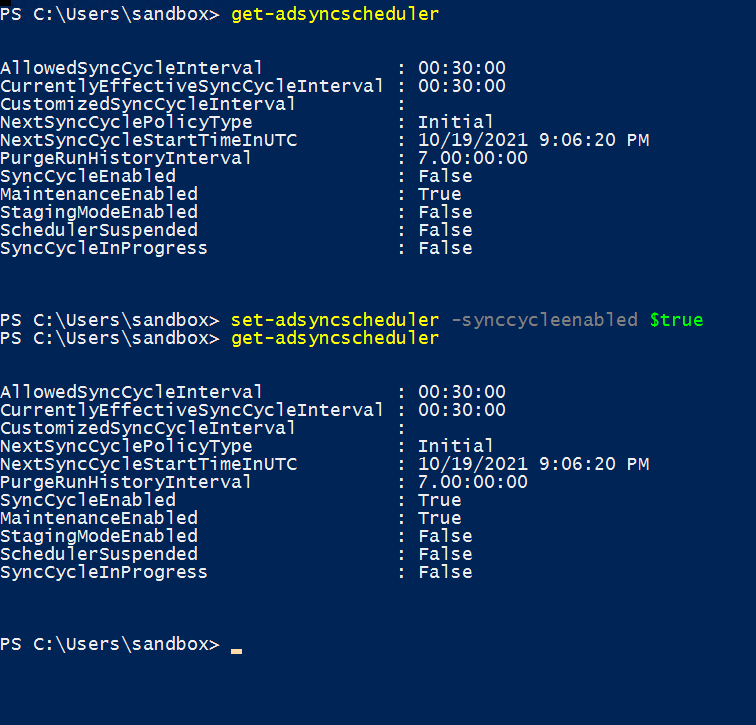
Lastly, you’ll need to enable sync by following these steps:
- Open PowerShell
- Enter “Get-adsyncscheduler”
- This should provide text which includes “Syncenabled = false”
- Set “adsyncshceduler -syncenabled $true”
- You should now see “Syncenabled = true”
Testing the Solution
To check if all your hard work has paid off, go to the sync service manager. Under “Connection Operations”, select your Azure AD name. Under “Statistics”, the number of adds should equal the number of objects synced from Active Directory to Azure AD via Azure AD Connect.
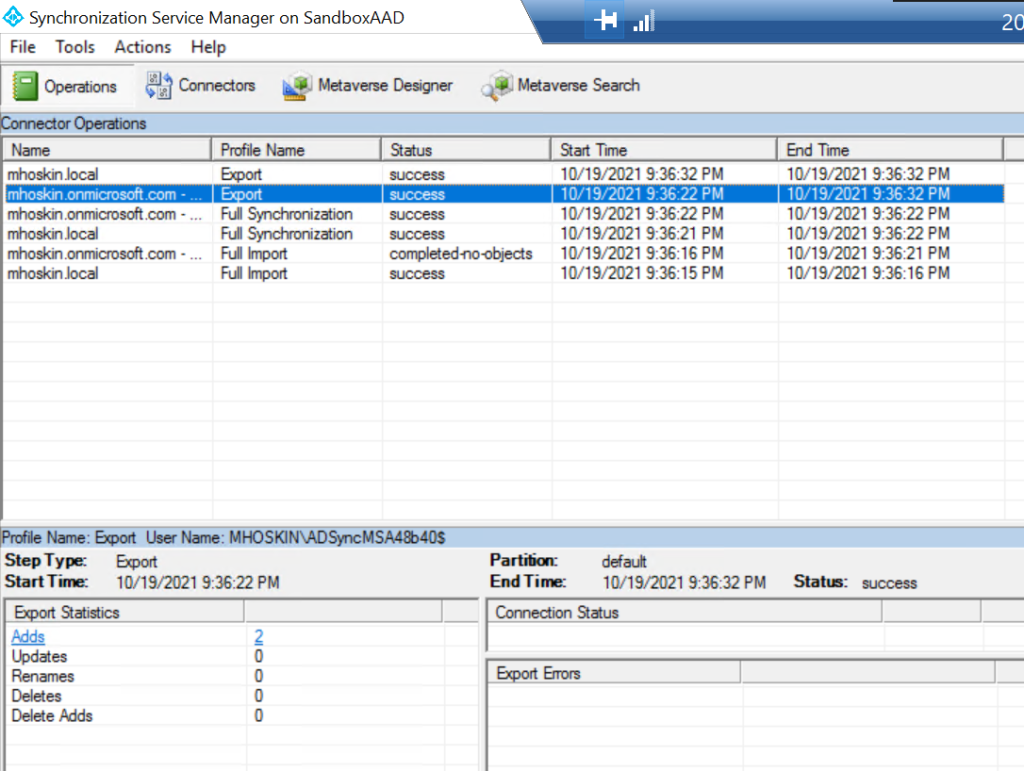
If that didn’t work, try “start-adsynccycle -policytype initial” in PowerShell.
Conclusion
SSO, and seamless SSO in Microsoft 365, have the ability to improve your end user experience, productivity, and security at your organization. We strongly recommend implementing SSO for your business.
Need assistance getting started? We can help! Get in touch with us at regroove.ca.
- cloud first
- cloud solutions
- cybersecurity
- Microsoft 365
- Microsoft Licensing
- Productivity
- remote work
Related posts
Remote work is here to stay: essential hardware for a microsoft 365-powered home office .
Three years into working from home means its likely time to update your home office hardware to help fuel productivity!
Optimizing Your Microsoft 365 Experience: A Guide to Choosing the Right Laptop
In the world of modern work, having the right tools can make all the difference for productivity and efficiency. To unlock Microsoft 365's potential, its important to choose the right laptop.
Microsoft To Do and Planner: Basic Project Management Tools You Can Start Using Right Now
Learn how to use Microsoft To Do and Planner to stay on top of tasks and organized for not only yourself, but your organization as well.
OneNote: The Better Way to Take Meeting Notes
How can Microsoft OneNote be used to collaborate on meeting minutes?
Cyber Security Insurance 101: A Fast-Track Overview and Key Considerations
As cyber threats continue to evolve, more organizes are investing in cyber security insurance (CSI) and security assessments. But what is CSI?
How to Implement a 'Meeting-Free Day' for Your Business
Thinking about implementing a meeting-free day at your organization? Check out how Regroove successfully accomplished it with Microsoft 365!
Navo - The company directory for the connected workplace.
Centrally organize all key company bookmarks to keep your team connected to the right resources, across workspaces and devices.
Newsletter sign-up
Stack Exchange Network
Stack Exchange network consists of 183 Q&A communities including Stack Overflow , the largest, most trusted online community for developers to learn, share their knowledge, and build their careers.
Q&A for work
Connect and share knowledge within a single location that is structured and easy to search.
IE11: How to check into which zone a URL falls?
I have applied several internet explorer settings via group policy. Especially a long list of URLs in the "site to zone assignment" setting. However it seems that one URL still falls into the "internet zone" even when assigned to the "trusted zone".
In earlier versions of internet explorer one could easily determine from the status bar into which zone an URL falls. How can this be done via IE11? Am I overlooking something obvious?
- group-policy
- internet-explorer
- I also agree with Matze. Even though, Microsoft provide the information in File-Properties. but it not easy to debug. If possible I would like to ask Microsoft return this feature back or give some option to selectable. – user255256 Nov 22, 2014 at 11:13
3 Answers 3
In the menu bar, if you go to File->Properties. The properties dialog shows the zone for that page.
- Just found it out by myself. Thanks for replying. support.microsoft.com/kb/2689449 – Matthias Güntert Jul 16, 2014 at 9:13
- 3 Press Alt + F + R key – Ivan Chau Jan 16, 2017 at 1:48
- 2 You can also right-click and go to properties. – davidtbernal Jul 12, 2018 at 21:32
This Microsoft created software will allow you to enter a URL and display not only the zone that falls into (including the local computer zone - there are actually four IE zones) but it will show the specific IE settings that would be applied. It's a great tool for diagnosing policy issues:
https://blogs.technet.microsoft.com/fdcc/2011/09/22/iezoneanalyzer-v3-5-with-zone-map-viewer/
You can check the zone via powershell:
Documentation for System.Security.Policy.Zone.CreateFromUrl: https://docs.microsoft.com/en-us/dotnet/api/system.security.policy.zone.createfromurl
You must log in to answer this question.
Not the answer you're looking for browse other questions tagged group-policy internet-explorer ..
- The Overflow Blog
- Reshaping the future of API platforms
- Between hyper-focus and burnout: Developing with ADHD
- Featured on Meta
- Our Partnership with OpenAI
- Imgur image URL migration: Coming soon to a Stack Exchange site near you!
Hot Network Questions
- What does "come the nut-cutting" mean?
- Did the widow of Zarephath know who Elijah was to just believe him?
- I keep blowing up irrigation solenoids
- Find the length of a line segment in a triangle
- What is the least number of circles with radius r is required to cover a circumference of a circle with radius R?
- Is there a minimum midi-chlorian count needed to live?
- "foresee" vs. "predict"
- Has there ever been a transfer of occupants from one aircraft to another while airborne?
- Can an employee be made to pay back training costs when resigning from the company?
- Is it a bad idea to design a purposefully inconsistent magic system?
- Java interpreter
- When in Rome... – a deconstruction sudoku
- Text Based Game about Synthesizing Fuel from Scratch?
- What can you use in your soil to kill bugs before planting vegetables?
- Golfing the complexity with subtraction
- Rambam contradiction
- How can I find a chord's root note?
- Defining an output format that doesn't break Ctrl+Shift+I
- Could Android go on PC?
- A word for not just optional but usually not done
- Origin and grammaticality of "I like me ..."
- How accurate is the model 42179 Planet Earth and Moon in Orbit?
- Schedule monotony constraints
- In OOP, what count as a "getter"
- ManageEngine Products
Securing zone levels in Internet Explorer
Managing and configuring Internet Explorer can be complicated. This is especially true when users meddle with the numerous settings it houses. Users may even unknowingly enable the execution of malicious codes. This highlights the importance of securing Internet Explorer.
In this blog, we’ll talk about restricting users from changing security settings, setting trusted sites, preventing them from changing security zone policies, adding or deleting sites from security zones, and removing the Security tab altogether to ensure that users have a secure environment when using their browser.
Restricting users from changing security settings
A security zone is a list of websites at the same security level. These zones can be thought of as invisible boundaries that prevent certain web-based applications from performing unauthorized actions. These zones easily provide the appropriate level of security for the various types of web content that users are likely to encounter. Usually, sites are added or removed from a zone depending on the functionality available to users on that particular site.
To set trusted sites via GPO
- Open the Group Policy Management Editor .
- Go to User Configuration > Policies > Administrative Templates > Windows Components > Internet Explorer > Internet Control Panel > Security Page .
- Select the Site to Zone Assignment List .
- Select Enabled and click Show to edit the list. Refer to Figure 1 below. The zone values are as follows: 1 — intranet, 2 — trusted sites, 3 — internet zone, 4 — restricted sites.
- Click Apply and OK .
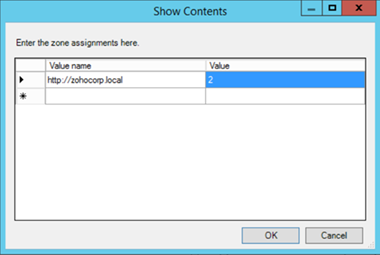
Figure 1. Assigning sites to the Trusted Sites zone.
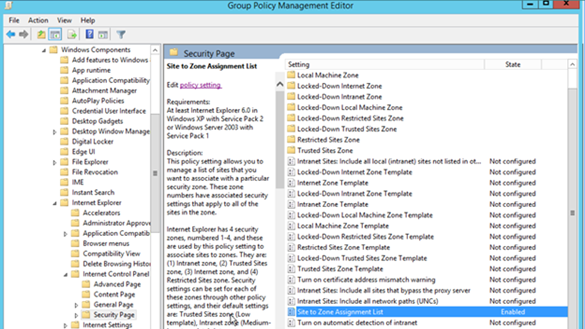
Figure 2. Enabling the Site to Zone Assignment List policy.
By enabling this policy setting, you can manage a list of sites that you want to associate with a particular security zone. See Figure 2.
Restricting users from changing security zone policies
- Go to Computer Configuration > Administrative Templates > Windows Components > Internet Explorer .
- Double-click Security Zones: Do not allow users to change policies .
- Select Enabled .
This prevents users from changing the security zone settings set by the administrator. Once enabled, this policy disables the Custom Level button and the security-level slider on the Security tab in the Internet Options dialog box. See Figure 3.
Restricting users from adding/deleting sites from security zones
- Double-click Security Zones: Do not allow users to add/delete sites .
This disables the site management settings for security zones, and prevents users from changing site management settings for security zones established by the administrator. Users won’t be able to add or remove websites from the Trusted Sites and Restricted Sites zones or alter settings for the Local Intranet zone. See Figure 3.
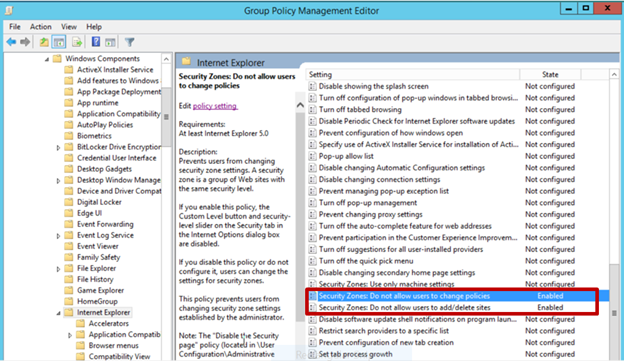
Figure 3. Enabling Security Zones: Do not allow users to change policies and Security Zones: Do not allow users to add/delete sites .
Removing the Security tab
The Security tab in Internet Explorer’s options controls access to websites by applying security settings to various download and browsing options, including defining security levels for respective security zones. By removing this tab, users will no longer be able to see or change the settings established by the administrator.
- Go to User Configuration > Policies > Administrative Templates > Windows Components > Internet Explorer > Internet Control Panel .
- Double-click Disable the Security page .
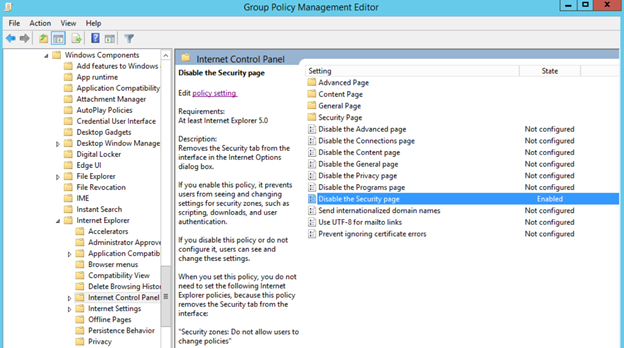
Figure 4. Enabling the Disable the Security page policy. Enabling this policy prevents users from seeing and changing settings for security zones such as scripting, downloads, and user authentication. See Figure 4.
There’s no denying the importance of securing Internet Explorer for any enterprise. By setting security levels, restricting users from changing security zone policies, preventing them from adding or deleting sites from security zones, and removing the Security tab, users will not be able to change any security settings in Microsoft Internet Explorer that have been established by the administrator. This helps you gain more control over Internet Explorer’s settings in your environment.
Derek Melber
Cancel reply.
Is there a way to enable Site to Zone assignment list and still let the user enter their own sites to the trusted list?
Hi Joe. You need to disable the below setting to achieve the requirement.
Note: Even if the policy is not configured, users can add their own sites. Only when the policy is enabled, users can’t add their own sites to trusted sites.
Thanks a lot.
Related Posts

El error de Microsoft que ha puesto en juego la seguridad del estado
Español 2 min read Read

a blog by Sander Berkouwer
- The things that are better left unspoken
HOWTO: Add the required Hybrid Identity URLs to the Trusted Sites list of Internet Explorer and Edge

Most Microsoft-based Hybrid Identity implementations use Active Directory Federation Services (AD FS) Servers, Web Application Proxies and Azure AD Connect installations. In this series, labeled Hardening Hybrid Identity , we’re looking at hardening these implementations, using recommended practices.
In this part of the series, we’ll look at the required Hybrid Identity URLs that you want to add to the Trusted Sites list in Internet Explorer.
Note: This is the second part for adding Microsoft Cloud URLs to Internet Explorer’s zone. In this part we look at the Trusted Sites zone. In the previous part we looked at the Local Intranet zone .
Note: Adding URLs to the Trusted Sites zone for Internet Explorer, also applies to Microsoft Edge.
Why look at the Trusted Sites?
Hybrid Identity enables functionality for people using on-premises user accounts, leveraging Azure Active Directory as an additional identity platform. By default, Azure AD is the identity platform for Microsoft Cloud services, like Exchange Online, SharePoint Online and Azure.
By adding the URLs for these services to the Trusted Sites list, we enable a seamless user experience without browser prompts or hick-ups to these services.
Internet Explorer offers built-in zones. Per zone, Internet Explorer is allowed specific functionality. Restricted Sites is the most restricted zone and Internet Explorer deploys the maximum safeguards and fewer secure features (like Windows Integrated Authentication) are enabled.
The Trusted Sites zone, by default, offers a medium level of security.
Possible negative impact (What could go wrong?)
Internet Explorer’s zones are defined with specific default settings to lower the security features for websites added to these zones.
When you use a Group Policy object to add websites that don’t need the functionality of the Trusted Sites zone to the zone, the systems in scope for the Group Policy object are opened up to these websites. This may result in unwanted behavior of the browser such as browser hijacks, identity theft and remote code executions, for example when you mistype the URLs or when DNS is compromised.
While this does not represent a clear and immediate danger, it is a situation to avoid.
Getting ready
The best way to manage Internet Explorer zones is to use Group Policy.
To create a Group Policy object, manage settings for the Group Policy object and link it to an Organizational Unit, Active Directory site and/or Active Directory domain, log into a system with the Group Policy Management Console (GPMC) installed with an account that is either:
- A member of the Domain Admins group, or;
- The current owner of the Group Policy Object, and have the Link GPOs permission on the Organizational Unit(s), Site(s) and/or Domain(s) where the Group Policy Object is to be linked, or;
- Delegated the Edit Settings or Edit settings, delete and modify security permission on the GPO, and have the Link GPOs permission on the Organizational Unit(s), Site(s) and/or Domain(s) where the Group Policy Object is to be linked.
The URLs to add
You’ll want to add the following URLs to the Trusted Sites zone, depending on the way you’ve setup your Hybrid Identity implementation:
*.microsoft.com
*.microsoftonline.com, *.windows.net, ajax.aspnetcdn.com, microsoft.com, microsoftline.com, microsoftonline-p.net, onmicrosoft.com.
The above URLs are used in Hybrid Identity environments. While they overlap with some of the URLs for the Local Intranet Zone, these URLs allow side services to work properly, too.
*.msappproxy.net
Web applications that you integrate with Azure Active Directory through the Azure AD Application Proxy are published using https://*.msappproxy.net URLs. Add the above wildcard URL to the Trusted Sites list, when you’ve deployed or are planning to deploy Azure AD App Proxy. If you use vanity names for Azure AD App Proxied applications, add these to the Trusted Sites list, as well.
Other Office 365 services
Most Hybrid Identity implementations are used to allow access to Office 365 only. Last year, 65% of Hybrid Identity implementations are used to unlock access to one or more Office 365 services, like Exchange Online, SharePoint Online, OneDrive for Business and Teams, only. This blogpost focuses on the Hybrid Identity URLs, but you might want to add more Office 365 URLs and IP address ranges to the Trusted Sites list as you deploy, roll out and use Office 365 services. You can use this (mostly outdated) Windows PowerShell script to perform that action , if you need.
How to add the URLs to the Trusted Sites zone
To add the URLs to the Trusted Sites zone, perform these steps:
- Log into a system with the Group Policy Management Console (GPMC) installed.
- Open the Group Policy Management Console ( gpmc.msc )
- In the left pane, navigate to the Group Policy objects node.
- Locate the Group Policy Object that you want to use and select it, or right-click the Group Policy Objects node and select New from the menu.
- Right-click the Group Policy object and select Edit… from the menu. The Group Policy Management Editor window appears.
- In the main pane of the Group Policy Management Editor window, expand the Computer Configuration node, then Policies , Administrative Templates , Windows Components , Internet Explorer , Internet Control Panel and then the Security Page node.
![SiteToZoneAssignmentListSettingGPO_thumb[3] SiteToZoneAssignmentListSettingGPO_thumb[3]](https://dirteam.com/sander/wp-content/uploads/sites/2/2019/10/SiteToZoneAssignmentListSettingGPO_thumb3_thumb.jpg)
- In the main pane, double-click the Sites to Zone Assignment List setting.
- Enable the Group Policy setting by selecting the Enabled option in the top pane.
- Click the Show… button in the left pane. The Show Contents window appears.
- Add the above URLs to the Trusted Sites zone by entering the URL in the Value name column and the number 2 in the Value column for each of the URLs.
- Click OK when done.
- Close the Group Policy Editor window.
- In the left navigation pane of the Group Policy Management Console, navigate to the Organization Unit (OU) where you want to link the Group Policy object.
- Right-click the OU and select Link an existing GPO… from the menu.
- In the Select GPO window, select the GPO.
- Click OK to link the GPO.
Repeat the last three steps to link the GPO to all OUs that require it. Take Block Inheritance into account for OUs by linking the GPO specifically to include all people in scope.
To enable functionality in a Hybrid Identity implementation, we need to open up the web browser to allow functionality for specific web addresses. By enabling the right URLs we minimize our efforts in enabling the functionality and also minimize the negative effect on browser security.
There is no need to add all the URLs to specific Internet Explorer zones, when you don’t need to functionality. However, do not forget to add the specific URLs when you enable specific functionality like the Azure AD Application Proxy and remove specific URLs when you move away from specific functionality.
Further reading
Office 365 URLs and IP address ranges Group Policy – Internet Explorer Security Zones Add Site to Local Intranet Zone Group Policy
Posted on October 17, 2019 by Sander Berkouwer in Active Directory , Entra ID , Security
2 Responses to HOWTO: Add the required Hybrid Identity URLs to the Trusted Sites list of Internet Explorer and Edge

Great Post! Thank you so much for teaching us on how to add hybrid identity urls to the trusted list of sites on browsers like internet explorer and Microsoft edge.
I want to block all websites on edge and only give access to 2 sites but using group policy can someone help on this?
leave your comment cancel
This site uses Akismet to reduce spam. Learn how your comment data is processed .
Advertisement

Search this site
Dirteam.com / activedir.org blogs.
- Strategy and Stuff
- Dave Stork's IMHO
- The way I did it
- Sergio's Shack
- Things I do
- Tomek's DS World
Microsoft MVP (2009-2024)
Veeam vanguard (2016-2024), vmware vexpert (2019-2022).

Xcitium Security MVP (2023)

Recent Posts
- On-premises Identity-related updates and fixes for April 2024
- What's New in Entra ID for April 2024
- I'm co-presenting KNVI's 'The Flow of Information' event
- I'm co-presenting at Techorama Belgium's Fun Fair Edition
- The video of my session on Backing up and Restoring Virtual Domain Controllers for the Dutch Veeam User Group Meetup is now available
Recent Comments
- Sander Berkouwer on KnowledgeBase: App Passwords are only available to users with a non-Conditional Access MFA requirement
- Frank on KnowledgeBase: App Passwords are only available to users with a non-Conditional Access MFA requirement
- Dick Sangers on TODO: Periodically reset the password for the KRBTGT_AzureAD account when using Hybrid Cloud Trust
- K Dude on HOWTO: Set an alert to notify when an additional person is assigned the Azure AD Global Administrator role
The information on this website is provided for informational purposes only and the authors make no warranties, either express or implied. Information in these documents, including URL and other Internet Web site references, is subject to change without notice. The entire risk of the use or the results from the use of this document remains with the user. Active Directory, Microsoft, MS-DOS, Windows, Windows NT, and Windows Server are either registered trademarks or trademarks of Microsoft Corporation in the United States and/or other countries. All other trademarks are property of their respective owners.
- Configuring Zones Using Group Policy
To manage security zones in an enterprise, use the Group Policy settings located at \Administrative Templates\Windows Components\Internet Explorer\Internet Control Panel \Security Page under both Computer Configuration and User Configuration. Using these settings, you can configure the exact rights applied to each zone. To assign a standard security level (Low, Medium Low, Medium, Medium High, or High) to a zone, enable one of the following settings:
- Internet Zone Template
- Intranet Zone Template
- Local Machine Zone Template
- Restricted Sites Zone Template
- Trusted Sites Zone Template
If none of the standard security levels provides the exact security settings you need, you can edit the settings in the appropriate zone's node within the Security Page node. In particular, notice the Turn On Protected Mode setting located in each zone's node.
To specify that a URL is part of a specific zone, enable the Site To Zone Assignment List setting in the Security Page node. After you have enabled a URL, you can assign it (using the Value Name field, with an optional protocol) to a specific zone (using the Value field) using the zone's number:
- 1: Local Intranet zone
- 2: Trusted Sites zone
- 3: Internet zone
- 4: Restricted Sites zone
In this tutorial:
- Managing Windows Internet Explorer
- Internet Explorer 8 Improvements
- InPrivate Browsing
- InPrivate Filtering
- Compatibility View
- SmartScreen
- Domain Highlighting
- Tab Isolation
- Accelerators
- Improvements Previously Introduced in Internet Explorer 7
- User Interface Changes
- Tabbed Browsing
- How to Create a Web Link to Add a Custom Search Provider
- How to Configure Custom Search Providers Using the Registry
- How to Configure Custom Search Providers Using Group Policy
- Improved Standards Support
- Expanded Group Policy Settings
- Defending Against Malware
- How Protected Mode Improves Security
- How the Protected Mode Compatibility Layer Works
- How to Solve Protected Mode Incompatibilities
- URL-Handling Protection
- Address Bar Visibility
- Cross-Domain Scripting Attack Protection
- Controlling Browser Add-ons
- Add -on Manager Improvements
- Protecting Against Data Theft
- Security Status Bar
- How the Smart Screen Filter Works
- How to Configure Smart Screen Options
- Deleting Browsing History
- Blocking IDN Spoofing
- Security Zones
- Understanding Zones
- Configuring Zones on the Local Computer
- Network Protocol Lockdown
- Managing Internet Explorer Using Group Policy
- Group Policy Settings for Internet Explorer 7 and Internet Explorer 8
- New Group Policy Settings for Internet Explorer 8
- Using the Internet Explorer Administration Kit
- Troubleshooting Internet Explorer Problems
- Internet Explorer Does Not Start
- An Add-on Does Not Work Properly
- Some Web Pages Do Not Display Properly
- Preventing Unwanted Toolbars
- The Home Page or Other Settings Have Changed
- MS PowerPoint
- Windows Vista
- Adobe Photoshop
- A+ Certification

Windows security encyclopedia
#microsoft #windows #security
Search form
Site to zone assignment list.
This policy setting allows you to manage a list of sites that you want to associate with a particular security zone. These zone numbers have associated security settings that apply to all of the sites in the zone.Internet Explorer has 4 security zones numbered 1-4 and these are used by this policy setting to associate sites to zones. They are: (1) Intranet zone (2) Trusted Sites zone (3) Internet zone and (4) Restricted Sites zone. Security settings can be set for each of these zones through other policy settings and their default settings are: Trusted Sites zone (Low template) Intranet zone (Medium-Low template) Internet zone (Medium template) and Restricted Sites zone (High template). (The Local Machine zone and its locked down equivalent have special security settings that protect your local computer.)If you enable this policy setting you can enter a list of sites and their related zone numbers. The association of a site with a zone will ensure that the security settings for the specified zone are applied to the site. For each entry that you add to the list enter the following information:Valuename – A host for an intranet site or a fully qualified domain name for other sites. The valuename may also include a specific protocol. For example if you enter http://www.contoso.com as the valuename other protocols are not affected. If you enter just www.contoso.com then all protocols are affected for that site including http https ftp and so on. The site may also be expressed as an IP address (e.g. 127.0.0.1) or range (e.g. 127.0.0.1-10). To avoid creating conflicting policies do not include additional characters after the domain such as trailing slashes or URL path. For example policy settings for www.contoso.com and www.contoso.com/mail would be treated as the same policy setting by Internet Explorer and would therefore be in conflict.Value - A number indicating the zone with which this site should be associated for security settings. The Internet Explorer zones described above are 1-4.If you disable or do not configure this policy users may choose their own site-to-zone assignments.
Policy path:
Scope: , supported on: , registry settings: , filename: , related content.
Add Site to Trusted Sites Zone with Group Policy
- Post author By Corey Blaz
- Post date May 29, 2018
- No Comments on Add Site to Trusted Sites Zone with Group Policy
Internet Explorer has four Security zones (numbered 1-4) which are used by the Site to Zone Assignment List policy to associate sites to:
- Intranet zone
- Trusted Sites zone
- Internet zone
- Restricted Sites zone
To add a site to the Trusted Sites zone, do the following:
- Create a new Group Policy Object (GPO) or edit a preexisting object
- Navigate to Computer Configuration -> Administrative Templates -> Windows Components -> Internet Explorer -> Internet Control Panel -> Security Page
- Select and open the “Site to Zone Assignment” List policy
- Set the policy to Enabled
- Click the “Show…” button
Leave a Reply Cancel reply
Your email address will not be published. Required fields are marked *
Save my name, email, and website in this browser for the next time I comment.
Notify me of follow-up comments by email.
Notify me of new posts by email.
This site uses Akismet to reduce spam. Learn how your comment data is processed .
SysAdminHell
A resource for those attempting to survive the world of the System Administrator.
- Zone Assignments and GPO settings
March 20, 2014

- For Action, choose Update.
- For Hive, choose HKEY_CURRENT_USER
- For Key Path, enter Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap\Domains\blogger.com
- Replace blogger.com with the domain you want to add.
- If you want to cover the entire domain, just put the domain name.
- If you want to cover only a sub domain, put it instead (example: client.blogger.com)
- If you want to cover only www, put that as well (example: www.blogger.com)
- For Value Name, you have a few options.
- You can use a wildcard to cover anything .blogger.com (*.blogger.com)
- You can specify a protocol (http, https). This will only cover that one protocol (example: www.blogger.com, with Value http = http://www.blogger.com)
- Value type: REG_DWORD
- Value Data: Enter the value of the zone you want to assign.
- 1 = Intranet Zone
- 2 = Trusted Sites Zone
- 3 = Internet Zone
- 4 = Restricted Sites Zone
- Base: Decimal.

52 comments:
We are top quality professional experts provides you Assignment Help at very affordable cost.
Hey Seth, wanted to thank you for your in-depth explanation. When I first stumbled across this issue it was an unwelcome surprise. Initially we tried changing our users' network paths from UNC to DFS shares but we found that now all their Office documents were opening in Protected View. I figured there had to be a way to prevent this from happening, but when I tried modifying the "Site to Zone Assignment List", a coworker realized I had obliterated the previously set sites (which were assigned using Internet Explorer Maintenance policies, which have since been deprecated in IE10+, hooray!). I'm still not sure the best way to administer IE sites now, but your entry is a wonderful step in the right direction. Thanks again! DL
Thanks for sharing info. My Assignment Help
I have a question. I want to add my domain.com into the trusted zone, but want a single web page such as, mine.domain.com excluded from the trusted zone. Is this possible?
Some of these information are really amazing. Thank you for giving me good information. Assignment Help Sydney
It is a nice post Finance Assignment help Accounting Assignment Help Statistics Assignment Help IT Assignment Help Java Programming Assignment Help Perdisco Assignment Help MBA Assignment Help Human resource assignment help Operations management assignment help Research Assignment help Business management assignment help Travel and tourism assignment help Hospitality management assignment help Case Study Assignment help Law Assignment Help Online Assignment Help Cheap Assignment help College Assignment help Last minute assignment help need assignment help Nursing assignment help Economics assignment help Marketing Assignment help Essay writing service Australia Taxation Assignment help Database assignment help austraila arlington management undefined unviersity of new south wales
The Best Assignment help is one of the best website for assignment help. For more details you may contact us at [email protected] or call at +447418324884, the best assignment help HI6008 mng932002 MKTG303 cab202 HC1041 mn503 MKT01425 HSC230 HI5019 ICT352 HI6007 HI6006 MN621 HI5017 Cost Benefit Forensic Hire a Tutor Law Assignment Essay writing
The Best assignment help is one of the best website for assignment help. For more details you may contact us at [email protected] or call at:+447418324884 the best assignment help bsbldr501 SIT221 BSBWOR502 ITC560 HSH725 HSH725 MN405 CIS8100 HI5015 Holmes Assignment Holmes College UNCC300 MAA103 COIT20263 UNCC300 CHCDIV001
It is a nice post the best assignment help assignment help Online Custom Essay Help Essay Writing Make My Assignment Dissertation Help Coursework Help asa 315 bortons framework woolworths marketing PPMP 20011 ITC 542 ACTY 5320
Pretty! This was a really wonderful post. Thank you for providing these details the best assignment help assignment help ICTICT501 BSBFIM601 BSBCOM603 ACC03043 s180 corporations act rio tinto values COM4056
Get best accounting assignment help for students
assignment help the best assignment help assignment help sydney australian assignment help university assignment help toronto university assignment help toronto university assignment help
Assignment Help in UAE The tutors have a large team of online UAE the tutors. You can order your assignment or homework of any subject with the requirements. Our Assignment Help in UAE completes your assignment to help UAE according to your requirements. Whatever the field you are Assignment Help Dubai, Assignment Help Kuwait, Assignment Help Saudi Arabia, Assignment help in Oman https://www.thetutorshelp.com/ https://www.thetutorshelp.com/uae.php
get the Perdisco Assignment Help We also provide as many academic references as much possible for the coursework. We also provide urgent assignment help at an affordable price.
Homework Help also provide for urgent completion of assignments at an affordable price.. get the MYOB Assignment Help
Nice Post... There are plenty of MS Office plans that come in different price ranges and offer different features. Before you ask what is the most affordable Office plan that you can buy, do consider what the plan is offering as it won’t be of any use for you if you can’t get all the things you need from it. If you are a student struggling to keep up with the prices of MS Office, you can use Microsoft’s Office Free Student Plan. This way you can use the Office for absolutely free. However, there’s one limitation with this offer that is your institute must be enrolled with Microsoft and you must have your school email address. If you can’t avail MS Office Student plan, there’s another way to avail its free version i.e. using the Microsoft www.office.com/setup Online website. office.com office.com/setup
We have a team of proficient Tutors and have been delivering top quality writing services to the students. MATLAB assignment help
The vulnerability of the disease is discriminatory and because certain types of cancer affect a particular group. assignment help
An assignment is a task and is slightly different. Every assignment task is planned by your personnel for novel results; even your friends and individual course mates will get different ones from yours. The academic experts with us treat each question with educational affectability and guarantee that exact substance and research are featured that completely answer the evaluation task while you learn amid the entire cycle. It isn't just about completing your assignments; it is additionally significant that when you are finished with your assignment, you can understand both essential and exclusive ideas of your course and can fathom the learning results of your assignment. What great is the accommodation of your paper if you don't wind up learning through it? Interface with Great Assignment Help in canada today to get more proficient in your picked fields of study. We emphatically suggest it as nobody can remove your scoring from you; regardless of whether you lose each other belonging.
By the way, we are providing machine learning assignment help service for the students so that they get to understand their assignments properly. The services help them in completing all kinds of assignments and essays within the specified time to get good grades in the subject.
Thanks for sharing this information. I have shared this link with others to keep posting such information to provide the best in class assignment help online at very affordable prices. Marketing Assignment Help Math Homework Help Nursing Assignment Help programming assignment help statistics homework help Finance Homework Help Business Plan Help
Do you need help completing your Finance Assignment? Get Fast and Reliable Finanace Assignment Help . My Assignment Help provides assignment help services at an affordable price. Our entire team of writers, subject matter experts, finance assignment experts, finance experts, proofreaders, and editors are Ph.D. qualified. They are profound in skills like time management, leadership, etc., for better teamwork and assistance.Place your order to avail our pocket–friendly services.
thanks for the information. if you need any help MYOB Assignment Help . Top writers are here to listen to your requirement and deliver quality work at a price that anybody can afford easily. MYOB Homework help
thanks for providing the great information. we provide the Economics Homework help for the students at the best price. Our expert writers and tutors will resolve your assignment problems within the given deadline. you can get the Economics Assignment help from the professionals.
Do you need any help with Database Assignment help , we are available to help you. You just need to visit our website and place your order. 24x7 online support. you can get the Database Homework help the best price in the market.
If anyone need the Java Homework Help from the experts. 100% plagiarism free. We are dedicatedly making efforts round the clock for students to achieve their academic potential. if you need Java Assignment Help .We are the best in providing custom assignments and homework help, at an best price in the market.
Nice & Informative Blog ! Our experts at QuickBooks Customer Service Number provide unmatched technical support service in the time of financial crisis.
We provide the Python Homework help at the best price to the students. . Our highly skilled assignment writers are well-versed with the need of the Australian students and can easily provide the proper guidance regarding the Python Assignment help We have the 24x7 live support and excellent faculty for your tasks.
Nice Blog ! Our team at QuickBooks Customer Service put their best foot forward into giving you the best services during these tumultuous times.
If you are looking for Nursing Assignment Help by which you can achieve high grades in assignments, then My Assignment Help can assure you that we will fulfill your dreams. We are always ready to help you. We provide high-quality nursing assignment from a team of professional academic writers.
Hands down, I agree with you on that. Well done for presenting such a beautiful post. The writers and editors of the Myassignmenthelpau platform are Ph.D. and Masters qualified professionals who strive to online Matlab assignment help services in Australia student achieve the highest possible grades in their academic program by helping them to submit flawless assignments every time. You can get in touch with them easily by making only a few clicks here and there.
Nice post. I used to be checking constantly this blog and I am impressed! Extremely useful info particularly the ultimate section 🙂 I take care of such information a lot. I was seeking this certain information for a long time. Thank you and best of luck. disadvantages of online classes during lockdown
咖啡除了有振奮精神之外,還與降低痛風、肝硬化、2型糖尿病、心髒病發作和中風的風險有關。 犀利士 、 ED是由哪些方面引起?
在正確的時間進行正確的篩查測試是一個人可以為自己的健康做的最重要的事情之一。篩查可以在您出現症狀之前及早發現疾病,如心臟病、糖尿病、勃起障礙等。 線上購買威而鋼 , 威而鋼的30分鐘起效時間,可用於性愛前戲
Hey! What a wonderful blog. I loved your blog. QuickBooks is the best accounting software, however, it has lots of bugs like QuickBooks Error. To fix such issues, you can contact experts via QuickBooks Customer Support Phone Number
Statistics is not only a mere branch of mathematics but also regarded to be an advanced version in the world of mathematics. The writers working in Statistics assignment help use their creative prowess to make the assignments cent percent original. Therefore, the assignments produced by Statistics assignment help have never ever been accused of plagiarism. Our experts are dealing with data and rescuing students globally for the last 6 years.
Hey , I found Your Blog is Amazing . As A content Writter You Explained Very Well In this . I learned alsot From Your Website . I Read Your Blog and and I would Like to Suggest You To Read This Blog Bellsouth Email Login Also. I surely believe that you will like it . Bellsouth.Net Email Login
This is absolutely the best information I have looking forward to get, and I must say that that you are doing a very nice job here in this fantastic blog. just keep it on, you are good. See funai departmental cut off mark
Mobilemall Bangladesh that is really an great work
Thanks for sharing this great informative article, found the discussion so helpful and beneficial. ffccibadan application form print out
Get Quick, Quality and A++ Assignment Help Adelaide by experienced writers. Contact us know for original Assignment help services in Adelaide Online. Visit us:-https://www.assignmenthelpexperts.com/assignment-help-adelaide/ Contact us at [email protected] or call us at +61-3-9088-1335 for more information.
On the internet, there are many blogs. However, your blog is definitely the best of them all. It has all the qualities that make a perfect blog. You can also read this article. We found this article very helpful for Norse mythology name generator .
Hey! Mind-blowing blog. Keep writing such beautiful blogs. In case you are struggling with issues on QuickBooks Enterprise Support (855)756-1077, dial QuickBooks Customer Service Number (855)885-5111. The team, on the other end, will assist you with the best technical services.
Hey! What a wonderful blog. I loved your blog. QuickBooks is the best accounting software; however, it has lots of bugs like QuickBooks Enterprise Support . To fix such issues, you can contact experts via QuickBooks Support Phone Number (855)963-5959.
Thank you so much such a nice blog writing, Directpointelectrical We are a team of expert Electrician offering wide range of electrical services in Australia and we offer premium support to our customers in Australia. directpointelectrical team has become the world leader in electrician filled. Electrician Frankston
A very good website. I have learned a lot from it. I'll recommend it to my friends. Thank you! Scrolling speed is measured by this mouse scroll test. You can learn more about it here Mouse scroll test .
This is a very unique and magnificent post with readable and informative content, I'm absolutely impressed. Thank you for sharing these amazing reads..... coe-agbor cut off mark for history
Airport Taxi Services is provided by professional drivers. Our drivers are always ready to provide first-class airport Cab service 24/7. Call now or book an early morning Airport ride online through the app SNUG RIDE. Airport taxi service includes a wide range of vehicles to fit all your needs. visit the website:http://www.croydoncar.co.uk/ Call:02086864000
Croydon MiniCab Service in London UK,We offer Low Fair for Airport Transfers from Croydon every day where you will be able to know all our services, our vehicles, page online booking to make a reservation every day 24x7 www.croydoncar.co.uk/
Hi there, thank you for sharing such a great informative post with us. It is really helpful. Java Program to Check Even and Odd Number Find the Factorial of a Number Find Area of Square, Rectangle and Circle Check Palindrome in Java
Post a Comment
- Active Directory (6)
- Delegation (2)
- End Users (7)
- Firewalls (1)
- Group Policy (1)
- Learning (4)
- Networking (1)
- Patching (2)
- Podcasts (1)
- Printers (1)
- Scripting (4)
- Security (11)
- Servers (6)
- SysAdmin Resources (7)
- Windows (9)
- WindowsXP/Vista (5)
Blog Archive
- ► May (1)
- ► April (2)
- ► March (2)
- ► January (1)
- ► December (1)
- ► August (1)
- ► April (1)
- ► March (5)
- ► February (7)
- ► February (6)
- ► September (4)
- ► August (4)
- ► July (9)
- ► June (7)
- ► May (3)
- ► April (5)
- ► March (7)
- ► February (18)
- ► January (14)
- ► November (3)
- ► October (12)
- ► August (8)
- ► July (13)
- ► May (8)
- ► April (9)
- ► February (10)
- ► January (15)
- ► December (4)
- ► November (4)
- ► October (10)
- ► September (22)
- ► August (17)
- ► July (21)
- ► June (20)
- ► May (14)
- ► April (23)
- ► March (16)
- ► February (23)
- ► January (27)
- ► December (12)
- ► November (18)
- ► October (19)
- ► September (11)
Contributors

an endpoint admin's journal
- Recent Posts
- Popular Posts
- Recent Comments

Deploy Trusted sites zone assignment using Intune
November 6, 2023

Zoom Desktop Client – Download older build versions from Zoom
October 31, 2023

Uninstall Teams chat app using remediation script and a configuration profile in Intune
October 30, 2023

Intune Last Check-in date not updating for Windows device
October 25, 2023

How to use Event Viewer to check cause of Blue screen of Death (BSOD)
October 23, 2023
5 Quick Mac OS Terminal commands to make a Mac user life easier

Powershell : Find disabled users and computers in AD
- Active Directory (1)
- Windows (7)
- November 2023
- October 2023
Deploy a set of trusted sites overriding users’ ability to add trusted sites themselves. To acheive this, an Intune configuration profile Trusted site zone assignment can be deployed to devices/users group as required.
Login to Intune Portal and navigate to: Devices > Windows > Configuration Profiles .
Hit the Create button and Select New policy

From the Create a profile menu, select Windows 10 and later for Platform , Templates for Profile type. Select Administrative templates and click Create .

Give the profile desired name and click Next .

In Configurations settings, select Computer Configuration and search for keyword “ Site to Zone “, Site to Zone Assignment List setting will be listed under search results. Go ahead click on it to Select it.

Once selected, a Site to Zone Assignment List page will appear on right side explaining different zones and values required for these zone for setup. Since this profile is being used for trusted sites, we will use the Value “2” . Go ahead and select Enabled button and start entering the trusted sites as required. please ensure to set each value to “2” . See example below:
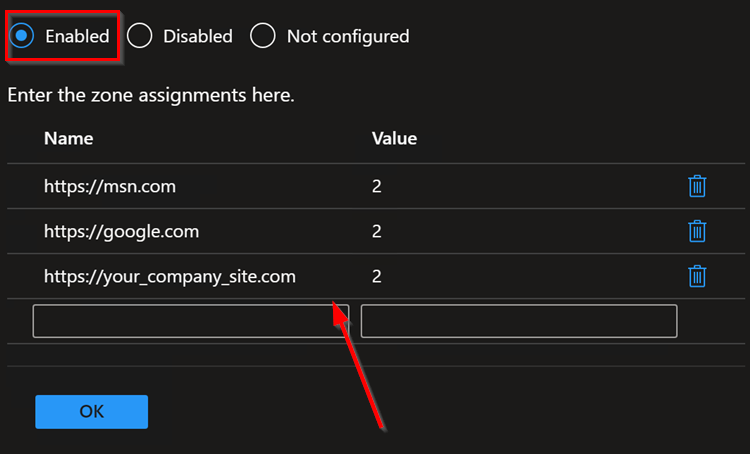
Once done adding the list of sites, click OK to close it and Hit Next on Configuration settings page.
Add Scope tags if needed.
Under Assignments , Click Add groups to target the policy deployment to specific group of devices/users. You can also select Add all users / All all devices .
Hit Next . Then Hit Review + Save button to save.
Tags: Intune Windows
You may also like...

[Windows 10] How to completely uninstall Flash player
Set your laptop screen’s brightness level to desired percentage every time you logon

- Previous Zoom Desktop Client – Download older build versions from Zoom
thanks! I was just looking for this exact solution!
The Federal Register
The daily journal of the united states government, request access.
Due to aggressive automated scraping of FederalRegister.gov and eCFR.gov, programmatic access to these sites is limited to access to our extensive developer APIs.
If you are human user receiving this message, we can add your IP address to a set of IPs that can access FederalRegister.gov & eCFR.gov; complete the CAPTCHA (bot test) below and click "Request Access". This process will be necessary for each IP address you wish to access the site from, requests are valid for approximately one quarter (three months) after which the process may need to be repeated.
An official website of the United States government.
If you want to request a wider IP range, first request access for your current IP, and then use the "Site Feedback" button found in the lower left-hand side to make the request.
This browser is no longer supported.
Upgrade to Microsoft Edge to take advantage of the latest features, security updates, and technical support.
Policy CSP - InternetExplorer
- 24 contributors
This CSP contains ADMX-backed policies which require a special SyncML format to enable or disable. You must specify the data type in the SyncML as <Format>chr</Format> . For details, see Understanding ADMX-backed policies .
The payload of the SyncML must be XML-encoded; for this XML encoding, there are a variety of online encoders that you can use. To avoid encoding the payload, you can use CDATA if your MDM supports it. For more information, see CDATA Sections .

This CSP contains some settings that are under development and only applicable for Windows Insider Preview builds . These settings are subject to change and may have dependencies on other features or services in preview.
AddSearchProvider
This policy setting allows you to add a specific list of search providers to the user's default list of search providers. Normally, search providers can be added from third-party toolbars or in Setup. The user can also add a search provider from the provider's website.
- If you enable this policy setting, the user can add and remove search providers, but only from the set of search providers specified in the list of policy keys for search providers (found under [HKCU or HKLM\Software\policies\Microsoft\Internet Explorer\SearchScopes]).
This list can be created from a custom administrative template file. For information about creating this custom administrative template file, see the Internet Explorer documentation on search providers.
- If you disable or don't configure this policy setting, the user can configure their list of search providers unless another policy setting restricts such configuration.
Description framework properties :
This is an ADMX-backed policy and requires SyncML format for configuration. For an example of SyncML format, refer to Enabling a policy .
ADMX mapping :
AllowActiveXFiltering
This policy setting controls the ActiveX Filtering feature for websites that are running ActiveX controls. The user can choose to turn off ActiveX Filtering for specific websites so that ActiveX controls can run properly.
If you enable this policy setting, ActiveX Filtering is enabled by default for the user. The user can't turn off ActiveX Filtering, although they may add per-site exceptions.
If you disable or don't configure this policy setting, ActiveX Filtering isn't enabled by default for the user. The user can turn ActiveX Filtering on or off.
AllowAddOnList
This policy setting allows you to manage a list of add-ons to be allowed or denied by Internet Explorer. Add-ons in this case are controls like ActiveX Controls, Toolbars, and Browser Helper Objects (BHOs) which are specifically written to extend or enhance the functionality of the browser or web pages.
This list can be used with the 'Deny all add-ons unless specifically allowed in the Add-on List' policy setting, which defines whether add-ons not listed here are assumed to be denied.
- If you enable this policy setting, you can enter a list of add-ons to be allowed or denied by Internet Explorer. For each entry that you add to the list, enter the following information:
Name of the Value - the CLSID (class identifier) for the add-on you wish to add to the list. The CLSID should be in brackets for example, '{000000000-0000-0000-0000-0000000000000}'. The CLSID for an add-on can be obtained by reading the OBJECT tag from a Web page on which the add-on is referenced.
Value - A number indicating whether Internet Explorer should deny or allow the add-on to be loaded. To specify that an add-on should be denied enter a 0 (zero) into this field. To specify that an add-on should be allowed, enter a 1 (one) into this field. To specify that an add-on should be allowed and also permit the user to manage the add-on through Add-on Manager, enter a 2 (two) into this field.
- If you disable this policy setting, the list is deleted. The 'Deny all add-ons unless specifically allowed in the Add-on List' policy setting will still determine whether add-ons not in this list are assumed to be denied.
AllowAutoComplete
This AutoComplete feature can remember and suggest User names and passwords on Forms.
If you enable this setting, the user can't change "User name and passwords on forms" or "prompt me to save passwords". The Auto Complete feature for User names and passwords on Forms will be turned on. You have to decide whether to select "prompt me to save passwords".
If you disable this setting the user can't change "User name and passwords on forms" or "prompt me to save passwords". The Auto Complete feature for User names and passwords on Forms is turned off. The user also can't opt to be prompted to save passwords.
If you don't configure this setting, the user has the freedom of turning on Auto complete for User name and passwords on forms and the option of prompting to save passwords. To display this option, the users open the Internet Options dialog box, click the Contents Tab and click the Settings button.
AllowCertificateAddressMismatchWarning
This policy setting allows you to turn on the certificate address mismatch security warning. When this policy setting is turned on, the user is warned when visiting Secure HTTP (HTTPS) websites that present certificates issued for a different website address. This warning helps prevent spoofing attacks.
If you enable this policy setting, the certificate address mismatch warning always appears.
If you disable or don't configure this policy setting, the user can choose whether the certificate address mismatch warning appears (by using the Advanced page in the Internet Control panel).
AllowDeletingBrowsingHistoryOnExit
This policy setting allows the automatic deletion of specified items when the last browser window closes. The preferences selected in the Delete Browsing History dialog box (such as deleting temporary Internet files, cookies, history, form data, and passwords) are applied, and those items are deleted.
If you enable this policy setting, deleting browsing history on exit's turned on.
If you disable this policy setting, deleting browsing history on exit's turned off.
If you don't configure this policy setting, it can be configured on the General tab in Internet Options.
If the "Prevent access to Delete Browsing History" policy setting is enabled, this policy setting has no effect.
AllowEnhancedProtectedMode
Enhanced Protected Mode provides additional protection against malicious websites by using 64-bit processes on 64-bit versions of Windows. For computers running at least Windows 8, Enhanced Protected Mode also limits the locations Internet Explorer can read from in the registry and the file system.
If you enable this policy setting, Enhanced Protected Mode will be turned on. Any zone that has Protected Mode enabled will use Enhanced Protected Mode. Users won't be able to disable Enhanced Protected Mode.
If you disable this policy setting, Enhanced Protected Mode will be turned off. Any zone that has Protected Mode enabled will use the version of Protected Mode introduced in Internet Explorer 7 for Windows Vista.
If you don't configure this policy, users will be able to turn on or turn off Enhanced Protected Mode on the Advanced tab of the Internet Options dialog.
AllowEnhancedSuggestionsInAddressBar
This policy setting allows Internet Explorer to provide enhanced suggestions as the user types in the Address bar. To provide enhanced suggestions, the user's keystrokes are sent to Microsoft through Microsoft services.
If you enable this policy setting, users receive enhanced suggestions while typing in the Address bar. In addition, users won't be able to change the Suggestions setting on the Settings charm.
If you disable this policy setting, users won't receive enhanced suggestions while typing in the Address bar. In addition, users won't be able to change the Suggestions setting on the Settings charm.
If you don't configure this policy setting, users can change the Suggestions setting on the Settings charm.
AllowEnterpriseModeFromToolsMenu
This policy setting lets you decide whether users can turn on Enterprise Mode for websites with compatibility issues. Optionally, this policy also lets you specify where to get reports (through post messages) about the websites for which users turn on Enterprise Mode using the Tools menu.
If you turn this setting on, users can see and use the Enterprise Mode option from the Tools menu. If you turn this setting on, but don't specify a report location, Enterprise Mode will still be available to your users, but you won't get any reports.
If you disable or don't configure this policy setting, the menu option won't appear and users won't be able to run websites in Enterprise Mode.
AllowEnterpriseModeSiteList
This policy setting lets you specify where to find the list of websites you want opened using Enterprise Mode IE, instead of Standard mode, because of compatibility issues. Users can't edit this list.
If you enable this policy setting, Internet Explorer downloads the website list from your location (HKCU or HKLM\Software\policies\Microsoft\Internet Explorer\Main\EnterpriseMode), opening all listed websites using Enterprise Mode IE.
If you disable or don't configure this policy setting, Internet Explorer opens all websites using Standards mode.
AllowFallbackToSSL3
This policy setting allows you to block an insecure fallback to SSL 3.0. When this policy is enabled, Internet Explorer will attempt to connect to sites using SSL 3.0 or below when TLS 1.0 or greater fails.
We recommend that you don't allow insecure fallback in order to prevent a man-in-the-middle attack.
This policy doesn't affect which security protocols are enabled.
If you disable this policy, system defaults will be used.
AllowInternetExplorer7PolicyList
This policy setting allows you to add specific sites that must be viewed in Internet Explorer 7 Compatibility View.
If you enable this policy setting, the user can add and remove sites from the list, but the user can't remove the entries that you specify.
If you disable or don't configure this policy setting, the user can add and remove sites from the list.
AllowInternetExplorerStandardsMode
This policy setting controls how Internet Explorer displays local intranet content. Intranet content is defined as any webpage that belongs to the local intranet security zone.
If you enable this policy setting, Internet Explorer uses the current user agent string for local intranet content. Additionally, all local intranet Standards Mode pages appear in the Standards Mode available with the latest version of Internet Explorer. The user can't change this behavior through the Compatibility View Settings dialog box.
If you disable this policy setting, Internet Explorer uses an Internet Explorer 7 user agent string (with an additional string appended) for local intranet content. Additionally, all local intranet Standards Mode pages appear in Internet Explorer 7 Standards Mode. The user can't change this behavior through the Compatibility View Settings dialog box.
If you don't configure this policy setting, Internet Explorer uses an Internet Explorer 7 user agent string (with an additional string appended) for local intranet content. Additionally, all local intranet Standards Mode pages appear in Internet Explorer 7 Standards Mode. This option results in the greatest compatibility with existing webpages, but newer content written to common Internet standards may be displayed incorrectly. This option matches the default behavior of Internet Explorer.
AllowInternetZoneTemplate
This template policy setting allows you to configure policy settings in this zone consistent with a selected security level, for example, Low, Medium Low, Medium, or High.
If you enable this template policy setting and select a security level, all values for individual settings in the zone will be overwritten by the standard template defaults.
If you disable this template policy setting, no security level is configured.
If you don't configure this template policy setting, no security level is configured.
Note. Local Machine Zone Lockdown Security and Network Protocol Lockdown operate by comparing the settings in the active URL's zone against those in the Locked-Down equivalent zone. If you select a security level for any zone (including selecting no security), the same change should be made to the Locked-Down equivalent.
Note. It's recommended to configure template policy settings in one Group Policy object (GPO) and configure any related individual policy settings in a separate GPO. You can then use Group Policy management features (for example, precedence, inheritance, or enforce) to apply individual settings to specific targets.
AllowIntranetZoneTemplate
Allowlocalmachinezonetemplate, allowlockeddowninternetzonetemplate, allowlockeddownintranetzonetemplate, allowlockeddownlocalmachinezonetemplate, allowlockeddownrestrictedsiteszonetemplate, allowonewordentry.
This policy allows the user to go directly to an intranet site for a one-word entry in the Address bar.
If you enable this policy setting, Internet Explorer goes directly to an intranet site for a one-word entry in the Address bar, if it's available.
If you disable or don't configure this policy setting, Internet Explorer doesn't go directly to an intranet site for a one-word entry in the Address bar.
AllowSaveTargetAsInIEMode
This policy setting allows admins to enable "Save Target As" context menu in Internet Explorer mode.
If you enable this policy, "Save Target As" will show up in the Internet Explorer mode context menu and work the same as Internet Explorer.
If you disable or don't configure this policy setting, "Save Target As" won't show up in the Internet Explorer mode context menu.
For more information, see https://go.microsoft.com/fwlink/?linkid=2102115
AllowSiteToZoneAssignmentList
This policy setting allows you to manage a list of sites that you want to associate with a particular security zone. These zone numbers have associated security settings that apply to all of the sites in the zone.
Internet Explorer has 4 security zones, numbered 1-4, and these are used by this policy setting to associate sites to zones. They are: (1) Intranet zone, (2) Trusted Sites zone, (3) Internet zone, and (4) Restricted Sites zone. Security settings can be set for each of these zones through other policy settings, and their default settings are: Trusted Sites zone (Low template), Intranet zone (Medium-Low template), Internet zone (Medium template), and Restricted Sites zone (High template). (The Local Machine zone and its locked down equivalent have special security settings that protect your local computer).
- If you enable this policy setting, you can enter a list of sites and their related zone numbers. The association of a site with a zone will ensure that the security settings for the specified zone are applied to the site. For each entry that you add to the list, enter the following information:
Valuename - A host for an intranet site, or a fully qualified domain name for other sites. The valuename may also include a specific protocol. For example, if you enter https://www.contoso.com as the valuename, other protocols aren't affected. If you enter just www.contoso.com , then all protocols are affected for that site, including http, https, ftp, and so on. The site may also be expressed as an IP address (e.g., 127.0.0.1) or range (e.g., 127.0.0.1-10). To avoid creating conflicting policies, don't include additional characters after the domain such as trailing slashes or URL path. For example, policy settings for www.contoso.com and www.contoso.com/mail would be treated as the same policy setting by Internet Explorer, and would therefore be in conflict.
Value - A number indicating the zone with which this site should be associated for security settings. The Internet Explorer zones described above are 1-4.
- If you disable or don't configure this policy, users may choose their own site-to-zone assignments.
This policy is a list that contains the site and index value.
The list is a set of pairs of strings. Each string is separated by F000. Each pair of strings is stored as a registry name and value. The registry name is the site and the value is an index. The index has to be sequential. See an example below.
Value and index pairs in the SyncML example:
- https://adfs.contoso.org 1
- https://microsoft.com 2
AllowsLockedDownTrustedSitesZoneTemplate
Allowsoftwarewhensignatureisinvalid.
This policy setting allows you to manage whether software, such as ActiveX controls and file downloads, can be installed or run by the user even though the signature is invalid. An invalid signature might indicate that someone has tampered with the file.
If you enable this policy setting, users will be prompted to install or run files with an invalid signature.
If you disable this policy setting, users can't run or install files with an invalid signature.
If you don't configure this policy, users can choose to run or install files with an invalid signature.
AllowsRestrictedSitesZoneTemplate
Allowsuggestedsites.
This policy setting controls the Suggested Sites feature, which recommends websites based on the user's browsing activity. Suggested Sites reports a user's browsing history to Microsoft to suggest sites that the user might want to visit.
If you enable this policy setting, the user isn't prompted to enable Suggested Sites. The user's browsing history is sent to Microsoft to produce suggestions.
If you disable this policy setting, the entry points and functionality associated with this feature are turned off.
If you don't configure this policy setting, the user can turn on and turn off the Suggested Sites feature.
AllowTrustedSitesZoneTemplate
Checkservercertificaterevocation.
This policy setting allows you to manage whether Internet Explorer will check revocation status of servers' certificates. Certificates are revoked when they've been compromised or are no longer valid, and this option protects users from submitting confidential data to a site that may be fraudulent or not secure.
If you enable this policy setting, Internet Explorer will check to see if server certificates have been revoked.
If you disable this policy setting, Internet Explorer won't check server certificates to see if they've been revoked.
If you don't configure this policy setting, Internet Explorer won't check server certificates to see if they've been revoked.
CheckSignaturesOnDownloadedPrograms
This policy setting allows you to manage whether Internet Explorer checks for digital signatures (which identifies the publisher of signed software and verifies it hasn't been modified or tampered with) on user computers before downloading executable programs.
If you enable this policy setting, Internet Explorer will check the digital signatures of executable programs and display their identities before downloading them to user computers.
If you disable this policy setting, Internet Explorer won't check the digital signatures of executable programs or display their identities before downloading them to user computers.
If you don't configure this policy, Internet Explorer won't check the digital signatures of executable programs or display their identities before downloading them to user computers.
ConfigureEdgeRedirectChannel
Enables you to configure up to three versions of Microsoft Edge to open a redirected site (in order of preference). Use this policy if your environment is configured to redirect sites from Internet Explorer 11 to Microsoft Edge. If any of the chosen versions aren't installed on the device, that preference will be bypassed.
If both the Windows Update for the next version of Microsoft Edge* and Microsoft Edge Stable channel are installed, the following behaviors occur:
If you disable or don't configure this policy, Microsoft Edge Stable channel is used. This is the default behavior.
If you enable this policy, you can configure redirected sites to open in up to three of the following channels where:
1 = Microsoft Edge Stable 2 = Microsoft Edge Beta version 77 or later 3 = Microsoft Edge Dev version 77 or later 4 = Microsoft Edge Canary version 77 or later.
If the Windows Update for the next version of Microsoft Edge* or Microsoft Edge Stable channel aren't installed, the following behaviors occur:
If you disable or don't configure this policy, Microsoft Edge version 45 or earlier is automatically used. This is the default behavior.
0 = Microsoft Edge version 45 or earlier 1 = Microsoft Edge Stable 2 = Microsoft Edge Beta version 77 or later 3 = Microsoft Edge Dev version 77 or later 4 = Microsoft Edge Canary version 77 or later.
- For more information about the Windows update for the next version of Microsoft Edge including how to disable it, see< https://go.microsoft.com/fwlink/?linkid=2102115> . This update applies only to Windows 10 version 1709 and higher.

ConsistentMimeHandlingInternetExplorerProcesses
Internet Explorer uses Multipurpose Internet Mail Extensions (MIME) data to determine file handling procedures for files received through a Web server.
This policy setting determines whether Internet Explorer requires that all file-type information provided by Web servers be consistent. For example, if the MIME type of a file is text/plain but the MIME sniff indicates that the file is really an executable file, Internet Explorer renames the file by saving it in the Internet Explorer cache and changing its extension.
If you enable this policy setting, Internet Explorer requires consistent MIME data for all received files.
If you disable this policy setting, Internet Explorer won't require consistent MIME data for all received files.
If you don't configure this policy setting, Internet Explorer requires consistent MIME data for all received files.
DisableActiveXVersionListAutoDownload
This setting determines whether IE automatically downloads updated versions of Microsoft's VersionList. XML. IE uses this file to determine whether an ActiveX control should be stopped from loading.
If you enable this setting, IE stops downloading updated versions of VersionList. XML. Turning off this automatic download breaks the out-of-date ActiveX control blocking feature by not letting the version list update with newly outdated controls, potentially compromising the security of your computer.
If you disable or don't configure this setting, IE continues to download updated versions of VersionList. XML.
For more information, see "Out-of-date ActiveX control blocking" in the Internet Explorer TechNet library.
DisableBypassOfSmartScreenWarnings
This policy setting determines whether the user can bypass warnings from SmartScreen Filter. SmartScreen Filter prevents the user from browsing to or downloading from sites that are known to host malicious content. SmartScreen Filter also prevents the execution of files that are known to be malicious.
If you enable this policy setting, SmartScreen Filter warnings block the user.
If you disable or don't configure this policy setting, the user can bypass SmartScreen Filter warnings.
DisableBypassOfSmartScreenWarningsAboutUncommonFiles
This policy setting determines whether the user can bypass warnings from SmartScreen Filter. SmartScreen Filter warns the user about executable files that Internet Explorer users don't commonly download from the Internet.
DisableCompatView
This policy setting controls the Compatibility View feature, which allows the user to fix website display problems that he or she may encounter while browsing.
If you enable this policy setting, the user can't use the Compatibility View button or manage the Compatibility View sites list.
If you disable or don't configure this policy setting, the user can use the Compatibility View button and manage the Compatibility View sites list.
DisableConfiguringHistory
This setting specifies the number of days that Internet Explorer tracks views of pages in the History List. To access the Temporary Internet Files and History Settings dialog box, from the Menu bar, on the Tools menu, click Internet Options, click the General tab, and then click Settings under Browsing history.
If you enable this policy setting, a user can't set the number of days that Internet Explorer tracks views of the pages in the History List. You must specify the number of days that Internet Explorer tracks views of pages in the History List. Users can't delete browsing history.
If you disable or don't configure this policy setting, a user can set the number of days that Internet Explorer tracks views of pages in the History list. Users can delete browsing history.
DisableCrashDetection
This policy setting allows you to manage the crash detection feature of add-on Management.
If you enable this policy setting, a crash in Internet Explorer will exhibit behavior found in Windows XP Professional Service Pack 1 and earlier, namely to invoke Windows Error Reporting. All policy settings for Windows Error Reporting continue to apply.
If you disable or don't configure this policy setting, the crash detection feature for add-on management will be functional.
DisableCustomerExperienceImprovementProgramParticipation
This policy setting prevents the user from participating in the Customer Experience Improvement Program (CEIP).
If you enable this policy setting, the user can't participate in the CEIP, and the Customer Feedback Options command doesn't appear on the Help menu.
If you disable this policy setting, the user must participate in the CEIP, and the Customer Feedback Options command doesn't appear on the Help menu.
If you don't configure this policy setting, the user can choose to participate in the CEIP.
DisableDeletingUserVisitedWebsites
This policy setting prevents the user from deleting the history of websites that he or she has visited. This feature is available in the Delete Browsing History dialog box.
If you enable this policy setting, websites that the user has visited are preserved when he or she clicks Delete.
If you disable this policy setting, websites that the user has visited are deleted when he or she clicks Delete.
If you don't configure this policy setting, the user can choose whether to delete or preserve visited websites when he or she clicks Delete.
If the "Prevent access to Delete Browsing History" policy setting is enabled, this policy setting is enabled by default.
DisableEnclosureDownloading
This policy setting prevents the user from having enclosures (file attachments) downloaded from a feed to the user's computer.
If you enable this policy setting, the user can't set the Feed Sync Engine to download an enclosure through the Feed property page. A developer can't change the download setting through the Feed APIs.
If you disable or don't configure this policy setting, the user can set the Feed Sync Engine to download an enclosure through the Feed property page. A developer can change the download setting through the Feed APIs.
DisableEncryptionSupport
This policy setting allows you to turn off support for Transport Layer Security (TLS) 1.0, TLS 1.1, TLS 1.2, Secure Sockets Layer (SSL) 2.0, or SSL 3.0 in the browser. TLS and SSL are protocols that help protect communication between the browser and the target server. When the browser attempts to set up a protected communication with the target server, the browser and server negotiate which protocol and version to use. The browser and server attempt to match each other's list of supported protocols and versions, and they select the most preferred match.
If you enable this policy setting, the browser negotiates or doesn't negotiate an encryption tunnel by using the encryption methods that you select from the drop-down list.
If you disable or don't configure this policy setting, the user can select which encryption method the browser supports.
SSL 2.0 is off by default and is no longer supported starting with Windows 10 Version 1607. SSL 2.0 is an outdated security protocol, and enabling SSL 2.0 impairs the performance and functionality of TLS 1.0.
DisableFeedsBackgroundSync
This policy setting controls whether to have background synchronization for feeds and Web Slices.
If you enable this policy setting, the ability to synchronize feeds and Web Slices in the background is turned off.
If you disable or don't configure this policy setting, the user can synchronize feeds and Web Slices in the background.
DisableFirstRunWizard
This policy setting prevents Internet Explorer from running the First Run wizard the first time a user starts the browser after installing Internet Explorer or Windows.
If you enable this policy setting, you must make one of the following choices:
Skip the First Run wizard, and go directly to the user's home page.
Skip the First Run wizard, and go directly to the "Welcome to Internet Explorer" webpage.
Starting with Windows 8, the "Welcome to Internet Explorer" webpage isn't available. The user's home page will display regardless of which option is chosen.
- If you disable or don't configure this policy setting, Internet Explorer may run the First Run wizard the first time the browser is started after installation.
DisableFlipAheadFeature
This policy setting determines whether a user can swipe across a screen or click Forward to go to the next pre-loaded page of a website.
Microsoft collects your browsing history to improve how flip ahead with page prediction works. This feature isn't available for Internet Explorer for the desktop.
If you enable this policy setting, flip ahead with page prediction is turned off and the next webpage isn't loaded into the background.
If you disable this policy setting, flip ahead with page prediction is turned on and the next webpage is loaded into the background.
If you don't configure this setting, users can turn this behavior on or off, using the Settings charm.
DisableGeolocation
This policy setting allows you to disable browser geolocation support. This will prevent websites from requesting location data about the user.
If you enable this policy setting, browser geolocation support is turned off.
If you disable this policy setting, browser geolocation support is turned on.
If you don't configure this policy setting, browser geolocation support can be turned on or off in Internet Options on the Privacy tab.
DisableHomePageChange
The Home page specified on the General tab of the Internet Options dialog box is the default Web page that Internet Explorer loads whenever it's run.
If you enable this policy setting, a user can't set a custom default home page. You must specify which default home page should load on the user machine. For machines with at least Internet Explorer 7, the home page can be set within this policy to override other home page policies.
If you disable or don't configure this policy setting, the Home page box is enabled and users can choose their own home page.
DisableHTMLApplication
This policy setting specifies if running the HTML Application (HTA file) is blocked or allowed.
If you enable this policy setting, running the HTML Application (HTA file) will be blocked.
If you disable or don't configure this policy setting, running the HTML Application (HTA file) is allowed.
DisableIgnoringCertificateErrors
This policy setting prevents the user from ignoring Secure Sockets Layer/Transport Layer Security (SSL/TLS) certificate errors that interrupt browsing (such as "expired", "revoked", or "name mismatch" errors) in Internet Explorer.
If you enable this policy setting, the user can't continue browsing.
If you disable or don't configure this policy setting, the user can choose to ignore certificate errors and continue browsing.
DisableInPrivateBrowsing
This policy setting allows you to turn off the InPrivate Browsing feature.
InPrivate Browsing prevents Internet Explorer from storing data about a user's browsing session. This includes cookies, temporary Internet files, history, and other data.
If you enable this policy setting, InPrivate Browsing is turned off.
If you disable this policy setting, InPrivate Browsing is available for use.
If you don't configure this policy setting, InPrivate Browsing can be turned on or off through the registry.
DisableInternetExplorerApp
This policy lets you restrict launching of Internet Explorer as a standalone browser.
If you enable this policy, it:
Prevents Internet Explorer 11 from launching as a standalone browser.
Restricts Internet Explorer's usage to Microsoft Edge's native 'Internet Explorer mode'.
Redirects all attempts at launching Internet Explorer 11 to Microsoft Edge Stable Channel browser.
Overrides any other policies that redirect to Internet Explorer 11.
If you disable, or don't configure this policy, all sites are opened using the current active browser settings.
Microsoft Edge Stable Channel must be installed for this policy to take effect.
DisableProcessesInEnhancedProtectedMode
Disableproxychange.
This policy setting specifies if a user can change proxy settings.
If you enable this policy setting, the user won't be able to configure proxy settings.
If you disable or don't configure this policy setting, the user can configure proxy settings.
DisableSearchProviderChange
This policy setting prevents the user from changing the default search provider for the Address bar and the toolbar Search box.
If you enable this policy setting, the user can't change the default search provider.
If you disable or don't configure this policy setting, the user can change the default search provider.
DisableSecondaryHomePageChange
Secondary home pages are the default Web pages that Internet Explorer loads in separate tabs from the home page whenever the browser is run. This policy setting allows you to set default secondary home pages.
If you enable this policy setting, you can specify which default home pages should load as secondary home pages. The user can't set custom default secondary home pages.
If you disable or don't configure this policy setting, the user can add secondary home pages.
If the "Disable Changing Home Page Settings" policy is enabled, the user can't add secondary home pages.
DisableSecuritySettingsCheck
This policy setting turns off the Security Settings Check feature, which checks Internet Explorer security settings to determine when the settings put Internet Explorer at risk.
If you enable this policy setting, the feature is turned off.
If you disable or don't configure this policy setting, the feature is turned on.
DisableUpdateCheck
Prevents Internet Explorer from checking whether a new version of the browser is available.
If you enable this policy, it prevents Internet Explorer from checking to see whether it's the latest available browser version and notifying users if a new version is available.
If you disable this policy or don't configure it, Internet Explorer checks every 30 days by default, and then notifies users if a new version is available.
This policy is intended to help the administrator maintain version control for Internet Explorer by preventing users from being notified about new versions of the browser.
DisableWebAddressAutoComplete
This AutoComplete feature suggests possible matches when users are entering Web addresses in the browser address bar.
If you enable this policy setting, user won't be suggested matches when entering Web addresses. The user can't change the auto-complete for web-address setting.
If you disable this policy setting, user will be suggested matches when entering Web addresses. The user can't change the auto-complete for web-address setting.
If you don't configure this policy setting, a user will have the freedom to choose to turn the auto-complete setting for web-addresses on or off.
DoNotAllowActiveXControlsInProtectedMode
This policy setting prevents ActiveX controls from running in Protected Mode when Enhanced Protected Mode is enabled. When a user has an ActiveX control installed that isn't compatible with Enhanced Protected Mode and a website attempts to load the control, Internet Explorer notifies the user and gives the option to run the website in regular Protected Mode. This policy setting disables this notification and forces all websites to run in Enhanced Protected Mode.
When Enhanced Protected Mode is enabled, and a user encounters a website that attempts to load an ActiveX control that isn't compatible with Enhanced Protected Mode, Internet Explorer notifies the user and gives the option to disable Enhanced Protected Mode for that particular website.
If you enable this policy setting, Internet Explorer won't give the user the option to disable Enhanced Protected Mode. All Protected Mode websites will run in Enhanced Protected Mode.
If you disable or don't configure this policy setting, Internet Explorer notifies users and provides an option to run websites with incompatible ActiveX controls in regular Protected Mode. This is the default behavior.
DoNotAllowUsersToAddSites
Prevents users from adding or removing sites from security zones. A security zone is a group of Web sites with the same security level.
If you enable this policy, the site management settings for security zones are disabled. (To see the site management settings for security zones, in the Internet Options dialog box, click the Security tab, and then click the Sites button).
If you disable this policy or don't configure it, users can add Web sites to or remove sites from the Trusted Sites and Restricted Sites zones, and alter settings for the Local Intranet zone.
This policy prevents users from changing site management settings for security zones established by the administrator.
The "Disable the Security page" policy (located in \User Configuration\Administrative Templates\Windows Components\Internet Explorer\Internet Control Panel), which removes the Security tab from the interface, takes precedence over this policy. If it's enabled, this policy is ignored.
Also, see the "Security zones: Use only machine settings" policy.
DoNotAllowUsersToChangePolicies
Prevents users from changing security zone settings. A security zone is a group of Web sites with the same security level.
If you enable this policy, the Custom Level button and security-level slider on the Security tab in the Internet Options dialog box are disabled.
If you disable this policy or don't configure it, users can change the settings for security zones.
This policy prevents users from changing security zone settings established by the administrator.
The "Disable the Security page" policy (located in \User Configuration\Administrative Templates\Windows Components\Internet Explorer\Internet Control Panel), which removes the Security tab from Internet Explorer in Control Panel, takes precedence over this policy. If it's enabled, this policy is ignored.
DoNotBlockOutdatedActiveXControls
This policy setting determines whether Internet Explorer blocks specific outdated ActiveX controls. Outdated ActiveX controls are never blocked in the Intranet Zone.
If you enable this policy setting, Internet Explorer stops blocking outdated ActiveX controls.
If you disable or don't configure this policy setting, Internet Explorer continues to block specific outdated ActiveX controls.
For more information, see "Outdated ActiveX Controls" in the Internet Explorer TechNet library.
DoNotBlockOutdatedActiveXControlsOnSpecificDomains
This policy setting allows you to manage a list of domains on which Internet Explorer will stop blocking outdated ActiveX controls. Outdated ActiveX controls are never blocked in the Intranet Zone.
- If you enable this policy setting, you can enter a custom list of domains for which outdated ActiveX controls won't be blocked in Internet Explorer. Each domain entry must be formatted like one of the following:
"domain.name. TLD". For example, if you want to include .contoso.com/ , use "contoso.com"
"hostname". For example, if you want to include https://example, use "example".
"file:///path/filename.htm". For example, use "file:///C:/Users/contoso/Desktop/index.htm".
- If you disable or don't configure this policy setting, the list is deleted and Internet Explorer continues to block specific outdated ActiveX controls on all domains in the Internet Zone.
EnableExtendedIEModeHotkeys
This policy setting lets admins enable extended Microsoft Edge Internet Explorer mode hotkeys, such as "Ctrl+S" to have "Save as" functionality.
If you enable this policy, extended hotkey functionality is enabled in Internet Explorer mode and work the same as Internet Explorer.
If you disable, or don't configure this policy, extended hotkeys won't work in Internet Explorer mode.
EnableGlobalWindowListInIEMode
This setting allows Internet Explorer mode to use the global window list that enables sharing state with other applications.
The setting will take effect only when Internet Explorer 11 is disabled as a standalone browser.
If you enable this policy, Internet Explorer mode will use the global window list.
If you disable or don't configure this policy, Internet Explorer mode will continue to maintain a separate window list.
To learn more about Internet Explorer mode, see https://go.microsoft.com/fwlink/?linkid=2102921 To learn more about disabling Internet Explorer 11 as a standalone browser, see https://go.microsoft.com/fwlink/?linkid=2168340
IncludeAllLocalSites
This policy setting controls whether local sites which aren't explicitly mapped into any Security Zone are forced into the local Intranet security zone.
If you enable this policy setting, local sites which aren't explicitly mapped into a zone are considered to be in the Intranet Zone.
If you disable this policy setting, local sites which aren't explicitly mapped into a zone won't be considered to be in the Intranet Zone (so would typically be in the Internet Zone).
If you don't configure this policy setting, users choose whether to force local sites into the Intranet Zone.
IncludeAllNetworkPaths
This policy setting controls whether URLs representing UNCs are mapped into the local Intranet security zone.
If you enable this policy setting, all network paths are mapped into the Intranet Zone.
If you disable this policy setting, network paths aren't necessarily mapped into the Intranet Zone (other rules might map one there).
If you don't configure this policy setting, users choose whether network paths are mapped into the Intranet Zone.
InternetZoneAllowAccessToDataSources
This policy setting allows you to manage whether Internet Explorer can access data from another security zone using the Microsoft XML Parser (MSXML) or ActiveX Data Objects (ADO).
If you enable this policy setting, users can load a page in the zone that uses MSXML or ADO to access data from another site in the zone. If you select Prompt in the drop-down box, users are queried to choose whether to allow a page to be loaded in the zone that uses MSXML or ADO to access data from another site in the zone.
If you disable this policy setting, users can't load a page in the zone that uses MSXML or ADO to access data from another site in the zone.
If you don't configure this policy setting, users can't load a page in the zone that uses MSXML or ADO to access data from another site in the zone.
InternetZoneAllowAutomaticPromptingForActiveXControls
This policy setting manages whether users will be automatically prompted for ActiveX control installations.
If you enable this policy setting, users will receive a prompt when a site instantiates an ActiveX control they don't have installed.
If you disable this policy setting, ActiveX control installations will be blocked using the Notification bar. Users can click on the Notification bar to allow the ActiveX control prompt.
If you don't configure this policy setting, ActiveX control installations will be blocked using the Notification bar. Users can click on the Notification bar to allow the ActiveX control prompt.
InternetZoneAllowAutomaticPromptingForFileDownloads
This policy setting determines whether users will be prompted for non user-initiated file downloads. Regardless of this setting, users will receive file download dialogs for user-initiated downloads.
If you enable this setting, users will receive a file download dialog for automatic download attempts.
If you disable or don't configure this setting, file downloads that aren't user-initiated will be blocked, and users will see the Notification bar instead of the file download dialog. Users can then click the Notification bar to allow the file download prompt.
InternetZoneAllowCopyPasteViaScript
This policy setting allows you to manage whether scripts can perform a clipboard operation (for example, cut, copy, and paste) in a specified region.
- If you enable this policy setting, a script can perform a clipboard operation.
If you select Prompt in the drop-down box, users are queried as to whether to perform clipboard operations.
If you disable this policy setting, a script can't perform a clipboard operation.
If you don't configure this policy setting, a script can perform a clipboard operation.
InternetZoneAllowDragAndDropCopyAndPasteFiles
This policy setting allows you to manage whether users can drag files or copy and paste files from a source within the zone.
If you enable this policy setting, users can drag files or copy and paste files from this zone automatically. If you select Prompt in the drop-down box, users are queried to choose whether to drag or copy files from this zone.
If you disable this policy setting, users are prevented from dragging files or copying and pasting files from this zone.
If you don't configure this policy setting, users can drag files or copy and paste files from this zone automatically.
InternetZoneAllowFontDownloads
This policy setting allows you to manage whether pages of the zone may download HTML fonts.
If you enable this policy setting, HTML fonts can be downloaded automatically.
If you enable this policy setting and Prompt is selected in the drop-down box, users are queried whether to allow HTML fonts to download.
If you disable this policy setting, HTML fonts are prevented from downloading.
If you don't configure this policy setting, HTML fonts can be downloaded automatically.
InternetZoneAllowLessPrivilegedSites
This policy setting allows you to manage whether Web sites from less privileged zones, such as Restricted Sites, can navigate into this zone.
If you enable this policy setting, Web sites from less privileged zones can open new windows in, or navigate into, this zone. The security zone will run without the added layer of security that's provided by the Protection from Zone Elevation security feature. If you select Prompt in the drop-down box, a warning is issued to the user that potentially risky navigation is about to occur.
If you disable this policy setting, the possibly harmful navigations is prevented. The Internet Explorer security feature will be on in this zone as set by Protection from Zone Elevation feature control.
If you don't configure this policy setting, Web sites from less privileged zones can open new windows in, or navigate into, this zone.
InternetZoneAllowLoadingOfXAMLFiles
This policy setting allows you to manage the loading of Extensible Application Markup Language (XAML) files. XAML is an XML-based declarative markup language commonly used for creating rich user interfaces and graphics that take advantage of the Windows Presentation Foundation.
If you enable this policy setting and set the drop-down box to Enable, XAML files are automatically loaded inside Internet Explorer. The user can't change this behavior. If you set the drop-down box to Prompt, the user is prompted for loading XAML files.
If you disable this policy setting, XAML files aren't loaded inside Internet Explorer. The user can't change this behavior.
If you don't configure this policy setting, the user can decide whether to load XAML files inside Internet Explorer.
InternetZoneAllowNETFrameworkReliantComponents
This policy setting allows you to manage whether . NET Framework components that aren't signed with Authenticode can be executed from Internet Explorer. These components include managed controls referenced from an object tag and managed executables referenced from a link.
If you enable this policy setting, Internet Explorer will execute unsigned managed components. If you select Prompt in the drop-down box, Internet Explorer will prompt the user to determine whether to execute unsigned managed components.
If you disable this policy setting, Internet Explorer won't execute unsigned managed components.
If you don't configure this policy setting, Internet Explorer will execute unsigned managed components.
InternetZoneAllowOnlyApprovedDomainsToUseActiveXControls
This policy setting controls whether or not the user is prompted to allow ActiveX controls to run on websites other than the website that installed the ActiveX control.
If you enable this policy setting, the user is prompted before ActiveX controls can run from websites in this zone. The user can choose to allow the control to run from the current site or from all sites.
If you disable this policy setting, the user doesn't see the per-site ActiveX prompt, and ActiveX controls can run from all sites in this zone.
InternetZoneAllowOnlyApprovedDomainsToUseTDCActiveXControl
This policy setting controls whether or not the user is allowed to run the TDC ActiveX control on websites.
If you enable this policy setting, the TDC ActiveX control won't run from websites in this zone.
If you disable this policy setting, the TDC Active X control will run from all sites in this zone.
InternetZoneAllowScriptingOfInternetExplorerWebBrowserControls
This policy setting determines whether a page can control embedded WebBrowser controls via script.
If you enable this policy setting, script access to the WebBrowser control is allowed.
If you disable this policy setting, script access to the WebBrowser control isn't allowed.
If you don't configure this policy setting, the user can enable or disable script access to the WebBrowser control. By default, script access to the WebBrowser control is allowed only in the Local Machine and Intranet zones.
InternetZoneAllowScriptInitiatedWindows
This policy setting allows you to manage restrictions on script-initiated pop-up windows and windows that include the title and status bars.
If you enable this policy setting, Windows Restrictions security won't apply in this zone. The security zone runs without the added layer of security provided by this feature.
If you disable this policy setting, the possible harmful actions contained in script-initiated pop-up windows and windows that include the title and status bars can't be run. This Internet Explorer security feature will be on in this zone as dictated by the Scripted Windows Security Restrictions feature control setting for the process.
If you don't configure this policy setting, the possible harmful actions contained in script-initiated pop-up windows and windows that include the title and status bars can't be run. This Internet Explorer security feature will be on in this zone as dictated by the Scripted Windows Security Restrictions feature control setting for the process.
InternetZoneAllowScriptlets
This policy setting allows you to manage whether the user can run scriptlets.
If you enable this policy setting, the user can run scriptlets.
If you disable this policy setting, the user can't run scriptlets.
If you don't configure this policy setting, the user can enable or disable scriptlets.
InternetZoneAllowSmartScreenIE
This policy setting controls whether SmartScreen Filter scans pages in this zone for malicious content.
If you enable this policy setting, SmartScreen Filter scans pages in this zone for malicious content.
If you disable this policy setting, SmartScreen Filter doesn't scan pages in this zone for malicious content.
If you don't configure this policy setting, the user can choose whether SmartScreen Filter scans pages in this zone for malicious content.
In Internet Explorer 7, this policy setting controls whether Phishing Filter scans pages in this zone for malicious content.
InternetZoneAllowUpdatesToStatusBarViaScript
This policy setting allows you to manage whether script is allowed to update the status bar within the zone.
If you enable this policy setting, script is allowed to update the status bar.
If you disable or don't configure this policy setting, script isn't allowed to update the status bar.
InternetZoneAllowUserDataPersistence
This policy setting allows you to manage the preservation of information in the browser's history, in favorites, in an XML store, or directly within a Web page saved to disk. When a user returns to a persisted page, the state of the page can be restored if this policy setting is appropriately configured.
If you enable this policy setting, users can preserve information in the browser's history, in favorites, in an XML store, or directly within a Web page saved to disk.
If you disable this policy setting, users can't preserve information in the browser's history, in favorites, in an XML store, or directly within a Web page saved to disk.
If you don't configure this policy setting, users can preserve information in the browser's history, in favorites, in an XML store, or directly within a Web page saved to disk.
InternetZoneAllowVBScriptToRunInInternetExplorer
This policy setting allows you to manage whether VBScript can be run on pages from the specified zone in Internet Explorer.
If you selected Enable in the drop-down box, VBScript can run without user intervention.
If you selected Prompt in the drop-down box, users are asked to choose whether to allow VBScript to run.
If you selected Disable in the drop-down box, VBScript is prevented from running.
If you don't configure or disable this policy setting, VBScript is prevented from running.
InternetZoneDoNotRunAntimalwareAgainstActiveXControls
This policy setting determines whether Internet Explorer runs antimalware programs against ActiveX controls, to check if they're safe to load on pages.
If you enable this policy setting, Internet Explorer won't check with your antimalware program to see if it's safe to create an instance of the ActiveX control.
If you disable this policy setting, Internet Explorer always checks with your antimalware program to see if it's safe to create an instance of the ActiveX control.
If you don't configure this policy setting, Internet Explorer always checks with your antimalware program to see if it's safe to create an instance of the ActiveX control. Users can turn this behavior on or off, using Internet Explorer Security settings.
InternetZoneDownloadSignedActiveXControls
This policy setting allows you to manage whether users may download signed ActiveX controls from a page in the zone.
If you enable this policy, users can download signed controls without user intervention. If you select Prompt in the drop-down box, users are queried whether to download controls signed by publishers who aren't trusted. Code signed by trusted publishers is silently downloaded.
If you disable the policy setting, signed controls can't be downloaded.
If you don't configure this policy setting, users are queried whether to download controls signed by publishers who aren't trusted. Code signed by trusted publishers is silently downloaded.
InternetZoneDownloadUnsignedActiveXControls
This policy setting allows you to manage whether users may download unsigned ActiveX controls from the zone. Such code is potentially harmful, especially when coming from an untrusted zone.
If you enable this policy setting, users can run unsigned controls without user intervention. If you select Prompt in the drop-down box, users are queried to choose whether to allow the unsigned control to run.
If you disable this policy setting, users can't run unsigned controls.
If you don't configure this policy setting, users can't run unsigned controls.
InternetZoneEnableCrossSiteScriptingFilter
This policy controls whether or not the Cross-Site Scripting (XSS) Filter will detect and prevent cross-site script injections into websites in this zone.
If you enable this policy setting, the XSS Filter is turned on for sites in this zone, and the XSS Filter attempts to block cross-site script injections.
If you disable this policy setting, the XSS Filter is turned off for sites in this zone, and Internet Explorer permits cross-site script injections.
InternetZoneEnableDraggingOfContentFromDifferentDomainsAcrossWindows
This policy setting allows you to set options for dragging content from one domain to a different domain when the source and destination are in different windows.
If you enable this policy setting and click Enable, users can drag content from one domain to a different domain when the source and destination are in different windows. Users can't change this setting.
If you enable this policy setting and click Disable, users can't drag content from one domain to a different domain when both the source and destination are in different windows. Users can't change this setting.
In Internet Explorer 10, if you disable this policy setting or don't configure it, users can't drag content from one domain to a different domain when the source and destination are in different windows. Users can change this setting in the Internet Options dialog.
In Internet Explorer 9 and earlier versions, if you disable this policy or don't configure it, users can drag content from one domain to a different domain when the source and destination are in different windows. Users can't change this setting.
InternetZoneEnableDraggingOfContentFromDifferentDomainsWithinWindows
This policy setting allows you to set options for dragging content from one domain to a different domain when the source and destination are in the same window.
If you enable this policy setting and click Enable, users can drag content from one domain to a different domain when the source and destination are in the same window. Users can't change this setting.
If you enable this policy setting and click Disable, users can't drag content from one domain to a different domain when the source and destination are in the same window. Users can't change this setting in the Internet Options dialog.
In Internet Explorer 10, if you disable this policy setting or don't configure it, users can't drag content from one domain to a different domain when the source and destination are in the same window. Users can change this setting in the Internet Options dialog.
In Internet Explorer 9 and earlier versions, if you disable this policy setting or don't configure it, users can drag content from one domain to a different domain when the source and destination are in the same window. Users can't change this setting in the Internet Options dialog.
InternetZoneEnableMIMESniffing
This policy setting allows you to manage MIME sniffing for file promotion from one type to another based on a MIME sniff. A MIME sniff is the recognition by Internet Explorer of the file type based on a bit signature.
If you enable this policy setting, the MIME Sniffing Safety Feature won't apply in this zone. The security zone will run without the added layer of security provided by this feature.
If you disable this policy setting, the actions that may be harmful can't run; this Internet Explorer security feature will be turned on in this zone, as dictated by the feature control setting for the process.
If you don't configure this policy setting, the MIME Sniffing Safety Feature won't apply in this zone.
InternetZoneEnableProtectedMode
This policy setting allows you to turn on Protected Mode. Protected Mode helps protect Internet Explorer from exploited vulnerabilities by reducing the locations that Internet Explorer can write to in the registry and the file system.
If you enable this policy setting, Protected Mode is turned on. The user can't turn off Protected Mode.
If you disable this policy setting, Protected Mode is turned off. The user can't turn on Protected Mode.
If you don't configure this policy setting, the user can turn on or turn off Protected Mode.
InternetZoneIncludeLocalPathWhenUploadingFilesToServer
This policy setting controls whether or not local path information is sent when the user is uploading a file via an HTML form. If the local path information is sent, some information may be unintentionally revealed to the server. For instance, files sent from the user's desktop may contain the user name as a part of the path.
If you enable this policy setting, path information is sent when the user is uploading a file via an HTML form.
If you disable this policy setting, path information is removed when the user is uploading a file via an HTML form.
If you don't configure this policy setting, the user can choose whether path information is sent when he or she is uploading a file via an HTML form. By default, path information is sent.
InternetZoneInitializeAndScriptActiveXControls
This policy setting allows you to manage ActiveX controls not marked as safe.
If you enable this policy setting, ActiveX controls are run, loaded with parameters, and scripted without setting object safety for untrusted data or scripts. This setting isn't recommended, except for secure and administered zones. This setting causes both unsafe and safe controls to be initialized and scripted, ignoring the Script ActiveX controls marked safe for scripting option.
If you enable this policy setting and select Prompt in the drop-down box, users are queried whether to allow the control to be loaded with parameters or scripted.
If you disable this policy setting, ActiveX controls that can't be made safe aren't loaded with parameters or scripted.
If you don't configure this policy setting, ActiveX controls that can't be made safe aren't loaded with parameters or scripted.
InternetZoneJavaPermissions
This policy setting allows you to manage permissions for Java applets.
- If you enable this policy setting, you can choose options from the drop-down box. Custom, to control permissions settings individually.
Low Safety enables applets to perform all operations.
Medium Safety enables applets to run in their sandbox (an area in memory outside of which the program can't make calls), plus capabilities like scratch space (a safe and secure storage area on the client computer) and user-controlled file I/O.
High Safety enables applets to run in their sandbox. Disable Java to prevent any applets from running.
If you disable this policy setting, Java applets can't run.
If you don't configure this policy setting, the permission is set to High Safety.
InternetZoneLaunchingApplicationsAndFilesInIFRAME
This policy setting allows you to manage whether applications may be run and files may be downloaded from an IFRAME reference in the HTML of the pages in this zone.
If you enable this policy setting, users can run applications and download files from IFRAMEs on the pages in this zone without user intervention. If you select Prompt in the drop-down box, users are queried to choose whether to run applications and download files from IFRAMEs on the pages in this zone.
If you disable this policy setting, users are prevented from running applications and downloading files from IFRAMEs on the pages in this zone.
If you don't configure this policy setting, users are queried to choose whether to run applications and download files from IFRAMEs on the pages in this zone.
InternetZoneLogonOptions
This policy setting allows you to manage settings for logon options.
- If you enable this policy setting, you can choose from the following logon options.
Anonymous logon to disable HTTP authentication and use the guest account only for the Common Internet File System (CIFS) protocol.
Prompt for user name and password to query users for user IDs and passwords. After a user is queried, these values can be used silently for the remainder of the session.
Automatic logon only in Intranet zone to query users for user IDs and passwords in other zones. After a user is queried, these values can be used silently for the remainder of the session.
Automatic logon with current user name and password to attempt logon using Windows NT Challenge Response (also known as NTLM authentication). If Windows NT Challenge Response is supported by the server, the logon uses the user's network user name and password for logon. If Windows NT Challenge Response isn't supported by the server, the user is queried to provide the user name and password.
If you disable this policy setting, logon is set to Automatic logon only in Intranet zone.
If you don't configure this policy setting, logon is set to Automatic logon only in Intranet zone.
InternetZoneNavigateWindowsAndFrames
This policy setting allows you to manage the opening of windows and frames and access of applications across different domains.
If you enable this policy setting, users can open windows and frames from other domains and access applications from other domains. If you select Prompt in the drop-down box, users are queried whether to allow windows and frames to access applications from other domains.
If you disable this policy setting, users can't open windows and frames to access applications from different domains.
If you don't configure this policy setting, users can open windows and frames from other domains and access applications from other domains.
InternetZoneRunNETFrameworkReliantComponentsSignedWithAuthenticode
This policy setting allows you to manage whether . NET Framework components that are signed with Authenticode can be executed from Internet Explorer. These components include managed controls referenced from an object tag and managed executables referenced from a link.
If you enable this policy setting, Internet Explorer will execute signed managed components. If you select Prompt in the drop-down box, Internet Explorer will prompt the user to determine whether to execute signed managed components.
If you disable this policy setting, Internet Explorer won't execute signed managed components.
If you don't configure this policy setting, Internet Explorer will execute signed managed components.
InternetZoneShowSecurityWarningForPotentiallyUnsafeFiles
This policy setting controls whether or not the "Open File - Security Warning" message appears when the user tries to open executable files or other potentially unsafe files (from an intranet file share by using File Explorer, for example).
If you enable this policy setting and set the drop-down box to Enable, these files open without a security warning. If you set the drop-down box to Prompt, a security warning appears before the files open.
If you disable this policy setting, these files don't open.
If you don't configure this policy setting, the user can configure how the computer handles these files. By default, these files are blocked in the Restricted zone, enabled in the Intranet and Local Computer zones, and set to prompt in the Internet and Trusted zones.
InternetZoneUsePopupBlocker
This policy setting allows you to manage whether unwanted pop-up windows appear. Pop-up windows that are opened when the end user clicks a link aren't blocked.
If you enable this policy setting, most unwanted pop-up windows are prevented from appearing.
If you disable this policy setting, pop-up windows aren't prevented from appearing.
If you don't configure this policy setting, most unwanted pop-up windows are prevented from appearing.
IntranetZoneAllowAccessToDataSources
If you don't configure this policy setting, users are queried to choose whether to allow a page to be loaded in the zone that uses MSXML or ADO to access data from another site in the zone.
IntranetZoneAllowAutomaticPromptingForActiveXControls
If you don't configure this policy setting, users will receive a prompt when a site instantiates an ActiveX control they don't have installed.
IntranetZoneAllowAutomaticPromptingForFileDownloads
If you disable or don't configure this setting, users will receive a file download dialog for automatic download attempts.
IntranetZoneAllowFontDownloads
Intranetzoneallowlessprivilegedsites, intranetzoneallownetframeworkreliantcomponents, intranetzoneallowscriptlets, intranetzoneallowsmartscreenie, intranetzoneallowuserdatapersistence, intranetzonedonotrunantimalwareagainstactivexcontrols.
If you don't configure this policy setting, Internet Explorer won't check with your antimalware program to see if it's safe to create an instance of the ActiveX control. Users can turn this behavior on or off, using Internet Explorer Security settings.
IntranetZoneInitializeAndScriptActiveXControls
Intranetzonejavapermissions.
If you don't configure this policy setting, the permission is set to Medium Safety.
IntranetZoneLogonOptions
Intranetzonenavigatewindowsandframes, jscriptreplacement.
This policy setting specifies whether JScript or JScript9Legacy is loaded for MSHTML/WebOC/MSXML/Cscript based invocations.
If you enable this policy setting, JScript9Legacy will be loaded in situations where JScript is instantiated.
If you disable this policy, then JScript will be utilized.
If this policy is left unconfigured, then MSHTML will use JScript9Legacy and MSXML/Cscript will use JScript.
KeepIntranetSitesInInternetExplorer
Prevents intranet sites from being opened in any browser except Internet Explorer. But note that If the 'Send all sites not included in the Enterprise Mode Site List to Microsoft Edge' ('RestrictIE') policy isn't enabled, this policy has no effect.
If you enable this policy, all intranet sites are opened in Internet Explorer 11. The only exceptions are sites listed in your Enterprise Mode Site List.
If you disable or don't configure this policy, all intranet sites are automatically opened in Microsoft Edge.
We strongly recommend keeping this policy in sync with the 'Send all intranet sites to Internet Explorer' ('SendIntranetToInternetExplorer') policy. Additionally, it's best to enable this policy only if your intranet sites have known compatibility problems with Microsoft Edge.
Related policies:
- Send all intranet sites to Internet Explorer ('SendIntranetToInternetExplorer')
- Send all sites not included in the Enterprise Mode Site List to Microsoft Edge ('RestrictIE')
For more info about how to use this policy together with other related policies to create the optimal configuration for your organization, see< https://go.microsoft.com/fwlink/?linkid=2094210> .
LocalMachineZoneAllowAccessToDataSources
If you don't configure this policy setting, users can load a page in the zone that uses MSXML or ADO to access data from another site in the zone.
LocalMachineZoneAllowAutomaticPromptingForActiveXControls
Localmachinezoneallowautomaticpromptingforfiledownloads, localmachinezoneallowfontdownloads, localmachinezoneallowlessprivilegedsites.
This policy setting allows you to manage whether Web sites from less privileged zones, such as Internet sites, can navigate into this zone.
If you don't configure this policy setting, the possibly harmful navigations is prevented. The Internet Explorer security feature will be on in this zone as set by Protection from Zone Elevation feature control.
LocalMachineZoneAllowNETFrameworkReliantComponents
If you don't configure this policy setting, Internet Explorer won't execute unsigned managed components.
LocalMachineZoneAllowScriptlets
Localmachinezoneallowsmartscreenie, localmachinezoneallowuserdatapersistence, localmachinezonedonotrunantimalwareagainstactivexcontrols, localmachinezoneinitializeandscriptactivexcontrols.
If you don't configure this policy setting, users are queried whether to allow the control to be loaded with parameters or scripted.
LocalMachineZoneJavaPermissions
Localmachinezonelogonoptions.
If you don't configure this policy setting, logon is set to Automatic logon with current username and password.
LocalMachineZoneNavigateWindowsAndFrames
Lockeddowninternetzoneallowaccesstodatasources, lockeddowninternetzoneallowautomaticpromptingforactivexcontrols, lockeddowninternetzoneallowautomaticpromptingforfiledownloads, lockeddowninternetzoneallowfontdownloads, lockeddowninternetzoneallowlessprivilegedsites, lockeddowninternetzoneallownetframeworkreliantcomponents, lockeddowninternetzoneallowscriptlets, lockeddowninternetzoneallowsmartscreenie, lockeddowninternetzoneallowuserdatapersistence, lockeddowninternetzoneinitializeandscriptactivexcontrols, lockeddowninternetzonejavapermissions.
If you don't configure this policy setting, Java applets are disabled.
LockedDownInternetZoneNavigateWindowsAndFrames
Lockeddownintranetjavapermissions, lockeddownintranetzoneallowaccesstodatasources, lockeddownintranetzoneallowautomaticpromptingforactivexcontrols, lockeddownintranetzoneallowautomaticpromptingforfiledownloads, lockeddownintranetzoneallowfontdownloads, lockeddownintranetzoneallowlessprivilegedsites, lockeddownintranetzoneallownetframeworkreliantcomponents, lockeddownintranetzoneallowscriptlets, lockeddownintranetzoneallowsmartscreenie, lockeddownintranetzoneallowuserdatapersistence, lockeddownintranetzoneinitializeandscriptactivexcontrols, lockeddownintranetzonenavigatewindowsandframes, lockeddownlocalmachinezoneallowaccesstodatasources, lockeddownlocalmachinezoneallowautomaticpromptingforactivexcontrols, lockeddownlocalmachinezoneallowautomaticpromptingforfiledownloads, lockeddownlocalmachinezoneallowfontdownloads, lockeddownlocalmachinezoneallowlessprivilegedsites, lockeddownlocalmachinezoneallownetframeworkreliantcomponents, lockeddownlocalmachinezoneallowscriptlets, lockeddownlocalmachinezoneallowsmartscreenie, lockeddownlocalmachinezoneallowuserdatapersistence, lockeddownlocalmachinezoneinitializeandscriptactivexcontrols, lockeddownlocalmachinezonejavapermissions, lockeddownlocalmachinezonenavigatewindowsandframes, lockeddownrestrictedsiteszoneallowaccesstodatasources, lockeddownrestrictedsiteszoneallowautomaticpromptingforactivexcontrols, lockeddownrestrictedsiteszoneallowautomaticpromptingforfiledownloads, lockeddownrestrictedsiteszoneallowfontdownloads.
If you don't configure this policy setting, users are queried whether to allow HTML fonts to download.
LockedDownRestrictedSitesZoneAllowLessPrivilegedSites
Lockeddownrestrictedsiteszoneallownetframeworkreliantcomponents, lockeddownrestrictedsiteszoneallowscriptlets, lockeddownrestrictedsiteszoneallowsmartscreenie, lockeddownrestrictedsiteszoneallowuserdatapersistence.
If you don't configure this policy setting, users can't preserve information in the browser's history, in favorites, in an XML store, or directly within a Web page saved to disk.
LockedDownRestrictedSitesZoneInitializeAndScriptActiveXControls
Lockeddownrestrictedsiteszonejavapermissions, lockeddownrestrictedsiteszonenavigatewindowsandframes.
If you enable this policy setting, users can open additional windows and frames from other domains and access applications from other domains. If you select Prompt in the drop-down box, users are queried whether to allow additional windows and frames to access applications from other domains.
If you disable this policy setting, users can't open other windows and frames from other domains or access applications from different domains.
If you don't configure this policy setting, users can't open other windows and frames from different domains or access applications from different domains.
LockedDownTrustedSitesZoneAllowAccessToDataSources
Lockeddowntrustedsiteszoneallowautomaticpromptingforactivexcontrols, lockeddowntrustedsiteszoneallowautomaticpromptingforfiledownloads, lockeddowntrustedsiteszoneallowfontdownloads, lockeddowntrustedsiteszoneallowlessprivilegedsites, lockeddowntrustedsiteszoneallownetframeworkreliantcomponents, lockeddowntrustedsiteszoneallowscriptlets, lockeddowntrustedsiteszoneallowsmartscreenie, lockeddowntrustedsiteszoneallowuserdatapersistence, lockeddowntrustedsiteszoneinitializeandscriptactivexcontrols, lockeddowntrustedsiteszonejavapermissions, lockeddowntrustedsiteszonenavigatewindowsandframes, mimesniffingsafetyfeatureinternetexplorerprocesses.
This policy setting determines whether Internet Explorer MIME sniffing will prevent promotion of a file of one type to a more dangerous file type.
If you enable this policy setting, MIME sniffing will never promote a file of one type to a more dangerous file type.
If you disable this policy setting, Internet Explorer processes will allow a MIME sniff promoting a file of one type to a more dangerous file type.
If you don't configure this policy setting, MIME sniffing will never promote a file of one type to a more dangerous file type.
MKProtocolSecurityRestrictionInternetExplorerProcesses
The MK Protocol Security Restriction policy setting reduces attack surface area by preventing the MK protocol. Resources hosted on the MK protocol will fail.
If you enable this policy setting, the MK Protocol is prevented for File Explorer and Internet Explorer, and resources hosted on the MK protocol will fail.
If you disable this policy setting, applications can use the MK protocol API. Resources hosted on the MK protocol will work for the File Explorer and Internet Explorer processes.
If you don't configure this policy setting, the MK Protocol is prevented for File Explorer and Internet Explorer, and resources hosted on the MK protocol will fail.
NewTabDefaultPage
This policy setting allows you to specify what's displayed when the user opens a new tab.
If you enable this policy setting, you can choose which page to display when the user opens a new tab: blank page (about:blank), the first home page, the new tab page or the new tab page with my news feed.
If you disable or don't configure this policy setting, the user can select his or her preference for this behavior.
NotificationBarInternetExplorerProcesses
This policy setting allows you to manage whether the Notification bar is displayed for Internet Explorer processes when file or code installs are restricted. By default, the Notification bar is displayed for Internet Explorer processes.
If you enable this policy setting, the Notification bar will be displayed for Internet Explorer Processes.
If you disable this policy setting, the Notification bar won't be displayed for Internet Explorer processes.
If you don't configure this policy setting, the Notification bar will be displayed for Internet Explorer Processes.
PreventManagingSmartScreenFilter
This policy setting prevents the user from managing SmartScreen Filter, which warns the user if the website being visited is known for fraudulent attempts to gather personal information through "phishing," or is known to host malware.
If you enable this policy setting, the user isn't prompted to turn on SmartScreen Filter. All website addresses that aren't on the filter's allow list are sent automatically to Microsoft without prompting the user.
If you disable or don't configure this policy setting, the user is prompted to decide whether to turn on SmartScreen Filter during the first-run experience.
PreventPerUserInstallationOfActiveXControls
This policy setting allows you to prevent the installation of ActiveX controls on a per-user basis.
If you enable this policy setting, ActiveX controls can't be installed on a per-user basis.
If you disable or don't configure this policy setting, ActiveX controls can be installed on a per-user basis.
ProtectionFromZoneElevationInternetExplorerProcesses
Internet Explorer places restrictions on each Web page it opens. The restrictions are dependent upon the location of the Web page (Internet, Intranet, Local Machine zone, etc.). Web pages on the local computer have the fewest security restrictions and reside in the Local Machine zone, making the Local Machine security zone a prime target for malicious users. Zone Elevation also disables JavaScript navigation if there is no security context.
If you enable this policy setting, any zone can be protected from zone elevation by Internet Explorer processes.
If you disable this policy setting, no zone receives such protection for Internet Explorer processes.
If you don't configure this policy setting, any zone can be protected from zone elevation by Internet Explorer processes.
RemoveRunThisTimeButtonForOutdatedActiveXControls
This policy setting allows you to stop users from seeing the "Run this time" button and from running specific outdated ActiveX controls in Internet Explorer.
If you enable this policy setting, users won't see the "Run this time" button on the warning message that appears when Internet Explorer blocks an outdated ActiveX control.
If you disable or don't configure this policy setting, users will see the "Run this time" button on the warning message that appears when Internet Explorer blocks an outdated ActiveX control. Clicking this button lets the user run the outdated ActiveX control once.
ResetZoomForDialogInIEMode
This policy setting lets admins reset zoom to default for HTML dialogs in Internet Explorer mode.
If you enable this policy, the zoom of an HTML dialog in Internet Explorer mode won't get propagated from its parent page.
If you disable, or don't configure this policy, the zoom of an HTML dialog in Internet Explorer mode will be set based on the zoom of it's parent page.
RestrictActiveXInstallInternetExplorerProcesses
This policy setting enables blocking of ActiveX control installation prompts for Internet Explorer processes.
If you enable this policy setting, prompting for ActiveX control installations will be blocked for Internet Explorer processes.
If you disable this policy setting, prompting for ActiveX control installations won't be blocked for Internet Explorer processes.
If you don't configure this policy setting, the user's preference will be used to determine whether to block ActiveX control installations for Internet Explorer processes.
RestrictedSitesZoneAllowAccessToDataSources
Restrictedsiteszoneallowactivescripting.
This policy setting allows you to manage whether script code on pages in the zone is run.
If you enable this policy setting, script code on pages in the zone can run automatically. If you select Prompt in the drop-down box, users are queried to choose whether to allow script code on pages in the zone to run.
If you disable this policy setting, script code on pages in the zone is prevented from running.
If you don't configure this policy setting, script code on pages in the zone is prevented from running.
RestrictedSitesZoneAllowAutomaticPromptingForActiveXControls
Restrictedsiteszoneallowautomaticpromptingforfiledownloads, restrictedsiteszoneallowbinaryandscriptbehaviors.
This policy setting allows you to manage dynamic binary and script behaviors: components that encapsulate specific functionality for HTML elements to which they were attached.
If you enable this policy setting, binary and script behaviors are available. If you select Administrator approved in the drop-down box, only behaviors listed in the Admin-approved Behaviors under Binary Behaviors Security Restriction policy are available.
If you disable this policy setting, binary and script behaviors aren't available unless applications have implemented a custom security manager.
If you don't configure this policy setting, binary and script behaviors aren't available unless applications have implemented a custom security manager.
RestrictedSitesZoneAllowCopyPasteViaScript
If you don't configure this policy setting, a script can't perform a clipboard operation.
RestrictedSitesZoneAllowDragAndDropCopyAndPasteFiles
If you don't configure this policy setting, users are queried to choose whether to drag or copy files from this zone.
RestrictedSitesZoneAllowFileDownloads
This policy setting allows you to manage whether file downloads are permitted from the zone. This option is determined by the zone of the page with the link causing the download, not the zone from which the file is delivered.
If you enable this policy setting, files can be downloaded from the zone.
If you disable this policy setting, files are prevented from being downloaded from the zone.
If you don't configure this policy setting, files are prevented from being downloaded from the zone.
RestrictedSitesZoneAllowFontDownloads
Restrictedsiteszoneallowlessprivilegedsites, restrictedsiteszoneallowloadingofxamlfiles, restrictedsiteszoneallowmetarefresh.
This policy setting allows you to manage whether a user's browser can be redirected to another Web page if the author of the Web page uses the Meta Refresh setting (tag) to redirect browsers to another Web page.
If you enable this policy setting, a user's browser that loads a page containing an active Meta Refresh setting can be redirected to another Web page.
If you disable this policy setting, a user's browser that loads a page containing an active Meta Refresh setting can't be redirected to another Web page.
If you don't configure this policy setting, a user's browser that loads a page containing an active Meta Refresh setting can't be redirected to another Web page.
RestrictedSitesZoneAllowNETFrameworkReliantComponents
Restrictedsiteszoneallowonlyapproveddomainstouseactivexcontrols, restrictedsiteszoneallowonlyapproveddomainstousetdcactivexcontrol, restrictedsiteszoneallowscriptingofinternetexplorerwebbrowsercontrols, restrictedsiteszoneallowscriptinitiatedwindows, restrictedsiteszoneallowscriptlets, restrictedsiteszoneallowsmartscreenie, restrictedsiteszoneallowupdatestostatusbarviascript, restrictedsiteszoneallowuserdatapersistence, restrictedsiteszoneallowvbscripttorunininternetexplorer, restrictedsiteszonedonotrunantimalwareagainstactivexcontrols, restrictedsiteszonedownloadsignedactivexcontrols.
If you don't configure this policy setting, signed controls can't be downloaded.
RestrictedSitesZoneDownloadUnsignedActiveXControls
Restrictedsiteszoneenablecrosssitescriptingfilter, restrictedsiteszoneenabledraggingofcontentfromdifferentdomainsacrosswindows, restrictedsiteszoneenabledraggingofcontentfromdifferentdomainswithinwindows, restrictedsiteszoneenablemimesniffing.
If you don't configure this policy setting, the actions that may be harmful can't run; this Internet Explorer security feature will be turned on in this zone, as dictated by the feature control setting for the process.
RestrictedSitesZoneIncludeLocalPathWhenUploadingFilesToServer
Restrictedsiteszoneinitializeandscriptactivexcontrols, restrictedsiteszonejavapermissions, restrictedsiteszonelaunchingapplicationsandfilesiniframe.
If you don't configure this policy setting, users are prevented from running applications and downloading files from IFRAMEs on the pages in this zone.
RestrictedSitesZoneLogonOptions
If you don't configure this policy setting, logon is set to Prompt for username and password.
RestrictedSitesZoneNavigateWindowsAndFrames
Restrictedsiteszonerunactivexcontrolsandplugins.
This policy setting allows you to manage whether ActiveX controls and plug-ins can be run on pages from the specified zone.
- If you enable this policy setting, controls and plug-ins can run without user intervention.
If you selected Prompt in the drop-down box, users are asked to choose whether to allow the controls or plug-in to run.
If you disable this policy setting, controls and plug-ins are prevented from running.
If you don't configure this policy setting, controls and plug-ins are prevented from running.
RestrictedSitesZoneRunNETFrameworkReliantComponentsSignedWithAuthenticode
If you don't configure this policy setting, Internet Explorer won't execute signed managed components.
RestrictedSitesZoneScriptActiveXControlsMarkedSafeForScripting
This policy setting allows you to manage whether an ActiveX control marked safe for scripting can interact with a script.
- If you enable this policy setting, script interaction can occur automatically without user intervention.
If you select Prompt in the drop-down box, users are queried to choose whether to allow script interaction.
If you disable this policy setting, script interaction is prevented from occurring.
If you don't configure this policy setting, script interaction is prevented from occurring.
RestrictedSitesZoneScriptingOfJavaApplets
This policy setting allows you to manage whether applets are exposed to scripts within the zone.
- If you enable this policy setting, scripts can access applets automatically without user intervention.
If you select Prompt in the drop-down box, users are queried to choose whether to allow scripts to access applets.
If you disable this policy setting, scripts are prevented from accessing applets.
If you don't configure this policy setting, scripts are prevented from accessing applets.
RestrictedSitesZoneShowSecurityWarningForPotentiallyUnsafeFiles
Restrictedsiteszoneturnonprotectedmode, restrictedsiteszoneusepopupblocker, restrictfiledownloadinternetexplorerprocesses.
This policy setting enables blocking of file download prompts that aren't user initiated.
If you enable this policy setting, file download prompts that aren't user initiated will be blocked for Internet Explorer processes.
If you disable this policy setting, prompting will occur for file downloads that aren't user initiated for Internet Explorer processes.
If you don't configure this policy setting, the user's preference determines whether to prompt for file downloads that aren't user initiated for Internet Explorer processes.
ScriptedWindowSecurityRestrictionsInternetExplorerProcesses
Internet Explorer allows scripts to programmatically open, resize, and reposition windows of various types. The Window Restrictions security feature restricts popup windows and prohibits scripts from displaying windows in which the title and status bars aren't visible to the user or obfuscate other Windows' title and status bars.
If you enable this policy setting, popup windows and other restrictions apply for File Explorer and Internet Explorer processes.
If you disable this policy setting, scripts can continue to create popup windows and windows that obfuscate other windows.
If you don't configure this policy setting, popup windows and other restrictions apply for File Explorer and Internet Explorer processes.
SearchProviderList
This policy setting allows you to restrict the search providers that appear in the Search box in Internet Explorer to those defined in the list of policy keys for search providers (found under [HKCU or HKLM\Software\policies\Microsoft\Internet Explorer\SearchScopes]). Normally, search providers can be added from third-party toolbars or in Setup, but the user can also add them from a search provider's website.
- If you enable this policy setting, the user can't configure the list of search providers on his or her computer, and any default providers installed don't appear (including providers installed from other applications). The only providers that appear are those in the list of policy keys for search providers.
This list can be created through a custom administrative template file. For information about creating this custom administrative template file, see the Internet Explorer documentation on search providers.
- If you disable or don't configure this policy setting, the user can configure his or her list of search providers.
SecurityZonesUseOnlyMachineSettings
Applies security zone information to all users of the same computer. A security zone is a group of Web sites with the same security level.
If you enable this policy, changes that the user makes to a security zone will apply to all users of that computer.
If you disable this policy or don't configure it, users of the same computer can establish their own security zone settings.
This policy is intended to ensure that security zone settings apply uniformly to the same computer and don't vary from user to user.
Also, see the "Security zones: Don't allow users to change policies" policy.
SendSitesNotInEnterpriseSiteListToEdge
This setting lets you decide whether to open all sites not included in the Enterprise Mode Site List in Microsoft Edge. If you use this setting, you must also turn on the Administrative Templates\Windows Components\Internet Explorer\Use the Enterprise Mode IE website list policy setting and you must include at least one site in the Enterprise Mode Site List.
Enabling this setting automatically opens all sites not included in the Enterprise Mode Site List in Microsoft Edge.
Disabling, or not configuring this setting, opens all sites based on the currently active browser.
If you've also enabled the Administrative Templates\Windows Components\Microsoft Edge\Send all intranet sites to Internet Explorer 11 policy setting, then all intranet sites will continue to open in Internet Explorer 11.
This MDM policy is still outstanding.
SpecifyUseOfActiveXInstallerService
This policy setting allows you to specify how ActiveX controls are installed.
If you enable this policy setting, ActiveX controls are installed only if the ActiveX Installer Service is present and has been configured to allow the installation of ActiveX controls.
If you disable or don't configure this policy setting, ActiveX controls, including per-user controls, are installed through the standard installation process.
TrustedSitesZoneAllowAccessToDataSources
Trustedsiteszoneallowautomaticpromptingforactivexcontrols, trustedsiteszoneallowautomaticpromptingforfiledownloads, trustedsiteszoneallowfontdownloads, trustedsiteszoneallowlessprivilegedsites.
If you don't configure this policy setting, a warning is issued to the user that potentially risky navigation is about to occur.
TrustedSitesZoneAllowNETFrameworkReliantComponents
Trustedsiteszoneallowscriptlets, trustedsiteszoneallowsmartscreenie, trustedsiteszoneallowuserdatapersistence, trustedsiteszonedonotrunantimalwareagainstactivexcontrols, trustedsiteszoneinitializeandscriptactivexcontrols, trustedsiteszonejavapermissions.
If you don't configure this policy setting, the permission is set to Low Safety.
TrustedSitesZoneLogonOptions
Trustedsiteszonenavigatewindowsandframes, related articles.
Policy configuration service provider
Was this page helpful?
Coming soon: Throughout 2024 we will be phasing out GitHub Issues as the feedback mechanism for content and replacing it with a new feedback system. For more information see: https://aka.ms/ContentUserFeedback .
Submit and view feedback for
Additional resources

IMAGES
VIDEO
COMMENTS
In the right-hand pane, double-click "Site to Zone Assignment List". Enable the policy and click the "Show…" button next to "Enter the zone assignments here." This will pop up the "Show Contents" window. Click the "Add…" button. This will pop up the "Add Item" window.
Step 2. Navigate to User Configuration > Administrative Templates > Windows Components > Internet Explorer > Internet Control Panel > Security Page and double click on the “Site to Zone Assignment List†and check the “Enable†option then click on the “Show..†button. Step 3.
Intranet zone; Trusted Sites zone; Internet zone; Restricted Sites zone; We will be adding a URL to the Restricted Sites Zone. So enter the value name as the site URL that to Restricted Sites zone and enter the value as 4. Click OK and close the Group Policy Management Editor. We will be applying the group policy to a group that consists of users.
When possible, use the computer configuration option as it will not impact user logons. When you enable the setting, you will be prompted for a value name (the website) and a value (the zone list). Here are the possible values and the zone that they correspond to: 1 = Intranet/Local Zone. 2 = Trusted Sites. 3 = Internet/Public Zone.
Tour Start here for a quick overview of the site ... double-click on the Site to Zone Assignment List option, then click Show... trusted sites are the ones with 2 in the Value column ... As each enter separates the value name and the value data with a comma, it could be further enhanced to output to a file with the csv extension and then opened ...
Go to "User Configuration", then "Policies", then "Administrative Templates", "Windows Components", "Internet Explorer", "Internal Control Panel", and finally "Security Page". Select site to "Zone Assignment List" and enable the policy. Enter the following values: Value name: https://autologon.microsoftazuread ...
The "Site To Zone Assignment List" policy. The format of the Site To Zone Assignment List policy is described within the policy. This policy setting allows you to manage a list of sites that you want to associate with a particular security zone. These zone numbers have associated security settings that apply to all sites in the zone.
note the text now included before the starting bracket, that text is also included Settings detail on the Review and deploy page before attempting the migration which then fails. I was thinking that if that initial text (Site to Zone Assignment List/Enter the zone assignments here. -) were removed it may then work on the migration.
Especially a long list of URLs in the "site to zone assignment" setting. However it seems that one URL still falls into the "internet zone" even when assigned to the "trusted zone". In earlier versions of internet explorer one could easily determine from the status bar into which zone an URL falls.
Select Site to Zone Assignment List. Enable the policy, and then enter the following values in the dialog: Value name: The Microsoft Entra URL where the Kerberos tickets are forwarded. Value (Data): 1 indicates the intranet zone. The result looks like this example: Value name: https://autologon.microsoftazuread-sso.com. Value (Data): 1
Select the Site to Zone Assignment List. Select Enabled and click Show to edit the list. Refer to Figure 1 below. The zone values are as follows: 1 — intranet, 2 — trusted sites, 3 — internet zone, 4 — restricted sites. Click OK. Click Apply and OK. Figure 1. Assigning sites to the Trusted Sites zone. Figure 2.
Users can use the Internet Control Panel to assign specific sites to Zones and to configure the permission results for each zone. In managed environments, administrators can use Group Policy to assign specific sites to Zones (via "Site to Zone Assignment List" policy) and specify the settings for URLActions on a per-zone basis.
This is the second part for adding Microsoft Cloud URLs to Internet Explorer's zone. In this part we look at the Trusted Sites zone. ... double-click the Sites to Zone Assignment List ... The Show Contents window appears. Add the above URLs to the Trusted Sites zone by entering the URL in the Value name column and the number 2 in the Value ...
To specify that a URL is part of a specific zone, enable the Site To Zone Assignment List setting in the Security Page node. After you have enabled a URL, you can assign it (using the Value Name field, with an optional protocol) to a specific zone (using the Value field) using the zone's number: 1: Local Intranet zone. 2: Trusted Sites zone.
Site to Zone Assignment List. This policy setting allows you to manage a list of sites that you want to associate with a particular security zone. These zone numbers have associated security settings that apply to all of the sites in the zone.Internet Explorer has 4 security zones numbered 1-4 and these are used by this policy setting to ...
To add a site to the Trusted Sites zone, do the following: In the pop-up window, each row represents a domain (Value name) and zone (Value) pair. Enter the site name in the "Value Name" field and 2 (for Trusted Sites zone) in "Value" field. ← Allow Internet Explorer Pop-up Exceptions with Group Policy → Citrix "Cannot start app.
Open Group Policy Management Console. Navigate to the desired GPO or create a new one. Expand User Configuration or Computer Configuration and go to Preferences -> Windows Settings -> Registry. Right-click and select New -> Registry Item. Configure the Registry Item to delete the specified entries under the ZoneMap registry key.
For the "Value", you must enter a number from 1-4 that designates what zone to put the domain in. They are: 1 = Intranet Zone. 2 = Trusted Sites Zone. 3 = Internet Zone. 4 = Restricted Sites Zone. After you are finished, assign the GPO to the OU's you want to apply it to. Let's say you want to be flexible.
Select the Site to Zone Assignment List. Select Enabled and click Show to edit the list. The zone values are as follows: 1 — intranet, 2 — trusted sites, 3 — internet zone, 4 — restricted sites. Click OK. Click Apply and OK.
Deploy a set of trusted sites overriding users' ability to add trusted sites themselves. To acheive this, an Intune configuration profile Trusted site zone assignment can be deployed to devices/users group as required. Login to Intune Portal and navigate to: Devices > Windows > Configuration Profiles. Hit the Create button and Select New ...
For technical information contact: Ingrid Feustel, Existing Chemicals Risk Management Division (7405M), Office of Pollution Prevention and Toxics, Environmental Protection Agency, 1200 Pennsylvania Ave. NW, Washington, DC 20460-0001; telephone number: (202) 564-3199; email address: [email protected].
(The Local Machine zone and its locked down equivalent have special security settings that protect your local computer). If you enable this policy setting, you can enter a list of sites and their related zone numbers. The association of a site with a zone will ensure that the security settings for the specified zone are applied to the site.