Stack Exchange Network
Stack Exchange network consists of 183 Q&A communities including Stack Overflow , the largest, most trusted online community for developers to learn, share their knowledge, and build their careers.
Q&A for work
Connect and share knowledge within a single location that is structured and easy to search.

Move Gitlab to new ip-adress, lfs stop working. How to fix?
We have GitLab 11.2.1-ee installation in our local network It had ip-address 192.168.1.100 before We use Git LFS in our projects And all work fine before we changed ip address of Gitlab machine. We changed the ip-adress of Gitlab machine to 192.168.160.160 and LFS stop working Now it shows error
We changed address of gitlab on clients to new one. Also we changed external_url in gitlab.rb Our git projects that do not use lfs works fine. Only projects with LFS shows this error
How to fix this?
I fix it. I miss that I must run
after editing external_url in /etc/gitlab/gitlab.rb We run this commands and all is fine now
You must log in to answer this question.
Not the answer you're looking for browse other questions tagged git gitlab ..
- The Overflow Blog
- Reshaping the future of API platforms
- Between hyper-focus and burnout: Developing with ADHD
- Featured on Meta
- Our Partnership with OpenAI
- Imgur image URL migration: Coming soon to a Stack Exchange site near you!
Hot Network Questions
- Fast and precise summation of random numbers
- Can I safely customize fingering of arpeggios?
- What is the equation relating the sides and the orthocenter segments of a triangle?
- Why is the reliability of Stormy Daniels testimony relevant in Trump's hush money process?
- Is it bad to branch off data traces into two separate connectors?
- How does Russia exactly define Russian territory in its state policy?
- In OOP, what count as a "getter"
- Ceiling box has two reds and two blacks - how to wire this?
- Why do Koreans have trouble telling apart /p/ and /f/, when their Discrete Fourier Transforms look nothing alike?
- Why doesn't constant acceleration give me total displacement?
- Why does the EU find the foreign agent law in Georgia against their values?
- Computer not booting after installing Ubuntu next to Windows
- Can an employee be made to pay back training costs when resigning from the company?
- Does making a ground plane and a power plane on a PCB make the board behave like a large capacitor?
- "Ka no taikoku shin" = China? [Rurouni Kenshin Live Action]
- Is it possible to stop/clear/refresh the source tracking for a single file?
- Has there ever been a transfer of occupants from one aircraft to another while airborne?
- How can I work with a senior researcher who is less knowledgeable than myself?
- Electrolysis experiment with CuSO4
- Dismissive and uncommunicative coworker when there are clear signs of tension
- Can I use "Britons" in data reports?
- A word for not just optional but usually not done
- How (or is there) a way to make my rice more fluffy than sticky? Given my current approach
- The Wu line drawing algorithm for anti-aliased lines optimization
CISA says GitLab account takeover bug is actively exploited in attacks
Sergiu gatlan.
- May 1, 2024

CISA warned today that attackers are actively exploiting a maximum-severity GitLab vulnerability that allows them to take over accounts via password resets.
GitLab hosts sensitive data, including proprietary code and API keys, and account hijacking can have a significant impact. Successful exploitation can also lead to supply chain attacks that can compromise repositories by inserting malicious code in CI/CD (Continuous Integration/Continuous Deployment) environments.
Tracked as CVE-2023-7028 , the security flaw is due to an improper access control weakness that can allow remote unauthenticated threat actors to send password reset emails to email accounts under their control to change the password and hijack targeted accounts without user interaction.
Although attackers can't exploit this vulnerability to hijack accounts where two-factor authentication (2FA) is enabled, it's critical to patch systems where accounts are not protected with this additional security measure.
The CVE-2023-7028 bug impacts GitLab Community and Enterprise editions, and GitLab fixed it in 16.7.2, 16.5.6, and 16.6.4 and backported patches to versions 16.1.6, 16.2.9, and 16.3.7.
While threat monitoring service Shadowserver found 5,379 vulnerable GitLab instances exposed online in January (the week security patches were released), less than half (2,394) are still reachable at the moment.
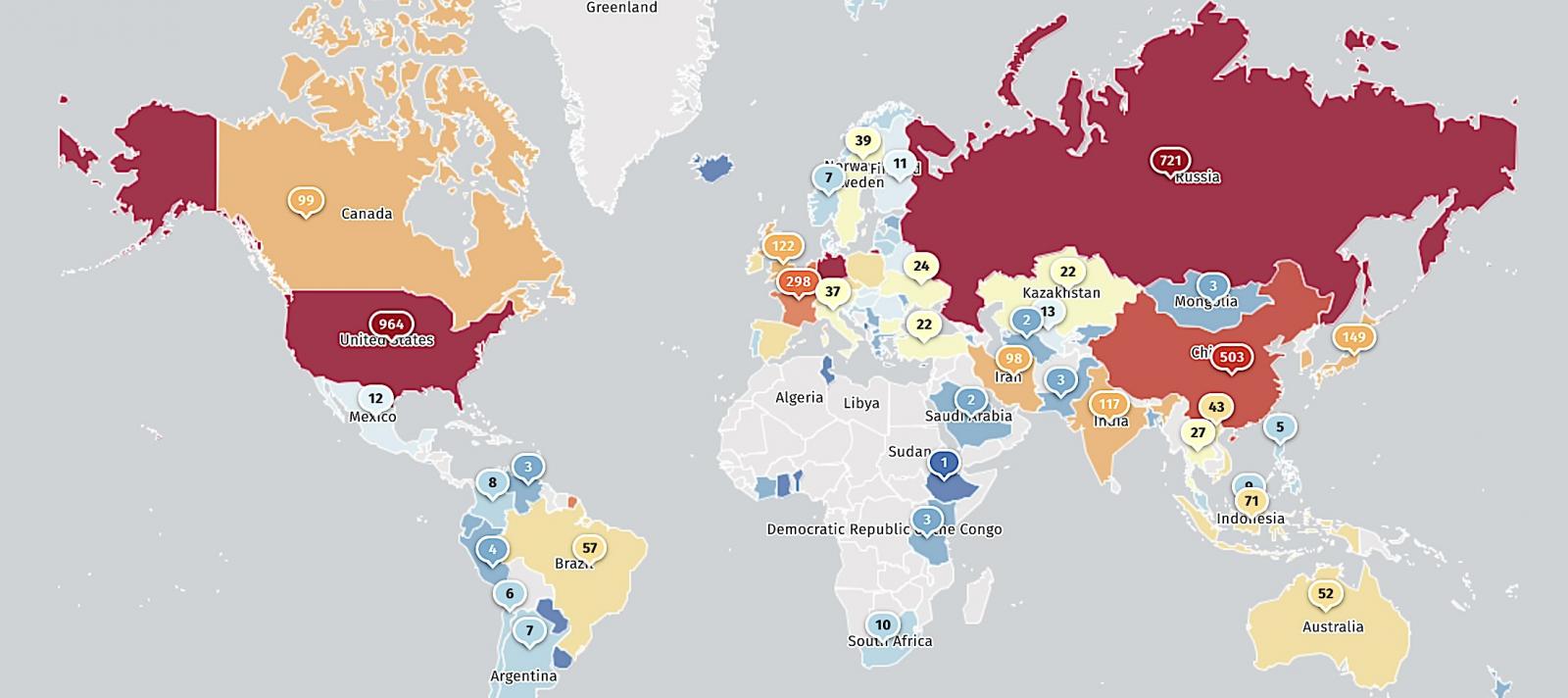
CISA added CVE-2023-7028 to its Known Exploited Vulnerabilities Catalog on Wednesday, confirming it's now actively exploited in attacks and ordering U.S. federal agencies to secure their systems within three weeks by May 22.
The U.S. cybersecurity agency hasn't shared any information regarding ongoing attacks exploiting this maximum severity GitLab security bug, but it did confirm it has no evidence that it's being used in ransomware attacks.
"These types of vulnerabilities are frequent attack vectors for malicious cyber actors and pose significant risks to the federal enterprise," CISA said today.
Although the agency's KEV catalog primarily targets federal agencies, private organizations using the GitLab DevOps platform should also prioritize patching this vulnerability to prevent attacks.
Those who haven't already patched may have been compromised already, so they should follow GitLab's incident response guide and check for signs of compromise as soon as possible.
Related Articles:
CISA tags Microsoft SharePoint RCE bug as actively exploited
Over 15,000 hacked Roku accounts sold for 50¢ each to buy hardware
Google fixes fifth Chrome zero-day exploited in attacks this year
CISA urges software devs to weed out path traversal vulnerabilities
Okta warns of "unprecedented" credential stuffing attacks on customers
- Account Takeover
- Actively Exploited
- Password Reset
- Previous Article
- Next Article
Post a Comment Community Rules
You need to login in order to post a comment.
Not a member yet? Register Now
You may also like:

Dell warns of data breach, 49 million customers allegedly affected

Zscaler takes "test environment" offline after rumors of a breach
Help us understand the problem. What is going on with this comment?
- Abusive or Harmful
- Inappropriate content
- Strong language
Read our posting guidelinese to learn what content is prohibited.
- Mobile Site
- Staff Directory
- Advertise with Ars
Filter by topic
- Biz & IT
- Gaming & Culture
Front page layout
A 10 OUT OF 10 —
Maximum-severity gitlab flaw allowing account hijacking under active exploitation, the threat is potentially grave because it could be used in supply-chain attacks..
Dan Goodin - May 2, 2024 7:02 pm UTC

A maximum severity vulnerability that allows hackers to hijack GitLab accounts with no user interaction required is now under active exploitation, federal government officials warned as data showed that thousands of users had yet to install a patch released in January.
A change GitLab implemented in May 2023 made it possible for users to initiate password changes through links sent to secondary email addresses. The move was designed to permit resets when users didn’t have access to the email address used to establish the account. In January, GitLab disclosed that the feature allowed attackers to send reset emails to accounts they controlled and from there click on the embedded link and take over the account.
While exploits require no user interaction, hijackings work only against accounts that aren’t configured to use multifactor authentication. Even with MFA, accounts remained vulnerable to password resets, but the attackers ultimately are unable to access the account, allowing the rightful owner to change the reset password. The vulnerability, tracked as CVE-2023-7028, carries a severity rating of 10 out of 10.
On Wednesday, the US Cybersecurity and Infrastructure Security Agency said it is aware of “evidence of active exploitation” and added the vulnerability to its list of known exploited vulnerabilities. CISA provided no details about the in-the-wild attacks. A GitLab representative declined to provide specifics about the active exploitation of the vulnerability.
Further Reading
These sorts of attacks are powerful. By hacking a single, carefully selected target, attackers gain the means to infect thousands of downstream users, often without requiring them to take any action at all.
According to Internet scans performed by security organization Shadowserver, more than 2,100 IP addresses showed they were hosting one or more vulnerable GitLab instances.
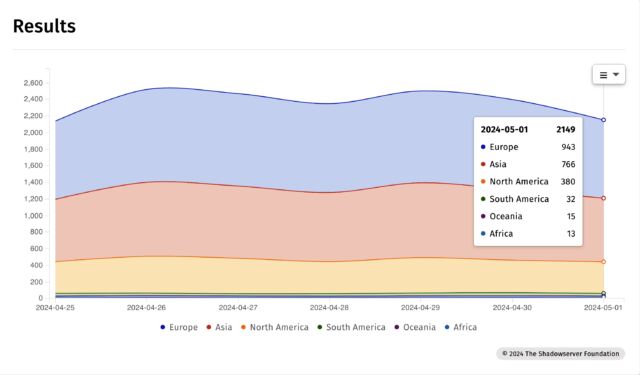
The biggest concentration of IP addresses was in India, followed by the US, Indonesia, Algeria, and Thailand.
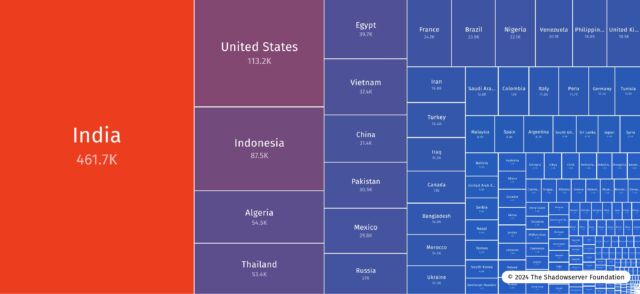
The number of IP addresses showing vulnerable instances has fallen over time. Shadowserver shows that there were more than 5,300 addresses on January 22, one week after GitLab issued the patch.
The vulnerability is classed as an improper access control flaw.
CISA has ordered all civilian federal agencies that have yet to patch the vulnerability to do so immediately. The agency made no mention of MFA, but any GitLab users who haven’t already done so should enable it, ideally with a form that complies with the FIDO industry standard.
GitLab users should also remember that patching does nothing to secure systems that have already been breached through exploits. GitLab has published incident response guidance here .
reader comments
Promoted comments.
Channel Ars Technica
You are viewing this page in an unauthorized frame window.
This is a potential security issue, you are being redirected to https://nvd.nist.gov
You have JavaScript disabled. This site requires JavaScript to be enabled for complete site functionality.
Official websites use .gov A .gov website belongs to an official government organization in the United States.
Information Technology Laboratory
National vulnerability database.
- Vulnerabilities
NIST has updated the NVD program announcement page with additional information regarding recent concerns and the temporary delays in enrichment efforts.
Weakness Enumeration
Change history, new cve received by nist 5/07/2024 9:15:48 am.
Configuring runners
Set the maximum job timeout, for an instance runner, for a group runner, for a project runner, how maximum job timeout works, set script and after_script timeouts, protecting sensitive information, configuring long polling, using instance runners in forked projects, reset the runner registration token for a project (deprecated), authentication token security, reset the runner authentication token, automatically rotate runner authentication tokens, prevent runners from revealing sensitive information, control jobs that a runner can run, how the runner uses tags, runner runs only tagged jobs, runner is allowed to run untagged jobs, a runner and a job have multiple tags, use tags to run jobs on different platforms, use ci/cd variables in tags, configure runner behavior with variables, git strategy, git submodule strategy, git checkout, git clean flags, git fetch extra flags, sync or exclude specific submodules from ci jobs, git submodule update flags, rewrite submodule urls to https, shallow cloning, git submodule depth, custom build directories, handling concurrency, nested paths, job stages attempts, system calls not available on gitlab.com instance runners, artifact and cache settings, artifact provenance metadata, provenance metadata format, staging directory, configure fastzip to improve performance, help & feedback, feature availability and product trials.
For problems setting up or using this feature (depending on your GitLab subscription).
Special Features
Vendor voice.

Cyber-crime
Federal frenzy to patch gaping GitLab account takeover hole
Warning comes exactly a year after the vulnerability was introduced.
The US Cybersecurity and Infrastructure Security Agency (CISA) is forcing all federal agencies to patch a critical vulnerability in GitLab's Community and Enterprise editions, confirming it is very much under "active exploit."
When CISA adds a vulnerability to its Known Exploited Vulnerabilities (KEV) list, it means all federal civilian executive branch (FCEB) agencies usually have a maximum of 21 days to fix the issue to prevent harmful attacks on the government.
The name is somewhat of a giveaway, but security flaws added to the KEV list also mean they're known to be under active exploitation, necessitating a quick fix.
The vulnerability, tracked as CVE-2023-7028, was disclosed by GitLab in January and was assigned a maximum 10 severity rating by the platform itself, which is a certified CVE Numbering Authority (CNA). The National Vulnerability Database (NVD) gave it a mere 7.5 score, however.
At the time of disclosure, GitLab reported that the vulnerability had existed since May 2023, though there was no evidence of successful exploitation. The addition to CISA's KEV means this is now no longer the case, so get those patches installed pronto if they weren't sorted in January.
The vulnerability is classed as an improper access control flaw, offering attackers a zero-click route to a full account takeover.
Starting in version 16.1.0, released May 1, 2023, a change was introduced that allowed users to reset their GitLab account passwords using a different email address, and a bug in the verification process opened up the vulnerability.
A specially crafted HTTP request sends a password reset link to an unverified, attacker-controlled email address, enabling unauthorized account takeovers.
Given the nature of GitLab's business, the obvious danger here is the vulnerability being abused by attackers to carry out software supply chain attacks – surreptitiously modifying source code to breach countless organizations.
Russia with SolarWinds and North Korea with 3CX are two examples of adversarial nations with an appetite for supply chain attacks in recent years. Ransomware crews such as REvil with Kaseya and Cl0p with MOVEit are also no strangers to compromising software at the source, although CISA said it isn't aware of any ransomware-associated activity with the GitLab flaw yet.
- Open source programming language R patches gnarly arbitrary code exec flaw
- Governments issue alerts after 'sophisticated' state-backed actor found exploiting flaws in Cisco security boxes
- Old Windows print spooler bug is latest target of Russia's Fancy Bear gang
- Exploit code for Palo Alto Networks zero-day now public
The upshot of all this is that admins who enabled some form of two-factor authentication (2FA) in GitLab are safe and unaffected by the vulnerability. And of course you enabled 2FA , didn't you?
The following versions are vulnerable:
16.1 to 16.1.5
16.2 to 16.2.8
16.3 to 16.3.6
16.4 to 16.4.4
16.5 to 16.5.5
16.6 to 16.6.3
16.7 to 16.7.1

Shadowserver data showing number of vulnerable GitLab instances since the vulnerability's disclosure – click to enlarge
Shadowserver's data shows that the number of publicly exposed GitLab instances has more than halved since the vulnerability's disclosure. There are currently 2,149 vulnerable GitLab environments, down from 4,652 in January, with the largest concentration in Europe and Asia.
GitLab fixed the vulnerability in versions 16.5.6, 16.6.4, and 16.7.2, and also backported the patches for versions 16.1.6, 16.2.9, 16.3.7, and 16.4.5. ®
- Cybersecurity
- Cybersecurity and Infrastructure Security Agency
- Vulnerability
Narrower topics
- RSA Conference
- Zero Day Initiative
Broader topics
- Federal government of the United States
Send us news
Other stories you might like
The truth about kev: cisa’s vuln deadlines good influence on private-sector patching, cisa says 'no more' to decades-old directory traversal bugs, chinese government website security is often worryingly bad, say chinese researchers, boosting throughput for cloud databases.
Patch up – 4 critical bugs in ArubaOS lead to remote code execution
Cisa boss: secure code is the 'only way to make ransomware a shocking anomaly', second time lucky for thoma bravo, which scoops up darktrace for $5.3b, it may take decade to shore up software supply chain security, says infosec ceo, 68 tech names sign cisa's secure-by-design pledge, three years on from biden infosec eo, and we're still trying to check all the boxes, germany points finger at fancy bear for widespread 2023 hacks, ddos attacks, discord dismantles spy.pet site that snooped on millions of users.
- Advertise with us
Our Websites
- The Next Platform
- Blocks and Files
Your Privacy
- Cookies Policy
- Privacy Policy
- Ts & Cs

Copyright. All rights reserved © 1998–2024
Change the hostname of your AL2 instance
When you launch an instance into a private VPC, Amazon EC2 assigns a guest OS hostname. The type of hostname that Amazon EC2 assigns depends on your subnet settings. For more information about EC2 hostnames, see Amazon EC2 instance hostname types in the Amazon EC2 User Guide for Linux Instances .
A typical Amazon EC2 private DNS name for an EC2 instance configured to use IP-based naming with an IPv4 address looks something like this: ip-12-34-56-78.us-west-2.compute.internal , where the name consists of the internal domain, the service (in this case, compute ), the region, and a form of the private IPv4 address. Part of this hostname is displayed at the shell prompt when you log into your instance (for example, ip-12-34-56-78 ). Each time you stop and restart your Amazon EC2 instance (unless you are using an Elastic IP address), the public IPv4 address changes, and so does your public DNS name, system hostname, and shell prompt.
This information applies to Amazon Linux. For information about other distributions, see their specific documentation.
Change the system hostname
If you have a public DNS name registered for the IP address of your instance (such as webserver.mydomain.com ), you can set the system hostname so your instance identifies itself as a part of that domain. This also changes the shell prompt so that it displays the first portion of this name instead of the hostname supplied by AWS (for example, ip-12-34-56-78 ). If you do not have a public DNS name registered, you can still change the hostname, but the process is a little different.
In order for your hostname update to persist, you must verify that the preserve_hostname cloud-init setting is set to true . You can run the following command to edit or add this setting:
If the preserve_hostname setting is not listed, add the following line of text to the end of the file:
To change the system hostname to a public DNS name
Follow this procedure if you already have a public DNS name registered.
For AL2: Use the hostnamectl command to set your hostname to reflect the fully qualified domain name (such as webserver.mydomain.com ).
For Amazon Linux AMI: On your instance, open the /etc/sysconfig/network configuration file in your favorite text editor and change the HOSTNAME entry to reflect the fully qualified domain name (such as webserver.mydomain.com ).
Reboot the instance to pick up the new hostname.
Alternatively, you can reboot using the Amazon EC2 console (on the Instances page, select the instance and choose Instance state , Reboot instance ).
Log into your instance and verify that the hostname has been updated. Your prompt should show the new hostname (up to the first ".") and the hostname command should show the fully-qualified domain name.
To change the system hostname without a public DNS name
For AL2: Use the hostnamectl command to set your hostname to reflect the desired system hostname (such as webserver ).
For Amazon Linux AMI: On your instance, open the /etc/sysconfig/network configuration file in your favorite text editor and change the HOSTNAME entry to reflect the desired system hostname (such as webserver ).
Open the /etc/hosts file in your favorite text editor and change the entry beginning with 127.0.0.1 to match the example below, substituting your own hostname.
You can also implement more programmatic solutions, such as specifying user data to configure your instance. If your instance is part of an Auto Scaling group, you can use lifecycle hooks to define user data. For more information, see Run commands on your Linux instance at launch and Lifecycle hook for instance launch in the AWS CloudFormation User Guide .
Change the shell prompt without affecting the hostname
If you do not want to modify the hostname for your instance, but you would like to have a more useful system name (such as webserver ) displayed than the private name supplied by AWS (for example, ip-12-34-56-78 ), you can edit the shell prompt configuration files to display your system nickname instead of the hostname.
To change the shell prompt to a host nickname
Create a file in /etc/profile.d that sets the environment variable called NICKNAME to the value you want in the shell prompt. For example, to set the system nickname to webserver , run the following command.
Open the /etc/bashrc (Red Hat) or /etc/bash.bashrc (Debian/Ubuntu) file in your favorite text editor (such as vim or nano ). You need to use sudo with the editor command because /etc/bashrc and /etc/bash.bashrc are owned by root .
Edit the file and change the shell prompt variable ( PS1 ) to display your nickname instead of the hostname. Find the following line that sets the shell prompt in /etc/bashrc or /etc/bash.bashrc (several surrounding lines are shown below for context; look for the line that starts with [ "$PS1" ):
Change the \h (the symbol for hostname ) in that line to the value of the NICKNAME variable.
(Optional) To set the title on shell windows to the new nickname, complete the following steps.
Create a file named /etc/sysconfig/bash-prompt-xterm .
Make the file executable using the following command.
Open the /etc/sysconfig/bash-prompt-xterm file in your favorite text editor (such as vim or nano ). You need to use sudo with the editor command because /etc/sysconfig/bash-prompt-xterm is owned by root .
Add the following line to the file.
Log out and then log back in to pick up the new nickname value.
Change the hostname on other Linux distributions
The procedures on this page are intended for use with Amazon Linux only. For more information about other Linux distributions, see their specific documentation and the following articles:
How do I assign a static hostname to a private Amazon EC2 instance running RHEL 7 or Centos 7?

To use the Amazon Web Services Documentation, Javascript must be enabled. Please refer to your browser's Help pages for instructions.
Thanks for letting us know we're doing a good job!
If you've got a moment, please tell us what we did right so we can do more of it.
Thanks for letting us know this page needs work. We're sorry we let you down.
If you've got a moment, please tell us how we can make the documentation better.
Modify the GitLab host name
Change the default address automatically.
It is advisable to use a host name instead of an IP address for Gitlab. However, we recommend not using git. in the host name as this causes problems when accessing Gitlab over HTTP.
Follow these steps:
At the server console, run the following command:
NOTE: If the result of the previous command shows a command not found error, execute the following command instead: $ sudo /opt/bitnami/apps/gitlab/bnconfig --machine_hostname IP_OR_DOMAIN IMPORTANT: If you’ve configured GitLab to use a static domain name, remove or rename the /opt/bitnami/apps/gitlab/bnconfig file to avoid it being reset on the next system reboot.
Change the default address manually for GitLab
To configure an external URL for GitLab, modify the external_url parameter in the /etc/gitlab/gitlab.rb file:
Run the gitlab-ctl script to apply the changes as follows:
Changes domain to local IP address in URL
Hello, please tell me how to fix the following problem. When entering through the browser by https://mysite.com it’s redirect to the page with url https://192.168.1.78/users/sign_in . 192.168.1.78 is the local IP address where GitLab Docker Image up. “Keenetic” router through the service “KeenDNS” redirects https traffic to local server with local IP 192.168.1.78. If in Browser manually change IP to domain then no redirects and all work fine. Thanks
The only two things I can think of it.
- external_url in gitlab, what was it configured with? IP or hostname/domain name for use with Gitlab?
- you mention keenetic router? Is this working as a proxy and if so, what is its redirect configuration?
- external_url like https://gitlab.mysite.keenetic.link/
- I can’t find information how it work, because it’s use service KeenDNS and no settings except routing domain name to local ip address and port. Example( https://help.keenetic.com/hc/en-us/articles/360000563719 )
while trying different configurations I’ve got managed solve this problem, but for that I setup routing all traffic by ports 443 to local ip, where GitLab Docker working
I’m having exactly the same issue with exactly the same Keenetic KeenDNS thing could you please elaborate on how you managed to solve this issue?

IMAGES
VIDEO
COMMENTS
I resolved the matter for myself. I modified variable external_url in the /etc/gitlab/gitlab.rb file, setting the new machine's IP address into this field: external_url = '10.57.3.38'. Then on the command prompt, I executed the following two commands in successive order: gitlab-ctl reconfigure. gitlab-ctl restart.
thanks. iwalker January 6, 2021, 9:05am 2. If your external_url in gitlab.rb has ip change this. If it is a fully qualified domain name then change the dns to use new ip and make sure the server also is using the new ip. Restart gitlab and that is all. kvstudio6 January 7, 2021, 12:07am 3.
1. I installed gitlab in my ubuntu server operated in Hyper-V. Surely, host is Windows Server that routing Hyper-V guests. My Ubuntu server and Hyper-V NIC have private IP addresses, "10.0.0.101" and "10.0.0.1". For routing to Hyper-V guest, I set IIS ARR and URL rewrite and it is operating well.
Update the IP address or hostname GitLab CE requires updating the IP address/domain name if the machine IP address/domain name changes. To configure it to run on a specific IP address or domain name, run the command below. Remember to replace the NEW_DOMAIN placeholder with an appropriate value: IMPORTANT: Be sure that your domain is propagated.
Go to the current instance configuration to see the SSH host key fingerprints on GitLab.com. Sign in to GitLab. On the left sidebar, select Help () > Help . On the Help page, select Check the current instance configuration . In the instance configuration, you see the SSH host key fingerprints : Algorithm. MD5 (deprecated) SHA256.
Modify the GitLab host name Change the default address automatically. It is advisable to use a host name instead of an IP address for Gitlab. However, we recommend not using git. in the host name as this causes problems when accessing Gitlab over HTTP. Follow these steps: At the server console, run the following command:
Hello, I would like to change the IP of my gitlab-runner server but I would like to keep the existing configuration (same projet, same tags, same tokens). I tried to change the IP in the Runners configuration page. I can see the IP but I am not able to change it. Do y ou know if I can change the IP somewhere or I need to break the config of the gitlab-runner with the old IP to create a new one ...
We have GitLab 11.2.1-ee installation in our local network It had ip-address 192.168.1.100 before We use Git LFS in our projects And all work fine before we changed ip address of Gitlab machine. We changed the ip-adress of Gitlab machine to 192.168.160.160 and LFS stop working Now it shows error
Update the IP address or hostname GitLab Enterprise (CORE) requires updating the IP address/domain name if the machine IP address/domain name changes. ... You can also change your hostname by modifying it in your hosts file. Enter the new hostname using your preferred editor. $ sudo nano /etc/hosts Add a new line with the IP address and the new ...
On the left sidebar, at the bottom, select Admin Area . Select Settings > Network . Expand User and IP rate limits . Select Enable authenticated API request rate limit . Optional. Update the Maximum authenticated API requests per rate limit period per user value. Defaults to 7200 . Optional. Update the Authenticated API rate limit period in ...
The script will set up your server to use the GitLab maintained repositories. This lets you manage GitLab with the same package management tools you use for your other system packages. Once this is complete, you can install the actual GitLab application with apt: sudo apt install GitLab-CE; Step 3: Firewall Configuration
I tried several places already. When I set the external_url in the gitlab.rb, the container wouldn't start up again. I searched the directory for the ddns string and found two other entries, gitlab-rails\etc\gitlab.yml and nginx\conf\gitlab-http.conf, but when I replaced the address with the IP address, nothing changed.
May 1, 2024. 12:29 PM. 0. CISA warned today that attackers are actively exploiting a maximum-severity GitLab vulnerability that allows them to take over accounts via password resets. GitLab hosts ...
A change GitLab implemented in May 2023 made it possible for users to initiate password changes through links sent to secondary email addresses. ... more than 2,100 IP addresses showed they were ...
References to Advisories, Solutions, and Tools. By selecting these links, you will be leaving NIST webspace. We have provided these links to other web sites because they may have information that would be of interest to you.
To set the maximum job timeout: On the left sidebar, at the bottom, select Admin Area . Select CI/CD > Runners . To the right of the runner, you want to edit, select Edit ( ). In the Maximum job timeout field, enter a value in seconds. The minimum amount is 600 seconds (10 minutes). Select Save changes .
Thu 2 May 2024 // 14:15 UTC. The US Cybersecurity and Infrastructure Security Agency (CISA) is forcing all federal agencies to patch a critical vulnerability in GitLab's Community and Enterprise editions, confirming it is very much under "active exploit." When CISA adds a vulnerability to its Known Exploited Vulnerabilities (KEV) list, it means ...
Previously, I have gitlab community server installed in my server with this IP 192.168.1.X, and I'm using it with no problem. But recently my network administrator change the server IP to different using 10.176.10.X. And when I trying to clone my projects from it, the default URL for clone still using the old IP number.
Change the system hostname. If you have a public DNS name registered for the IP address of your instance (such as webserver.mydomain.com), you can set the system hostname so your instance identifies itself as a part of that domain.This also changes the shell prompt so that it displays the first portion of this name instead of the hostname supplied by AWS (for example, ip-12-34-56-78).
Modify the GitLab host name Change the default address automatically. It is advisable to use a host name instead of an IP address for Gitlab. However, we recommend not using git. in the host name as this causes problems when accessing Gitlab over HTTP. Follow these steps: At the server console, run the following command:
1.1 The Surveillance Panel (SP) was tasked by the Air Navigation Commission to undertake specific studies and to develop technical and operational ICAO provisions for aeronautical surveillance systems, collision avoidance systems and their applications as outlined in the Global Air Navigation Plan. 1.2 This paper highlights the changes to the ...
thanks for response, we want to setup Gitlab like you described in 1st option but my question is how it can be accessed from other network. The link you said, talks about configuration of "external url" that's right but that is only accessible over internet to the people on same network. Do i need to configure the static IP for this ? -
Can I somehow chenge default URL of the gitlab? I have set localhost http://192.168.1.189/group/repo but i need to use public IP for my team mates. Is it possible to ...
The US Patent and Trademark Office proposed to add a requirement for terminal disclaimers filed to address nonstatutory double patenting, the agency announced Thursday. The proposed rule would require a patentee to agree that the patent covered by the terminal disclaimer will be enforceable only if the patent has never been tied through one or ...
"Keenetic" router through the service "KeenDNS" redirects https traffic to local server with local IP 192.168.1.78. If in Browser manually change IP to domain then no redirects and all work fine.
But I'm caught at the configuration of the IP / domain. Because I don't have a domain I want to use my static server IP like this: Sudo gitlab-ctl reconfigure -> "133.713.37.01/gitlab" Is it even possible to set up gitlab without a domain or am I doing something wrong? I'm grateful for any help